Cybercriminals are abusing a widespread lack of authentication in the customer service platform Zendesk to flood targeted email inboxes with menacing messages that come from hundreds of Zendesk corporate customers simultaneously.
Zendesk is an automated help desk service designed to make it simple for people to contact companies for customer support issues. Earlier this week, KrebsOnSecurity started receiving thousands of ticket creation notification messages through Zendesk in rapid succession, each bearing the name of different Zendesk customers, such as CapCom, CompTIA, Discord, GMAC, NordVPN, The Washington Post, and Tinder.
The abusive missives sent via Zendesk’s platform can include any subject line chosen by the abusers. In my case, the messages variously warned about a supposed law enforcement investigation involving KrebsOnSecurity.com, or else contained personal insults.
Moreover, the automated messages that are sent out from this type of abuse all come from customer domain names — not from Zendesk. In the example below, replying to any of the junk customer support responses from The Washington Post’s Zendesk installation shows the reply-to address is help@washpost.com.
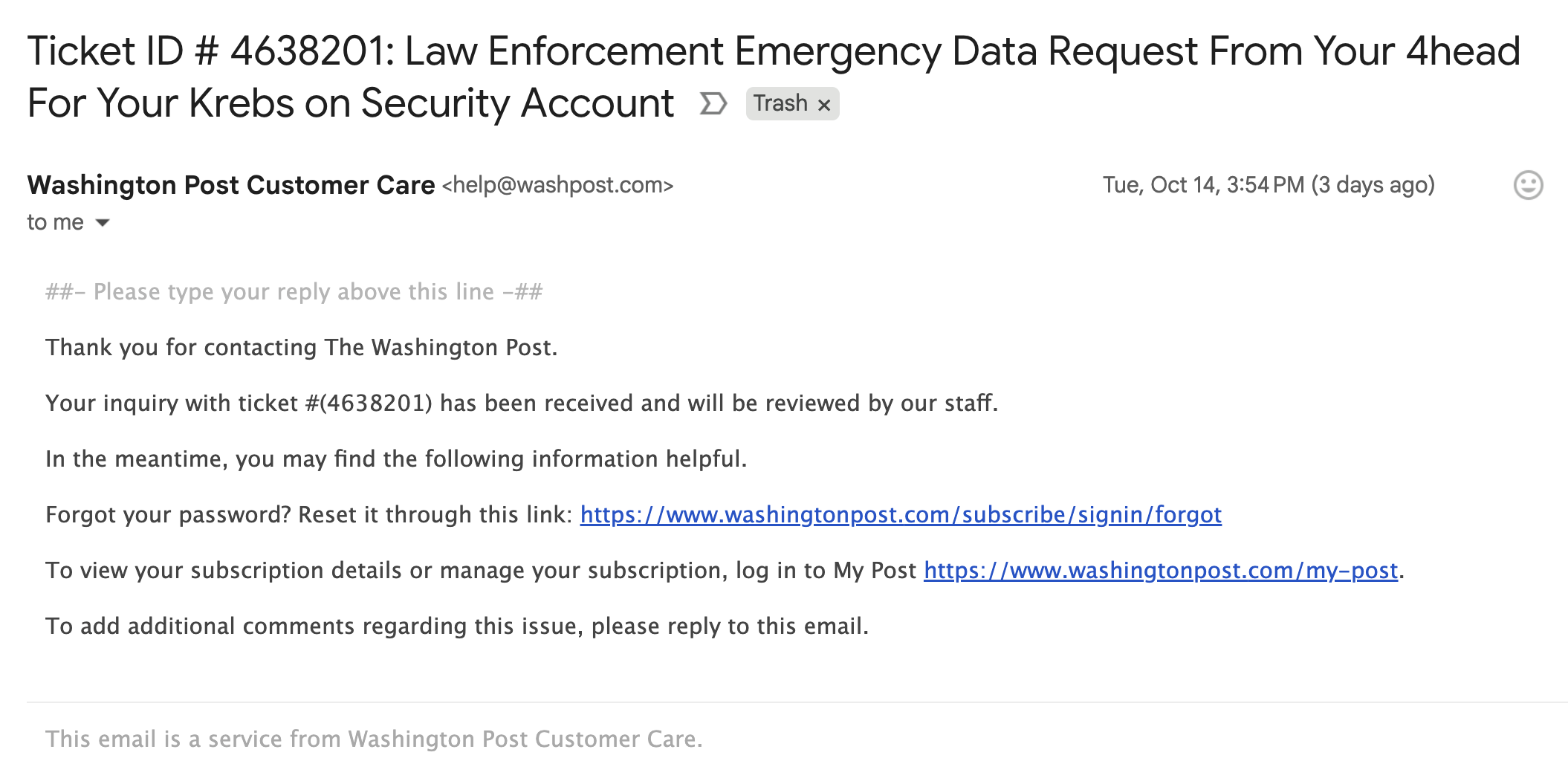
One of dozens of messages sent to me this week by The Washington Post.
