Many GitHub users this week received a novel phishing email warning of critical security holes in their code. Those who clicked the link for details were asked to distinguish themselves from bots by pressing a combination of keyboard keys that causes Microsoft Windows to download password-stealing malware. While it’s unlikely that many programmers fell for this scam, it’s notable because less targeted versions of it are likely to be far more successful against the average Windows user.
A reader named Chris shared an email he received this week that spoofed GitHub’s security team and warned: “Hey there! We have detected a security vulnerability in your repository. Please contact us at https://github-scanner[.]com to get more information on how to fix this issue.”
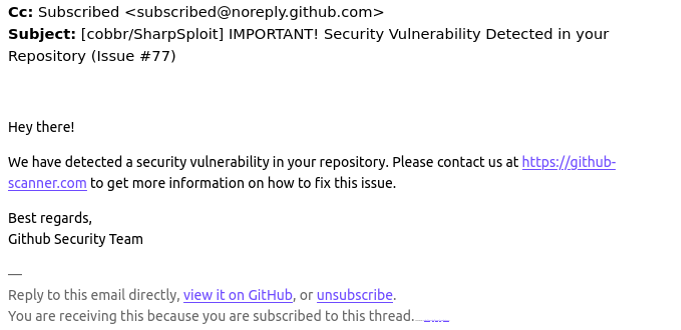
Visiting that link generates a web page that asks the visitor to “Verify You Are Human” by solving an unusual CAPTCHA.
This malware attack pretends to be a CAPTCHA intended to separate humans from bots.
Clicking the “I’m not a robot” button generates a pop-up message asking the user to take three sequential steps to prove their humanity. Step 1 involves simultaneously pressing the keyboard key with the Windows icon and the letter “R,” which opens a Windows “Run” prompt that will execute any specified program that is already installed on the system.
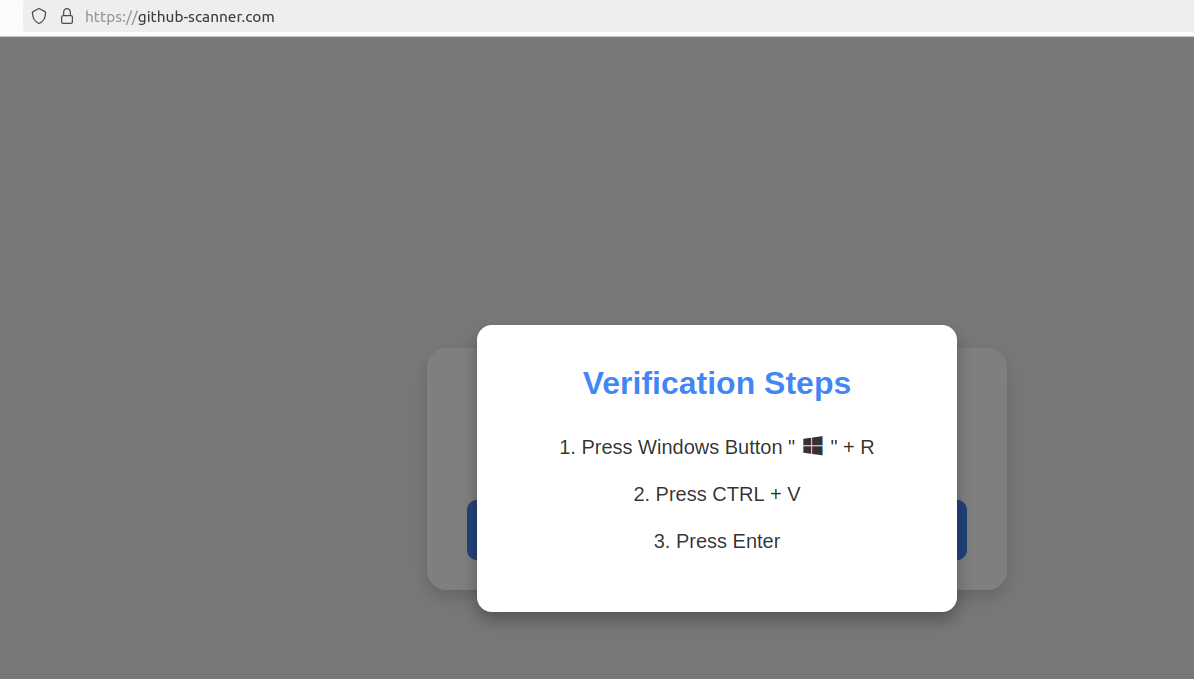
Executing this series of keypresses prompts the built-in Windows Powershell to download password-stealing malware.
