This month’s Patch Tuesday offers a little something for everyone, including security updates for a zero-day flaw in Microsoft Windows that is under active attack, and another Windows weakness experts say could be used to power a fast-spreading computer worm. Also, Apple has also quashed a pair of zero-day bugs affecting certain macOS and iOS users, and released iOS 16, which offers a new privacy and security feature called “Lockdown Mode.” And Adobe axed 63 vulnerabilities in a range of products.
Microsoft today released software patches to plug at least 64 security holes in Windows and related products. Worst in terms of outright scariness is CVE-2022-37969, which is a “privilege escalation” weakness in the Windows Common Log File System Driver that allows attackers to gain SYSTEM-level privileges on a vulnerable host. Microsoft says this flaw is already being exploited in the wild.
Kevin Breen, director of cyber threat research at Immersive Labs, said any vulnerability that is actively targeted by attackers in the wild must be put to the top of any patching list.
“Not to be fooled by its relatively low CVSS score of 7.8, privilege escalation vulnerabilities are often highly sought after by cyber attackers,” Breen said. “Once an attacker has managed to gain a foothold on a victim’s system, one of their first actions will be to gain a higher level of permissions, allowing the attacker to disable security applications and any device monitoring. There is no known workaround to date, so patching is the only effective mitigation.”
Satnam Narang at Tenable said CVE-2022-24521 — a similar vulnerability in the same Windows log file component — was patched earlier this year as part of Microsoft’s April Patch Tuesday release and was also exploited in the wild.
“CVE-2022-37969 was disclosed by several groups, though it’s unclear if CVE-2022-37969 is a patch-bypass for CVE-2022-24521 at this point,” Narang said.
Another vulnerability Microsoft patched this month — CVE-2022-35803 — also seems to be related to the same Windows log file component. While there are no indications CVE-2022-35803 is being actively exploited, Microsoft suggests that exploitation of this flaw is more likely than not.
Trend Micro’s Dustin Childs called attention to CVE-2022-34718, a remote code execution flaw in the Windows TCP/IP service that could allow an unauthenticated attacker to execute code with elevated privileges on affected systems without user interaction.
“That officially puts it into the ‘wormable’ category and earns it a CVSS rating of 9.8,” Childs said. “However, only systems with IPv6 enabled and IPSec configured are vulnerable. While good news for some, if you’re using IPv6 (as many are), you’re probably running IPSec as well. Definitely test and deploy this update quickly.”
Cisco Talos warns about four critical vulnerabilities fixed this month — CVE-2022-34721 and CVE-2022-34722 — which have severity scores of 9.8, though they are “less likely” to be exploited, according to Microsoft.
“These are remote code execution vulnerabilities in the Windows Internet Key Exchange protocol that could be triggered if an attacker sends a specially crafted IP packet,” wrote Jon Munshaw and Asheer Malhotra. “Two other critical vulnerabilities, CVE-2022-35805 and CVE-2022-34700 exist in on-premises instances of Microsoft Dynamics 365. An authenticated attacker could exploit these vulnerabilities to run a specially crafted trusted solution package and execute arbitrary SQL commands. The attacker could escalate their privileges further and execute commands as the database owner.”
 Not to be outdone, Apple fixed at least two zero-day vulnerabilities when it released updates for iOS, iPadOS, macOS and Safari. CVE-2022-32984 is a problem in the deepest recesses of the operating system (the kernel). Apple pushed an emergency update for a related zero-day last month in CVE-2022-32983, which could be used to foist malware on iPhones, iPads and Macs that visited a booby-trapped website.
Not to be outdone, Apple fixed at least two zero-day vulnerabilities when it released updates for iOS, iPadOS, macOS and Safari. CVE-2022-32984 is a problem in the deepest recesses of the operating system (the kernel). Apple pushed an emergency update for a related zero-day last month in CVE-2022-32983, which could be used to foist malware on iPhones, iPads and Macs that visited a booby-trapped website.
Also listed under active attack is CVE-2022-32817, which has been fixed on macOS 12.6 (Monterey), macOS 11.7 (Big Sur), iOS 15.7 and iPadOS 15.7, and iOS 16. The same vulnerability was fixed in Apple Watch in July 2022, and credits Xinru Chi of Japanese cybersecurity firm Pangu Lab.
“Interestingly, this CVE is also listed in the advisory for iOS 16, but it is not called out as being under active exploit for that flavor of the OS,” Trend Micro’s Childs noted. “Apple does state in its iOS 16 advisory that ‘Additional CVE entries to be added soon.’ It’s possible other bugs could also impact this version of the OS. Either way, it’s time to update your Apple devices.”
