A Ukrainian man indicted in 2012 for conspiring with a prolific hacking group to steal tens of millions of dollars from U.S. businesses was arrested in Italy and is now in custody in the United States, KrebsOnSecurity has learned.
Sources close to the investigation say Yuriy Igorevich Rybtsov, a 41-year-old from the Russia-controlled city of Donetsk, Ukraine, was previously referenced in U.S. federal charging documents only by his online handle “MrICQ.” According to a 13-year-old indictment (PDF) filed by prosecutors in Nebraska, MrICQ was a developer for a cybercrime group known as “Jabber Zeus.”
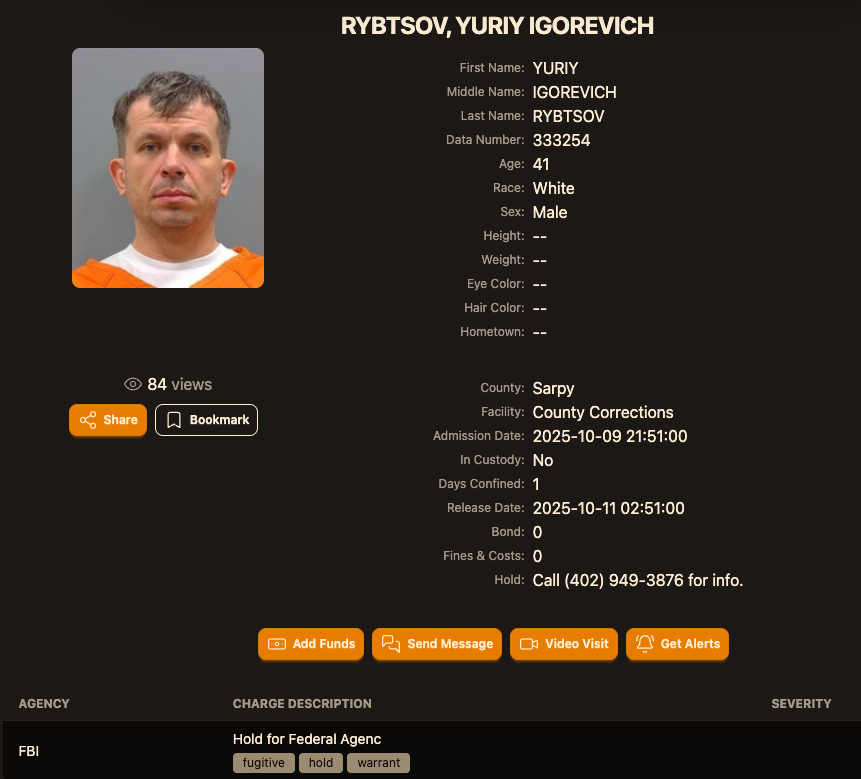
Image: lockedup dot wtf.
The Jabber Zeus name is derived from the malware they used — a custom version of the ZeuS banking trojan — that stole banking login credentials and would send the group a Jabber instant message each time a new victim entered a one-time passcode at a financial institution website. The gang targeted mostly small to mid-sized businesses, and they were an early pioneer of so-called “man-in-the-browser” attacks, malware that can silently intercept any data that victims submit in a web-based form.
Once inside a victim company’s accounts, the Jabber Zeus crew would modify the firm’s payroll to add dozens of “money mules,” people recruited through elaborate work-at-home schemes to handle bank transfers. The mules in turn would forward any stolen payroll deposits — minus their commissions — via wire transfers to other mules in Ukraine and the United Kingdom.
The 2012 indictment targeting the Jabber Zeus crew named MrICQ as “John Doe #3,” and said this person handled incoming notifications of newly compromised victims. The Department of Justice (DOJ) said MrICQ also helped the group launder the proceeds of their heists through electronic currency exchange services.
Two sources familiar with the Jabber Zeus investigation said Rybtsov was arrested in Italy, although the exact date and circumstances of his arrest remain unclear. A summary of recent decisions (PDF) published by the Italian Supreme Court states that in April 2025, Rybtsov lost a final appeal to avoid extradition to the United States.
According to the mugshot website lockedup[.]wtf, Rybtsov arrived in Nebraska on October 9, and was being held under an arrest warrant from the U.S. Federal Bureau of Investigation (FBI).
The data breach tracking service Constella Intelligence found breached records from the business profiling site bvdinfo[.]com showing that a 41-year-old Yuriy Igorevich Rybtsov worked in a building at 59 Barnaulska St. in Donetsk. Further searching on this address in Constella finds the same apartment building was shared by a business registered to Vyacheslav “Tank” Penchukov, the leader of the Jabber Zeus crew in Ukraine.