Step 2 asks the user to press the “CTRL” key and the letter “V” at the same time, which pastes malicious code from the site’s virtual clipboard.
Step 3 — pressing the “Enter” key — causes Windows to launch a PowerShell command, and then fetch and execute a malicious file from github-scanner[.]com called “l6e.exe.”
PowerShell is a powerful, cross-platform automation tool built into Windows that is designed to make it simpler for administrators to automate tasks on a PC or across multiple computers on the same network.
According to an analysis at the malware scanning service Virustotal.com, the malicious file downloaded by the pasted text is called Lumma Stealer, and it’s designed to snarf any credentials stored on the victim’s PC.
This phishing campaign may not have fooled many programmers, who no doubt natively understand that pressing the Windows and “R” keys will open up a “Run” prompt, or that Ctrl-V will dump the contents of the clipboard.
But I bet the same approach would work just fine to trick some of my less tech-savvy friends and relatives into running malware on their PCs. I’d also bet none of these people have ever heard of PowerShell, let alone had occasion to intentionally launch a PowerShell terminal.
Given those realities, it would be nice if there were a simple way to disable or at least heavily restrict PowerShell for normal end users for whom it could become more of a liability.
However, Microsoft strongly advises against nixing PowerShell because some core system processes and tasks may not function properly without it. What’s more, doing so requires tinkering with sensitive settings in the Windows registry, which can be a dicey undertaking even for the learned.
Still, it wouldn’t hurt to share this article with the Windows users in your life who fit the less-savvy profile. Because this particular scam has a great deal of room for growth and creativity.




Hi, nextdns to block the phishing website and hardentools to disable powershell.
All the tools to block phishing scams already exist.
Why would you want to disable Powershell? The URL in this phishing scam is github-scanner[.]com, not github[.]com. Learning how to read and understand URLs might serve you better than disabling the most useful app Microsoft ever created. Also, as the author stated in the article, Windows + R opens the run dialog, and CTL + V dumps the clipboard. All this happens on your screen in front of your eyes. If you push the enter key from there, your problem isn’t just limited to malware.
The average user has no more use for powershell than they do the cmd line or even less. Since they aren’t using it and malware is targeting it, the reason is pretty obvious why the average user might want to disable it.
Not really true, as often time as deskside support, you’ll need access to command line or powershell to fix an issue specific to the profile. It also does not stop the run command from functioning.
> Learning how to read and understand URLs might serve you better than disabling the most useful app Microsoft ever created.
Are you suggesting that the best defense is to rely on uninformed users educating themselves entirely on their own volition? I hope you don’t work in security…
Except how to stop humans from believing lies…and how to block BEFORE they click on new, unknown bait…
How are they stuffing the Windows clipboard with the download command? That shouldn’t be possible, so it seems that’s where the actual vulnerability is at.
It’s the browsers Clipboard api that they are using.
Possibly when the “I’m not a robot” button is clicked, fulfilling a “user interaction”. It’s a fairly common javascript-powered browser function for a user to “click to copy” something, via the Clipboard API.
That’s correct. They are just using the same function as when you click to copy text. The exploit relies on the user’s inexperience of what the powershell is and how rare it would be for something like this to actually occur. Unless you are doing something like installing software there should never be a need to verify using your powershell. Maybe if you were trying to ssh or use git commands but this should just be a red flag to any user with at least a little technical sense. I can see how some of the more seasoned developers might think it is part of github though, as they work a lot with the command line interface.
Simple browser permission anyone falling for this is a moron
These sorts of comments don’t help the conversation. You moron.
Other commentators are correct; it is the browsers Clipboard api.
John Hammond from Huntress Labs does an excellent job of breaking down the attack vector here;
https://youtu.be/lSa_wHW1pgQ
I don’t click on URLs in Kreb’s comments section. It.just.feels.Dangerous…….
