New details are emerging about a breach at National Public Data (NPD), a consumer data broker that recently spilled hundreds of millions of Americans’ Social Security Numbers, addresses, and phone numbers online. KrebsOnSecurity has learned that another NPD data broker which shares access to the same consumer records inadvertently published the passwords to its back-end database in a file that was freely available from its homepage until today.

In April, a cybercriminal named USDoD began selling data stolen from NPD. In July, someone leaked what was taken, including the names, addresses, phone numbers and in some cases email addresses for more than 272 million people (including many who are now deceased).
NPD acknowledged the intrusion on Aug. 12, saying it dates back to a security incident in December 2023. In an interview last week, USDoD blamed the July data leak on another malicious hacker who also had access to the company’s database, which they claimed has been floating around the underground since December 2023.
Following last week’s story on the breadth of the NPD breach, a reader alerted KrebsOnSecurity that a sister NPD property — the background search service recordscheck.net — was hosting an archive that included the usernames and password for the site’s administrator.
A review of that archive, which was available from the Records Check website until just before publication this morning (August 19), shows it includes the source code and plain text usernames and passwords for different components of recordscheck.net, which is visually similar to nationalpublicdata.com and features identical login pages.
The exposed archive, which was named “members.zip,” indicates RecordsCheck users were all initially assigned the same six-character password and instructed to change it, but many did not.
According to the breach tracking service Constella Intelligence, the passwords included in the source code archive are identical to credentials exposed in previous data breaches that involved email accounts belonging to NPD’s founder, an actor and retired sheriff’s deputy from Florida named Salvatore “Sal” Verini.
Reached via email, Mr. Verini said the exposed archive (a .zip file) containing recordscheck.net credentials has been removed from the company’s website, and that the site is slated to cease operations “in the next week or so.”
“Regarding the zip, it has been removed but was an old version of the site with non-working code and passwords,” Verini told KrebsOnSecurity. “Regarding your question, it is an active investigation, in which we cannot comment on at this point. But once we can, we will [be] with you, as we follow your blog. Very informative.”
The leaked recordscheck.net source code indicates the website was created by a web development firm based in Lahore, Pakistan called creationnext.com, which did not return messages seeking comment. CreationNext.com’s homepage features a positive testimonial from Sal Verini.

A testimonial from Sal Verini on the homepage of CreationNext, the Lahore, Pakistan-based web development firm that apparently designed NPD and RecordsCheck.
There are now several websites that have been stood up to help people learn if their SSN and other data was exposed in this breach. One is npdbreach.com, a lookup page erected by Atlas Data Privacy Corp. Another lookup service is available at npd.pentester.com. Both sites show NPD had old and largely inaccurate data on Yours Truly.
The best advice for those concerned about this breach is to freeze one’s credit file at each of the major consumer reporting bureaus. Having a freeze on your files makes it much harder for identity thieves to create new accounts in your name, and it limits who can view your credit information.
A freeze is a good idea because all of the information that ID thieves need to assume your identity is now broadly available from multiple sources, thanks to the multiplicity of data breaches we’ve seen involving SSN data and other key static data points about people.
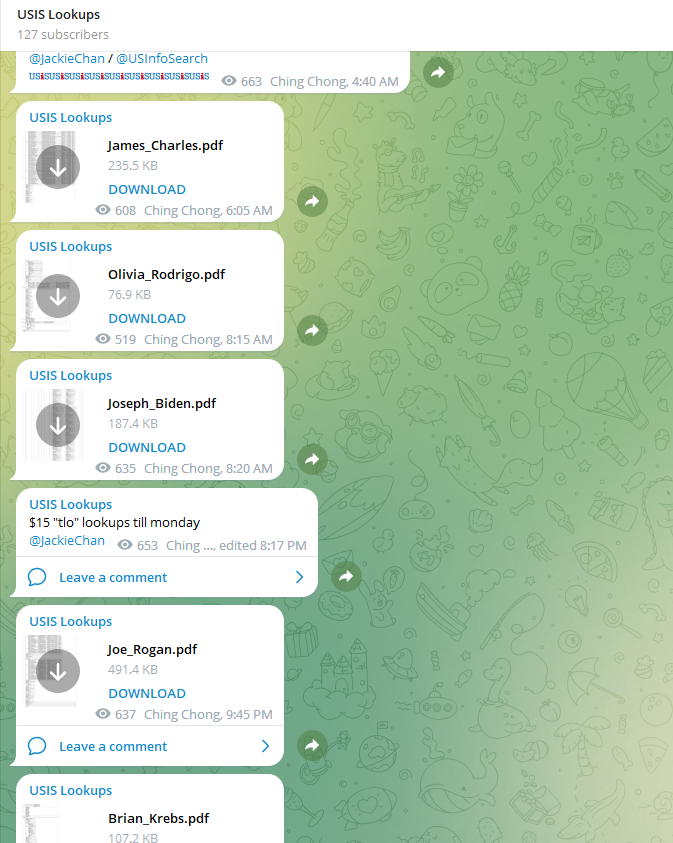
Screenshots of a Telegram-based ID theft service that was selling background reports using hacked law enforcement accounts at USInfoSearch.
