Two men have been arrested for allegedly stealing data from and extorting dozens of companies that used the cloud data storage company Snowflake, but a third suspect — a prolific hacker known as Kiberphant0m — remains at large and continues to publicly extort victims. However, this person’s identity may not remain a secret for long: A careful review of Kiberphant0m’s daily chats across multiple cybercrime personas suggests they are a U.S. Army soldier who is or was recently stationed in South Korea.
Kiberphant0m’s identities on cybercrime forums and on Telegram and Discord chat channels have been selling data stolen from customers of the cloud data storage company Snowflake. At the end of 2023, malicious hackers discovered that many companies had uploaded huge volumes of sensitive customer data to Snowflake accounts that were protected with nothing more than a username and password (no multi-factor authentication required).
After scouring darknet markets for stolen Snowflake account credentials, the hackers began raiding the data storage repositories for some of the world’s largest corporations. Among those was AT&T, which disclosed in July that cybercriminals had stolen personal information, phone and text message records for roughly 110 million people. Wired.com reported in July that AT&T paid a hacker $370,000 to delete stolen phone records.
On October 30, Canadian authorities arrested Alexander Moucka, a.k.a. Connor Riley Moucka of Kitchener, Ontario, on a provisional arrest warrant from the United States, which has since indicted him on 20 criminal counts connected to the Snowflake breaches. Another suspect in the Snowflake hacks, John Erin Binns, is an American who is currently incarcerated in Turkey.

A surveillance photo of Connor Riley Moucka, a.k.a. “Judische” and “Waifu,” dated Oct 21, 2024, 9 days before Moucka’s arrest. This image was included in an affidavit filed by an investigator with the Royal Canadian Mounted Police (RCMP).
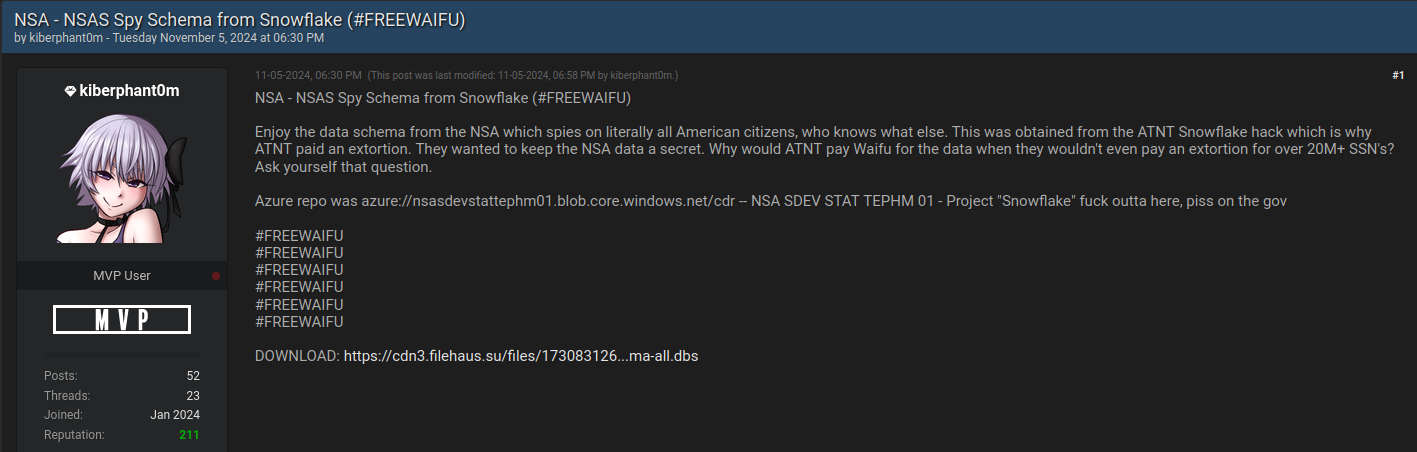
Investigators say Moucka, who went by the handles Judische and Waifu, had tasked Kiberphant0m with selling data stolen from Snowflake customers who refused to pay a ransom to have their information deleted. Immediately after news broke of Moucka’s arrest, Kiberphant0m was clearly furious, and posted on the hacker community BreachForums what they claimed were the AT&T call logs for President-elect Donald J. Trump and for Vice President Kamala Harris.
