One of the oldest malware tricks in the book — hacked websites claiming visitors need to update their Web browser before they can view any content — has roared back to life in the past few months. New research shows the attackers behind one such scheme have developed an ingenious way of keeping their malware from being taken down by security experts or law enforcement: By hosting the malicious files on a decentralized, anonymous cryptocurrency blockchain.
In August 2023, security researcher Randy McEoin blogged about a scam he dubbed ClearFake, which uses hacked WordPress sites to serve visitors with a page that claims you need to update your browser before you can view the content.
The fake browser alerts are specific to the browser you’re using, so if you’re surfing the Web with Chrome, for example, you’ll get a Chrome update prompt. Those who are fooled into clicking the update button will have a malicious file dropped on their system that tries to install an information stealing trojan.
Earlier this month, researchers at the Tel Aviv-based security firm Guardio said they tracked an updated version of the ClearFake scam that included an important evolution. Previously, the group had stored its malicious update files on Cloudflare, Guardio said.
But when Cloudflare blocked those accounts the attackers began storing their malicious files as cryptocurrency transactions in the Binance Smart Chain (BSC), a technology designed to run decentralized apps and “smart contracts,” or coded agreements that execute actions automatically when certain conditions are met.
Nati Tal, head of security at Guardio Labs, the research unit at Guardio, said the malicious scripts stitched into hacked WordPress sites will create a new smart contract on the BSC Blockchain, starting with a unique, attacker-controlled blockchain address and a set of instructions that defines the contract’s functions and structure. When that contract is queried by a compromised website, it will return an obfuscated and malicious payload.
“These contracts offer innovative ways to build applications and processes,” Tal wrote along with his Guardio colleague Oleg Zaytsev. “Due to the publicly accessible and unchangeable nature of the blockchain, code can be hosted ‘on-chain’ without the ability for a takedown.”
Tal said hosting malicious files on the Binance Smart Chain is ideal for attackers because retrieving the malicious contract is a cost-free operation that was originally designed for the purpose of debugging contract execution issues without any real-world impact.
“So you get a free, untracked, and robust way to get your data (the malicious payload) without leaving traces,” Tal said.
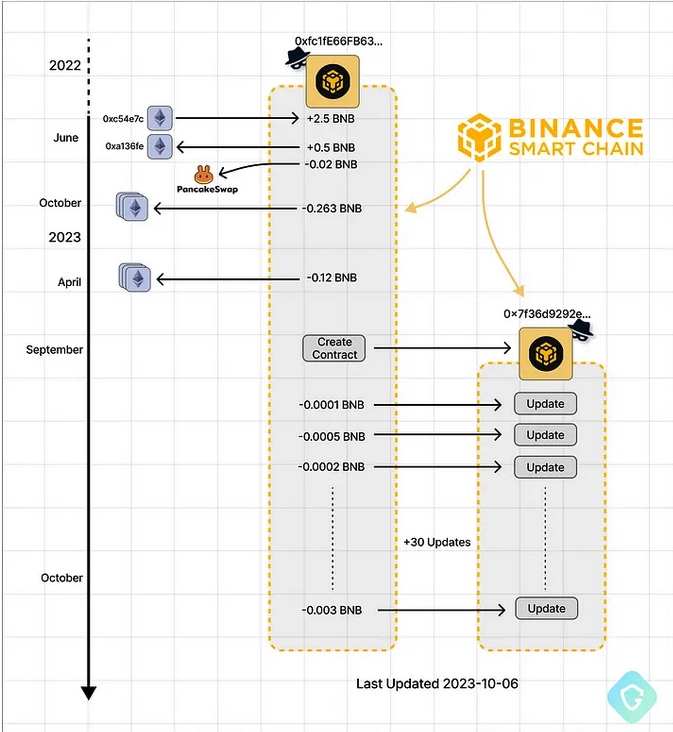
Attacker-controlled BSC addresses — from funding, contract creation, and ongoing code updates. Image: Guardio
In response to questions from KrebsOnSecurity, the BNB Smart Chain (BSC) said its team is aware of the malware abusing its blockchain, and is actively addressing the issue. The company said all addresses associated with the spread of the malware have been blacklisted, and that its technicians had developed a model to detect future smart contracts that use similar methods to host malicious scripts.