Vyacheslav “Tank” Penchukov, seen here performing as “DJ Slava Rich” in Ukraine, in an undated photo from social media.
Penchukov was arrested in 2022 while traveling to meet his wife in Switzerland. Last year, a federal court in Nebraska sentenced Penchukov to 18 years in prison and ordered him to pay more than $73 million in restitution.
Lawrence Baldwin is founder of myNetWatchman, a threat intelligence company based in Georgia that began tracking and disrupting the Jabber Zeus gang in 2009. myNetWatchman had secretly gained access to the Jabber chat server used by the Ukrainian hackers, allowing Baldwin to eavesdrop on the daily conversations between MrICQ and other Jabber Zeus members.
Baldwin shared those real-time chat records with multiple state and federal law enforcement agencies, and with this reporter. Between 2010 and 2013, I spent several hours each day alerting small businesses across the country that their payroll accounts were about to be drained by these cybercriminals.
Those notifications, and Baldwin’s tireless efforts, saved countless would-be victims a great deal of money. In most cases, however, we were already too late. Nevertheless, the pilfered Jabber Zeus group chats provided the basis for dozens of stories published here about small businesses fighting their banks in court over six- and seven-figure financial losses.
Baldwin said the Jabber Zeus crew was far ahead of its peers in several respects. For starters, their intercepted chats showed they worked to create a highly customized botnet directly with the author of the original Zeus Trojan — Evgeniy Mikhailovich Bogachev, a Russian man who has long been on the FBI’s “Most Wanted” list. The feds have a standing $3 million reward for information leading to Bogachev’s arrest.

Evgeniy M. Bogachev, in undated photos.
The core innovation of Jabber Zeus was an alert that MrICQ would receive each time a new victim entered a one-time password code into a phishing page mimicking their financial institution. The gang’s internal name for this component was “Leprechaun,” (the video below from myNetWatchman shows it in action). Jabber Zeus would actually re-write the HTML code as displayed in the victim’s browser, allowing them to intercept any passcodes sent by the victim’s bank for multi-factor authentication.
“These guys had compromised such a large number of victims that they were getting buried in a tsunami of stolen banking credentials,” Baldwin told KrebsOnSecurity. “But the whole point of Leprechaun was to isolate the highest-value credentials — the commercial bank accounts with two-factor authentication turned on. They knew these were far juicier targets because they clearly had a lot more money to protect.”
Baldwin said the Jabber Zeus trojan also included a custom “backconnect” component that allowed the hackers to relay their bank account takeovers through the victim’s own infected PC.
“The Jabber Zeus crew were literally connecting to the victim’s bank account from the victim’s IP address, or from the remote control function and by fully emulating the device,” he said. “That trojan was like a hot knife through butter of what everyone thought was state-of-the-art secure online banking at the time.”
Although the Jabber Zeus crew was in direct contact with the Zeus author, the chats intercepted by myNetWatchman show Bogachev frequently ignored the group’s pleas for help. The government says the real leader of the Jabber Zeus crew was Maksim Yakubets, a 38-year Ukrainian man with Russian citizenship who went by the hacker handle “Aqua.”

Alleged Evil Corp leader Maksim “Aqua” Yakubets. Image: FBI
The Jabber chats intercepted by Baldwin show that Aqua interacted almost daily with MrICQ, Tank and other members of the hacking team, often facilitating the group’s money mule and cashout activities remotely from Russia.
The government says Yakubets/Aqua would later emerge as the leader of an elite cybercrime ring of at least 17 hackers that referred to themselves internally as “Evil Corp.” Members of Evil Corp developed and used the Dridex (a.k.a. Bugat) trojan, which helped them siphon more than $100 million from hundreds of victim companies in the United States and Europe.
This 2019 story about the government’s $5 million bounty for information leading to Yakubets’s arrest includes excerpts of conversations between Aqua, Tank, Bogachev and other Jabber Zeus crew members discussing stories I’d written about their victims. Both Baldwin and I were interviewed at length for a new weekly six-part podcast by the BBC that delves deep into the history of Evil Corp. Episode One focuses on the evolution of Zeus, while the second episode centers on an investigation into the group by former FBI agent Jim Craig.

Image: https://www.bbc.co.uk/programmes/w3ct89y8




main di jo777. pasti cuan
So why do all these indictments come out of Nebraska?
Meant to mention that in the story. I don’t recall the politics of it, but more than a decade ago the Nebraska FBI field office was given the lead in investigating most of these Zeus trojan attacks. As a consequence, all of the indictments and complaints fired at this group and their derivatives tend to come from there.
