Most of us have probably heard the term “smishing” — which is a portmanteau for traditional phishing scams sent through SMS text messages. Smishing messages usually include a link to a site that spoofs a popular bank and tries to siphon personal information. But increasingly, phishers are turning to a hybrid form of smishing — blasting out linkless text messages about suspicious bank transfers as a pretext for immediately calling and scamming anyone who responds via text.
KrebsOnSecurity recently heard from a reader who said his daughter received an SMS that said it was from her bank, and inquired whether she’d authorized a $5,000 payment from her account. The message said she should reply “Yes” or “No,” or 1 to decline future fraud alerts.
Since this seemed like a reasonable and simple request — and she indeed had an account at the bank in question — she responded, “NO.”
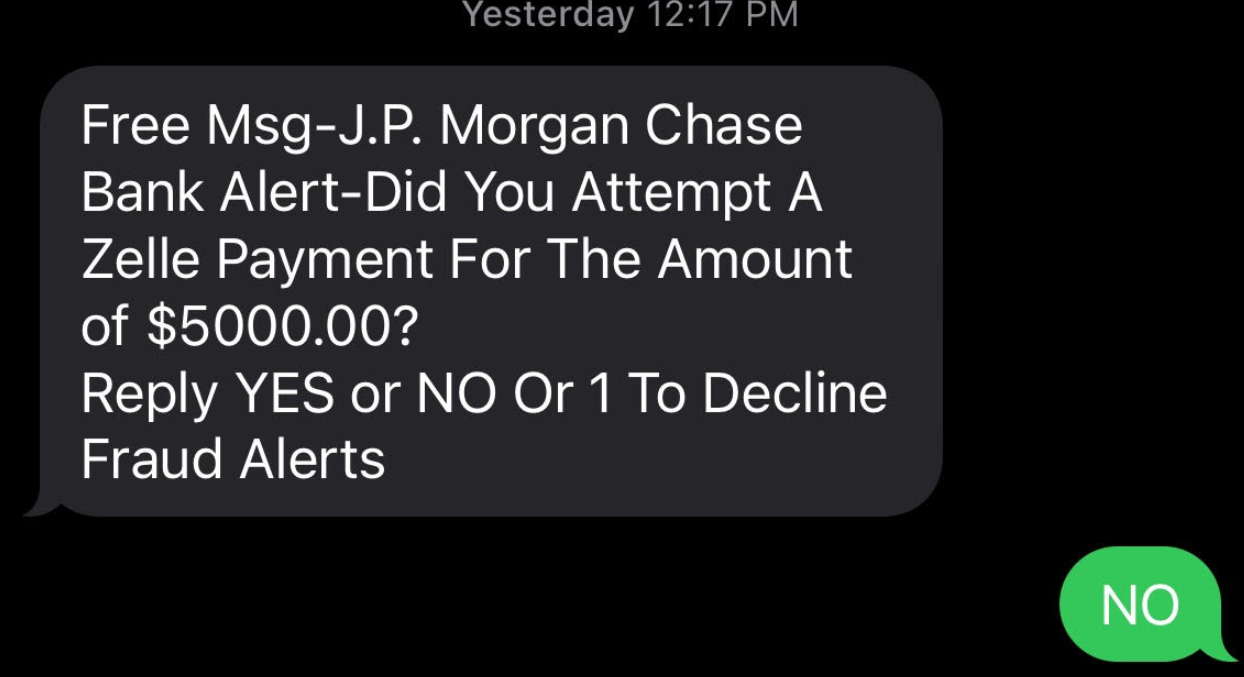
Seconds later, her mobile phone rang.
“When she replied ‘no,’ someone called immediately, and the caller ID said ‘JP Morgan Chase’,” reader Kris Stevens told KrebsOnSecurity. “The person on the phone said they were from the fraud department and they needed to help her secure her account but needed information from her to make sure they were talking to the account owner and not the scammer.”
Thankfully, Stevens said his daughter had honored the gold rule regarding incoming phone calls about fraud: When In Doubt, Hang up, Look up, and Call Back.
“She knows the drill so she hung up and called Chase, who confirmed they had not called her,” he said. “What was different about this was it was all very smooth. No foreign accents, the pairing of the call with the text message, and the fact that she does have a Chase account.”
The remarkable aspect of these phone-based phishing scams is typically the attackers never even try to log in to the victim’s bank account. The entirety of the scam takes place over the phone.
