One of the most notorious providers of abuse-friendly “bulletproof” web hosting for cybercriminals has started routing its operations through networks run by the Russian antivirus and security firm Kaspersky Lab, KrebsOnSecurity has learned.
Security experts say the Russia-based service provider Prospero OOO (the triple O is the Russian version of “LLC”) has long been a persistent source of malicious software, botnet controllers, and a torrent of phishing websites. Last year, the French security firm Intrinsec detailed Prospero’s connections to bulletproof services advertised on Russian cybercrime forums under the names Securehost and BEARHOST.
The bulletproof hosting provider BEARHOST. This screenshot has been machine-translated from Russian. Image: Ke-la.com.
Bulletproof hosts are so named when they earn or cultivate a reputation for ignoring legal demands and abuse complaints. And BEARHOST has been cultivating its reputation since at least 2019.
“If you need a server for a botnet, for malware, brute, scan, phishing, fakes and any other tasks, please contact us,” BEARHOST’s ad on one forum advises. “We completely ignore all abuses without exception, including SPAMHAUS and other organizations.”
Intrinsec found Prospero has courted some of Russia’s nastiest cybercrime groups, hosting control servers for multiple ransomware gangs over the past two years. Intrinsec said its analysis showed Prospero frequently hosts malware operations such as SocGholish and GootLoader, which are spread primarily via fake browser updates on hacked websites and often lay the groundwork for more serious cyber intrusions — including ransomware.
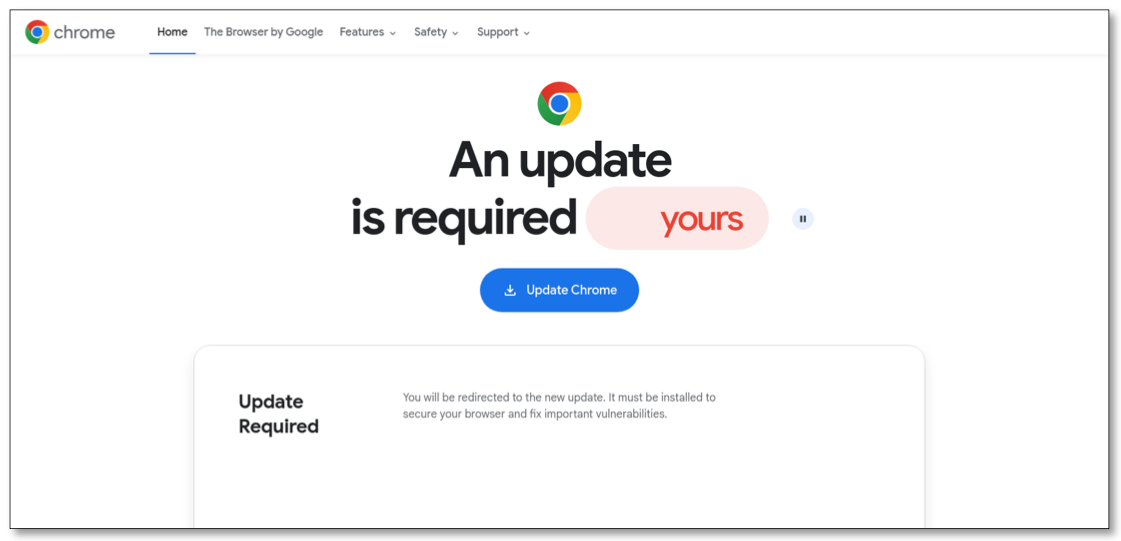
A fake browser update page pushing mobile malware. Image: Intrinsec.
BEARHOST prides itself on the ability to evade blocking by Spamhaus, an organization that many Internet service providers around the world rely on to help identify and block sources of malware and spam. Earlier this week, Spamhaus said it noticed that Prospero was suddenly connecting to the Internet by routing through networks operated by Kaspersky Lab in Moscow.