Notified about the mass abuse of their platform, Zendesk said the emails were ticket creation notifications from customer accounts that configured their Zendesk instance to allow anyone to submit support requests — including anonymous users.
“These types of support tickets can be part of a customer’s workflow, where a prior verification is not required to allow them to engage and make use of the Support capabilities,” said Carolyn Camoens, communications director at Zendesk. “Although we recommend our customers to permit only verified users to submit tickets, some Zendesk customers prefer to use an anonymous environment to allow for tickets to be created due to various business reasons.”
Camoens said requests that can be submitted in an anonymous manner can also make use of an email address of the submitter’s choice.
“However, this method can also be used for spam requests to be created on behalf of third party email addresses,” Camoens said. “If an account has enabled the auto-responder trigger based on ticket creation, then this allows for the ticket notification email to be sent from our customer’s accounts to these third parties. The notification will also include the Subject added by the creator of these tickets.”
Zendesk claims it uses rate limits to prevent a high volume of requests from being created at once, but those limits did not stop Zendesk customers from flooding my inbox with thousands of messages in just a few hours.
“We recognize that our systems were leveraged against you in a distributed, many-against-one manner,” Camoens said. “We are actively investigating additional preventive measures. We are also advising customers experiencing this type of activity to follow our general security best practices and configure an authenticated ticket creation workflow.”
In all of the cases above, the messaging abuse would not have been possible if Zendesk customers validated support request email addresses prior to sending responses. Failing to do so may make it easier for Zendesk clients to handle customer support requests, but it also allows ne’er-do-wells to sully the sender’s brand in service of disruptive and malicious email floods.




Zendesk instance to allow anyone to submit support requests — including anonymous users. –> That should be defaulted to off along with the ability to pick any email or should really in this day and age, the option should be removed altogether. It’s just lazy programming.
What I really hate is sites that only accept gmail as a valid email address — even if you have your own domain. Clearly other email sites should work also (I’m not even talking about only comment sections or things Zendesk does; some places won’t even let you do a damn thing unless ‘google’ is involved).
Mentioning because, cool banner ad/conference thing and also relevant. Might check it out.
But that’s because they are in the Google ecosystem or are using a tool that authenticates to something that is in that ecosystem. For instance, Youtube. But I don’t see that to be the norm, like on banking or overseas sites like BBC.
I see the value of Google for a number of things. I was one of the people that had a Google email address when it was invite-only. It’s changed a lot since then, though, and its ‘motto’ changed accordingly (but how much of that is due to users that most people don’t categorize as ‘bad users’ but nevertheless introduce untrustworthiness into every environment they enter, knowingly or not?).
Gmail has been consistently better for some things than others. But some things I just don’t want Google to know about. Well, most things. And creeping AI sure makes that happen.
There is more privacy for most people not in the United States. Most countries don’t allow every person’s name and personally identifiable information to be indexed eternally on websites and searchable on google for instance. In fact almost no other country does. Come to think of it, only the United States does.
I have a really really dead but apparently still demented ‘father’, who served in Korea during the war back then, who thinks that all coins (and I’m speaking of about 80 cents or 90 cents, not like, “a bathtub full”) are cryptocurrency. No matter how often I tried to explain to him you can’t (and no-one could) survive on or buy a house for 90 cents, he just kept insisting ‘you’ll be just fine, Mike’. He died in the 60s, before I was born, and before my adoptive father died, but man, do I remember that.
These attacks remind me of that. Damn sure AI is parsing ‘coin’ and ‘coin purse’ as something it absolutely is not.
I also guarantee you that 90 cents isn’t 90 thousand or ninety million. It ain’t even a buck.
couldn’t even buy that red dress on eBay, there, Tim tam.
moving to Tremont/Fremont soon to be near you. then we can take the British train in cost of RICO again.
still waiting for my free truck in payment for the pound of coffee I gave you then, desk clerk/CIA agent/super leet American Horror Story never a bestie!
how’s our identity theft ring going? I hear your cucaracha hotel shut down.
FWIR its default is validate but can be configured to non-validation ‘for various business reasons’.
So they give you the rope. I can see that being useful in some cases. You ‘can’ side-validate other ways.
Throttling alone is obviously not enough to deal with bots, so if you leave it wide open it’s exactly that.
Optional feature meets abuse and becomes bug.
Not to get into the whole ‘bug’ argument with you, but it’s not really a bug OR a ‘feature’.
It’s both – as they apparently intended it to be in there, but it’s flawed. What’s your argument?
😀
Go back to your early 1990s SVR unix exploit already.
Oh noes. Did sum one upset dumdums did they. Are your feefees so hurt you gonna have a big cry in public? :p
I dunno, fake Paul. Let me know how you are doing before you’re born, too. Then we can all get together and put ‘Job Like You Also’ in the slammerkin.
If I wanted an intelligent conversation with you Princess, I would have flushed again … and again … and again … and again.