“In the event you do not reach out to us @ATNT all presidential government call logs will be leaked,” Kiberphant0m threatened, signing their post with multiple “#FREEWAIFU” tags. “You don’t think we don’t have plans in the event of an arrest? Think again.”
On the same day, Kiberphant0m posted what they claimed was the “data schema” from the U.S. National Security Agency.
“This was obtained from the ATNT Snowflake hack which is why ATNT paid an extortion,” Kiberphant0m wrote in a thread on BreachForums. “Why would ATNT pay Waifu for the data when they wouldn’t even pay an extortion for over 20M+ SSNs?”
Also on Nov. 5, Kiberphant0m offered call logs stolen from Verizon’s push-to-talk (PTT) customers — mainly U.S. government agencies and emergency first responders. On Nov. 9, Kiberphant0m posted a sales thread on BreachForums offering a “SIM-swapping” service targeting Verizon PTT customers. In a SIM-swap, fraudsters use credentials that are phished or stolen from mobile phone company employees to divert a target’s phone calls and text messages to a device they control.
MEET ‘BUTTHOLIO’
Kiberphant0m joined BreachForums in January 2024, but their public utterances on Discord and Telegram channels date back to at least early 2022. On their first post to BreachForums, Kiberphant0m said they could be reached at the Telegram handle @cyb3rph4nt0m.
A review of @cyb3rph4nt0m shows this user has posted more than 4,200 messages since January 2024. Many of these messages were attempts to recruit people who could be hired to deploy a piece of malware that enslaved host machines in an Internet of Things (IoT) botnet.
On BreachForums, Kiberphant0m has sold the source code to “Shi-Bot,” a custom Linux DDoS botnet based on the Mirai malware. Kiberphant0m had few sales threads on BreachForums prior to the Snowflake attacks becoming public in May, and many of those involved databases stolen from companies in South Korea.
On June 5, 2024, a Telegram user by the name “Buttholio” joined the fraud-focused Telegram channel “Comgirl” and claimed to be Kiberphant0m. Buttholio made the claim after being taunted as a nobody by another denizen of Comgirl, referring to their @cyb3rph4nt0m account on Telegram and the Kiberphant0m user on cybercrime forums.
“Type ‘kiberphant0m’ on google with the quotes,” Buttholio told another user. “I’ll wait. Go ahead. Over 50 articles. 15+ telecoms breached. I got the IMSI number to every single person that’s ever registered in Verizon, Tmobile, ATNT and Verifone.”
On Sept. 17, 2023, Buttholio posted in a Discord chat room dedicated to players of the video game Escape from Tarkov. “Come to Korea, servers there is pretty much no extract camper or cheater,” Buttholio advised.
In another message that same day in the gaming Discord, Buttholio told others they bought the game in the United States, but that they were playing it in Asia.
“USA is where the game was purchased from, server location is actual in game servers u play on. I am a u.s. soldier so i bought it in the states but got on rotation so i have to use asian servers,” they shared.
‘REVERSESHELL’
The account @Kiberphant0m was assigned the Telegram ID number 6953392511. A review of this ID at the cyber intelligence platform Flashpoint shows that on January 4, 2024 Kibertphant0m posted to the Telegram channel “Dstat,” which is populated by cybercriminals involved in launching distributed denial-of-service (DDoS) attacks and selling DDoS-for-hire services [Full disclosure: Flashpoint is currently an advertiser on this website].
Immediately after Kiberphant0m logged on to the Dstat channel, another user wrote “hi buttholio,” to which Kiberphant0m replied with an affirmative greeting “wsg,” or “what’s good.” On Nov. 1, Dstat’s website dstat[.]cc was seized as part of “Operation PowerOFF,” an international law enforcement action against DDoS services.