That is a fair point. I otherwise suggest you Google ‘Fake CAPTCHA Runs Malware’ by John Hammond on YouTube, as my original comment still stands.
Also, for your own future information/protection, you can securely analyse suspect URL’s at VirusTotal[.]com, a security tool and subsidiary of Google.
Assuming virustotal dot com is legit. I think what we have here is a bootstrapping problem.
You can assume whatever you like, but did you even READ the article? Bootstrapping would only be a problem if I was the only one referencing VirusTotal, but I wasn’t. Not only does Brian reference VirusTotal in paragraph eight, he also includes a link to the analysis of the malicious ‘VQP.exe’ file discussed in his report, on said site.
VirusTotal is an industry standard security research tool supported by at least 72 Antivirus vendors’ engines and research teams globally and if you were a regular here you would know that. Maybe it isn’t legit and you are the only one who knows better, but you do you.
Also, the the Powershell command has been hashed. So even at a glance, you couldn’t read the pasted string without decrypting it.
There is no vulnerability in this case.
The author has abused the available browsers’ JavaScript features.
In this example, the author created a dynamic text box with a pre-populated malicious PowerShell command, copied it using a Javascript document object (select & execCommand), and removed the textbox after copy.
Powershell command gets executed after pressing the enter button.
I am someone with a lifetime of both personal and employment experience using computers and going online, as well as some formal education in computer networking. Several years ago I received an email from a company that I easily recognized (I actually can’t remember which one at this moment) as a place I had done business with often in the past. “You may have received a spam or fraudulent email recently. Please click on this link to read for more information.”
I clicked on the link and immediately downloaded some kind of virus that completely destroyed my computer hard drive. I knew almost immediately that there was a problem because something with .exe showed up on my screen. I even unplugged my ethernet cable to try and stop the download, but it was too late. Later, nobody I know, including my own father, could actually believe that someone like me would click on a link that was so destructive, but I did. I had to reinstall Windows from install disks and start over from the beginning. Luckily for me, I have always been obsessed with owning external hard drives and such so I didn’t permanently lose any important data.
Thank you, Delilah, for sharing your experience. I need reminders like this to keep me vigilant.
Shouldn’t Windows just show a huge warning explaining the implications of such actions ehen a user who has never user the Windows Run function nor PowerShell suddenly attempts to run some suspicious posted code?
During the course of regular installs or updates it’s quite normal to see the software run something in PS. As far as the run command I’d think many users in the course of ownership have used the run command for something.
Yup. A user would, in a properly secured environment, get another notice and/or block before a program can run or install.
Shouldn’t Windows just show a huge warning explaining the implications of such actions when a user who has never used the Windows Run function nor PowerShell suddenly attempts to run some suspicious code pasted from the clipboard?
For this type of attack, knowledge is power. Yes, there are technical vulnerabilities which may be dismissed as features or too hard or dangerous to mitigate. But a key factor in this attack is social engineering and the best defense if knowledge. The trick is conveying this knowledge in a manner which does not make the recipient tune out.
Claiming anybody is a moron for falling for this is rather disingenuous. I would not have fallen for it, but I have relevant experience. I fully expect I may fall for something like this, in spite of being very cautious.
My $.02.
For Microsoft Edge and go to Settings.
Navigate to Site permissions > Clipboard.
Toggle off the option to allow sites to access the clipboard.
The setting has this text “Will block if turned off”
the guy that falls for that definitely does not have any idea that is even a thing, browsers should block by default tbh.
It would be informative to know if this works with the default Microsoft Power-Shell “ExecutionPolicy”
the benigne Get-ExecutionPolicy -List will get the current ExecutionPolicy
It’s not too painful on Windows 10 to disable Powershell if you use the local group policy editor. Because what you want to do is disable the user from starting it, only, not the system. But it certainly isn’t simple like a button click… Theoretically, you could make a batch file out of enable/disable if the policy editor accepts command line arguments, linking that as an icon on the desktop, but that’s outside of the scope of what I know.
https://www.windowscentral.com/how-disable-powershell-windows-10
10 Home does not include the GPE.
?….link is rife with nonsensical/dangerous “clicks”. Go back to speaking softly to your “pussies”.
Then don’t click on them. That’s a problem with lots of current websites, but it doesn’t make the information invalid.