The Nebraska FBI office handled investigations of the Zeus Jabber ring because one of the first companies that was a victim was based in Nebraska.
“Hell, I even thought I was dead until I found out it was just that I was in Nebraska. — Little Bill Daggett (Gene Hackman) from the Unforgiven.”
Because that’s where all the corn is. I mean when it’s not in Kansas.
Thank you KrebsonSecurity for sharing this incredible, uplifting story of hope.
Lawrence Baldwin is an amazing hero of the modern world. I am so really proud of him and of our country. I’m almost crying. I had thought we were done for, that no one would be able to stop these criminals. They had us living in fear and now they are the ones feeling that fear. Each one of those heartless criminals are staring straight at the punishment that is their due.
Agreed. Larry is the biggest hero here for doing the right thing at the right time!
It’s better with half and half and heavy cream.
You in the United States are being victimized by hackers because you don’t use our Brazilian electronic voting technology. Our electronic voting system is the most advanced technology, completely resistant to cyberattacks, according to our president.
“according to our president.” – Bwa… hahahahhaaaa.
If only you understood what that means to Americans in 2025.
Hasn’t the statue of limitations far passed by these nearly 15 year old cases?
Charging documents filed prior to statutes of limitations supersede statutes of limitations, especial federal ones. Sealed cases that are not unsealed over a period of many years, however, would rightly face Constitutional challenges, included (but not limited to) timely trial. Imagine having committing a crime when you were 19, and getting charged when you were in your 50s. That would clearly be a gross infringement of civil rights.
Please help me understand why the statute of limitations even exists? Especially in these cases of defrauding victims of millions of dollars, that finally being held accountable, would somehow infringe on the perpetrators civil rights. What about the rights of the victims? Do they not get their day in court?
Genuine question; because I am not a US citizen and there is not much in the way of time limits for criminal offences in my home country. Minor offences like shoplifting, drink driving, street dealing after fifteen years I get. But why would a major financial crime, like stealing life changing sums from random bank accounts get a golden pass?
Murder has no statute of limitations.
Technically, cases like drunk driving, evading parking tickets, not showing up for a court date, are all ‘chargeable offenses’ as soon as the ticket is issued, a bail bond is evaded, or probation or parole terms are violated. Those are not ‘new charges’. Rarely will someone get charged for a drug crime unless they were named as an ‘unknown subject’ on a preexisting case with a successful charge against a ring-leader (eg, a large RICO case).
If someone hacked a computer network in 1992, they’re almost certainly not going to get charged for that in 2025, unless by some strange coincidence they backdoored a machine in 1992, it still worked, and they accessed it again after 2020. If that same person was charged as an unknown subject in 1992-1998, then I suppose it’s within the realm of vast possibility they could unseal charges decades and decades later, but it seems highly unlikely; for one thing, the witnesses and evidence would almost certainly be tainted or non-existent at that point. Conjecturing here. I’ve never done anything like that myself. I am sure there are District Attorneys (or foreign countries) with cases they’ve never forgotten and grudges, but would something like that be considered ‘fair’ in a ‘Justice System’? I wouldn’t find it so.
The United States is a very litigious country, and has really short statutes of limitations a lot of civil offenses. Part of this is due to the court system simply not being able to keep up, if they let people file for something that I would find incredible — for instance, suing over a hot beverage. Other countries wouldn’t even entertain such a civil case, and would throw it out before it even reached a court docket. At the same time, some civil cases which SHOULD have longer statutes of limitations to file, often do not.
Ongoing cases of fraud, etc, are always fileable, as long as the crime is ongoing; when the crime or conspiracy ceases, the clock stops at the last criminal act.
The limit of time to charge, for the gross majority of criminal cases, including conspiracy, is five years, and for the rest of the cases up to ten years (for instance, espionage’s statute of limitations is ten years (though I am sure they’d find a way to charge after that if they wanted to)). Some state and city laws are probably in the range of five to ten years; less familiar with these, myself).
The statute of limitations for almost all federal crimes, including perjury, is five years (see United States of America, Federal statute 18 USC 3282).
It’s worth noting that a continuing criminal conspiracy to *cover up* the fact that, as in your post, they defrauded people of millions, or billions, or even trillions, of dollars, would still be indictable, decades after the fact, as the ‘cover-up’ would be ongoing, long after the original crime of theft had been committed (hence the addition of charges of conspiracy and RICO to many federal charges involving multiple parties).