Flashpoint’s data shows that @kiberphant0m told a fellow member of Dstat on April 10, 2024 that their alternate Telegram username was “@reverseshell,” and did the same two weeks later in the Telegram chat The Jacuzzi. The Telegram ID for this account is 5408575119.
Way back on Nov. 15, 2022, @reverseshell told a fellow member of a Telegram channel called Cecilio Chat that they were a soldier in the U.S. Army. This user also shared the following image of someone pictured waist-down in military fatigues, with a camouflaged backpack at their feet:

Kiberphant0m’s apparent alias ReverseShell posted this image on a Telegram channel Cecilio Chat, on Nov. 15, 2022. Image: Flashpoint.
In September 2022, Reverseshell was embroiled in an argument with another member who had threatened to launch a DDoS attack against Reverseshell’s Internet address. After the promised attack materialized, Reverseshell responded, “Yall just hit military base contracted wifi.”
In a chat from October 2022, Reverseshell was bragging about the speed of the servers they were using, and in reply to another member’s question said that they were accessing the Internet via South Korea Telecom.
Telegram chat logs archived by Flashpoint show that on Aug. 23, 2022, Reverseshell bragged they’d been using automated tools to find valid logins for Internet servers that they resold to others.
“I’ve hit US gov servers with default creds,” Reverseshell wrote, referring to systems with easy-to-guess usernames and/or passwords. “Telecom control servers, machinery shops, Russian ISP servers, etc. I sold a few big companies for like $2-3k a piece. You can sell the access when you get a big SSH into corporation.”
On July 29, 2023, Reverseshell posted a screenshot of a login page for a major U.S. defense contractor, claiming they had an aerospace company’s credentials to sell.
PROMAN AND VARS_SECC
Flashpoint finds the Telegram ID 5408575119 has used several aliases since 2022, including Reverseshell and Proman557.
A search on the username Proman557 at the cyber intelligence platform Intel 471 shows that a hacker by the name “Proman554” registered on Hackforums in September 2022, and in messages to other users Proman554 said they can be reached at the Telegram account Buttholio.
Intel 471 also finds the Proman557 moniker is one of many used by a person on the Russian-language hacking forum Exploit in 2022 who sold a variety of Linux-based botnet malware.
Proman557 was eventually banned — allegedly for scamming a fellow member out of $350 — and the Exploit moderator warned forum users that Proman557 had previously registered under several other nicknames, including an account called “Vars_Secc.”
Vars_Secc’s thousands of comments on Telegram over two years show this user divided their time between online gaming, maintaining a DDoS botnet, and promoting the sale or renting of their botnets to other users.
“I use ddos for many things not just to be a skid,” Vars_Secc pronounced. “Why do you think I haven’t sold my net?” They then proceeded to list the most useful qualities of their botnet:
-I use it to hit off servers that ban me or piss me off
-I used to ddos certain games to get my items back since the data reverts to when u joined
-I use it for server side desync RCE vulnerabilities
-I use it to sometimes ransom
-I use it when bored as a source of entertainment
Flashpoint shows that in June 2023, Vars_Secc responded to taunting from a fellow member in the Telegram channel SecHub who had threatened to reveal their personal details to the federal government for a reward.
“Man I’ve been doing this shit for 4 years,” Vars_Secc replied nonchalantly. “I highly doubt the government is going to pay millions of dollars for data on some random dude operating a pointless ddos botnet and finding a few vulnerabilities here and there.”
For several months in 2023, Vars_Secc also was an active member of the Russian-language crime forum XSS, where they sold access to a U.S. government server for $2,000. However, Vars_Secc would be banned from XSS after attempting to sell access to the Russian telecommunications giant Rostelecom. [In this, Vars_Secc violated the Number One Rule for operating on a Russia-based crime forum: Never offer to hack or sell data stolen from Russian entities or citizens].