“This model is designed to proactively identify and mitigate potential threats before they can cause harm,” BNB Smart Chain wrote. “The team is committed to ongoing monitoring of addresses that are involved in spreading malware scripts on the BSC. To enhance their efforts, the tech team is working on linking identified addresses that spread malicious scripts to centralized KYC [Know Your Customer] information, when possible.”
Guardio says the crooks behind the BSC malware scheme are using the same malicious code as the attackers that McEoin wrote about in August, and are likely the same group. But a report published today by email security firm Proofpoint says the company is currently tracking at least four distinct threat actor groups that use fake browser updates to distribute malware.
Proofpoint notes that the core group behind the fake browser update scheme has been using this technique to spread malware for the past five years, primarily because the approach still works well.
“Fake browser update lures are effective because threat actors are using an end-user’s security training against them,” Proofpoint’s Dusty Miller wrote. “In security awareness training, users are told to only accept updates or click on links from known and trusted sites, or individuals, and to verify sites are legitimate. The fake browser updates abuse this training because they compromise trusted sites and use JavaScript requests to quietly make checks in the background and overwrite the existing website with a browser update lure. To an end user, it still appears to be the same website they were intending to visit and is now asking them to update their browser.”
More than a decade ago, this site published Krebs’s Three Rules for Online Safety, of which Rule #1 was, “If you didn’t go looking for it, don’t install it.” It’s nice to know that this technology-agnostic approach to online safety remains just as relevant today.




We published an analysis of ClearFake this week: https://blog.sekoia.io/clearfake-a-newcomer-to-the-fake-updates-threats-landscape/
I’m sorry people still fall for this.
I think Netscape Navigator 1.1 was the last time I *really* had to update my browser to view a site.
Good times.
Brian,
I didn’t recall reading the story 12 years ago (yikes, it has been a while), so I clicked to read it. You haven’t aged a bit based on the photo at the top. 🙂
There are 56 comments on it. And, yes, it is still relevant even today. I am glad I am subscriber. Thank you.
Thanks for sticking with me this long, Stephen!
Wait what? How does it help them to store it on a block chain, when they still have to use a centralized gateway to get the data back from the chain? It doesn’t matter what’s on the chain if the browser can’t retrieve it.
It’s not like the browser they’re trying to attack can natively talk to, or even find, the actual P2P crypto nodes. The browser can’t send a request “to the chain”. It has to send it to the gateway, whose URL is hardwired into the first stage. The gateway can be made to filter out calls to that specific contract, at which point they have to change gateways just like they’d have to change any other hosts. And there are fewer gateways onto any given block chain than there are random places you could stick data on the plain old Internet.
I don’t understand how this is “bulletproof”, other than maybe taking advantage of Binance not being set up to block specific contracts at its gateway.
“the malicious scripts stitched into hacked WordPress sites”
Vulnerable WordPress sites? Pretty much an inexhaustible resource.
There are more details here: https://labs.guard.io/etherhiding-hiding-web2-malicious-code-in-web3-smart-contracts-65ea78efad16
I don’t understand it myself but I don’t get blockchains. Maybe that has the info you’re looking for.
RB
I read it before ever posting anything. It makes no sense. Neither does this article’s claim that every hacked WordPress site creates its own smart contract with its own address; that would be way too expensive, among other things.
You’re right and the link provided by Reinis actually explains the confusion.
There it says “It creates a new contract instance […]”, but looking at the code snippet clearly shows that it’s just instantiating a new `ethers.Contract` pointing to an existing address.
So it’s actually just querying an already deployed smart contract.
