Late last year, security researchers made a startling discovery: Kremlin-backed disinformation campaigns were bypassing moderation on social media platforms by leveraging the same malicious advertising technology that powers a sprawling ecosystem of online hucksters and website hackers. A new report on the fallout from that investigation finds this dark ad tech industry is far more resilient and incestuous than previously known.

Image: Infoblox.
In November 2024, researchers at the security firm Qurium published an investigation into “Doppelganger,” a disinformation network that promotes pro-Russian narratives and infiltrates Europe’s media landscape by pushing fake news through a network of cloned websites.
Doppelganger campaigns use specialized links that bounce the visitor’s browser through a long series of domains before the fake news content is served. Qurium found Doppelganger relies on a sophisticated “domain cloaking” service, a technology that allows websites to present different content to search engines compared to what regular visitors see. The use of cloaking services helps the disinformation sites remain online longer than they otherwise would, while ensuring that only the targeted audience gets to view the intended content.
Qurium discovered that Doppelganger’s cloaking service also promoted online dating sites, and shared much of the same infrastructure with VexTrio, which is thought to be the oldest malicious traffic distribution system (TDS) in existence. While TDSs are commonly used by legitimate advertising networks to manage traffic from disparate sources and to track who or what is behind each click, VexTrio’s TDS largely manages web traffic from victims of phishing, malware, and social engineering scams.
BREAKING BAD
Digging deeper, Qurium noticed Doppelganger’s cloaking service used an Internet provider in Switzerland as the first entry point in a chain of domain redirections. They also noticed the same infrastructure hosted a pair of co-branded affiliate marketing services that were driving traffic to sketchy adult dating sites: LosPollos[.]com and TacoLoco[.]co.
The LosPollos ad network incorporates many elements and references from the hit series “Breaking Bad,” mirroring the fictional “Los Pollos Hermanos” restaurant chain that served as a money laundering operation for a violent methamphetamine cartel.

The LosPollos advertising network invokes characters and themes from the hit show Breaking Bad. The logo for LosPollos (upper left) is the image of Gustavo Fring, the fictional chicken restaurant chain owner in the show.
Affiliates who sign up with LosPollos are given JavaScript-heavy “smartlinks” that drive traffic into the VexTrio TDS, which in turn distributes the traffic among a variety of advertising partners, including dating services, sweepstakes offers, bait-and-switch mobile apps, financial scams and malware download sites.
LosPollos affiliates typically stitch these smart links into WordPress websites that have been hacked via known vulnerabilities, and those affiliates will earn a small commission each time an Internet user referred by any of their hacked sites falls for one of these lures.
The Los Pollos advertising network promoting itself on LinkedIn.
According to Qurium, TacoLoco is a traffic monetization network that uses deceptive tactics to trick Internet users into enabling “push notifications,” a cross-platform browser standard that allows websites to show pop-up messages which appear outside of the browser. For example, on Microsoft Windows systems these notifications typically show up in the bottom right corner of the screen — just above the system clock.
In the case of VexTrio and TacoLoco, the notification approval requests themselves are deceptive — disguised as “CAPTCHA” challenges designed to distinguish automated bot traffic from real visitors. For years, VexTrio and its partners have successfully tricked countless users into enabling these site notifications, which are then used to continuously pepper the victim’s device with a variety of phony virus alerts and misleading pop-up messages.
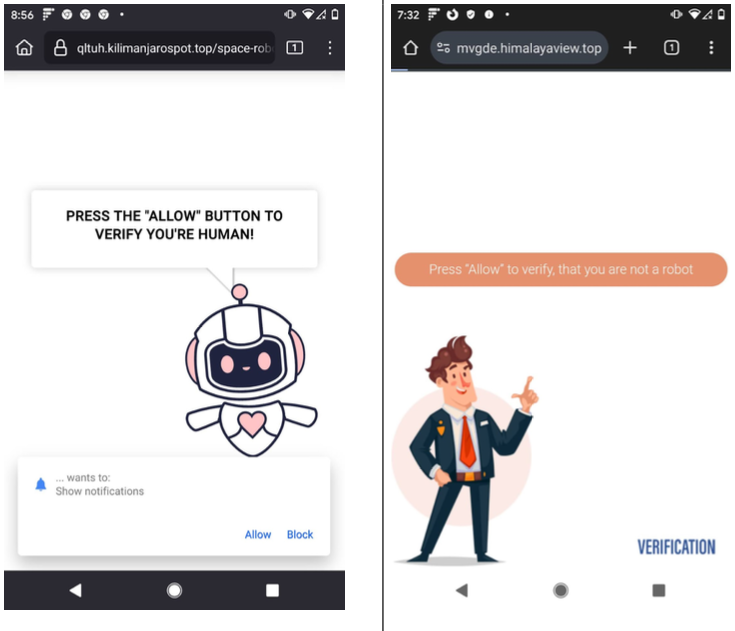
Examples of VexTrio landing pages that lead users to accept push notifications on their device.