There is an open source tool for that;
https://github.com/hardentools/hardentools
Hardentools is intended for individuals at risk, who might want an extra level of security at the price of some usability. It is not intended for corporate environments. It can disable an array of Windows features not commonly used by the average home user such as Powershell.
Be sure to set a system restore point before using these tools.
There are limitations and known issues, so take note of the README before executing.
Hey guys I found a cool trick to get into AOL admin mode! Just press ALT+F4!
[Somebody22 has left the chat.]
As Brian suspected this “clipboard paste to command execution” is an effective social engineering method – we’ve been constantly running into incidents originating from various vectors (watering hole being most common) utilizing this technique into getting code running on the victim device.
Then there’s all the fuss with “who should be able to run PowerShell and why” in corporate environments, and while waiting for hardening actions these cases keep popping up.
An exemplary analysis of Lumma Stealer: https://www.vmray.com/analyses/_mb/91f03b0ae9dc/report/overview.html
This link really is irrelevant to the conversation. Lumma Stealer is a MaaS information stealer payload that has been seen in the wild since at least August 2022.
https://malpedia.caad.fkie.fraunhofer.de/details/win.lumma
What is of extreme interest in Brians article is the novel approach taken to inject the payload on an unsuspecting users system ie; clipboard paste hashed command and execution. This form of social engineering will only evolve and become more dangerous over time. For a more relevant understanding of this attack vector see John Hammonds walk through here;
https://youtu.be/lSa_wHW1pgQ
respect, thank you for explaining.
Did this email actually originate from Github? I’m guessing not. Github has all the right DNS entries to prevent spoofing, which makes me wonder why the victim’s email system ignored them.
It looks like the attacker opened an issue on a github repo, which would have made the email come from the github system in the first place. The comment is what’s malicious, but the email would pass SPF etc since it’s a notification email from github itself which contains the user input. The only line of defense I see against the email itself would be if the URL is blacklisted and the receiver has email security that does URL analysis. Or, github could consider not including the message body of a newly opened issue in the email notification, since technically you can spam that way using their email servers as we saw here.
What does the script look like? Does it work/cause harm if the user does not have admin rights on the computer?
I wouldn’t place much ‘trust’ in being non-admin anymore. Too many priv-elevation exploits exist, SYSTEM privs via side-loaded or hollow DLL’s or other circumvention. It was a very first line of defense back in the day, maybe still a best practice in a general sense, but as far as protecting you from payload execution currently… I wouldn’t count on it.
This site has, in the past, on several occasions, touted the site askwoody.com as a useful place to get information about Windows Update patches, including whether there have been any reported problems with recently released patches.
Unfortunately, that site has now done me a dirty. They have a weekly “newsletter” with one or sometimes two free articles, plus two or three paywalled ones; the most recent one offered two free articles, but when I went to view either of them the link went to the first article (so the second free article was inaccessible). I went into their comments to report the problem, as did another user who even included a screenshot.
Their response was … to rescind the free offer for the second article, rather than fix the URL so it was possible to read the second article for free as they had originally promised.
That’s bad.
When criticized for making and then overtly and intentionally breaking a promise to their readership, their response was then … to start censoring the thread to suppress the criticism, rather than apologize and do the right thing (offer the promised 2nd free article, with the link working properly this time).
That’s worse.
If anyone here knows of a better-behaved site that also tracks problems with Windows patches and offers recommendations for when to wait and when to go ahead, I’d be interested in knowing.
Pete and Repeat were in a boat.
Pete fell out, who was left?
At some point, one has to recognize that there is a basic level of competence required to safely operate a computer.
Yeah or just don’t use Windoze.
This attack works on Linux too, lol
abbacus, finger counting possibly..
but darn side channels keep listening to my counting.. jk
*** SCRIPT BLOCKERS ARE YOU FRIEND *** NOSCRIPT VIA FIREFOX
Probably can disable powershell via GPO or manually destroy any entries via regedit
but there is a powershell backup that can be called up anytime via the ms admins or any
skilled it user.
Go back to basics… back up your vip data off line, create an image of your most vital systems,
harden vital systems but know zeros days exist and will always exist to crash any system.
The bhat and whats need job security and would find ways to fook with each other without computers
like to skilled chess players wanting to prove their metal.