We don’t know what the fraudsters behind this clever hybrid SMS/voice phishing scam intended to do with the information they might have coaxed from Stevens’ daughter. But in previous stories and reporting on voice phishing schemes, the fraudsters used the phished information to set up new financial accounts in the victim’s name, which they then used to receive and forward large wire transfers of stolen funds.
Even many security-conscious people tend to focus on protecting their online selves, while perhaps discounting the threat from less technically sophisticated phone-based scams. In 2020 I told the story of “Mitch” — the tech-savvy Silicon Valley executive who got voice phished after he thought he’d turned the tables on the scammers.
Unlike Stevens’ daughter, Mitch didn’t hang up with the suspected scammers. Rather, he put them on hold. Then Mitch called his bank on the other line and asked if their customer support people were in fact engaged in a separate conversation with him over the phone.
The bank replied that they were indeed speaking to the same customer on a different line at that very moment. Feeling better, Mitch got back on the line with the scammers. What Mitch couldn’t have known at that point was that a member of the fraudster’s team simultaneously was impersonating him on the phone with the bank’s customer service people.
So don’t be Mitch. Don’t try to outsmart the crooks. Just remember this anti-fraud mantra, and maybe repeat it a few times in front of your friends and family: When in doubt, hang up, look up, and call back. If you believe the call might be legitimate, look up the number of the organization supposedly calling you, and call them back.
And I suppose the same time-honored advice about not replying to spam email goes doubly for unsolicited text messages: When in doubt, it’s best not to respond.




If you need to look up a customer service phone number be sure to get it directly off the businesses web page, not just a Google search.
Even better to call the number on the back of your credit card or on a recent statement (electronic or paper).
I work for a bank and we have had this same issue. My question is how do they know that the people that they are calling are that bank’s customer? Also, how did they get that person’s cell phone number? In our case, the scammers actually went as far as recording our on-hold message and played that back to the victim.
The initial texts seem to be random. It’s more rare now with all the bank consolidations, but I’ve gotten several texts from banks that I have never SET FOOT IN, let alone had an account with.
And “Hang up, Look up and Call the Website number” is excellent advice.
Ten Years ago I was one Enter key away from being scammed out of $500.
The laughable ones are the texts and calls purporting to be from the IRS. You didn’t send me a letter first? SCAM.
when I worked for a Bank, In a similar situation, e had a fraud (management) system and very alert customer service representatives that knew the voice of the customer, whose email AND phone had been taken over, and were able to stop the scam.
Social media may be one area – if you follow the bank on twitter or facebook or linkedin, coupled with positive interaction with the bank, then that’s enough for a scammer to attempt this kind of attack.
People “follow” banks? Really? Seems weird unless you work at one?
It can either be targeted or just the nature of mass communication. If they send 1000 sms messages claiming to be from Chase the odds are a few who receive the messages well have a Chase account.
You also have scammers who pay people to steal physical mail. They then use that stolen mail in targeted phishing attacks sometimes called spear phishing.
It could be “The Case of the Swami Scam” [1].
They could be smarter than that (picking the most likely banks for a given range). Or it could be that they picked up a list of stolen Credit Card / Debit Card transactions as those numbers tend to be tied to banks.
[1] https://www.youtube.com/watch?v=Tj-XMRu_q4s
If you have a calling center making 1000s of calls, chases are at least one of those calls the person has a bank account at the bank you are talking about. I think it is random. I never ever answer my phone unless it is my husband or son. Period. I will call back. Nothing is that important to me.
We do all our banking in person at a local branch office. To many banks require online access.
I wouldn’t even trust the web site – since there can be DNS hacks and other things.
Look at the back of your credit card or at your most recent statement and you will always find a customer service phone number. I would trust that over anything on any web page.
ipconfig /flushdns
use a script blocker, it a pain but well worth the added security.
some security over unneeded unsecure security.
You´d be surprised how many calls come into us (bank) through the central switchboard that customers googled off our name on the back of the card in the small “this card is issued by” print.
And that is instead of calling the customer service number printed in bigger and bolder typeface listed just centimeters next to it on that card back.
Now as backoffice we do not have access to customer data, so we need to refer them back to the customer service number on their very card.
