A whistleblower at the National Labor Relations Board (NLRB) alleged last week that denizens of Elon Musk’s Department of Government Efficiency (DOGE) siphoned gigabytes of data from the agency’s sensitive case files in early March. The whistleblower said accounts created for DOGE at the NLRB downloaded three code repositories from GitHub. Further investigation into one of those code bundles shows it is remarkably similar to a program published in January 2025 by Marko Elez, a 25-year-old DOGE employee who has worked at a number of Musk’s companies.
According to a whistleblower complaint filed last week by Daniel J. Berulis, a 38-year-old security architect at the NLRB, officials from DOGE met with NLRB leaders on March 3 and demanded the creation of several all-powerful “tenant admin” accounts that were to be exempted from network logging activity that would otherwise keep a detailed record of all actions taken by those accounts.
Berulis said the new DOGE accounts had unrestricted permission to read, copy, and alter information contained in NLRB databases. The new accounts also could restrict log visibility, delay retention, route logs elsewhere, or even remove them entirely — top-tier user privileges that neither Berulis nor his boss possessed.
Berulis said he discovered one of the DOGE accounts had downloaded three external code libraries from GitHub that neither NLRB nor its contractors ever used. A “readme” file in one of the code bundles explained it was created to rotate connections through a large pool of cloud Internet addresses that serve “as a proxy to generate pseudo-infinite IPs for web scraping and brute forcing.” Brute force attacks involve automated login attempts that try many credential combinations in rapid sequence.
A search on that description in Google brings up a code repository at GitHub for a user with the account name “Ge0rg3” who published a program roughly four years ago called “requests-ip-rotator,” described as a library that will allow the user “to bypass IP-based rate-limits for sites and services.”
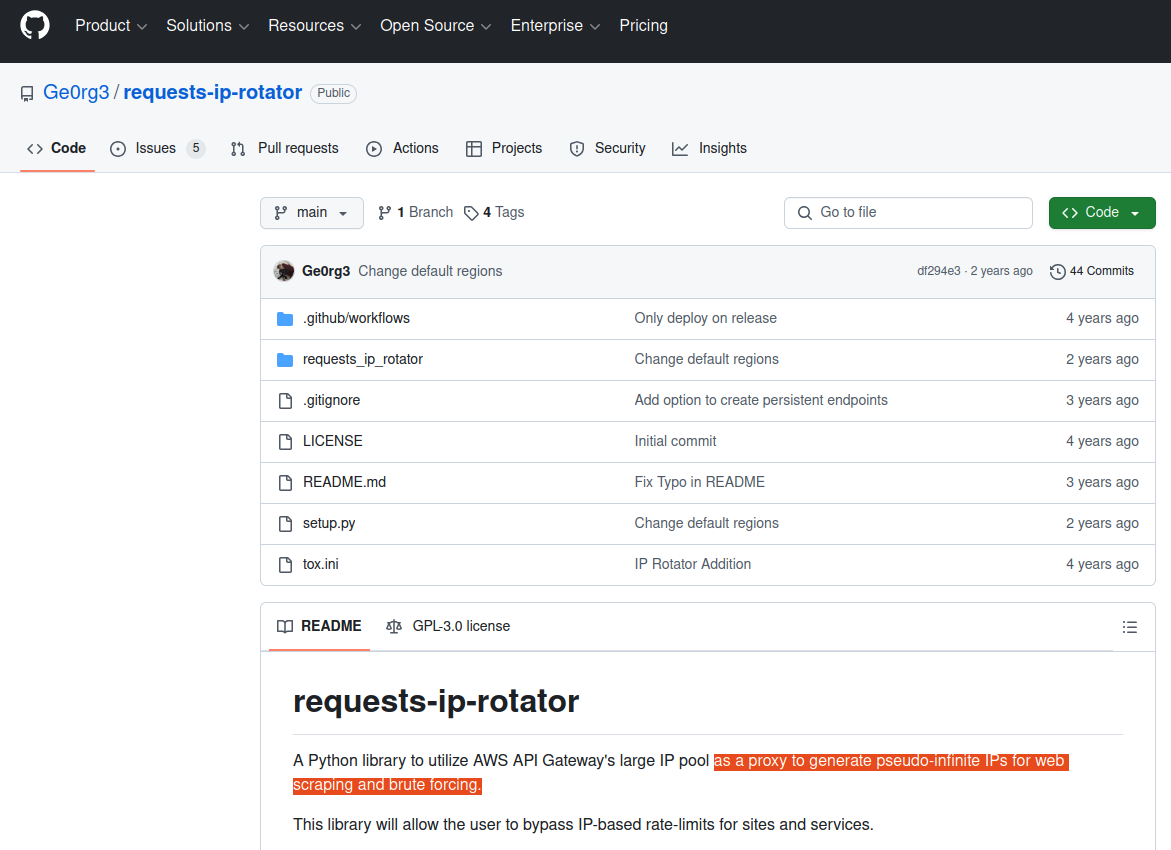
The README file from the GitHub user Ge0rg3’s page for requests-ip-rotator includes the exact wording of a program the whistleblower said was downloaded by one of the DOGE users. Marko Elez created an offshoot of this program in January 2025.
“A Python library to utilize AWS API Gateway’s large IP pool as a proxy to generate pseudo-infinite IPs for web scraping and brute forcing,” the description reads.
Ge0rg3’s code is “open source,” in that anyone can copy it and reuse it non-commercially. As it happens, there is a newer version of this project that was derived or “forked” from Ge0rg3’s code — called “async-ip-rotator” — and it was committed to GitHub in January 2025 by DOGE captain Marko Elez.