On June 20, 2023, Vars_Secc posted a sales thread on the cybercrime forum Ramp 2.0 titled, “Selling US Gov Financial Access.”
“Server within the network, possible to pivot,” Vars_Secc’s sparse sales post read. “Has 3-5 subroutes connected to it. Price $1,250. Telegram: Vars_Secc.”
Vars_Secc also used Ramp in June 2023 to sell access to a “Vietnam government Internet Network Information Center.”
“Selling access server allocated within the network,” Vars_Secc wrote. “Has some data on it. $500.”
BUG BOUNTIES
The Vars_Secc identity claimed on Telegram in May 2023 that they made money by submitting reports about software flaws to HackerOne, a company that helps technology firms field reports about security vulnerabilities in their products and services. Specifically, Vars_Secc said they had earned financial rewards or “bug bounties” from reddit.com, the U.S. Department of Defense, and Coinbase, among 30 others.
“I make money off bug bounties, it’s quite simple,” Vars_Secc said when asked what they do for a living. “That’s why I have over 30 bug bounty reports on HackerOne.”
A month before that, Vars_Secc said they’d found a vulnerability in reddit.com.
“I poisoned Reddit’s cache,” they explained. “I’m going to exploit it further, then report it to reddit.”
KrebsOnSecurity sought comment from HackerOne, which said it would investigate the claims. This story will be updated if they respond.
The Vars_Secc telegram handle also has claimed ownership of the BreachForums member “Boxfan,” and Intel 471 shows Boxfan’s early posts on the forum had the Vars_Secc Telegram account in their signature. In their most recent post to BreachForums in January 2024, Boxfan disclosed a security vulnerability they found in Naver, the most popular search engine in South Korea (according to statista.com). Boxfan’s comments suggest they have strong negative feelings about South Korean culture.
“Have fun exploiting this vulnerability,” Boxfan wrote on BreachForums, after pasting a long string of computer code intended to demonstrate the flaw. “Fuck you South Korea and your discriminatory views. Nobody likes ur shit kpop you evil fucks. Whoever can dump this DB [database] congrats. I don’t feel like doing it so I’ll post it to the forum.”
The many identities tied to Kiberphant0m strongly suggest they are or until recently were a U.S. Army soldier stationed in South Korea. Kiberphant0m’s alter egos never mentioned their military rank, regiment, or specialization.
However, it is likely that Kiberphant0m’s facility with computers and networking was noticed by the Army. According to the U.S. Army’s website, the bulk of its forces in South Korea reside within the Eighth Army, which has a dedicated cyber operations unit focused on defending against cyber threats.
On April 1, 2023, Vars_Secc posted to a public Telegram chat channel a screenshot of the National Security Agency’s website. The image indicated the visitor had just applied for some type of job at the NSA.

A screenshot posted by Vars_Secc on Telegram on April 1, 2023, suggesting they just applied for a job at the National Security Agency.
The NSA has not yet responded to requests for comment.
Reached via Telegram, Kiberphant0m acknowledged that KrebsOnSecurity managed to unearth their old handles.
“I see you found the IP behind it no way,” Kiberphant0m replied. “I see you managed to find my old aliases LOL.”
Kiberphant0m denied being in the U.S. Army or ever being in South Korea, and said all of that was a lengthy ruse designed to create a fictitious persona. “Epic opsec troll,” they claimed.
Asked if they were at all concerned about getting busted, Kiberphant0m called that an impossibility.
“I literally can’t get caught,” Kiberphant0m said, declining an invitation to explain why. “I don’t even live in the USA Mr. Krebs.”
Below is a mind map that hopefully helps illustrate some of the connections between and among Kiberphant0m’s apparent alter egos.