Life is too short worrying about something your didn’t create like flawed os. install the known updates but live
your life.
You also have to realise that only the truly paranoid will not get harmed by such things.
For instance do you know that this kind of attack is over half a century old?
Back in the 1970’s the switch over from mechanical KSR and ASR Teletypes to the early “Visual Display Units”(VDUs) was in progress.
As part of VDU’s was the notion if “screens” with “addressable cursors” that in turn gave rise to the idea of menus and “function keys” that then became remotely programmable…
Yup the “Mainframe” could download a bunch of command sequences down into the VDU that when a user pressed a function key the downloaded command sequences would be executed.
Around this time Unix had started gaining some considerable popularity. And with it came the command line application “write” that could be used to send a line of text to another users terminal (the most famous use was “Wall” used by admins to send admin messages to all users).
Well it was not long before someone worked out how to use “write” to send a string to a VDU to program a function key with a small “shell script” and get a user to press the function key to run it…
This issue continued with the “talk” program.
So here we are half a century later with it not being a function key but the very similar in functionality Web clipboard buffer…
Could such an attack happen again with another “useful feature”?
Simple answer is “yes” the only real question is,
“What idiot will create the enabling buffer / clipboard functionality?”
Oh and “When?”
Because beyond any doubt the ICT industry does not learn from it’s “security history”,
“So the wheel goes around doing the same old same old.”
With people getting hurt/harmed.
Ah, Clive, you bring up fond memories of youth, college hotties and the community college’s DEC PDP-11/780…
I have the memories, but these days also the thinning hair and joints that creak loud enough they alarm the neighborhood dogs as I try to walk past there homes …
Seems a majority of commenters missed this…
“Still, it wouldn’t hurt to share this article with the Windows users in your life who fit the less-savvy profile. Because this particular scam has a great deal of room for growth and creativity.”
So we get it, most regulars here wouldn’t fall for this…so let’s make sure others don’t
Thanks again Brian, the go to source for all things security!
Just disable Win+R hotkey
Ha! I read it as github-scammer.com
I think this is more a skill issue rather than something that needs to try to be stopped technically. Let’s say you stop the browser from accessing the clipboard, what stops the site from just adding one more step of having to press Ctrl+C which the website already selected?
Although, being able to download and run the offending software from powershell should not be possible. Powershell shouldn’t be allowed to download anything without the appropriate permissions that admins have.
Since this was targeting developers who would need powershell, blocking it wouldn’t have prevented any of this from occurring either.
IMO the issue is allowing clipboard to paste into PS at all. Clipboard is not a protected app. PS should be.
Sure it’d be inconvenient to have to type out commands – maybe PS could have a library/repo inside itself that securely stores commands after additional priv/verification, or checks them in a sandbox or something for heuristics or weird urls, rather than just allowing ANY user’s clipboard contents to be instantly run on the most powerful system tool M$ offers. It’s actually a basic security fail if you think about it. Convenience and legacy inter-op rule in Redmond.
‘Since this was targeting developers who would need powershell, blocking it wouldn’t have prevented any of this from occurring either.’
You are totally missing the whole point of the article. Yes, it is a skill issue, but you can’t point the finger of blame at non-technical end users. PEBKAC is real. Why do you think Help Desk and MSPs exist? That’s like a bank blaming a scam victim when they don’t even offer decent MFA, and many don’t.
To further Mealy’s comments above, this attack vector is only in its infancy and is going to evolve. And its future targets won’t be Software Devs, I can guarantee that. This is a security issue that Microsoft needs to address NOW. Convenience be damned. If Microsoft want the market share, they should also take responsibility for end user security seriously. If Apple can do it, so can they.
If some moron with a github repository has been fooled by this, I’d like to see his code.
Once again the Classic Model M from Unicomp proves its superiority to all other keyboards. Can’t get tricked into using a shortcut with the Windows key if you don’t have a windows key.
It would be interesting to see if this sparks some type of signature based defense from microsoft. It almost reminds me of the old .vbs files exploit we used to have back on windows 98 and xp I think had the issue. Quite the similar modus operandi. There are a lot of ways this will work because of the way github autheticates over https for it’s command line. Sometimes coders are just copying and pasting 99% of their time on github in order to get the environment set up. So i can see how someone who is not paying attention would fall victim to this type of scam.