The whistleblower stated that one of the GitHub files downloaded by the DOGE employees who transferred sensitive files from an NLRB case database was an archive whose README file read: “Python library to utilize AWS API Gateway’s large IP pool as a proxy to generate pseudo-infinite IPs for web scraping and brute forcing.” Elez’s code pictured here was forked in January 2025 from a code library that shares the same description.
A key DOGE staff member who gained access to the Treasury Department’s central payments system, Elez has worked for a number of Musk companies, including X, SpaceX, and xAI. Elez was among the first DOGE employees to face public scrutiny, after The Wall Street Journal linked him to social media posts that advocated racism and eugenics.
Elez resigned after that brief scandal, but was rehired after President Donald Trump and Vice President JD Vance expressed support for him. Politico reports Elez is now a Labor Department aide detailed to multiple agencies, including the Department of Health and Human Services.
“During Elez’s initial stint at Treasury, he violated the agency’s information security policies by sending a spreadsheet containing names and payments information to officials at the General Services Administration,” Politico wrote, citing court filings.
KrebsOnSecurity sought comment from both the NLRB and DOGE, and will update this story if either responds.
The NLRB has been effectively hobbled since President Trump fired three board members, leaving the agency without the quorum it needs to function. Both Amazon and Musk’s SpaceX have been suing the NLRB over complaints the agency filed in disputes about workers’ rights and union organizing, arguing that the NLRB’s very existence is unconstitutional. On March 5, a U.S. appeals court unanimously rejected Musk’s claim that the NLRB’s structure somehow violates the Constitution.
Berulis’s complaint alleges the DOGE accounts at NLRB downloaded more than 10 gigabytes of data from the agency’s case files, a database that includes reams of sensitive records including information about employees who want to form unions and proprietary business documents. Berulis said he went public after higher-ups at the agency told him not to report the matter to the US-CERT, as they’d previously agreed.
Berulis told KrebsOnSecurity he worried the unauthorized data transfer by DOGE could unfairly advantage defendants in a number of ongoing labor disputes before the agency.
“If any company got the case data that would be an unfair advantage,” Berulis said. “They could identify and fire employees and union organizers without saying why.”

Marko Elez, in a photo from a social media profile.