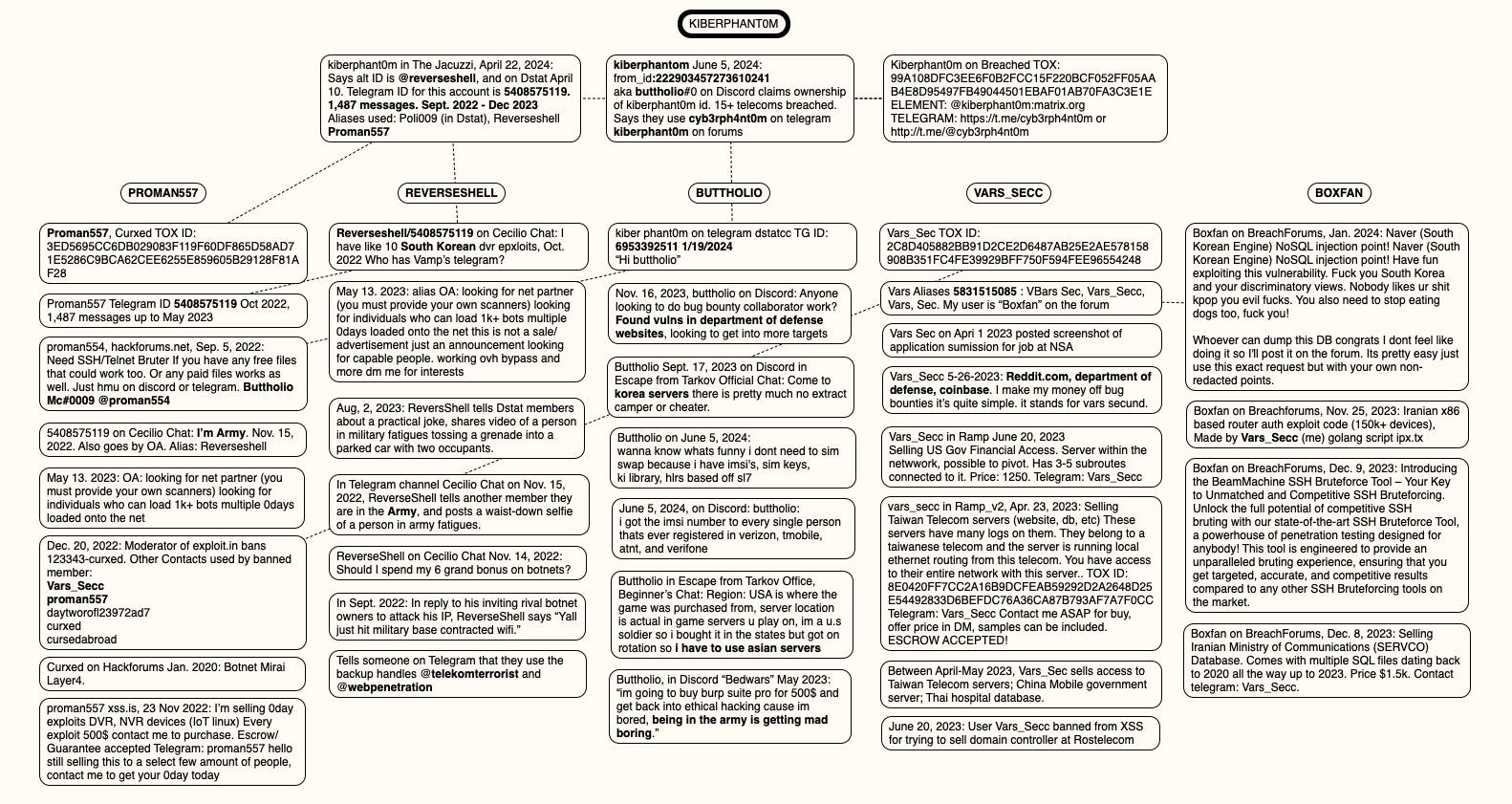
A mind map of the connections between and among the identities apparently used by Kiberphant0m. Click to enlarge.
KrebsOnSecurity would like to extend a special note of thanks to the New York City based security intelligence firm Unit 221B for their assistance in helping to piece together key elements of Kiberphant0m’s different identities.