According to a December 2024 annual report from GoDaddy, nearly 40 percent of compromised websites in 2024 redirected visitors to VexTrio via LosPollos smartlinks.
ADSPRO AND TEKNOLOGY
On November 14, 2024, Qurium published research to support its findings that LosPollos and TacoLoco were services operated by Adspro Group, a company registered in the Czech Republic and Russia, and that Adspro runs its infrastructure at the Swiss hosting providers C41 and Teknology SA.
Qurium noted the LosPollos and TacoLoco sites state that their content is copyrighted by ByteCore AG and SkyForge Digital AG, both Swiss firms that are run by the owner of Teknology SA, Giulio Vitorrio Leonardo Cerutti. Further investigation revealed LosPollos and TacoLoco were apps developed by a company called Holacode, which lists Cerutti as its CEO.
The apps marketed by Holacode include numerous VPN services, as well as one called Spamshield that claims to stop unwanted push notifications. But in January, Infoblox said they tested the app on their own mobile devices, and found it hides the user’s notifications, and then after 24 hours stops hiding them and demands payment. Spamshield subsequently changed its developer name from Holacode to ApLabz, although Infoblox noted that the Terms of Service for several of the rebranded ApLabz apps still referenced Holacode in their terms of service.
Incredibly, Cerutti threatened to sue me for defamation before I’d even uttered his name or sent him a request for comment (Cerutti sent the unsolicited legal threat back in January after his company and my name were merely tagged in an Infoblox post on LinkedIn about VexTrio).
Asked to comment on the findings by Qurium and Infoblox, Cerutti vehemently denied being associated with VexTrio. Cerutti asserted that his companies all strictly adhere to the regulations of the countries in which they operate, and that they have been completely transparent about all of their operations.
“We are a group operating in the advertising and marketing space, with an affiliate network program,” Cerutti responded. “I am not [going] to say we are perfect, but I strongly declare we have no connection with VexTrio at all.”
“Unfortunately, as a big player in this space we also get to deal with plenty of publisher fraud, sketchy traffic, fake clicks, bots, hacked, listed and resold publisher accounts, etc, etc.,” Cerutti continued. “We bleed lots of money to such malpractices and conduct regular internal screenings and audits in a constant battle to remove bad traffic sources. It is also a highly competitive space, where some upstarts will often play dirty against more established mainstream players like us.”
Working with Qurium, researchers at the security firm Infoblox released details about VexTrio’s infrastructure to their industry partners. Just four days after Qurium published its findings, LosPollos announced it was suspending its push monetization service. Less than a month later, Adspro had rebranded to Aimed Global.
