A cybercrook who has been setting up websites that mimic the self-destructing message service privnote.com accidentally exposed the breadth of their operations recently when they threatened to sue a software company. The disclosure revealed a profitable network of phishing sites that behave and look like the real Privnote, except that any messages containing cryptocurrency addresses will be automatically altered to include a different payment address controlled by the scammers.
The real Privnote, at privnote.com.
Launched in 2008, privnote.com employs technology that encrypts each message so that even Privnote itself cannot read its contents. And it doesn’t send or receive messages. Creating a message merely generates a link. When that link is clicked or visited, the service warns that the message will be gone forever after it is read.
Privnote’s ease-of-use and popularity among cryptocurrency enthusiasts has made it a perennial target of phishers, who erect Privnote clones that function more or less as advertised but also quietly inject their own cryptocurrency payment addresses when a note is created that contains crypto wallets.
Last month, a new user on GitHub named fory66399 lodged a complaint on the “issues” page for MetaMask, a software cryptocurrency wallet used to interact with the Ethereum blockchain. Fory66399 insisted that their website — privnote[.]co — was being wrongly flagged by MetaMask’s “eth-phishing-detect” list as malicious.
“We filed a lawsuit with a lawyer for dishonestly adding a site to the block list, damaging reputation, as well as ignoring the moderation department and ignoring answers!” fory66399 threatened. “Provide evidence or I will demand compensation!”
MetaMask’s lead product manager Taylor Monahan replied by posting several screenshots of privnote[.]co showing the site did indeed swap out any cryptocurrency addresses.
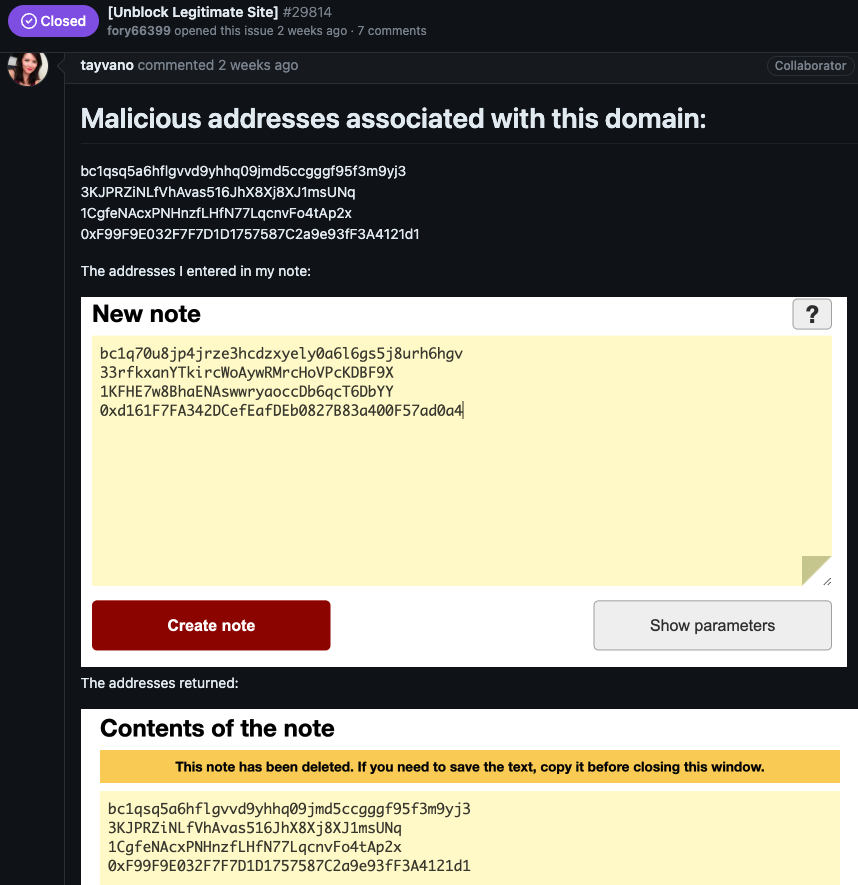
After being told where they could send a copy of their lawsuit, Fory66399 appeared to become flustered, and proceeded to mention a number of other interesting domain names:
You sent me screenshots from some other site! It’s red!!!!
The tornote.io website has a different color altogether
The privatenote,io website also has a different color! What’s wrong?????
A search at DomainTools.com for privatenote[.]io shows it has been registered to two names over as many years, including Andrey Sokol from Moscow and Alexandr Ermakov from Kiev. There is no indication these are the real names of the phishers, but the names are useful in pointing to other sites targeting Privnote since 2020.