kiberphantom is Russian and resides in Russia
I was going to say, how do we know he’s in the U.S. Military? It’s pure speculation, no?
Because he claimed it. The claims were reported in the article prominently. Whether BK believes that or not is undisclosed, but I’d suspect he knows more than he’d print as fact here.
Please stop with they/them gender stuff in articles, it’s impossible to read and try to figure out if you are talking about single person or group of people. You wrote somehow 4 years ago without all this gender crap and it was not confusing or offending anybody.
It’s been used as a singular since the 1300s. Maybe time for you to catch up.
https://en.wikipedia.org/wiki/Singular_they
I don’t understand this complaint. Since the gender, or even the number of people involved, is truly unknown, I didn’t find the grammar choice of they/their to be wrong at all. I would have written it the same way and I will never use gender stupidity in my writing.
Uh-oh, that’s a “you” problem – you wouldn’t have had any problem with the common, constant and century-old use of “they” in that context until a few years ago. Now, you feel politically obligated to pretend you don’t understand. I would drop the political posturing if I were you. It’s tedious and embarrassing.
I agree with GS – it does my head in trying to read it. The lefty obsession with pronouns and social engineering is one of the big reasons the Democrats just got pasted by the openly fascist MAGA Republicans. People are fed up with it. (but as usual, the investigative journalism is first class)
What a fucking moron.
“You wrote somehow 4 years ago without all this gender crap.”
You absolute fucking dolt. I’m tired of goddamn idiots going around acting like they have a triple-digit IQ.
Surely you could have phrased that more effectively…
Oh dear TheCritic89 …. Did GS hit a nerve?
B tier bait
You would think with all this intelligence – and I’m talking about smarts, not data – they could come up with less gay names. WAIFU? I mean I’m not judging but that’s super gay. I’m sure NEO was taken but at least take a shot a B4TM4N or something similar for godsakes. It’s embarrassing.
??? are we in an 8th grade changing room here? Just as a reminder, between 2 and 10% of adults are homosexual or attracted to persons of their own gender. If you are explicitly _afraid_ of that, maybe it’s time to get some consulting.
Love it when skids realize their OPSEC sucks and double down trying to mislead the investigator.
If it really was an “epic opsec trolling” he wouldnt admit to it and instead continue trolling a little bit more. Sounds more like some desperate last attempts to save his ass.
Congrats brian, another week another skid busted by krebs. I love it!
South Korea Telecom doesn’t exist; it’s a misinterpretation of SK (Sunkyong) Telecom.
“Number one rule” in Russian groups not to target Russians’ data is smart, given that Russia, like many countries, has robust protections in law for the storage and use of locals’ data that the United States completely lacks for people living there… presumably because of bipartisan capture of the U.S. legislature and executive agencies by big social-media companies.
The thing is, Russia’s law enforcement agencies won’t bring charges against one of their own unless there is an actual victim in Russia. That is why all RU-based forums universally ban any money making schemes that seek to profit by recklessly or intentionally hacking or stealing data from Russian entities and individuals.
Furthermore, for those suggesting Kiberphant0m is somehow Russian, a Russian hacker would never have made the noob mistake they did in offering to sell access to Russia’s largest telecommunications provider.
just like war is a racket, hacking is a racket now.
this game is not for kids.. druggas, blackmail, ect, ect.. it is a layered cake of crappola..
but eat up if you think you can survive ecoli or worse.
doing the crime is the punishment.. forever trapped or pressed to do someone’s bidding
so they in turn don’t turn you in.
Just listen to the song, “The message” by Grand Master Flash and take it to heart, it just might save you from jail or wooden box.
‘Russia, like many countries, has robust protections in law for the storage and use of locals’ data that the United States completely lacks’
This statement may be correct on paper but please explain to me how Bellingcat, The Insider and Meduza in coordination with Navalnys’ Anti-Corruption Foundation managed to track down, identify and report on all of the senior high ranking FSB and GRU officials and their black ops activities over the last decade or two? For example; Flight MH17 incident, the Czechian warehouse explosion and Navalny/Skirpal poisonings?