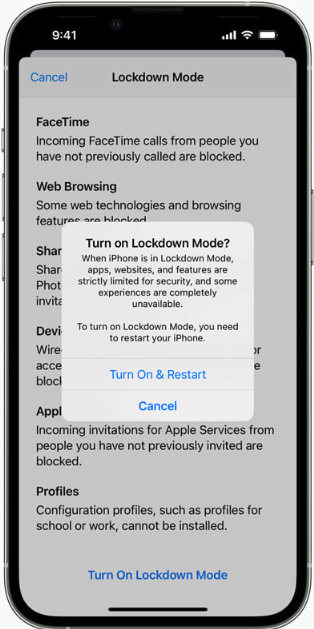
Apple’s iOS 16 includes two new security and privacy features — Lockdown Mode and Safety Check. Wired.com describes Safety Check as a feature for users who are at risk for, or currently experiencing, domestic abuse.
“The tool centralizes a number of controls in one place to make it easier for users to manage and revoke access to their location data and reset privacy-related permissions,” wrote Lily Hay Newman.
“Lockdown Mode, on the other hand, is meant for users who potentially face targeted spyware attacks and aggressive state-backed hacking. The feature comprehensively restricts any nonessential iOS features so there are as few potential points of entry to a device as possible. As more governments and repressive entities around the world have begun purchasing powerful commodity spyware to target individuals of particular importance or interest, iOS’s general security defenses haven’t been able to keep pace with these specialized threats.”
To turn on Lockdown Mode in iOS 16, go to Settings, then Privacy and Security, then Lockdown Mode. Safety Check is located in the same area.
Finally, Adobe released seven patches addressing 63 security holes in Adobe Experience Manager, Bridge, InDesign, Photoshop, InCopy, Animate, and Illustrator. More on those updates is here.
Don’t forget to back up your data and/or system before applying any security updates. If you experience glitches or problems installing any of these patches this month, please consider leaving a comment about it below; there’s a decent chance other readers have experienced the same and may chime in here with useful tips.




SUSAN BRADLEY (The Techs all over the world follow her on Windows Updates)
September updates get released
Posted on September 13, 2022 at 12:05 CDT by Susan Bradley • Comment in the Forums
…and here we go again. Remember our mantra, if you care about your machine ensure that you have a full image backup.
Ensure that you have deferred updates (always check the master patch page for the deferral date) and/or put your computer on “metered” network trick.
79 vulnerabilities
2 publicly disclosed
5 critical
1 exploited
Another print spooler (ugh)
Too soon to tell if the bugs (audio/etc) of last month are included in this update. More as I digest the details.
Updates to this post:
Windows 10 patch does NOT indicate audio issues are triggered in this release.
Other resources include Dustin Childs’ Zero day blog
The one critical bug in TCP/IP impacts IPv6 with IPsec configurations (translations corporations with IPsec so not home and consumer users)
Windows Security MS-DEFCON 2, Patch Lady Posts, September 2022 Black Tuesday
“if you care about your machine ensure that you have a full image backup.”
If you care about your machine, run Unix/Linux and run Windows as a virtual machine, at best. A full image backup should not be a requirement of doing what is a periodic maintenance task of all operating systems.
(From a guy that first started using Windows when it came on floppies…)
It ought to be but it’s not a requirement to backup, just a damn good idea.
On any platform. Linux updates have had regression issues in the past.
Just not every other month like our dear friends in Redmond.
I had a issue with KB5012170: “Security update for Secure Boot DBX” August 9 security patch which threw a error after trying to install . It was on a Windows 10 machine that is ten years old and originally had Windows 7
After trial and error trying to fix the issue , I ended up just hiding KB5012170 which allowed me to install the September security updates without any issues
iOS 16 offers a variety of features that can be beneficial for students. For example, the new iOS 16 operating system includes an update to the Notes app that makes it easier to keep track of homework assignments and deadlines. In addition, the Messages app has been updated to allow for more seamless communication between classmates. And the Maps app now includes indoor mapping capabilities, which can be useful for finding classrooms and other facilities on campus. Finally, iOS 16 also includes a number of accessibility improvements that can make it easier for students with disabilities to use Apple products.
I want to see 3rd party testing of lockdown mode. Sounds like my kind of mode.
Last evening I updated my desktop and notebook both running 21H2. Both restarted fine. No prob’s so far.
With the update to MacOS Monterey 12.5.1, Bluetooth tethering with cellphone hotspots just went away, and no tech “journalist” warned us about it.
I’m hoping that the solution isn’t to disable SMB, as that is the most stable protocol I’ve found for my needs.