Update, March 1, 9:43 a.m. ET: In a written statement, Kaspersky said it is aware of the public claim about the company allegedly providing services to a “bulletproof” web hosting provider. Here is their full statement:
“Kaspersky denies these claims as the company does not work and has never worked with the service provider in question. The routing through networks operated by Kaspersky doesn’t by default mean provision of the company’s services, as Kaspersky’s automatic system (AS) path might appear as a technical prefix in the network of telecom providers the company works with and provides its DDoS services.”
“Kaspersky pays great attention to conducting business ethically and ensuring that its solutions are used for their original purpose of providing cybersecurity protection. The company is currently investigating the situation to inform the company whose network could have served as a transit for a “bulletproof” web hosting provider so that the former takes the necessary measures.”
Kaspersky began selling antivirus and security software in the United States in 2005, and the company’s malware researchers have earned accolades from the security community for many important discoveries over the years. But in September 2017, the Department of Homeland Security (DHS) barred U.S. federal agencies from using Kaspersky software, mandating its removal within 90 days.
Cybersecurity reporter Kim Zetter notes that DHS didn’t cite any specific justification for its ban in 2017, but media reports quoting anonymous government officials referenced two incidents. Zetter wrote:
According to one story, an NSA contractor developing offensive hacking tools for the spy agency had Kaspersky software installed on his home computer where he was developing the tools, and the software detected the source code as malicious code and extracted it from his computer, as antivirus software is designed to do. A second story claimed that Israeli spies caught Russian government hackers using Kaspersky software to search customer systems for files containing U.S. secrets.
Kaspersky denied that anyone used its software to search for secret information on customer machines and said that the tools on the NSA worker’s machine were detected in the same way that all antivirus software detects files it deems suspicious and then quarantines or extracts them for analysis. Once Kaspersky discovered that the code its antivirus software detected on the NSA worker’s machine were not malicious programs but source code in development by the U.S. government for its hacking operations, CEO Eugene Kaspersky says he ordered workers to delete the code.
Last year, the U.S. Commerce Department banned the sale of Kaspersky software in the U.S. effective July 20, 2024. U.S. officials argued the ban was needed because Russian law requires domestic companies to cooperate in all official investigations, and thus the Russian government could force Kaspersky to secretly gather intelligence on its behalf.
Phishing data gathered last year by the Interisle Consulting Group ranked hosting networks by their size and concentration of spambot hosts, and found Prospero had a higher spam score than any other provider by far.

AS209030, owned by Kaspersky Lab, is providing connectivity to the bulletproof host Prospero (AS200593). Image: cidr-report.org.
It remains unclear why Kaspersky is providing transit to Prospero. Doug Madory, director of Internet analysis at Kentik, said routing records show the relationship between Prospero and Kaspersky started at the beginning of December 2024.
Madory said Kaspersky’s network appears to be hosting several financial institutions, including Russia’s largest — Alfa-Bank. Kaspersky sells services to help protect customers from distributed denial-of-service (DDoS) attacks, and Madory said it could be that Prospero is simply purchasing that protection from Kaspersky.
But if that is the case, it doesn’t make the situation any better, said Zach Edwards, a senior threat researcher at the security firm Silent Push.
“In some ways, providing DDoS protection to a well-known bulletproof hosting provider may be even worse than just allowing them to connect to the rest of the Internet over your infrastructure,” Edwards said.




I wonder if the financial impact of restrictions on the “legitimate” AV business is a factor in branching out to… less legitimate ways of raising revenue?
This is a stupid question, but can’t we just cut Russia off from the public internet?
they’ll go through china, just like north korea.
So keep cutting?
yup. they are also now using proxies through Brazil, Turkey, Israel, and Belarus – as of February. Primarily Brazil though, it seems.
Important reporting. Is Eugene still at all in effective control of the company, I wonder. Of course when they force you to do the bidding of the ministry of X, you obviously can’t respond to western journalists seeking comment about it unless you fancy a swift window exit from the building. It will be interesting to see how this plays out.
Sounds like a “gag order” in the U.S.
Except in the US they don’t throw you out of the building, sure. Meanwhile US Cyber Command is being told to stand down and take Russia off the cyber threat list… nobody else, just Russia. Interesting times.
