A Croatian national has been arrested for allegedly operating NetWire, a Remote Access Trojan (RAT) marketed on cybercrime forums since 2012 as a stealthy way to spy on infected systems and siphon passwords. The arrest coincided with a seizure of the NetWire sales website by the U.S. Federal Bureau of Investigation (FBI). While the defendant in this case hasn’t yet been named publicly, the NetWire website has been leaking information about the likely true identity and location of its owner for the past 11 years.
Typically installed by booby-trapped Microsoft Office documents and distributed via email, NetWire is a multi-platform threat that is capable of targeting not only Microsoft Windows machines but also Android, Linux and Mac systems.
NetWire’s reliability and relatively low cost ($80-$140 depending on features) has made it an extremely popular RAT on the cybercrime forums for years, and NetWire infections consistently rank among the top 10 most active RATs in use.
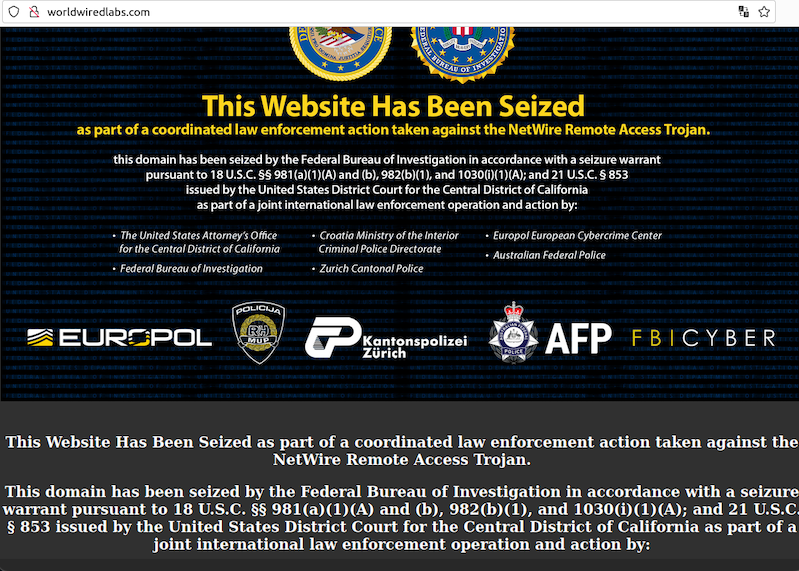
NetWire has been sold openly on the same website since 2012: worldwiredlabs[.]com. That website now features a seizure notice from the U.S. Department of Justice (DOJ), which says the domain was taken as part of “a coordinated law enforcement action taken against the NetWire Remote Access Trojan.”
“As part of this week’s law enforcement action, authorities in Croatia on Tuesday arrested a Croatian national who allegedly was the administrator of the website,” reads a statement by the DOJ today. “This defendant will be prosecuted by Croatian authorities. Additionally, law enforcement in Switzerland on Tuesday seized the computer server hosting the NetWire RAT infrastructure.”
Neither the DOJ’s statement nor a press release on the operation published by Croatian authorities mentioned the name of the accused. But it’s fairly remarkable that it has taken so long for authorities in the United States and elsewhere to move against NetWire and its alleged proprietor, given that the RAT’s author apparently did very little to hide his real-life identity.
The WorldWiredLabs website first came online in February 2012 using a dedicated host with no other domains. The site’s true WHOIS registration records have always been hidden by privacy protection services, but there are plenty of clues in historical Domain Name System (DNS) records for WorldWiredLabs that point in the same direction.
In October 2012, the WorldWiredLabs domain moved to another dedicated server at the Internet address 198.91.90.7, which was home to just one other domain: printschoolmedia[.]org, also registered in 2012.
According to DomainTools.com, printschoolmedia[.]org was registered to a Mario Zanko in Zapresic, Croatia, and to the email address zankomario@gmail.com. DomainTools further shows this email address was used to register one other domain in 2012: wwlabshosting[.]com, also registered to Mario Zanko from Croatia.
A review of DNS records for both printschoolmedia[.]org and wwlabshosting[.]com shows that while these domains were online they both used the DNS name server ns1.worldwiredlabs[.]com. No other domains have been recorded using that same name server.

The WorldWiredLabs website, in 2013. Source: Archive.org.
DNS records for worldwiredlabs[.]com also show the site forwarded incoming email to the address tommaloney@ruggedinbox.com. Constella Intelligence, a service that indexes information exposed by public database leaks, shows this email address was used to register an account at the clothing retailer romwe.com, using the password “123456xx.”
Running a reverse search on this password in Constella Intelligence shows there are more than 450 email addresses known to have used this credential, and two of those are zankomario@gmail.com and zankomario@yahoo.com.
