
The 911 service as it existed until July 28, 2022.
911[.]re, a proxy service that since 2015 has sold access to hundreds of thousands of Microsoft Windows computers daily, announced this week that it is shutting down in the wake of a data breach that destroyed key components of its business operations. The abrupt closure comes ten days after KrebsOnSecurity published an in-depth look at 911 and its connections to shady pay-per-install affiliate programs that secretly bundled 911’s proxy software with other titles, including “free” utilities and pirated software.
911[.]re is was one of the original “residential proxy” networks, which allow someone to rent a residential IP address to use as a relay for his/her Internet communications, providing anonymity and the advantage of being perceived as a residential user surfing the web.
Residential proxy services are often marketed to people seeking the ability to evade country-specific blocking by the major movie and media streaming providers. But some of them — like 911 — build their networks in part by offering “free VPN” or “free proxy” services that are powered by software which turns the user’s PC into a traffic relay for other users. In this scenario, users indeed get to use a free VPN service, but they are often unaware that doing so will turn their computer into a proxy that lets others use their Internet address to transact online.
From a website’s perspective, the IP traffic of a residential proxy network user appears to originate from the rented residential IP address, not from the proxy service customer. These services can be used in a legitimate manner for several business purposes — such as price comparisons or sales intelligence — but they are massively abused for hiding cybercrime activity because they can make it difficult to trace malicious traffic to its original source.
As noted in KrebsOnSecurity’s July 19 story on 911, the proxy service operated multiple pay-per-install schemes that paid affiliates to surreptitiously bundle the proxy software with other software, continuously generating a steady stream of new proxies for the service.
A cached copy of flashupdate[.]net circa 2016, which shows it was the homepage of a pay-per-install affiliate program that incentivized the silent installation of 911’s proxy software.
Within hours of that story, 911 posted a notice at the top of its site, saying, “We are reviewing our network and adding a series of security measures to prevent misuse of our services. Proxy balance top-up and new user registration are closed. We are reviewing every existing user, to ensure their usage is legit and [in] compliance with our Terms of Service.”
At this announcement, all hell broke loose on various cybercrime forums, where many longtime 911 customers reported they were unable to use the service. Others affected by the outage said it seemed 911 was trying to implement some sort of “know your customer” rules — that maybe 911 was just trying to weed out those customers using the service for high volumes of cybercriminal activity.
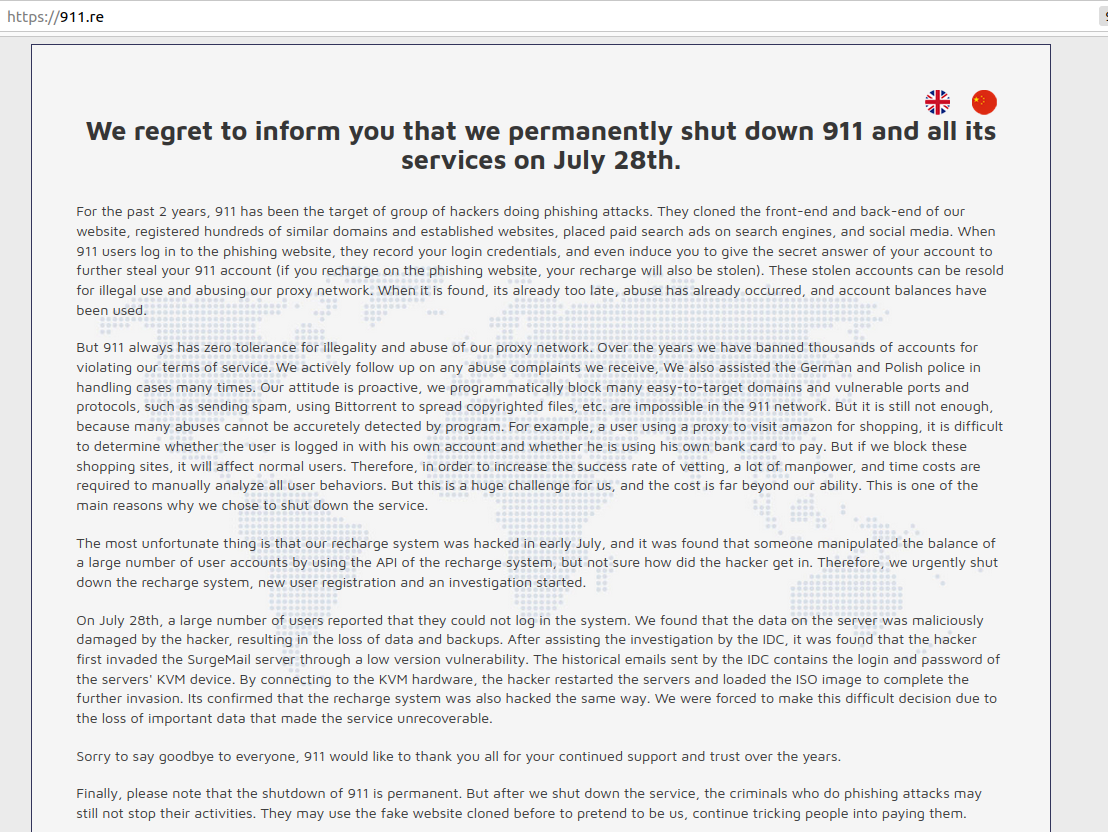
Then on July 28, the 911 website began redirecting to a notice saying, “We regret to inform you that we permanently shut down 911 and all its services on July 28th.”