Berulis said the other two GitHub archives that DOGE employees downloaded to NLRB systems included Integuru, a software framework designed to reverse engineer application programming interfaces (APIs) that websites use to fetch data; and a “headless” browser called Browserless, which is made for automating web-based tasks that require a pool of browsers, such as web scraping and automated testing.
On February 6, someone posted a lengthy and detailed critique of Elez’s code on the GitHub “issues” page for async-ip-rotator, calling it “insecure, unscalable and a fundamental engineering failure.”
“If this were a side project, it would just be bad code,” the reviewer wrote. “But if this is representative of how you build production systems, then there are much larger concerns. This implementation is fundamentally broken, and if anything similar to this is deployed in an environment handling sensitive data, it should be audited immediately.”
Further reading: Berulis’s complaint (PDF).
Update 7:06 p.m. ET: Elez’s code repo was deleted after this story was published. An archived version of it is here.




“insecure, unscalable and a fundamental engineering failure.”
Quick, someone cry politics and set yourself on fire.
What a mess. We’ll probably be hearing repeatedly the next few years how the “waste fraud and abuse” purposely and inadvertently excised/corrupted by DOGE from agency repositories turns out to have been the data integrity and security measures that serve and protect the US so long as government employees are there and not instructed from maintaining them.
Let’s put Musk in Mt Rushmore – with no food clothing or shelter – for a month or so before we deport him packed in the back of a self driving Tesla truck.
Spring 2025 – the apotheosis of anosognosia.
Obstructed not “instructed.”
“obstructed” not “instructed”
Thanks Brian
Obstructed not “instructed.”
I was fortunately able to look at the provided links before they were removed or made private. Incredible times in the industry and I appreciate the reporting Krebs!
imagine doing something this shady and leaving such an obvious paper trail. dude truly believes he is above the law, and unfortunately that belief has been reinforced by his higher-ups.
Speaking as a now-retired programmer and sr. Linux sysadmin, I’ve been referring to them almost since they appeared as hacker-wannabe. They’re *amateurs*, and that they’re being caught proves it.
Thanks, Brian
https://web.archive.org/web/20250423135719/https://github.com/markoelez/async-ip-rotator/issues/1
I found the archive link for the github issue: https://web.archive.org/web/20250423135719/https://github.com/markoelez/async-ip-rotator/issues/1
it’s a pretty thorough, but sound and level-headed review
It looks like some sort of LLM wrote that GitHub issue
I particularly like this quote from that evaluation;
“My original critique of your code addressed technical issues and provided solutions, but after learning about your expressed views, it’s clear that poor coding isn’t the root problem here. Your mindset is incompatible with the fundamental values of IT: collaboration, respect, and global interconnectedness.”
Sounds very much like the recruiting requirements of a DOGE psychophant.
Puts the finger in the right spot. You must be a special kind of person to do something like this. Probably just as narcistic as a lot of others in the current administration.
Looks like the “async-ip-rotator” Github page has been deleted now.
Please use archive.org links, looks like the GitHub stuff got taken down.,
So he downloaded a public open-source project and forked it. What’s the problem?
Reading comprehension apparently…
Seriously? You don’t see anything questionable in his actions.
If he didn’t believe he was doing anything nefarious, then why wouldn’t he have just used his own forked repo. But he didn’t. He used the upstream repo he forked from.
But wait, there’s more. He then goes and deletes his fork after this story is published to try and cover his tracks. 🙂
Doh. The OpSec is definitely not strong in this one.
Obviously he’s a misunderstood forking genius.
Marko “Forks” Elez is a great example of how churning out mid-tier Python code and being male can bring you to some crazy places in life. Side note, if you want to bore yourself to sleep tonight, take a walk down Elez’s recent GitHub repos. At least Big Balls is exciting–hosting VPS’s for cybercriminal gangs and being an alleged hacking forum kiddie. Elez in comparison just comes off like a sad, boring racist.
Roast aside, One important point to note related to the flaming GitHub issue: This repo was forked from “Ge0rg3” so a lot of the code was not authored by Elez, but rather “Ge0rg3”. Due to this, the only critique point pointed at Elez is #3. The remainder of the critique points are to be pointed at “Ge0rg3”.