A search on zankomario@gmail.com in Skype returns three results, including the account name “Netwire” and the username “Dugidox,” and another for a Mario Zanko (username zanko.mario).
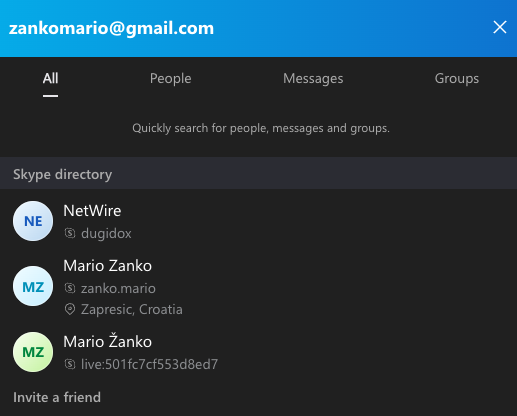 Dugidox corresponds to the hacker handle most frequently associated with NetWire sales and support discussion threads on multiple cybercrime forums over the years.
Dugidox corresponds to the hacker handle most frequently associated with NetWire sales and support discussion threads on multiple cybercrime forums over the years.
Constella ties dugidox@gmail.com to a number of website registrations, including the Dugidox handle on BlackHatWorld and HackForums, and to IP addresses in Croatia for both. Constella also shows the email address zankomario@gmail.com used the password “dugidox2407.”
In 2010, someone using the email address dugidox@gmail.com registered the domain dugidox[.]com. The WHOIS registration records for that domain list a “Senela Eanko” as the registrant, but the address used was the same street address in Zapresic that appears in the WHOIS records for printschoolmedia[.]org, which is registered in Mr. Zanco’s name.
Prior to the demise of Google+, the email address dugidox@gmail.com mapped to an account with the nickname “Netwire wwl.” The dugidox email also was tied to a Facebook account (mario.zanko3), which featured check-ins and photos from various places in Croatia.
That Facebook profile is no longer active, but back in January 2017, the administrator of WorldWiredLabs posted that he was considering adding certain Android mobile functionality to his service. Three days after that, the Mario.Zank3 profile posted a photo saying he was selected for an Android instruction course — with his dugidox email in the photo, naturally.
Incorporation records from the U.K.’s Companies House show that in 2017 Mr. Zanko became an officer in a company called Godbex Solutions LTD. A Youtube video invoking this corporate name describes Godbex as a “next generation platform” for exchanging gold and cryptocurrencies.
The U.K. Companies House records show Godbex was dissolved in 2020. It also says Mr. Zanko was born in July 1983, and lists his occupation as “electrical engineer.”
A statement from the Croatian police about the NetWire takedown is here.
Update, Oct. 26, 11:11 a.m. ET: Mario Zanko responded to requests for comment. Zanko said while he was indeed detained for three months by Croatian authorities in connection with the Netwire investigation, he has not yet been charged with a crime.
“I have not been charged with any crime, be it in Croatia, the United States, the UK, or the EU,” Zanko said. “The detention was a distressing experience, being separated from our family, we have 2 minors.”




I always enjoy that some of these high-tech bandits get undone by careless mistakes and good old fashioned legwork that exposes them.
It exposed some random dude who might have no clue about all that. Especially if the creators of that trojan chose him as patient zero and used their horse to it’s full potential.
“Nobody can prove aliens don’t exist.”
It’s != its. BK’s expose is not “enough” by itself to convict someone in a court of law – but this isn’t a court. Actual law enforcement agencies in multiple countries that shut down and physically confiscated the servers in a coordinated action to shut down this malware service have the evidence that they need. BK wrote about some interesting details that seem to point to the individual behind this. Can you debunk any of them in any capacity? Any to add?
There’s a sizeable difference between (actually) reading carefully and finding such interesting and compounding details versus just having “blanket doubts” of everything and without any concrete reason or rationale suggesting ALL these various “coincidences,” breadcrumbs, (photos!) are all mistakenly pointing at a completely innocent party (who just happens to not bother asserting that innocence when asked several times for comment.) You’d like further confirmation? Then wait for it. Authorities likely will announce his identity in the coming days, though if you’d like to “believe” they’ve all made a massive oversight in this investigation spanning years and have the wrong guy, you’re not bound by the evidence they present either. If BK turns out to be mistaken and it’s a deeper conspiracy framing Zanko as an unwitting patsy, BK will no doubt the first to admit and explore any evidence of that in detail as well.
“no doubt _be_ the first…”
He’s probably lived comfortably for 11 years. From what I’ve learned over the years, major malware purveyors outside of Russia, PRC, and few other locales are eventually located, put out of business, and/or arrested–no matter how much effort they put into being incognito. Especially if has put aside some money for later in life, I”d say he’s don well for himself–ethics aside, of course.