There are numerous cybercriminal services that offer detailed background checks on consumers, including full SSNs. These services are powered by compromised accounts at data brokers that cater to private investigators and law enforcement officials, and some are now fully automated via Telegram instant message bots.
In November 2023, KrebsOnSecurity wrote about one such service, which was being powered by hacked accounts at the U.S. consumer data broker USInfoSearch.com. This is notable because the leaked source code indicates Records Check pulled background reports on people by querying NPD’s database and records at USInfoSearch. KrebsOnSecurity sought comment from USInfoSearch and will update this story if they respond.
The point is, if you’re an American who hasn’t frozen their credit files and you haven’t yet experienced some form of new account fraud, the ID thieves probably just haven’t gotten around to you yet.
All Americans are also entitled to obtain a free copy of their credit report weekly from each of the three major credit bureaus. It used to be that consumers were allowed one free report from each of the bureaus annually, but in October 2023 the Federal Trade Commission announced the bureaus had permanently extended a program that lets you check your credit report once a week for free.
If you haven’t done this in a while, now would be an excellent time to order your files. To place a freeze, you’ll need to create an account at each of the three major reporting bureaus, Equifax, Experian and TransUnion. Once you’ve established an account, you should be able to then view and freeze your credit file. If you spot errors, such as random addresses and phone numbers you don’t recognize, do not ignore them. Dispute any inaccuracies you may find.




I thought a person could freeze access to their information through adding a PIN to their social security number directly? Wouldn’t this be a better option?
I think creating a PIN for your social security number with the government may be a better option?
If you think your SSA online account has been compromised, you can request SSA to Block Electronic Access.
“Block Electronic Access
If you know your Social Security information has
been compromised, you can request to Block
Electronic Access. This is done by calling our
National 800 number (Toll Free 1-800-772-1213
or at our TTY number at 1-800-325-0778).
Once requested, any automated telephone and
electronic access to your Social Security record
is blocked. No one, including you, will be able
to see or change your personal information on
the internet or through our automated telephone
service. If you have requested that we block
access to your record and later change your mind,
you can contact us and ask to have the block
removed. You will need to prove your identity
when you call.”
https://www.google.com/url?sa=t&source=web&rct=j&opi=89978449&url=https://www.ssa.gov/pubs/EN-05-10220.pdf&ved=2ahUKEwih1IXy54yIAxXoDTQIHf6KBOwQFnoECBkQAw&usg=AOvVaw1bgOdqzK2y-WecZ8rae_fb
I just checked my status on pentester, along with that of my parents and sibling. None of the birthdates listed for myself are correct, nor are they correct for my parents (my sibling is not so lucky). Not only are the birthdates for myself and my parents wrong, one of the incorrect birthdates attributed to me is also incorrectly attributed to one of my parents.
Anyone have any idea what is going on here? Is pentester returning accurate data to my searches? If the thieves have entirely incorrect birthdates for myself and my parents, I feel a tiny bit of relief. That will at least make it a teensy bit harder to exploit the data. But what are the odds that the original National Public Data records would have such accurate details otherwise, yet be completely off in terms of birthdates?
Any ideas or info appreciated.
who says pentester.com is legit ?
https://www.whois.com/whois/pentester.com
Who says they are not?