I work in Account Takeover/Identity Theft at a very large bank. I’ve been seeing this specific scam in action every day, probably 3-4 times per day for the last month. I’ve listened in real-time as criminals continue their scam on a customer with me in the background. It’s interesting to hear customers’ stories and discover how different some of the scams can be. One thing’s for sure, some criminals are much better than others!
I spoke recently with a customer who hung up and called us before the criminals could finish their scam. He was amazed that they’ve spoofed not only our main phone number and our SMS text number, but also the hold music, security questions, and our lingo. We began to compare and the ONLY thing we discovered they could NOT do is read our regulatory and compliance disclosures when we are sending the customer a new debit or credit card or when we are accessing their credit card account.
After reading Brian’s article on bots that the criminals are using to send SMS security codes, and I’m convinced that these are what our customers are receiving.
With all the data breaches worldwide, it doesn’t surprise me that my information is out there! I know my landline and my mobile numbers are out there — so are my husband’s — and my emails have been part of data breaches that total over 20 BILLION emails. Genealogy websites have been breached — yes, even the biggies — and the Equifax breach put all my info out there too.
Someone filed an unemployment claim in Kentucky in my husband’s name and also tried to open a Chase account with his info. Thank God for credit alerts, freezes and lockdowns! I believe EVERYTHING about me is out on the dark web and that we have no reason to believe that ANYTHING is private anymore.
Thanks for your comment and perspective, Bella. I can see this scam being especially effective because while people may be on guard against unsolicited messages asking them to click a link, this never asks for that but sets up beautifully the context for a follow-up call. But…man, the hold music and the security questions? That’s insane.
Does anyone have knowledge of scammers using 5-6 digit short codes to send smishing attempts?
I had an incident that happened to me last year where my famous bank sent me an SMS alert for me to call them about possible misuse of my debit card. I called the number in the text and the operator told me that someone in Nigeria was using my debit card number but he then told me he needed to verify my identity and asked for some of my PII. An alarm went off and I explained that I work in data security and I would need to call my famous bank back at a number that I knew was legit. He said he understood perfectly, but I thought that could have been part of his scam to win my confidence and keep me on the line! I called the bank back and as it turned out, there was a guy in Nigeria buying stuff with my debit card number.
A legitimate text or email warning of possible theft to a customer should include the words, ” please call the number that’s on the back of your card or from your last statement and ask for the fraud department” . Even better would be if the message includes words that note in effect that the email or SMS warning is a one way message (i.e. that no one will respond if you Reply to the message), so that the customer has to call that the number. No pone numbers should be provided in the alert. This should be the standard operating procedure for every financial institution and it should be widely publicized by the industry that this is the only way a customer will alerted to possible theft.
Good suggestions.
A legitimate text or email warning of possible theft to a customer should include the words, ” please call the number that’s on the back of your card or from your last statement and ask for the fraud department” . Even better would be if the message includes words that note in effect that the email or SMS warning is a one way message (i.e. that no one will respond if you Reply to the message), so that the customer has to call that number. This should be standard operating procedure for every financial institution and it should be widely publicized by the industry that this is the only way you will alerted to possible theft.
A few days ago I received a similar message. These blogs would definitely help us keep posted about new trends in the market.
The crappy thing about the whole hang up, call them at a known number thing is we all know it’s going to be a slog to get through to someone that way.
The banks have made reaching a real person so hard that having someone on the line already, even if there’s a chance they’re a criminal, It’s a risk some are going to take for convenience
Now That I See It Again, The Enthusiastic Capitalization Of Words Should Have Been Enough To Tip Us Off.
The problem with this advice is:
You might be calling your local branch to verify, but they may not know that some outsourced customer service or even fraud detection call center is or is notz reaching out to you that moment.
Not every bank has real-time CRM where everybody in the bank can see what is going on with the customer at that second.
So yes, by all means, check and call back. But even if the brtanch said they didn´t call you, the card fraud department may very well have tried. Utter dilemma.
If they have integrated call-log consumer systems ‘they’ would know if either side did, probably.
If they don’t it’s as you say.
Have the bank put a secret word/phrase/number of your choice in your file. Then whenever you speak to Customer service ask them to tell you what it is.
This doesn’t work, since an attacker could ask the bank for the same information.
There’s no way for this form of authentication to work.
STIR/SHAKEN should fix this, since we should get the equivalent of a lock icon for banks, and thus you’d be able to know that a phone number that’s calling you is the phone number it says (or is at least authorized by that number), and then you could validate it w/ the printed number on your card.
