You’ve probably never heard of “16Shop,” but there’s a good chance someone using it has tried to phish you.
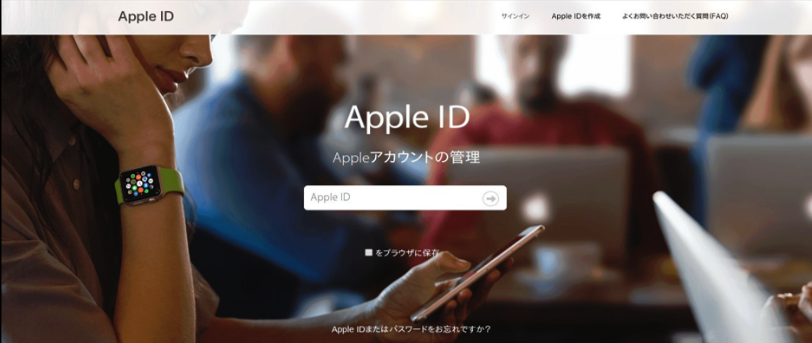
A 16Shop phishing page spoofing Apple and targeting Japanese users. Image: Akamai.com.
The international police organization INTERPOL said last week it had shuttered the notorious 16Shop, a popular phishing-as-a-service platform launched in 2017 that made it simple for even complete novices to conduct complex and convincing phishing scams. INTERPOL said authorities in Indonesia arrested the 21-year-old proprietor and one of his alleged facilitators, and that a third suspect was apprehended in Japan.
The INTERPOL statement says the platform sold hacking tools to compromise more than 70,000 users in 43 countries. Given how long 16Shop has been around and how many paying customers it enjoyed over the years, that number is almost certainly highly conservative.
Also, the sale of “hacking tools” doesn’t quite capture what 16Shop was all about: It was a fully automated phishing platform that gave its thousands of customers a series of brand-specific phishing kits to use, and provided the domain names needed to host the phishing pages and receive any stolen credentials.
Security experts investigating 16Shop found the service used an application programming interface (API) to manage its users, an innovation that allowed its proprietors to shut off access to customers who failed to pay a monthly fee, or for those attempting to copy or pirate the phishing kit.
16Shop also localized phishing pages in multiple languages, and the service would display relevant phishing content depending on the victim’s geolocation.

Various 16Shop lures for Apple users in different languages. Image: Akamai.
For example, in 2019 McAfee found that for targets in Japan, the 16Shop kit would also collect Web ID and Card Password, while US victims will be asked for their Social Security Number.
“Depending on location, 16Shop will also collect ID numbers (including Civil ID, National ID, and Citizen ID), passport numbers, social insurance numbers, sort codes, and credit limits,” McAfee wrote.
In addition, 16Shop employed various tricks to help its users’ phishing pages stay off the radar of security firms, including a local “blacklist” of Internet addresses tied to security companies, and a feature that allowed users to block entire Internet address ranges from accessing phishing pages.
The INTERPOL announcement does not name any of the suspects arrested in connection with the 16Shop investigation. However, a number of security firms — including Akamai, McAfee and ZeroFox, previously connected the service to a young Indonesian man named Riswanda Noor Saputra, who sold 16Shop under the hacker handle “Devilscream.”
According to the Indonesian security blog Cyberthreat.id, Saputra admitted being the administrator of 16Shop, but told the publication he handed the project off to others by early 2020.
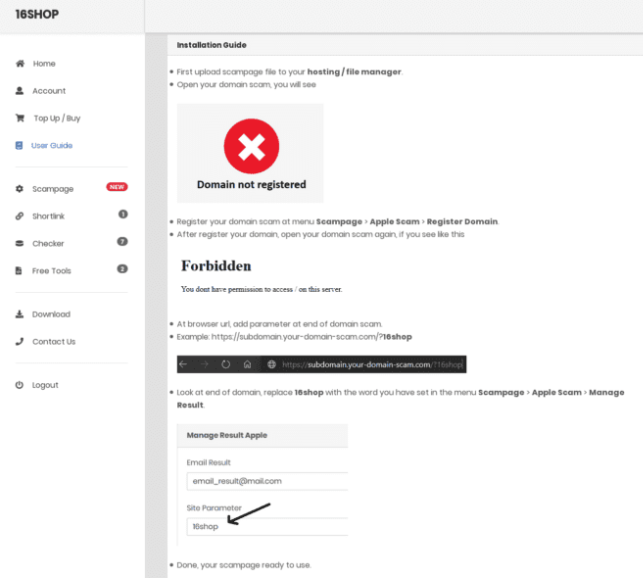
16Shop documentation instructing operators on how to deploy the kit. Image: ZeroFox.