They cross referenced hoards of leaked “protected” government data. Passports, flight/border logs, real estate holdings, military and criminal records, telecommunication logs, phone numbers, emails and text messages, car registration and licence details. How did they get access to all of this so called “protected” information? They paid for it!
You see, the US may have sh*tty privacy and security protections for its citizens personally identifiable information but Russia has had thriving underground black market data brokers for decades, if you know where to look and it is no secret. It’s just not advertised like Western data. Why? One word; CORRUPTION. Sure, Russian citizens and corporations may be safer than their Western counterparts when it comes to digital cybercrime but that doesn’t protect them from the unscrupulous officials selling said data out the backdoor to fund their lifestyles. Go figure?
The Telegram ID account looks like a phone # for Roanoke City VA
telegram ids arent phone numbers however. theyre sequential
FWIW, the clothing and gear in his Nov. 15, 2022 photo are current US Army OCP (“Operational Camouflage Pattern”).
I think the opsec troll is pretending that your information is wrong. I remember hearing a hacker say that if you mess up your opsec, just spread disinformation so nobody knows what’s real and what isn’t. I say follow the evidence. If it points towards him being American, he is. Personally I think he’s low self esteem, the ” I need to brag” type. So the military stuff fits that persona.
“Personally I think he’s low self esteem, the ” I need to brag” type.”
Well he’s a human being on the internet.
Thank you for the story. It’s clear his capture is close at hand. I’m looking forward to hearing him cry about his life story in court next year. That is if he doesn’t get disappeared by the FBI under the Patriot Act by Indefinite Detention, which is very likely.
With Telegram’s CEO having surrendered the keys to the Castle, one can only expect these noobs to be caught like flies in a spider Web.
By the way that NSA application might have been April’s fool joke but if not, the first thing to do is check who applied for jobs with the NSA and is currently stationed in South Korea.
It will take 10 minutes to nail that “he she they them hers we”. LOL.
Do you think being a proponent of principal agency with sadistic intent is something to be proud of? Enjoy basking in the metacognitive resonance of your own false consensus. Reveling in the dehumanization and downfall of another can never be justified as anything other than vicarious thrill-seeking, no matter what mental gymnastics you perform to morally disengage.
Objectively, empathy IS a virtue.
“Kiberphant0m’s alter egos never mentioned their military rank, regiment, or specialization.” . Kiberphant0m actually made a post about him working 17C MOS today (11/29/24) on his main acc which was deleted 10 minutes after he posted.
“Kiberphant0m’s alter egos never mentioned their military rank, regiment, or specialization.” . Kiberphant0m actually made a post about him working 17C MOS today (11/29/24) on his main acc which was deleted 10 minutes after he posted. Don’t know how true this is though….
The photo of his legs and feet show him wearing faded neglected boots. I don’t think a U.S. soldier would be allowed to wear such poorly maintained boots on duty.
The camo pants might be faded beyond acceptable wear, too, but I don’t know. The boots, though, sheesh.
Boot inspections stopped a long time ago.
This article feels like a real-life spy movie, but it’s unsettling to think it’s happening for real.
The idea that someone linked to the U.S. military could be behind these attacks raises big questions. How does this even happen?
What stood out to me was how simple security oversights, like weak passwords, led to such massive breaches. It’s a reminder that things like multi-factor authentication aren’t optional anymore—they’re essential.
The connections between Kiberphant0m’s online personas were fascinating. But it’s also scary to think about how often hackers might get away with this kind of thing.
And that NSA job application screenshot? That gave me chills. It really shows how blurred the lines can be between cybercrime and national security.
What do you all think? Are companies and governments doing enough to protect against this stuff?
ChatGPT comment
Take your fishing expeditions elsewhere, ai
Turns out the army stopped boot inspections long ago.
“Kiberphant0m’s alter egos never mentioned their military rank, regiment, or specialization.” As a former 11B, I can tell you he’s almost certainly not an 11B. 😉