Not sure how the STIR/SHAKEN rollout is going in the US.
I think it is the other way around… you tell them.
I have never had an account where they have identify themselves with a secret code.
But then I don’t talk to anyone who CALLS me about my account…. I call my bank back and discuss the issue.
Banks in the United States don’t call you if their is a problem with your account, you call them
A VP at my bank called me two or three years ago to ask if a certain wire transfer was legitimate. It was. Also, I’ve known that VP for years — there was no doubt that it really was the VP from the bank.
yes we do . all the time. I’m a bank fraud investigator and it’s done on all kinds of transactions.
They do from the Fraud department, and also if you have a business account and an account manager…
My wife got a call a couple of years ago, supposedly about a problem transaction on her credit card. We followed the rule, hung up immediately and called right back at a known number. Turns out they HAD called her just seconds earlier!
I have absolutely had calls from my credit union when there was an issue with my account.
In one case, my wife’s death for some reason made them change my account number (which had been my sole account, then I added her to it, then she died, so I lost my account number?).
My bad, I hadn’t realized that invalidated my checks. They had automatically replaced my credit cards, but not checks. The call I received was because I had written a check (1st one in many years) on the old account.
Anyway, there is definitely a problem with old and new systems coordinating properly.
(This same institution once had a “security-ish” feature when you logged in to them online that showed you a special image and caption that you had selected to prove they were the real deal. When they changed to a new online vendor, this went away. Took me a long time on hold before a weary CS rep told me that yes, the powers that be had made the change, and no, they hadn’t deigned to notify either customers or the CS reps!)
Most banks IVR’s have week authentication. Fraudsters will exploit the security vulnerable to data mine and use the obtained information to help “legitimize” the fraud attempt and further the scheme e.g. account balance, recent activity, etc. I’ve also seen fraudsters requiring the OLB username to “authenticate” the customer, initiating an online password reset online, prompting the OTP and requesting the customer to provide to further validate. They fraudster will then create a new password and successfully completed the ATO.
I work in a bank. when we issue debit cards, we give them a card protector sleeve with important debit card phone numbers/websites printed on it. Many customers remove the sleeve, as it interferes with their wallet. I always mention to them, to keep that sleeve – has important information regarding debit card. Sometimes, reps tell customers to call the number in back of card- but if you happen to lose your card ….
First, always tell an unknown caller that it’s not your phone. “This is my girlfriend’s phone, she’s busy, I’ll give her the message”. End of scam.
90% of these scams are designed to get the person to read off an SMS code so the cybercriminal can get access to the account. They already have the user’s login credentials. They just need the OTP to pass the step-up challenge and these sophisticated phone scams are what they use to do that. The updated CFPB guidance issued a few months back was expanded to protect consumers against these very types of social engineering scams. Trace Fooshee at Aite Group published a nice piece on this:
https://aite-novarica.com/blogs/trace-fooshee/did-cfpb-just-take-first-step-shifting-liability-scams
Are they looking to withdraw money or to get your info?
And ya’ll think I am a wuss for not banking from my phone. I’m laughing all the way to the bank.
Just as fun comment: I have my phone set up to NOT confirm I opened a text message.
And if it not from a friend I do not press 1 or type NO or STOP.
I just delete and they will never know if they got through or not.
I only use STOP if it a company I use. They will send texts at 6 am and wake me UP!
This works great because I RARELY text…
Problem is that at least here (Germany) my credit-card bank sends legitimate text messages if they detect suspicious activity and temporary disable the card. Then you can answer if this was really you or not and the card is reactivated or will be replaced. Fully automated without talking to anyone. So in this case not answering might be not the best advise.
First, always tell an unknown caller that it’s not your phone. “This is my girlfriend’s phone, she’s busy, I’ll give her the message”. End of scam.
Thanks for the information keep sharing such informative post keep suggesting such post.
I highly appreciate your hard-working skills as the post you published have some great information which is quite beneficial for me, I hope you will post more like that in the future.
My wife just got phished. They had her bank name and the suspicious charges were charges we made in the past. When they called it was her bank name on the caller id. I wish I had read this sooner. They got the OTP. She’s on her way to the bank now. Now what?
I’ve been researching this for a long time. I found this place by chance from Google. Thank you for the useful information.