DomainTools says other domains registered to Alexandr Ermakov include pirvnota[.]com, privatemessage[.]net, privatenote[.]io, and tornote[.]io.
A screenshot of the phishing domain privatemessage dot net.
The registration records for pirvnota[.]com at one point were updated from Andrey Sokol to “BPW” as the registrant organization, and “Tambov district” in the registrant state/province field. Searching DomainTools for domains that include both of these terms reveals pirwnote[.]com.
Other Privnote phishing domains that also phoned home to the same Internet address as pirwnote[.]com include privnode[.]com, privnate[.]com, and prevnóte[.]com. Pirwnote[.]com is currently selling security cameras made by the Chinese manufacturer Hikvision, via an Internet address based in Hong Kong.
It appears someone has gone to great lengths to make tornote[.]io seem like a legitimate website. For example, this account at Medium has authored more than a dozen blog posts in the past year singing the praises of Tornote as a secure, self-destructing messaging service. However, testing shows tornote[.]io will also replace any cryptocurrency addresses in messages with their own payment address.
These malicious note sites attract visitors by gaming search engine results to make the phishing domains appear prominently in search results for “privnote.” A search in Google for “privnote” currently returns tornote[.]io as the fifth result. Like other phishing sites tied to this network, Tornote will use the same cryptocurrency addresses for roughly 5 days, and then rotate in new payment addresses.
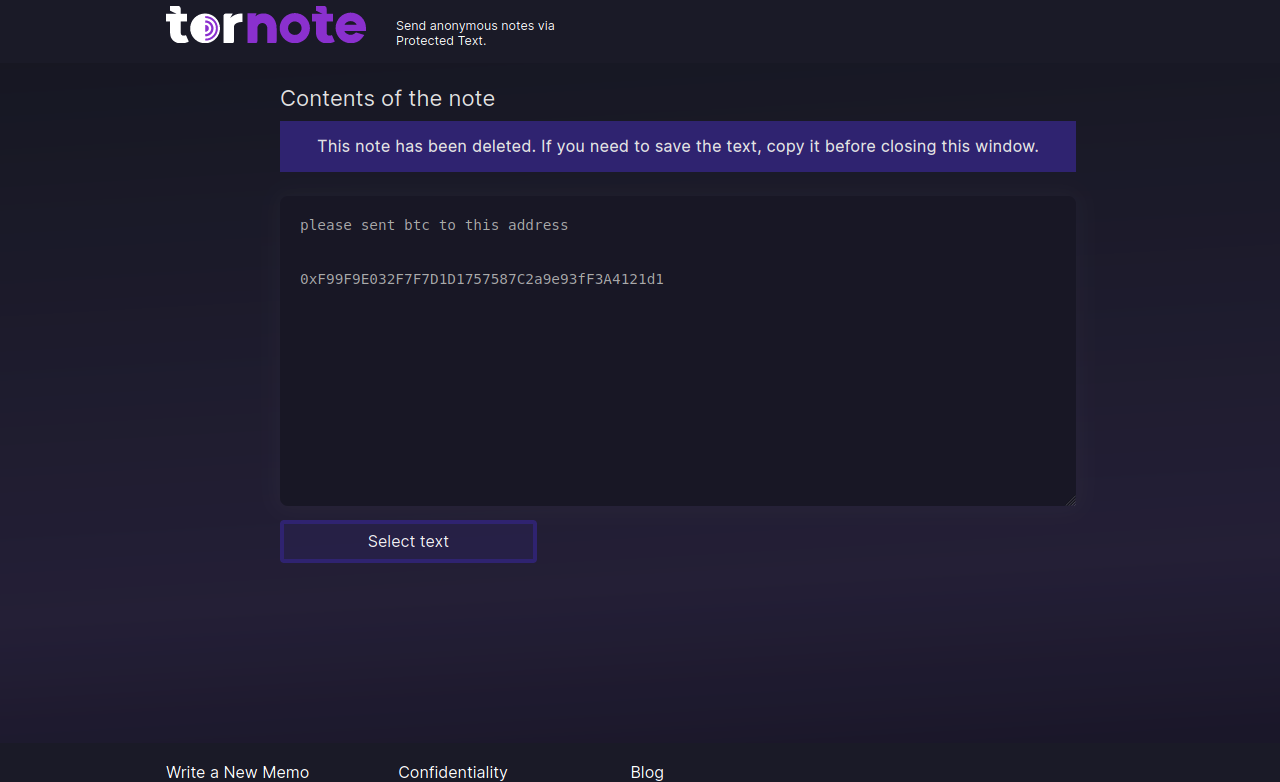
Tornote changed the cryptocurrency address entered into a test note to this address controlled by the phishers.