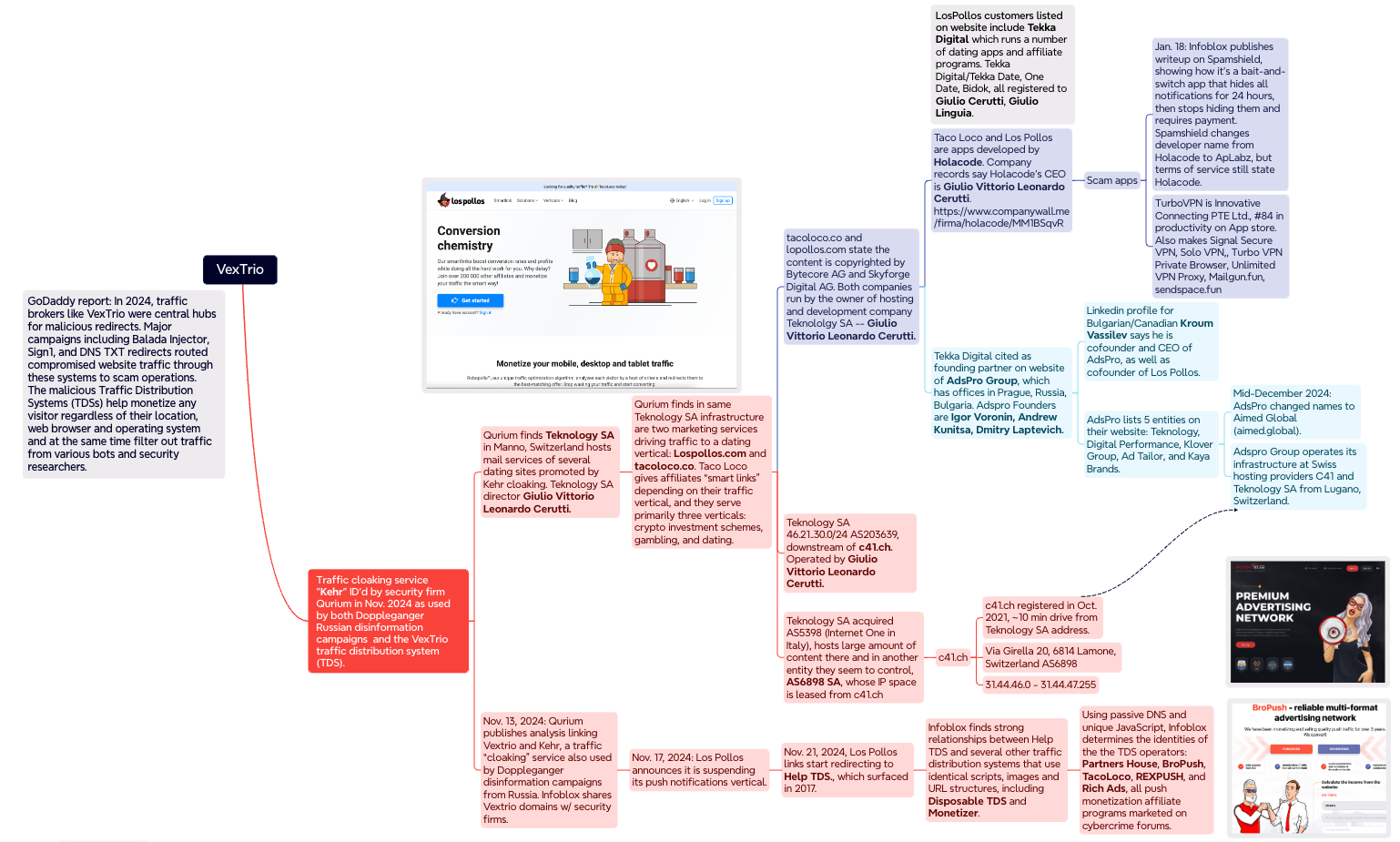
A mind map illustrating some of the key findings and connections in the Infoblox and Qurium investigations. Click to enlarge.
A REVEALING PIVOT
In March 2025, researchers at GoDaddy chronicled how DollyWay — a malware strain that has consistently redirected victims to VexTrio throughout its eight years of activity — suddenly stopped doing that on November 20, 2024. Virtually overnight, DollyWay and several other malware families that had previously used VexTrio began pushing their traffic through another TDS called Help TDS.
Digging further into historical DNS records and the unique code scripts used by the Help TDS, Infoblox determined it has long enjoyed an exclusive relationship with VexTrio (at least until LosPollos ended its push monetization service in November).
In a report released today, Infoblox said an exhaustive analysis of the JavaScript code, website lures, smartlinks and DNS patterns used by VexTrio and Help TDS linked them with at least four other TDS operators (not counting TacoLoco). Those four entities — Partners House, BroPush, RichAds and RexPush — are all Russia-based push monetization programs that pay affiliates to drive signups for a variety of schemes, but mostly online dating services.