To me I don’t get how this is much more different than a regular CDN which would not want to block anything. Like Cloudflare did remove the content, but what about a smaller one serving both legit content and more questionable one?
Also, the good thing with the BSC is that they did trade a lot of decentralization to get way more speed and lower fees, so there is actually a chance they could block interacting with some smart contract addresses. Though it would be an issue if the attackers moved to a more decentralized chain.
“First, they are not centralized like the addresses used by banks. Secondly, every possible blockchain address already exists. It existed the moment the blockchain was created, because blockchain addresses are the result of mathematical operations.”
unblock . net/what-is-a-blockchain-address/
They’re procedurally generated. It costs just about nothing.
Instantiating a contract on a chain costs you a gas fee, even if the code for the contract is already on the chain. Until you do that, the contract has no address and is not usable. It’s not about the address existing in some liminal mathematical world.
Sure, I didn’t/don’t know how well you understand the subject.
Actual fee is pretty negligible given the targeted matter.
The point is it’s obfuscated, irrevocable, accessible in situ.
They have the minimal budget required to pay the fees, day 1.
They have bitcoin. The fee is negligible.
From what I understand, you’re absolutely right. The last line in the article sent from “Reinis” (which only appears on mobile, strange), says exactly this:
why won’t Binance just disable any query to already tagged as
“Malicious” addresses? Or at least let’s disable this eth_call
debug method for unvalidated contracts?
So much for “decentralization” in blockchains.
“How does it help them to store it on a block chain, when they still have to use a centralized gateway to get the data back from the chain?”
Because it’s code-obfuscated, irrevocable, and accessible.
“It doesn’t matter what’s on the chain if the browser can’t retrieve it.”
-This seems to be the core misunderstanding.
“How does it help them to store it on a block chain, when they still have to use a centralized gateway to get the data back from the chain?”
I think the main point of them taking this approach is that instead of the malware coming from randommaliciouswebsite.hack, the request is going to normallygoodguyblockchain.com and won’t be blocked by blacklists. or other URL/IP based defenses.
This is one of the many reasons you should automate your WordPress updates *and* regularly verify that everything is properly updated and none of your plugins has a known security issue. It requires some effort, time, and knowledge.
WordPress is a highly targeted platform. There are alternatives.
Wildly off topic but Finnish authorities have their hands on Julius Kivimäki and prosecutors are asking for a 7 year sentence with the trial starting November 13.
I feel for this. Dagnabbit! Is there a place I should go to see how to fix it?
How long can this scam go undetected by the website owners? If my site had this issue I’d take it down and investigate for backdoors and malicious scripts. My assumption is the threat actors would be targeting many websites with common vulnerabilities.
Well, a lot of these sites are legit getting decent traffic every day. I asked the researchers at Guardio and they said they didn’t see any signs attackers were somehow driving traffic to the hacked sites. They said the sites were getting a fair amount of organic traffic each day because they’d been around for a while and had decent search rankings for certain terms.
So how long does a site like that need to be compromised to snare a large number of victims? Probably not long. And notifying the affected admin and getting them the help they need to clean things up properly and prevent a recurrence of the malware takes time. Sometimes hours, sometimes days, sometimes weeks, sometimes never.
Almost forever is definitely an outcome. Many sites have a content owner who only needs to make seasonal updates and an on call volunteer tech admin who checks in as requested.
Sadly, I’m in that category for one too many sites (1). I need to check it this month…
many malicious wp plugins go a long way to stay undetected from the website owner, which should be logged into the website’s wp admin console already and easy to identify
On Ubuntu, browser updates are integrated into the OS. It sounds like a Windows problem to me.
OT: We’re missing your posts / insight on bluesky.
DM via Mail for a an unconditional invite.
Seb
Pretty sophisticated… granted I had to read the post on https://labs.guard.io/etherhiding-hiding-web2-malicious-code-in-web3-smart-contracts-65ea78efad16
I didn’t realize blockchain can be used in this manner.
Ian