Forking a repo is a lot like choosing the DNA for your next baby. You’re choosing an architecture, pattern, tooling–everything, and building from it. Elez, a eugenicist, selectively breeding a repo with really objectively bad code (traits), is either A) ironic and/or B) demonstrates lack of software engineering experience and/or C) demonstrates a disconnect between his values and his actions.
That certainly begs the question: “Why do they have tenant-level access to such sensitive US government data?”
This is such an hilarious take it made me laugh til I blew snot bubbles.
I could not agree with you more. They are just lost little boys seeking ill-perceived validation from their fascist heroes. The sad thing is, the moment they prove to be a liability, they get thrown to the wolves. Go figure.
Why would mananagement allow unlimited tenant-level access without a posibility of monitoring it? How can you ever agree to such a thing?
Opinions are like the author of this rubbish, of course, everyone has one. While we’re forensically auditing, there is no evidence the code was implemented, ever run, deployed, etc. How convenient for the author “tenant admin” accounts were added for DOGE. If the same level of concern was distributed evenly, let’s talk about the level of corruption rife across all of government. Lost interest? meh, same for this smoke but no fire articles picked up by Reuters, PBS, and NPR in my news feed. NLRB? are you kidding me, they revise their numbers based on politics. BTW, names and payments aren’t PII, your name is public information despite “policy”, same root word as politics. I suppose those who oppose Trump condone the corruption including election fraud. Go forensic audit that.
I agree with your BTW statement, names associated to payments is Non Public Information (NPI) not PII (to be pedantic). NPI is generally considered more sensitive than PII and requires higher safeguards. Regardless, the issue of creating superuser accounts with access to logging / auditing functions violates basic tenants of Cybersecurity for Least Privilege and Segmentation of Trust. I demand auditability from my government regardless who is in charge or if local, state, or federal.
Hi Alfred-
Your comments are all over the place, but you seem to not believe the data is sensitive. The article clearly explains why it’s sensitive, but basically is contains “information about employees who want to form unions and proprietary business documents.” Also, SpaceX has been suing the NLRB.
If you’re anti-union, and I’d wager a lot of money you are, then perhaps you don’t care about misuse of this data. That’s besides the point. Nobody seems to know what DOGE is going to do with this data. The fact that DOGE covered it’s tracks regarding the data transfer should be profoundly disturbing. If you believe that DOGE should operate above the law without any transparency or oversight into its activities, then I’m not sure what to say.
Please give examples of corruption “rife” across the government, and election fraud. Based on this regime’s view, the 2024 election was perfectly fair compared to 2020, which showed no evidence of election fraud. There still is no evidence of “corruption” in any of the departments/agencies “audited” (I’d prefer ransacked), by DOGE or the administration. Just because something does not follow the agenda does not mean its “corruption”.
Information is contextually based, where confidentiality is based on the consequences of the exposure of it. It’s clearly explained in the article the concerns/consequences if some of the information exfiltrated was exposed. It shows you didn’t read this article and took it at face value. Your statement about PII is wrong. PII stand for Personally Identifiable Information. Your name is certainly PII. I think you are confusing the term NPPI (Non-Public Private Information).
Politics aside, these actions are concerning for a number of reasons. It’s the fact these tenant account accounts were made, without any kind of accountability, especially since they are super-privileged accounts. This is a big no-no in cyber-security, logging is everything, and the integrity of those logs is even more important. Lastly, I see your point regarding the code never being implemented, ever run, etc. However, in government environments, and in most enterprise environments, code & software go through an evaluation process (3rd party risk management). This is to justify business use cases, potential risks, and address security concerns of dependencies in the program or code usage (not limited to this list, just some examples of steps in the process). The fact he even downloaded this software is a cause for concern, especially having the permissions he does. Granted, there is still no evidence showing it was ever run. Speculating though, it is certainly possible he deleted the evidence of him running it.