“As Los Pollos push monetization ended, we’ve seen an increase in fake CAPTCHAs that drive user acceptance of push notifications, particularly from Partners House,” the Infoblox report reads. “The relationship of these commercial entities remains a mystery; while they are certainly long-time partners redirecting traffic to one another, and they all have a Russian nexus, there is no overt common ownership.”
Renee Burton, vice president of threat intelligence at Infoblox, said the security industry generally treats the deceptive methods used by VexTrio and other malicious TDSs as a kind of legally grey area that is mostly associated with less dangerous security threats, such as adware and scareware.
But Burton argues that this view is myopic, and helps perpetuate a dark adtech industry that also pushes plenty of straight-up malware, noting that hundreds of thousands of compromised websites around the world every year redirect victims to the tangled web of VexTrio and VexTrio-affiliate TDSs.
“These TDSs are a nefarious threat, because they’re the ones you can connect to the delivery of things like information stealers and scams that cost consumers billions of dollars a year,” Burton said. “From a larger strategic perspective, my takeaway is that Russian organized crime has control of malicious adtech, and these are just some of the many groups involved.”
WHAT CAN YOU DO?
As KrebsOnSecurity warned way back in 2020, it’s a good idea to be very sparing in approving notifications when browsing the Web. In many cases these notifications are benign, but as we’ve seen there are numerous dodgy firms that are paying site owners to install their notification scripts, and then reselling that communications pathway to scammers and online hucksters.
If you’d like to prevent sites from ever presenting notification requests, all of the major browser makers let you do this — either across the board or on a per-website basis. While it is true that blocking notifications entirely can break the functionality of some websites, doing this for any devices you manage on behalf of your less tech-savvy friends or family members might end up saving everyone a lot of headache down the road.
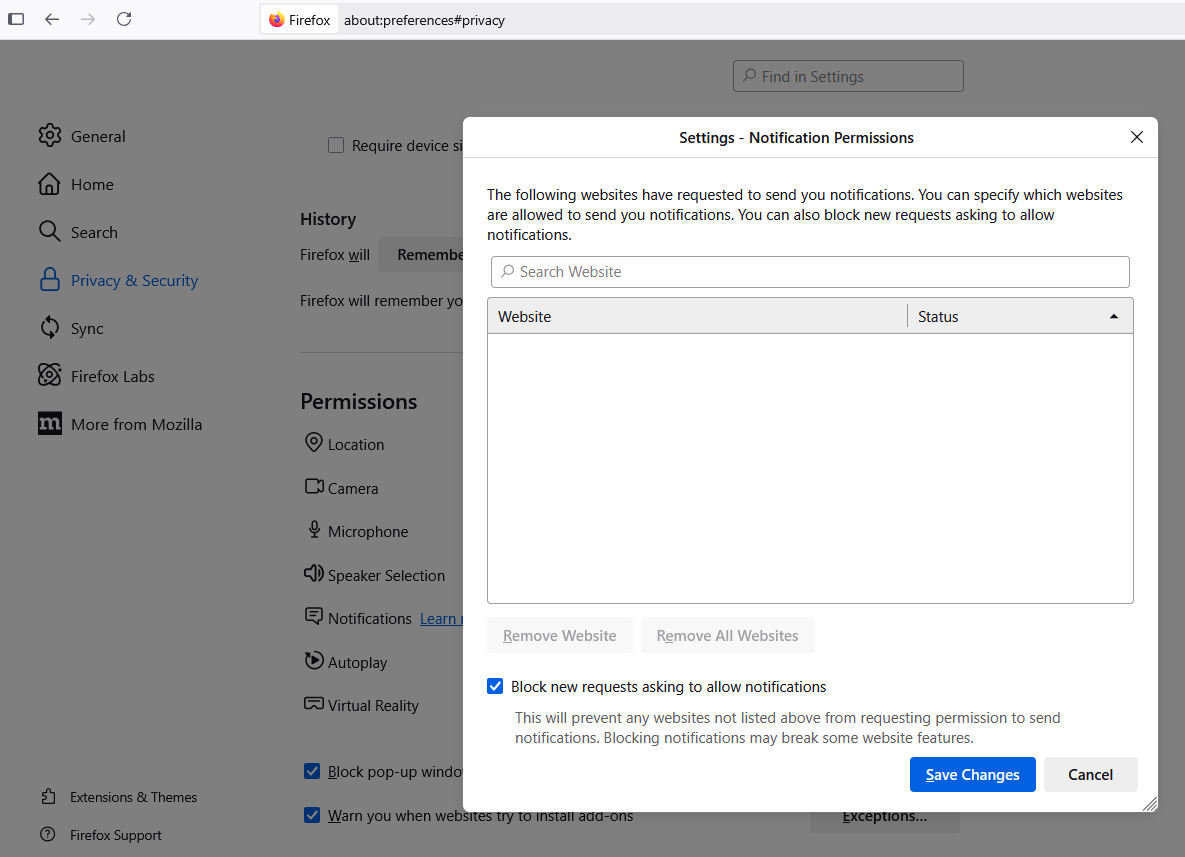
To modify site notification settings in Mozilla Firefox, navigate to Settings, Privacy & Security, Permissions, and click the “Settings” tab next to “Notifications.” That page will display any notifications already permitted and allow you to edit or delete any entries. Tick the box next to “Block new requests asking to allow notifications” to stop them altogether.