Nevertheless, Cyberthreat reported that Devilscream was arrested by Indonesian police in late 2021 as part of a collaboration between INTERPOL and the U.S. Federal Bureau of Investigation (FBI). Still, researchers who tracked 16Shop since its inception say Devilscream was not the original proprietor of the phishing platform, and he may not be the last.
RIZKY BUSINESS
It is not uncommon for cybercriminals to accidentally infect their own machines with password-stealing malware, and that is exactly what seems to have happened with one of the more recent administrators of 16Shop.
Constella Intelligence, a data breach and threat actor research platform, now allows users to cross-reference popular cybercrime websites and denizens of these forums with inadvertent malware infections by information-stealing trojans. A search in Constella on 16Shop’s domain name shows that in mid-2022, a key administrator of the phishing service infected their Microsoft Windows desktop computer with the Redline information stealer trojan — apparently by downloading a cracked (and secretly backdoored) copy of Adobe Photoshop.
Redline infections steal gobs of data from the victim machine, including a list of recent downloads, stored passwords and authentication cookies, as well as browser bookmarks and auto-fill data. Those records indicate the 16Shop admin used the nicknames “Rudi” and “Rizki/Rizky,” and maintained several Facebook profiles under these monikers.
It appears this user’s full name (or at least part of it) is Rizky Mauluna Sidik, and they are from Bandung in West Java, Indonesia. One of this user’s Facebook pages says Rizky is the chief executive officer and founder of an entity called BandungXploiter, whose Facebook page indicates it is a group focused mainly on hacking and defacing websites.
A LinkedIn profile for Rizky says he is a backend Web developer in Bandung who earned a bachelor’s degree in information technology in 2020. Mr. Rizky did not respond to requests for comment.





I tend to worry mostly about phishing attacks by text messages these days. The article didn’t say whether 16Shop kits were limited to e-mail and web pages. With the difficulty of vetting scams using text messages, wouldn’t that be a likely profitable approach for 16Shop as well?
It seems that many of the Two Factor Authentication methods involve sending a text message to your cell phone containing a PIN. But then an attacker tells a victim that they just sent them a PIN to their cell phone and the victim must read it back to confirm the victim’s identity. He reads it back and there goes his bank account.
Or attackers can swap SIM cards in some cases and take over the victim’s calls and text messages so that they can respond to incoming PIN numbers and verify themselves as the victim.
One thing I’m curious about is whether something like Google Voice might be better to use as a two factor authentication number. No SIM card, so no SIM card swap. If you use a Google Voice number for text messages, how easy would it be for an attacker to get Google to hand over the number to them? Is it more difficult than swapping SIM cards?
And whether or not you have two factor authentication via text messages on a cell phone or an on-line phone, the idea that the text messages are becoming so commonly used to control access to secure sites is scary.
One thing in my favor is that I don’t pay much attention to telephones. My primary use for it is for emergencies. On the other hand, I depend heavily on e-mail, but at least we can dig through the headers on an e-mail to get some idea about whether the e-mail seems legitimate.
And the use of +aliases to help in filtering the e-mails. For some of my more sensitive e-mail traffic such as for banks and credit card companies, I have set the sieve filter so that they look at both the sender address and the exact destination aliased address, to tag them appropriately. If only one of the sender or the destination address matches, then it still adds the tag, but it also adds a WARNING tag to let me know that it is more likely a scam.
I have seen posts on Reddit where people use Google voice to get around simjacking. I have no first hand knowledge of this.
I use a secure ID air gapped token generator where money is involved.
NIST has a funny way of saying SMS is not allowed. They call it restricted. Google SP800-63.
I do wonder with the expanding facility of AI-generated voice matching how easy it would be to spoof a voice.