Throughout 2023, Tornote was hosted with the Russian provider DDoS-Guard, at the Internet address 186.2.163[.]216. A review of the passive DNS records tied to this address shows that apart from subdomains dedicated to tornote[.]io, the main other domain at this address was hkleaks[.]ml.
In August 2019, a slew of websites and social media channels dubbed “HKLEAKS” began doxing the identities and personal information of pro-democracy activists in Hong Kong. According to a report (PDF) from Citizen Lab, hkleaks[.]ml was the second domain that appeared as the perpetrators began to expand the list of those doxed.
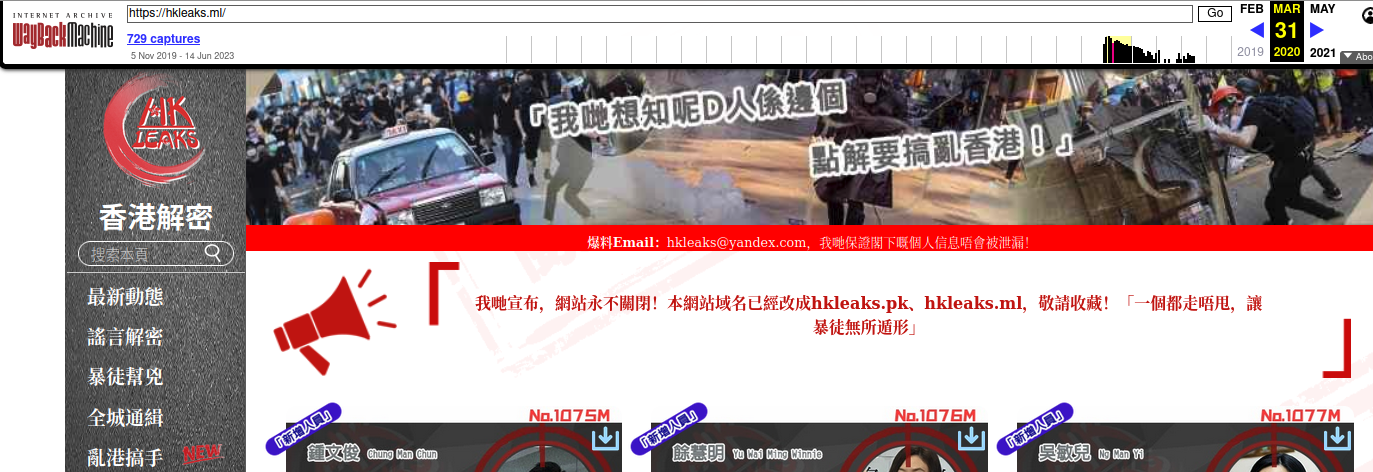
HKleaks, as indexed by The Wayback Machine.
DomainTools shows there are more than 1,000 other domains whose registration records include the organization name “BPW” and “Tambov District” as the location. Virtually all of those domains were registered through one of two registrars — Hong Kong-based Nicenic and Singapore-based WebCC — and almost all appear to be phishing or pill-spam related.
Among those is rustraitor[.]info, a website erected after Russia invaded Ukraine in early 2022 that doxed Russians perceived to have helped the Ukrainian cause.