If anyone wanted an intelligent conversation, it is overwhelmingly obvious they would not be having one with you.
Even mealy (cold as it may be now, though I bought it hot) is an improvement over your imagined highness.
Please Mike, words like that are gonna make mealy blush.
As for me, I don’t really care for what you think. If you had actually attempted some form of cerebral discourse with me, I would be happy to oblige, but you did not. Instead, you piggybacked off the dribble of these demented numbskulls; so you can go kick a landmine for all I care.
Ciao for now and have a nice day.
I think I’ll pass as well.
the post count is 40 at this moment (though krebsy is holding back); therefore, you’re really fine now.
Note, if this posts, then it’ll be 41 posts then you’ll have found work too! fine win! or are just a guinea fowl. most likely none of those.
I mean, that’s how words work, clearly. just wish it into existence! poof!
you go, America!
TIME TO BE THUNDERSTRUCK.
No need to SHOUT there Cupcake, I heard you the first time.
gracias, now I know how deep comments nest.
I lol’ed too, fr00ty.
Your observation is well-founded, Phil. Permitting anonymous submissions and unrestricted email input by default represents a significant lapse in security design, particularly considering how readily such features can be exploited for malicious purposes like harassment or spam. In the current cybersecurity climate, platforms such as Zendesk must adopt secure default configurations, especially when serving prominent organizations. This is no longer a matter of user convenience—it is a critical responsibility to safeguard users from the misuse of digital infrastructure. Implementing robust authentication and validation protocols by default is not merely a best practice; it is an ethical imperative in modern software development.
all options should be removed forever. Taylor Swift is god. er, I mean, some things should never have options.
Myself not included, of course.
Why Zendesk is NOT validating email addresses is beyond me
I can see plenty of reasons for not validating email addresses.
Doesn’t make this, of course, more pleasant for Herr Krebs, but there are good reasons to not do so.
Not lazy programming, lazy management, this was a configuration option and I know our development team warns against this sort of thing and we are often ignored or overruled.
> Camoens said requests that can be submitted in an anonymous manner can also make use of an email address of the submitter’s choice.
Then you haven’t really made it anonymous, have you?
Zendesk is hardly the only platform guilty of this, either. I’ve *frequently* given something like `justfixit@example.com` on feedback forms that “require” an email address when I do not want to engage with them beyond a simple bug report. It should come as no surprise that bad actors would instead use that mechanism as an attack vector. Validations are Mailing List Management 101, too. Zendesk is big enough to know better.
I’d be curious if they gave you any details on what IP addresses were the source of the fake tickets. There really ought to be a followup on what *actual* actions they take against the abusers of their system. It’s just not enough to be “actively investigating” mitigations.
Hey Kreb, did you notice anything that reminds you about the first generation Lizard Squad?
Yes, you are correct. They now have more young guys working for them (do the dirty job and get busted by feds).
But you do know all of them and pretty well.
And no, MLT is not in that group as he is most likely under some bridge begging for a dose.
Far more noxious than them.
Wow cant believe these attackers get so creative would be so much better if the energy could be channeled to more productive things
Like what, running a public domain sql injection scanning tool from 2009? :/
TIL: Brian is on Tinder ¯\_(ツ)_/¯
Really? is he interested in some hot soggy four decade old cigarette on cigarette action at his palatial home in mumbye?
santa@northpole.com is my favorite
lol tell me about it.
mark sandman dying was a h00t but not as funny as the dude from that .so file I rm’ed in the 90s finally kicking the bucket.
This nearly impossible to do but I think you have done it. I am sure about this but my team says it’s not true. Please tell us that is he interested in some hot soggy four decade old cigarette on cigarette action at his palatial home in Georgia.
Zendesk is used by mafiosos to measure the health of a company, perhaps manipulate it to suffer loss so that it is an attractive investment to short.
Interesting.
New York City’s mob families are still in business.
https://www.nytimes.com/live/2025/10/23/nyregion/nba-illegal-gambling-arrests#nba-gambling-mafia-gambino-genovese-bonanno-luchese
lol never even once gambled online and haven’t even played a game in a casino in almost a decade and a half.
That said, I’m continually surprised they’re not doing something to rescind the bills allowing online gambling in the United States. It was messed up enough already when things were overseas, but now it’s a nightmare.
I don’t think the mob families are that involved in that stuff anymore. It’s a whole new bunch of crooks.
mobs want things that make money. Gambling makes money. Illegal gambling makes a lot of money.
It’s like saying “I don’t think the mob would be involved in the heroin trade.”
Okay…
sometimes mobs want things that lose money. doesn’t mean they run a hot dog cart.
saw you eating from the garbage outside a park one day several years ago great times
They can get the hot dog cart guy to do stuff for them if they need. Degrees of separation between the mob and the mules, or it’s malpractice.
yo Carolyn Camoens, can we discuss your female rapist ways? I didn’t need you claiming those Etsy purchases either. no wonder your sequel flopped.