According to 911, the service was hacked in early July, and it was discovered that someone manipulated the balances of a large number of user accounts. 911 said the intruders abused an application programming interface (API) that handles the topping up of accounts when users make financial deposits with the service.
“Not sure how did the hacker get in,” the 911 message reads. “Therefore, we urgently shut down the recharge system, new user registration, and an investigation started.”
However the intruders got in, 911 said, they managed to also overwrite critical 911[.]re servers, data and backups of that data.
“On July 28th, a large number of users reported that they could not log in the system,” the statement continues. “We found that the data on the server was maliciously damaged by the hacker, resulting in the loss of data and backups. Its [sic] confirmed that the recharge system was also hacked the same way. We were forced to make this difficult decision due to the loss of important data that made the service unrecoverable.”
Operated largely out of China, 911 was an enormously popular service across many cybercrime forums, and it became something akin to critical infrastructure for this community after two of 911’s longtime competitors — malware-based proxy services VIP72 and LuxSocks — closed their doors in the past year.
Now, many on the crime forums who relied on 911 for their operations are wondering aloud whether there are any alternatives that match the scale and utility that 911 offered. The consensus seems to be a resounding “no.”
I’m guessing we may soon learn more about the security incidents that caused 911 to implode. And perhaps other proxy services will spring up to meet what appears to be a burgeoning demand for such services at the moment, with comparatively little supply.
In the meantime, 911’s absence may coincide with a measurable (if only short-lived) reprieve in unwanted traffic to top Internet destinations, including banks, retailers and cryptocurrency platforms, as many former customers of the proxy service scramble to make alternative arrangements.
Riley Kilmer, co-founder of the proxy-tracking service Spur.us, said 911’s network will be difficult to replicate in the short run.
“My speculation is [911’s remaining competitors] are going to get a major boost in the short term, but a new player will eventually come along,” Kilmer said. “None of those are good replacements for LuxSocks or 911. However, they will all allow anyone to use them. For fraud rates, the attempts will continue but through these replacement services which should be easier to monitor and stop. 911 had some very clean IP addresses.”
911 wasn’t the only major proxy provider disclosing a breach this week tied to unauthenticated APIs: On July 28, KrebsOnSecurity reported that internal APIs exposed to the web had leaked the customer database for Microleaves, a proxy service that rotates its customers’ IP addresses every five to ten minutes. That investigation showed Microleaves — like 911 — had a long history of using pay-per-install schemes to spread its proxy software.




Could this be a case of /actual/ hactivism? I would love to see the post-mortem of what happened.
Congrats again, Brian; keep up the good fight!
“None of those are good replacements for L*s or 9*. However, (!) they will _all_ allow anyone to use them(!) For fraud rates, the attempts _will_ continue but through these replacement services which _should_ (?) be easier to monitor and stop. 911 had some very clean IP addresses.” Clean IP addresses come and go all the time. Like MS switching off macros makes malware go %more into containers that circumvent MOTW it’s 6 of one half dozen of another. There will be a proportional %dip in overall throughput – until the next crest. “eventually” = 30-90 days?
Perhaps a rival gang or even a nation state did this to take over 911’s infrastructure for their own purposes? What happens to all the personal computers still running 911’s software?
Well, I do not believe the service was unrecoverable. They just looked for an easy way out before things get difficult. So a “we were hacked – all data lost – not our fault, sorry” makes total sense. They get out clean. But seriously, I highly doubt that they had no means in recovering the services.
Exactly.
Where can we get a similar proxy?
Have you checked the prisons?
Are you able to get any help ??
Any similar to 911 s5?
Prob of future will be daily proxies
“The cost is far beyond our ability.” They just bailed out on us and took the easy way out, nothing else. I also had some credits in my account, but I doubt they’ll refund anyone.
Refund what? That which does not exist?
That’s really sad. They should pay the money which they took for services they didn’t provide.
So they tricked people into installing malware that would add their computers to what was basically an IP address laundering ring, leaving those people vulnerable to criminal charges when the company’s customers use the people’s computers for cybercrime? Then good riddance.
I don’t care if some boomer installed malware on their PC. they are not going to get charged for cybercrime because someone was posting memes from 911.re service.
I’ve noticed a SIGNIFICANT reduction in spam since these proxy services have shut down.
I haven’t gotten a spam email in 4 years.
Less volume but higher quality.
My computer has been working smoothly with less humming and heat-up for the past week.
Can one be an unwilling proxy?
Windows was trying to install an update the entire time.
If you’re using any service operated from within territory ruled by the CCP just know that it’s 99% likely to be SPYWARE, and it’s also highly probable that the data was routed directly to CCP Intelligence collection services. When I saw the words “surreptitious install” and “China” in the same article, I knew right away what was going on. MITM data harvesting op.
If you’re using any service operated from within territory ruled by Russia just know that it’s 99% likely to be MALWARE, and it’s also highly probable that the data was routed directly to SVR Intelligence collection services.
The problem is in knowing where things are actually operated. If you know it’s easy.
And by easy I mean feasible, maybe. Not easy. Wrong word.