Spewing Fox News propaganda doesn’t change the fact there are processes for things, even if there was/is corruption (which I doubt). Those processes are there to maintain an adequate cybersecurity posture, against sophisticated foreign and domestic threat actors. DOGE here (and in many other cases) has a blatant disregard for this. There are already several examples of cyber-security leaks/incidents and dubious actions as a result of DOGE and this administration.
This is a long-winded reply, you probably won’t read this, and there is a high chance you’re a bot. But I felt it was a good brain-exercise, to explain why everything you said was wrong. Right or left, what’s happening here, isn’t right and as cyber-professionals we have ethical obligations we have to follow, regardless of politics.
Brian, keep up the good reporting. I look forward to new information about this possible/likely incident. Feel free to correct anything I have said here.
Ah, the classic deflection cocktail — a dash of whataboutism, a splash of conspiracy, and a whole lot of misunderstanding how security actually works.
Let’s clear a few things up: the fact that the code existed, especially written by someone with tenant admin access, is already a massive security failure. In cybersecurity, you don’t wait for the detonation to call something a bomb. The intentional development and concealment of code that could potentially exfiltrate data or enable surveillance is grounds for immediate investigation, regardless of whether it was “run” or “deployed.” That’s Security 101.
Saying “there’s no evidence it was used” misses the point entirely. If you find a backdoor welded into your server rack, you don’t go “meh, well nobody walked through it yet.” You tear it out, audit everything, and start asking very hard questions.
Also, on the “names and payments aren’t PII” comment — that’s just wrong. Names in context — especially tied to internal systems, credentials, payments, or whistleblower activity — can absolutely constitute sensitive information, legally and operationally. That’s why we have data classification policies, not political slogans.
This isn’t about left, right, or center. It’s about trust, accountability, and basic operational security. If we’re shrugging off insider code with admin rights because it wasn’t yet exploited, we’re in way deeper trouble than one article can cover.
Well put.
If there was nothing wrong and everything is above board, why are they working to hide/delete the evidence?
abcnews.go.com/Politics/hegseth-signal-app-connected-dirtly-line-computer-pentagon/story?id=121142551
Why indeed.
Da, author of rubbish comrade, excellent whataboutism and attempt to change the subject.
You’re the next Secretary of Stale.
The point of this story is evidence supporting a NLRB whistleblower’s complaint about DOGE having fundamental security controls disabled and transferring NLRB case data to an unknown site for unknown purposes in the face of DOGE denials. Thank you, Brian.
After reading Brian’s original story on this topic, I wrote my Senator to advocate that the complaint be investigated seriously and thoroughly. The issue shouldn’t be about politics. Whether you are a fan or foe of DOGE, I would think everyone across the political spectrum would want transparency as to its activities and understand the need to diligently protect sensitive data. I would also hope that everyone would find the account of the whistleblower being harassed profoundly disturbing and requiring further investigation.
I’ll say it again, but the network activity from Russia is a red herring. The real issue is DOGE having standard security controls disabled on a system that stores sensitive data and then transferring sensitive data to an unknown location with unknown data protection for unknown purposes.
Original story: https://krebsonsecurity.com/2025/04/whistleblower-doge-siphoned-nlrb-case-data/
“but the network activity from Russia is a red herring” – Well maybe, but a “red herring” is something you put in to deliberately throw people off what’s important to be obfuscated. In this case a “Russian” IP tried to access sensitive systems using DOGE credentials mere minutes after they were created. Valid ones. It wasn’t brute forced. We don’t have any information yet beyond that fact, but it seems to me if you’ve got credentials being given to DOGE for unfettered access to a sensitive system, (which you cede is the ‘main’ part of this) and 15 minutes later someone “in Russia” (or even someone with a VPN pretending to be) is using those exact brand new credentials in attempting to gain access… I’d say that’s a material fact and not something you can just shrug off as unrelated or unimportant. Either the DOGE agent is rooted, the DOGE agent willingly is transmitting those credentials to a 3rd XYZ party, potentially in Russia, or someone on the extremely short list with access to those credentials is trying to make it ‘look like’ ‘Russia’ is attempting access – presumably for the point of making the situation look even more serious and drawing more scrutiny. In all three scenarios that’s a very real problem that needs solved – immediately. Like you say it’s important that the data was stolen, but each step of proving how/what/where/why/who is potentially as important as the next. It’s like saying “the Prime Minister was shot, the smoking gun is just a red herring.” Agree to disagree on that.