That’s a lot of breadcrumbs. God I love these breakdowns. Thanks BK.
Hahaha noob… so many mistakes, this guy was just a sales good apparently, he seems to dumb to create a RAT.
It seems for the looks of it, vaporware all over it
Me and my son are being hacked,they infiltrated are emails,trying to take are crypto and nfts, they keyloged us and mirrored are phones and other devices. We need a little help, thanks
I’ll help you:
Go to the police and report it & stop risking your money in NFTs which are literally worthless in real life
Exactly!
Take your computer to someone who knows what they’re doing. In the mean time use another device to change your passwords and enable 2factor.
“Take your computer to someone who knows what they’re doing.”
What to look for in terms of certification? Avg User has zero idea.
Is that an ubiquitous available service? And how do they find that?
Which reputation ranks are worthwhile, which are spamfarm BS?
Open Yelpy pages and look for what? Virus repair? Anti-hacking?
The one with a slick full page paid ad leveraging marketing bias?
How many will give time of day to a non-corporate client 1-off?
How many of those aren’t backed up for weeks+ and can ASAP?
Add language barrier or vision/audio impairment, advanced age,
total unfamiliarity with basic terms, no idea what’s “wrong” really.
“The password didn’t work. The bank says send gift card #’s,
then they can unlock my data for a security fee. What do I do?”
Average User has a steep learning curve just to get to help.
Your comment is very insightful.
There’s been little effective effort by government and law enforcement to help protect the vulnerable from cyber threats Some LE organizations are helpful after a successful attack, but there’s little preventive help available. Some of the ISPs and social media companies have started to put in some limited efforts to filter out the most egregious attacks and to make some high-level soft-pedaled warnings to end users, but it looks like they want to figure out how to monetize this before doing anything substantial.
The current trickle of cyber and telephone scam attacks are not being effectively countered and vulnerable people are being hurt. That trickle is going to turn into a flood as more criminals realize that these scams WORK. And NOBODY has a plan!
https://www.linkedin.com/in/mario-zanko-8a3371207/ – its this guy obviously, also have a twitter – there’s a strict connection to that profile in term of GODBEX SOLUTIONS LTD https://www.linkedin.com/in/tamara-beljak/?originalSubdomain=hr
They both worked in same “companies”.
Such cases should be dealt with very strictly and closely.
Always love following your work, keep it up Brian!
I’ve known about the netwire RAT for quite some time, puts a smile on my face knowing the creator will see justice. What bugs me is so many of these MAAS platforms portray themselves as legitimate… yet all keep getting raided. Luminosity, Orcus, imminent monitor and now netwire. What’s their deal? Anyone with half a brain can see they’re malicious so why are they so obsessed with their image?
Only malicious if sold to the public it seems. If your company sells to the police or governments, then the same software and services are suddenly legit.
So the crime commited was that the software itself was automatically exfiltrating username and passwords as a keylogger? Otherwise it’s just a remote access tool?
Remote access tools ask users for consent, they also make it clear that it’s running and give users an easy way to close the connection. Remote access tools do not quietly install with persistence, hide from the user, include password recovery or keylogging. That’s what Remote access TROJANS do. If you think otherwise you’re a
Exactly. And legit remote access tools don’t typically recommend or advertise services to make your remote control executable undetectable by antivirus products, or bind them with desirable/benign programs, or provide support/instructions on how to evade security tools.
> or bind them with desirable/benign programs
TeamViewer wants a word with you(to sell you a subscription, obviously)
Hey Brian, what about REMCOS? This italian punk basically has been selling a RAT and other malware for years.
Do you even know the difference between malware and pentesting tools?
lol… hella lot of noobs around.
Hello,
Where are my credits, my name is Arena and I helped with AI live worm. I my AI helped with live tracking over youtube and gmail service
This hacked have couple billion dollars on his bank account
Thanks FBI
r/masterhacker
Hello,
Where are my credits, my name is Arena and I helped with AI type live worm. I my AI helped with live tracking over youtube and gmail services
To FBI: This hacked have couple billion dollars on his bank accounts
Maybe I should just create another bus virus and stole his money? What you think guys
Thanks FBI
Not true. Croatian media did release both the name and the picture of Mario Zanko in relation to this.
https://www.24sata.hr/news/uhiceni-haker-mario-rodom-je-iz-sinja-pao-je-u-zapresicu-a-na-racunu-su-mu-nasli-milijun-eura-896644
It’s great to see law enforcement agencies taking action against cybercrime and shutting down websites that sell malware like NetWire. The use of remote access trojans poses a significant threat to individuals and organizations alike, and it’s crucial to hold those responsible accountable for their actions. It’s also essential to take steps to protect your systems from malware by keeping your software up-to-date, being cautious of suspicious emails, and using reputable antivirus software.