In Google Chrome, click the icon with the three dots to the right of the address bar, scroll all the way down to Settings, Privacy and Security, Site Settings, and Notifications. Select the “Don’t allow sites to send notifications” button if you want to banish notification requests forever.
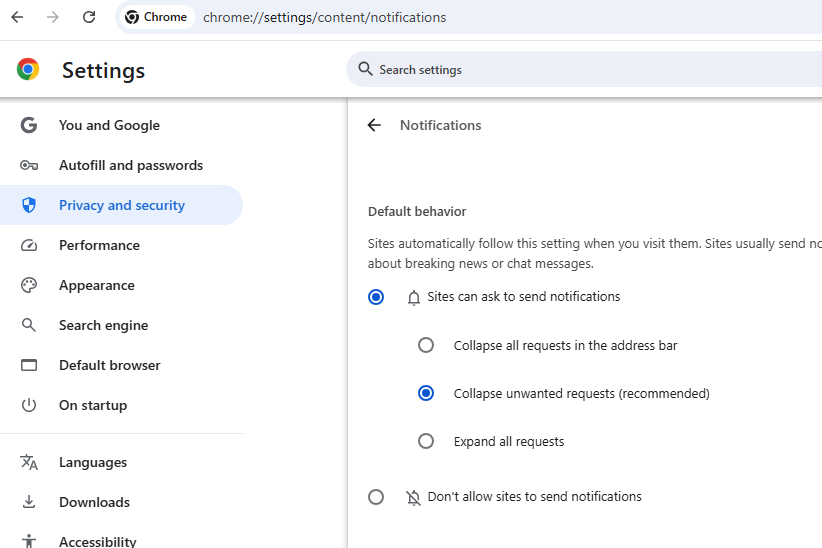
In Apple’s Safari browser, go to Settings, Websites, and click on Notifications in the sidebar. Uncheck the option to “allow websites to ask for permission to send notifications” if you wish to turn off notification requests entirely.




‘Less than a month later, Adspro had rebranded to Aimed Global.’
It does not matter how much you polish a turd, it is still a piece of sh*t.
Nora is fake.
Apologies for the pedantry, but “Breaking Bad” was an AMC series, not HBO. Obviously a minor error, but even small errors then allow others to call more important and well research points into question.
“but even small errors then allow others to call more important and well research points into question.”
That’s really not how ‘well-researched points’ are questioned. A single noted ‘error’ anyhow.
(HBO also openly runs licensed AMC content after the original premier run.)
wikipedia.org/wiki/Faulty_generalization#Hasty_generalization
wikipedia.org/wiki/Jumping_to_conclusions
I use Vivaldi, in part because of its Security settings for notifications.
Me, too!!
> Guilio Vitorrio Leonardo Cerutti
I believe you have typos there, it probably is:
Giulio Vittorio Leonardo Cerutti.