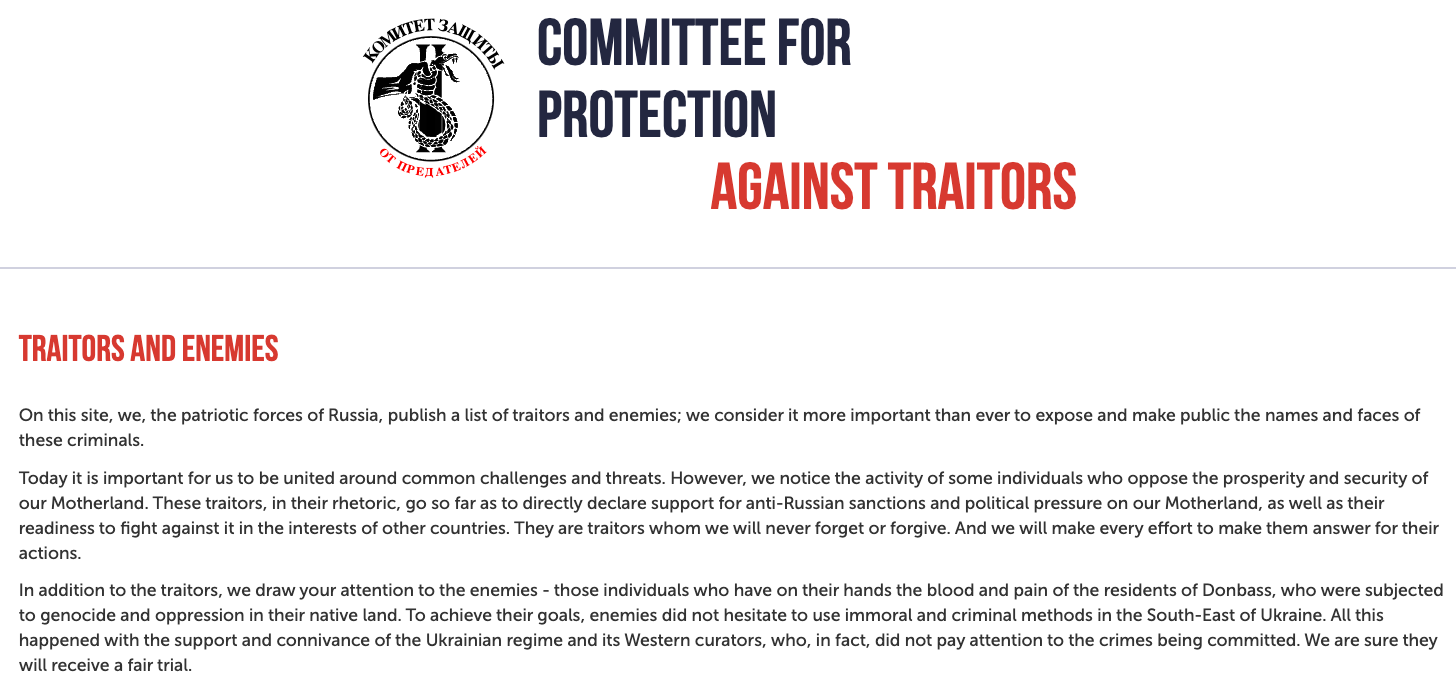
An archive.org copy of Rustraitor.
In keeping with the overall theme, these phishing domains appear focused on stealing usernames and passwords to some of the cybercrime underground’s busiest shops, including Brian’s Club. What do all the phished sites have in common? They all accept payment via virtual currencies.
It appears MetaMask’s Monahan made the correct decision in forcing these phishers to tip their hand: Among the websites at that DDoS-Guard address are multiple MetaMask phishing domains, including metarrnask[.]com, meternask[.]com, and rnetamask[.]com.
How profitable are these private note phishing sites? Reviewing the four malicious cryptocurrency payment addresses that the attackers swapped into notes passed through privnote[.]co (as pictured in Monahan’s screenshot above) shows that between March 15 and March 19, 2024, those address raked in and transferred out nearly $18,000 in cryptocurrencies. And that’s just one of their phishing websites.




I’ve been using my self made private note service: https://github.com/yani/safewhisper
I’ve never trusted privnote because of the ads they serve. Injecting a few bad ads that log the data would be too easy.
There are a number of service providers available that will search the Internet for phishing sites and help shut them down. When I worked for a popular online retailer we used a service like this and shut down dozens of phishing sites over the years. It seems to me like Privnote needs to do more to protect their brand and a good first step would be to hire one of these providers.
> the main other domain at this address was
well, ddos-guard works like cloudflare, there’s obviously gonna be multiple unrelated sites on the same ip
Having been a customer of ddos-guard, I can tell you it does not work like Cloudflare. You get root/ access, yes it could be a VPS but the customer ~ owns the IP for the duration of the contract. So if these sites were seen at the same time on the same ddos-guard IP they are likely tied to the same customer — unless the customer was renting out their server to 3rd parties. If they were observed on the IP at different times, all bets are off — it could be different customers.
lol
Why would a Russian website doxing traitors be written in English? That got me curious. Thanks for the translation, Mr. Krebs, LOL!
It’s not. That screenshot is a machine-translated version of the page. The original is in Russian.
Brian,
Thank you for a timely article!
Earlier today, someone had sent me login credentials – username and password- using priwnote.com ( note the “w” not the “v” in the domain name), but I didn’t catch the error in the website name and that it was not the real privnote.com website.
After reading you article just now, I went back and checked the link that had been sent to me and noticed the error and alerted the person who sent it to me.
Your article prevented a potential password compromise.
Thank you !!
TeknSec
Great work as always Brian. Thank you for what you do.