Right, until someone can definitively prove that it is not legit, you should assume it is legit and give it all your personal information. – Your dear Nigerian Prince.
What I want to know is why the email address that was exposed in my case is a ProtonMail account that I use exclusively for my bank accounts, and nowhere else? This means NPD acquired my data from one of my banks, who should have my data locked down, but are obviously selling it to 3rd parties. This needs to stop. Our elected officials need to work a lot harder than they presently do.
Exactly THIS! I’ve posted below, that nobody seems to be questioning the LEGALITY of NPD possessing everyone’s SSN, or even HOW they acquired them. Given the fact that people only share their SSN with a small number of entities, suggests to me that NPD has either acquired SSNs from OTHER data breaches, or they have acquired them through other illegal means. Either way, the people who are responsible for acquiring this data, should be prosecuted, and made to give up their sources! But of course, that will never happen.
It could be someone internally in the bank is in on it. You need to contact your bank so they can investigate too (but maybe ask the popo first.)
Good advice, Mike.
Also remember that virtually all banks allow customers to access their accounts via their automated telephone banking system. Don’t confuse this with your mobile banking app. It’s a different system. Access codes for automated telephone banking always default to your SSN. Even if you exclusively bank online, your account is accessible via your bank’s automated telephone banking so change the access code to a self selected number. (Note: Some banks require you to speak to an agent to set it up. With other banks, it’s all automated.) If yours is a joint account, make sure to set a unique access code for each account holder. If you bank at multiple banks, use a different code at each bank just as you would use a different password for online accounts. What you can do via automated telephone banking varies by bank but, at a minimum, all banks will provide account balances and details of all recent transactions. Equipped with that information, a person might be able to call your bank and impersonate you since banks often pick a random transaction from your account and use that as an additional authenticator.
And while you’re at it, call your bank and ask to set a verbal password to be used to authenticate you when you call them. Once this is done, banks will use all the typical authenticators (SSN, DOB, address, etc.) but in addition will ask for your verbal password. This helps reduce the risk of someone calling your bank and impersonating you. Again, use a different verbal password for each account holder and at each bank. Be sure to write these passwords down. If you can’t remember your verbal password, some banks that are scrupulous about security will require you to go to the bank in person to re-authenticate yourself and set a new verbal password.
Thank you, Liz!
I just set up a verbal password with my bank for phone calls from me. They are looking into the automated banking system access codes for me (I have never used it).
I feel like I’m trying to close all the windows and doors to my personal information.
I would like to be able to change my legal name every time my SSN gets exposed.
The most ridiculous part, besides how the data was protected, is how utterly useless our government is when it comes to protecting the people’s data. Nobody will be held accountable for the breach (or collecting the data…), all that will happen will be an email “out of abundance of caution, we are letting you know that you are fucked…” and the idiots continue with their activities.
On the other hand – this company was SELLING that exact data, so technically, the only difference seems to be that this time, they don’t get any money for distributing the data.
One reckless person is responsible for this disaster, and the onus is on _us_ to mop up _his_ mess. We need robust federal protection from these shady creeps.
My mother recently passed away. As I was her financial POA, I had placed a credit freeze with 2 of the 3 bureaus a couple years ago (the 3rd acted like it couldn’t find her/credit history, so it wasn’t successful). For probate I’ll be the appointed next of kind/executor. Wondering if I should do anything else? I’m thinking creating a new SSA (login.gov) is a waste of time, since she won’t receive it anymore. I just wonder how much nefariousness can be done on something who is now deceased?
You should look into SSA, there may be survivor benefits.
Why the heck is everyone concerned with “criminals”? Have you ever heard of an outfit called . . . . Wells Fargo? With all the criminal schemes they have been involved with, surely, the phrase “fox guarding the hen house” fits.
I was commenting on Wells Fargo at a meeting and my client, who was formerly a banker, replied, “If you think Wells Fargo is the only bank pulling all this crap, you are crazy.” There was a local case where a not Wells Fargo banker was the one applying for the fake loans and accounts.
I guess we should think about it the same way my daughter talks to her children. She doesn’t warn them about bad people. She warns them about bad activity, acknowledging that much abuse comes from family members.