Alfred Barnes
Why do people delete code the minute they read about it in an article like this?
Democrats for Waste! They hate DOGE because the apparatchiks don’t want their cheese moved.
Possibly, but irrelevant. Auditing should be maintained to understand what cheese is moved where.
Serious question, can Republicans still read? Do they just find it too much work?
Derps for reading! They hate investigations into infosec breaches because … wait, why DO they hate that?
MAGAts are about to flock to this comment section to “own the libs” even if it means their data is compromised
And the libs are jumping at the chance to prove Elon is a Russian operative that sent all our data over to Russia. A low-level NLRB employee, that has been there less than a year cries wolf and you don’t even wait until any of it has been proven.
“the libs” lol, you’ve already removed your pants. You’re not presenting any (credible or otherwise) alternative to the facts by saying “it’s unproven” – obviously Krebsonsecurity is not a court of law, prosecutor nor judge, but an investigatory journalist. If you have any concept of how investigations work, (ha.) you don’t start out by “proving” the case. You start out by investigating the case, and it often takes a long time to get to “proof” sufficient to call it that. (Still with me, illiterate?)
If you refuse to even READ into the investigation and the “proven” facts of the case thus far before forming an opinion that it’s all “hoaxgate” or whatever mental box you information-diode lizard-brains put anything remotely political-adjacent in the Trump era, why should anyone care if you’re convinced, unconvinced, or setting himself on fire in protest preemptively?
Nobody cares what you refuse to read, but why comment when you obviously have zero insights whatsoever?
The entire _point_ of the site is to read the information, then share insights. You blew it. Start over.
You’re right, nobody should at all investigate until we’ve proven there’s something to investigate.
Derp.
Please – stick to Security issues? Do not become Politicized.
Great Security site – until it goes woke :(.
Did you fail to read the article about the Security issue somehow? What did you read instead?
Let’s be clear: this is a security issue. When a federal agency like DOGE creates privileged accounts with no oversight, disables logging, and pulls in code libraries from GitHub that resemble tools used for brute-forcing and scraping — inside the National Labor Relations Board, no less — that’s not just misconfiguration. That’s potential weaponization of insider access against citizens and institutions.
And if your response is “don’t get political,” let me put it bluntly:
If you can’t recognize this as a security issue, you have no business being in security.
Security isn’t just firewalls and CVEs. It’s about integrity, accountability, and trust in the systems that handle sensitive data. When those systems are compromised from the inside — especially by individuals tied to powerful political interests — that’s a security red flag the size of the sun.
This isn’t “going woke.” It’s staying awake. If you’re more offended by Krebs covering abuse of power than by actual abuse of privileged access, then maybe you’re the one politicizing things.
Security without ethics is surveillance. And “don’t go woke” is not a rebuttal — it’s a deflection.
Well articulated. I concur.
Steve’s other comments really capture the truth of my feelings on this so I’ll just say +1 to everything he stated. I’m completely apolitical to be honest.
In addition, from my point of view, this is about a (potential) fundamental failure to adhere to basic auditing and zero-trust principles. That is the core transgression. Everything else is just the effects of that failure and secondary issues.
As expected with his reporting, Brian again did an entirely independent investigation in this matter and thought of so many angles I had not considered. I think it’s vital that he did so in order to call into light the seeming lack of accountability without making assumptions to simply try to bring the issue into focus enough that a better audit can be requested. The more eyes that look, the more truth that will come out, and will lead to a better outcome for everyone involved.
– Daniel