Dear Brian, Thank you for keeping up the good fight. The information you provide is so useful. It looks like you will never run out of topics, since the internet will never run out of crimes.
You wrote: “It is not uncommon for cybercriminals to accidentally infect their own machines with password-stealing malware […]” Hilarious! Poetic justice…
Brian, your “continue reading” link is not at the bottom of this story on the main page. I knew to come here, but others won’t.
I do wonder with the expanding facility of AI-generated voice matching how easy it would be to spoof a voice.
i’m not a very highly evolved primate, so i don’t use a mobile phone [capital letters], i.e., all codes are received through google voicemail. but many companies won’t deal with users who only have gmail addresses, so we unhighly evolved ones get left out in the cold with the monkeys.
It appears that American Express may have decided that SMS messages are not a secure idea. I received an e-mail from American Express tonight that said they will discontinue sending most notifications by SMS toward the end of September. The notification messages will be delivered by e-mail or by their own app.
I have heard that scammers frequently send out SMS messages that purport to be from major credit cards in order to get their target to fall for their scams. So this sounds like a really good move.
And the e-mail from American Express was sent to a secret e-mail address of mine that only they have (first thing I checked). So it is most likely actually from American Express.
Since e-mail is so easily taken over (unless using MFA for it too), I prefer an App from the Financial Institution or using an authenticator App over e-mail or SMS.
I prefer e-mail. I’m not someone who lives by the cell phone. There’s nothing I like better than to put my cell phone on the charger and leave it there a few days.
Using an e-mail address for correspondence with American Express that nobody else in the world has seen works quite well. Any legitimate e-mail from American Express to me should have that secret e-mail address. If it doesn’t, then it is very suspicious. Even if it does, if it says to call American Express, I’m calling the number on the card, not the one in the e-mail.
For what it’s worth, my main e-mail is through my ProtonMail account. but I do have a number of other e-mail addresses elsewhere, often for testing purposes.
For the purpose of discussion, assume that one address is intuitively.obvious.to.the.most.casual.observer@protonmail.ch for use with American Express. (Note: I have no idea if anyone actually has that address.)
Then, in the Sieve Filter:
if allof
(
envelope :domain :comparator “i;unicode-casemap” :is
“From” [“americanexpress.com”, “*.americanexpress.com”,
“aexp.com”, “*.aexp.com”],
envelope :all :is “To” “intuitively.obvious.to.the.most.casual.observer@protonmail.ch”
)
{
addflag “\\Flagged” ;
fileinto “_Banking” ;
fileinto “Amex” ;
stop ;
}
if anyof
(
envelope :domain :comparator “i;unicode-casemap” :is
[“To”, “”Cc”, “Bcc”, “From] [“americanexpress.com”, “*.americanexpress.com”,
“aexp.com”, “*.aexp.com”],
envelope :all :is [“To”, “Cc”, “Bcc”, “From”] “intuitively.obvious.to.the.most.casual.observer@protonmail.ch”
{
addflag “\\Flagged” ;
fileinto “_Banking” ;
fileinto “Amex” ;
fileinto “WARNING”;
stop ;
}
Thus, if the e-mail domains shows it to be from American Express and the recipient address is the super duper secret address that shall not be whispered, then it is put into the _Banking folder and tagged “Amex” and starred to indicate high priority. On the other hand, if only one of the conditions are met, it is still put into the _Banking folder, tagged “Amex” and starred to indicate a high priority, but it is also marked with an unmistakable “WARNING” tag to warn me that something is wrong.
It is disappointing to me that American Express fails to understand ‘+’ aliases. Something like intuitively.obvious.to.the.most.casual.observer+american_express_member_since_1971@example.com would have been more satisfying.
This has the makings for a great module at the kernel level…
Why is ReadersMagnet not a scam? Because as a publishing service provider, ReadersMagnet provides quality service packages to its client-authors. These packages are designed not only to meet the standard requirement for book publication but also sensitive to the financial capabilities of most aspiring authors. It has consistently delivered top of the line publishing services and the fulfillment of over 100 published titles is enough proof that ReadersMagnet is not a scam…
It’s really shocking to know the above stated facts, never thought of it. phishing is unpredictable.