I have seen some bank account agreements that state if your credentials were used you acknowledge that you are liable for the loss. They can’t seem to accept that I am just as concerned about the bank’s people as I am with “outside criminals”. I didn’t sign the agreement!
The R E A S O N , why this nation US is 1 step from Un-civil War is because “WE” do not work a lot harder , STOP expecting persons who are suppose to be PUBLIC SERVANTS to do all .
Public Servants now act like they are our masters , BE your own master , take action , now .
I have to say when it comes to internet security , skimmers and much more Brian Krebs is one of the few I would trust for much more than TEN YEARS , not to be confused with the Brian Krebs who worked in US executive branch under trump . Having anything to do with credit companies is the last thing I have ever wanted to do . NOW I must . I truly want to REJECT the thought of speaking my SS number over the phone .
Brian
which way do you feel is safest , in freezing credit reports
By phone , By Mail , By internet ?
it all sucks
Our useless congress can’t even pass any legislation to protect EVERY US Citizen from these endless breaches. In addition, they won’t do anything to supersede Social Security numbers as a primary identifier for US citizens. WTF! Come ON!!!! Enough is enough!
Last week, I got a fraud alert from my bank for suspicious transactions from someone in India using Meta Pay. I don’t use Facebook or Meta Pay. Racking my brain to try and figure out how my bank was compromised and hit a dead end every time. All three credit reports are locked or frozen. But, this news of the massive hack for these two companies is giving me a good assumption that either this data hack was how someone got my bank info, or my bank sold my personal info to another company. I had to go and get a new debit card as my other one was closed. My bank did help me dispute the charges with Facebook Meta, and I got my money back.
I am getting TIRED of doing all I can to protect my info and my credit reports, and it happens more and more, it doesn’t matter if you are vigilant, the companies entrusted to keep our info safe are either not upgrading their security measures to protect US or enriching themselves by selling our info. Right now, I am also dealing with another company that was compromised
The thing that’s driving me crazy about all of this is that nobody seems to be questioning HOW NPD acquired SSNs and other highly sensitive personal data that typically, the only third party that has access to, is credit bureaus. SSNs are usually only shared by people with a small number of entities like medical, educational, financial and employers. So how then, could NPD have legitimately acquired this data? In my opinion, real crimes subject to incarceration, would have had to been committed in order for NPD to have amassed so much sensitive data of so many people. Yet, all of the outrage seems to be directed at NPD’s “leaking” of the data, RATHER than the fact that they had the data in the FIRST place!
If there EVER was a legitimate occasion for a Congressional Inquiry, THIS is it!
Having this information is extremely important because it gives you real life examples to look at that coincide with an attack that may be in your email currently. It allows you to be more aware of threats and look out for similar attacks. 10
Having searched the breached database from National Public Data, I saw personal information about myself dating back to when I was 16 years old. Much of it clearly linked back to my credit reports. Several of the records included my personal employee ID number for a company I worked at, where we were issued a company credit card with our employee ID number attached to it.
Why do the companies who tell us whether or not our data was breached, openly offer all our personal information freely on the internet, to anyone who searches for it? I got my own and many other peoples’ full name, full address, full phone number, partial DOB, and the last 2 digits of their (and my) SSN. This seems like a tremendous breach in and of itself! Outrageous to publish this data online, for anyone and everyone to access.
Freezing our credit is entirely inadequate. There are many fraudulent uses of our personal information that do not involve new account creation, which is the only use that’s impacted by a credit freeze.
Criminals can still participate in account-takeover (intercepting an existing account, using it for fraud, possibly changing the address/phone number/password and locking you out of the account).
There’s using someone’s personal info for employment (their wages illegally being attributed to the innocent victim).
There is medical identity theft–using someone’s personal info to run up costly medical bills.
There is hijacking the title to someone’s home, transferring it into their own name, and selling the home.
Good luck with stopping these crimes. Freezing our credit will have no impact. Even just having our online accounts get hacked will be possible with the data that has been exposed.
How do we get these background check companies to delete our info, or at least the obsolete incorrect data? They show all my personal info going back 40+ years. The addresses and phone numbers are wrong. We don’t want people contacting these incorrect places, sending junk mail, credit applications, or other material to former locations. We should have the right to correct their databases, but we don’t even have access to do so. This is completely outrageous and infuriating.