Suppose that is meant to read as your holiness has unfettered access to identified threats list, and an itemized notation detailing the addition and omission of each, and by whom
Sure.
KDP in KL-KDP stands for Kaspersky DDoS Protection. Hosted DDoS Protection services from Kaspersky Lab. As Prospero has legal entity (OOO) in Russia, they can be just commercial customer.
Hey Brian. I published a write-up on this topic six months ago.
https://aibaranov.github.io/kaspersky/
Threat actors abusing legit services … that’s incredible news, thank you for this article. Fortunately we can be sure it will never happen to good, western, trustworthy companies like cloudflare.
Well it’s specific actors on a specifically “antimalware” host that makes it a little more interesting than unknown actors using fragment routing or the like through cloudflare. Also it’s interesting that Kasp isn’t responding, is it not? What you’re doing is a form of whataboutism whether you intend that or not, and I hope not.
Hm I’m sure Kaspersky detecting the source code and maybe doing the same with NSA tools has nothing to do with it.
The leaps of logic in this are embarrassing and so are the comments. Where else does that law that private companies have to cooperate with government requests for BACKDOORS sound like? Just because Israel cracked Apples login for the FBI first I guarantee they will easily gain a court order either way. Easier to get too when you have an clear and present enemy propped up to fight like Russia.
I cut Kaspersky about 2020. I never used any of their services or products and was even wary of their alerts/news. Whew! Thanks.
I always wanted to know what that OOO was when I do geoiplookup. “LLC”, LOL, of all things.
Somebody asked if you could block Russia, but a better question is can you block off CIDR address spaces. Blocking off IPv4 address spaces is pretty easy at the server or firewall level. For IPv6 it gets a bit more complex. But why block off a country?
I’ve got years of server access logs in a mysql database, and as example, 91.202.0.0/16 and 91.215.0.0/16 come up 64 times since August 2022, with one nefarious attempt. Meaning 63/64 accesses from that 128K address space where status code 200, “OK”. That’s in close to a million rows, 2025 excluded. Sometimes it’s not worth messing with at the country level, as the miscreants are usually at the /24 level.
It’s much more common for this to happen to many other websites that are commonly used. The URL can say one thing but redirect somewhere else. It’s important to run the URL on a malware scanner if possible or to make sure the url is legit and the one intended.
I think that this article was very useful in terms of how important it is to implement cybersecurity strategies in the workplace. I rate it 10/10
#Ironic Mode On
I beleive this is a great company with great software from a great country. We should put this software again on the great american market, for our great companies. BTW with a greatest president of the world, ok, second greatest president, because the greatest i my greatest follower mr. Vladimir Putin, of course.
#Ironic Mode Off
How Droll
Someone help me here: Has Kaspersky gone over to the dark side, or are they still the Russian anomaly of a legit internet services company?
dark side not yet. K is reviewing the situation to. I hope they outlive putin. I used KL products up until RU staged their attack – because of putin, not because of the product. It is a great product. I used to get support from their US team out of Burlington MA (some for former NSA), good guys. We got stuck with MS Defender, the product is horrid, the support worse. They can’t even keep menus the same in their system. Reporting in MS Defender (intune) is like something out of the ’80’s. Gad I hate putin for making us use such a pathetic product, and the MS engineers that only add button in place of making a better product. We all know putin will kill anyone that defies him, I am surprised he hasn’t dragged their product down with him, yet. But I won’t use it while he is alive.
so valid. it’s very unfortunate for Kaspersky since I was also a fan before the aggression started.
The issue is that the Kremlin has the ability to compell cooperation from any company operating within their country, and as they have been targeting American businesses, activists, journalists, and govt officials with constant hacking attempts – we can safely assume they are, in fact, utilizing multinational companies to aid their efforts. Especially with regard to crypto theft and ransomware, which has singlehandedly crippled entire industries here.
IDK. How come one of the biggest companies on earth allows Russian entities to provide “enhancements” to its products?
Not even Hitler trusted them.
Of course Kaspersky denies everything 😀