I never understood this trend of just about every second website (including clearly legitimate ones) now asking me to allow push notifications. To me this comes across as plain ridiculous, tasteless and greedy. Just imagine going to a shop in person, and them asking if it is OK if they send people to “visit” you at your home address.
Or just ‘sending’ people there, claiming your shoe brand offered some sort of waiver.
Creepy.
When notification functionality arrived in web browsers – I disabled it immediately and I’m doing so for my loved ones 😉
USA say Russia make fake news
The land of genocide maker
Mongo only pawn in game of news analysis.
Russian notifications??
Yes
Mongo take chance!
Thanks for smartening us up, Brian.
I feel smartened more and more every day also by the amazing job that Brian Krebs is doing as a Dark AdTech Empire Fed.
I always set my browsers (and those of most of my clients) to block all notification requests. But I’ve noticed that doesn’t actually block ALL notifications. This definately happens on Chrome and I think, perhaps, on Firefox as well. I don’t recall what the situation is with Brave, as I only use that under certain circumstances. I haven’t taken the time to research it further, since I dismiss all of the requests that sneak through no matter what.
Anyone have an idea of what might be happening here? Thank you in advance.
There could be any number of reasons for persistent notification behaviour ranging from;
Existing permissions already being granted, i.e. Blocking new notification requests doesn’t revoke permissions already given in the past. These can persist across browser profiles or sessions unless you manually audit and clear them.
To, malicious extensions or notification hijacking, i.e. A browser extension (especially an adblocker, coupon tool, or shopping assistant) may inject scripts or register notification permissions under the hood. Run in incognito or safe mode to see if the issue persists. Heavier infections might require a fresh OS install/rebuild.
While disabling notifications across the board is the best option (and practical for managing other people’s devices), you can take several other layered and less intrusive actions.
For the average home user, extensions such as uBlock Origin, NoScript, PushBlock and Decentraleyes/LocalCDN can help track and manage unwanted scripts.
Or for the more tech savvy network-based filtering using services like NextDNS, AdGuard DNS, or Pi-hole to prevent known malicious push domains from resolving.
But most importantly of all is end user behaviour. Teach users to:
Never click “Allow” on notification requests unless they intentionally initiated the interaction.
Recognise fake CAPTCHA behaviour: real CAPTCHAs don’t ask for notifications.
Check notification permissions periodically in browser settings.
Use the lock icon in the address bar to manage site-specific permissions.
Thanks. But I’m already aware of all that and unfortunately it still doesn’t block every request. No biggie. I simply click it off or let it go away. But very good advice in general
Cheers.
I just reread my comment and there is a huge error. I meant to say it doesn’t necessarily stop All REQUESTS for notifications. Sorry for any confusion.
> Those four entities — Partners House, BroPush, RichAds and RexPush — are all Russia-based
They all are Ukranians, tbh
It’s the same, Nora
Nora is a fake person. There is impersonation here.
Please, stop responding to this troll.
Oh , have a Fanta. They still make it in orange and grape.
Both flavors contain neither fruit. Apt comparison.
Stop responding to “Nora.” It is a troll.
Yes, they are.
Nora was right twice today.
Nora is a fake person. Stop responding.
Stop replying to “Nora”.
It is a scammer.
“Those four entities — Partners House, BroPush, RichAds and RexPush — are all Russia-based
They all are Ukranians, tbh”
It was written by a scammer. The real name of this person is not Nora. There is a bot or a Russian man behind it.
Dont’ forget BRAVE browser….
People seem to keep recommending that browser and while I wouldn’t say it’s much worse than any of the other browsers out there, I’m not sure it’s much better than any of the other ones out there either (though Opera is far too bloated now, Chrome has gotten sorta crazy (especially with Peachy thinking he is the sudo Charles Xavier of the tech world), and Firefox has an issue with using words like Quantum the wrong way. DuckDuckGo isn’t totally bad but has its own issues. I haven’t seen a decent browser that’s much better than any of the others since before Puffin went to the cloud.
Not sure why you’re recommending Brave (Disney fan??) any more than Brian used to recommend Puppy Linux years ago. I think people just seem to fixate on names as magic shields, and they aren’t.
Unrelated: Hey, Brian, you ever wonder what happened to all of those little pieces of Conficker that are still probably out there in the void somewhere? Was thinking about it earlier today. Someone mentioned 2004 and got me thinking.
“… wants to: Show notifications” in your screenshot there is a red flag. It should be showing the domain. I think browsers only do that when there’s some question about the domain. (3rd party service or similar…)
“sketchy adult dating sites: LosPollos”
What the fruit is an “adult dating site”? I see that in the infographic at the top too. It sounds from the next section like LosPollos is an advertising network? The article also says “Doppelganger’s cloaking service also promoted online dating sites”, which makes me think like Grindr or OK Cupid, which sure are sketchy but I don’t think are like malware level of sketchy. Is it that kind of “dating” site, in which case what’s “adult” getting at beyond just typical dating sites? Or is it a slang term I don’t know?
Its a fake dating site where men chat with fake women, the point is to get the men to pay for credits so they can continue chatting
How are those push notifications not disabled by default in beyond me?
I am not sure about Chrome, as I stopped using it after it became a bloated dumpster dive of a web browser since it changed its extension model to disable ad blockers. But Firefox too? Really.
I just got hit with nonsense on my laptop two days ago. Alerts were turned off. New alerts started popping up in the lower left corner offering antivirus services. Couldn’t stop them. Minutes later Windows Defender did what it’s supposed to and the nonsense was eliminated. Ran other scans just to make sure, had the tech at work check it and all is well. During this episode, Microsoft Edge was running at 100% and I couldn’t terminate the service. I feel foolish that I fell for the scam.
I was going to be snarky and say “people still use edge?” but I know they do.
The tech guy at work even swears by it sometimes.
Swears by it or swears at it?
I wasn’t clear….Edge started running in the background (task manager and process hacker) without any actions on my part. I use Vivaldi or Brave.
The simplest way to remove all of Microsoft’s tentacles is Chris Titus’s Windows Utility Tool here;
https://github.com/ChrisTitusTech/winutil
Add/change/customise features and settings at a single click, bulk install/update programs from the Winget repository. Tweak Security and Power profiles. Disable Microsoft’s unwanted bloat like Telemetry, Copilot and Location Tracking, you can even remove Edge and OneDrive.
Thank-you!
Thank-you for the information!
You’re welcome.
Nora is fake.
Script Blocker.
Because websites and the browsers that read them have been a hellscape since… I dunno, the late 90’s or so.
agree 100% sometimes a pain but better than the problems not using it causes
Before you trust in any browser, open a window running something like EtherApe and watch for a few minutes. That is why many times its safer to use a text browser like Elinks, where possible…
Excellent expose on how fake CAPTCHA schemes and push-notification abuse are being weaponized via cloaking networks. At COE Security, we’ve observed similar malicious domain rotations paired with telemetry-triggered endpoint locks that effectively interrupt browser-to-C2 redirections. In recent tests, this method reduced false-allow breaches by nearly 60%. We’ve documented these detection and containment tactics in our analytics-driven defense framework – feel free to visit COE Security for a detailed breakdown.
Should you really be ‘advertising’ things on here? I’m pretty sure Brian Krebs used to prohibit suggestive posts like this.
I think he is on vacation or something.
You know the hilarious thing about this post, is that Brian, in his article, has not only detailed the who, why, where and how of this attack vector, but has even taken the time to explain effective counter measures, followed up by further discussions/options in the comments, which, if all implemented by the average home user, would offer upwards of 90% protection.
Yet Krishna, who’s company he is spruiking for, can only offer “reduced false-allow breaches by nearly 60%.” and is specifically peddling itself to the Corporate/Government market. Duh.
I’d rather Brian leave this post here so prospective clients know who to avoid.
Well who’s to say 60 is not better than 90 nowadays.
Well, I suppose if your talking about the number of breaches; 60 is definitely better than 90. But if your are talking about $’s per breach, I’d rather pay myself nothing, knowing I had only a 1 in 10 chance of intrusion compared to paying an exorbitant sum for a more than 1 in 3 chance. 😉
i remember ~around 2005, a very popular scam was try overblend the brwoser address bar with js based popups.
this never works well for the scamers cuz of toolbars and so on. but after 20 years it seems we are back on this level.