This is so stupid. I said this many times. If you want to do crime and go unpunished then stay in mother ruzzia. Don’t go to Italy, dum dum.
His wife is to blame therefore
I heard that Ukraine is too very safe for cybercriminal. Especially if they work with SBU.
That’s probably true of all countries, no? If you’re the security you get the wink.
Holy sh*t, DJ Slava actually gave an interview in part 3.
Were these real time chat logs the ones you had been reading from during the filming of Koppelman’s Zero Day doc? It’s incredible that they were able to get this guy 13 years after the fact. Kudos to Italy for their amazing partnership in ensuring he was swiftly detained
Yes, the same. https://krebsonsecurity.com/2012/04/help-kickstart-a-film-on-cybercrime/
Great food, amazing times, uncomfortable chairs.
Brian,
I keep coming back, in my mind, to the long-ago story where you were relaying messages from hacked instant message servers to federal agents.
No offense, but how in the world was that considered legal? I’m struggling both with the concept in and of itself, as well as the evidentiary issues (fruit of the poisoned tree, etc). I struggle with the legality of a lot of the sinkholing private companies also do. That’s not to say I back the ‘other parties’, only to state it seems illegal to me, just as you find the acts they commit illegal.
Shouldn’t you need a warrant for things like this? Basic law school 101.
Your question seems to be more about the legality of acting on information that cybercriminals inadvertently leaked from their servers. I am not in the business of prosecuting cybercrimes, so figuring out whether what I’m looking at is real and reliable information is far more important than trying to determine if the data is somehow legal to look at (according to whom?).
Imagine that by some kind of magic you were given a list of people that were going to be robbed of all that they own each day. Each day you get a new list of upcoming victims. You know law enforcement has this list, but you also know that they’re not in the pre-crime business and aren’t at all interested in or prepared to alert individual victims before it is too late. Do you just sit on the information and hope those people/companies can fend for themselves? I would say doing nothing in that case — especially when it is well within your power to prevent major losses — is the more ethically fraught situation.
Okay…
Let’s say someone were given a list like that, or something like it, every day (I’m pretty sure there was a fictional tv show out a couple of decades ago called ‘Early Edition’ that was similar to this, but whatever). For the same of credibility, let’s say it wasn’t “magical” (note, I do not believe there is any science that could do this, but it wouldn’t totally strain credulity to suggest that quantum tunnel computing could effectively make minute wormholes possible to pass tiny bits of information through to different points in the future of some super-conscious AI to the current present but the past to that AI. Would you want that sort of science? NO. The dangers of this have been discussed ad nauseam in numerous sci fi stories for the past century or so, in various ways. I’m going to dismiss the Tom Cruise movie, because, let’s face it, that’s a dystopia no-one wants (including the part where Tom Cruise would have to go through the whole married to a Dawson’s Creek actor at some point, and jumping on a couch (not database, hah)).
But okay, let’s say this happens, anyway. People are notorious for doing things that are bad for them, and making excuses for it, and it’ll probably lead to our extinction. They don’t heed warnings and plough through believing that what seems good in the temporary, immediate or near future, will have enough ‘good repercussions’ to make up for the negative ones. This rarely happens. But people tend to think it will, and will keep pursuing it long after they’ve been proven wrong because of their ego or unwillingness to admit they f*ed up.
What is your culpability if you sit on it? If you don’t sit on it? If you attempt to pass it along to someone who decides not to pursue it because it is, in fact, illegal for themselves to pursue it (for instance, the FBI, in theory, without proper judicial oversight and a constant need to renew warrants after a certain amount of time; if they don’t, no case. “bad guy” or not, their rights were violated.
Constitutional law declares, UNEQUIVOCABLY, that the rights of a person to a fair trial *includes* the right for a perceived perpetrator of a crime to (a) be considered innocent until proven guilty (not through only mere ‘evidence’ — with proper chain of evidence — but in a ‘court of law’ (let’s put ‘peers’ aside here, since most technical cases are not judged by actual peers; a strict definition would probably ruin every murder trial, heh)), and (b) not have their right to privacy violated get that warrant in the first place.
Sort of tricky, I admit, but let’s say you ignore those things altogether, or shrug them off.
You’re mentioning ethics, but this is about legality. While I ‘get’ that you would not want whatever random people to become victims of a crime, you’re still violating the law. Would the proper thing not have been to hand that over to a district attorney (and I know you have those sorts of connections, and did even 10-15 years ago) to access, instead of accessing yourself and (as an old article of yours stated) ‘running back and forth’ to check ‘messages’ and pass them along. For some reason this reminds me of the old stories I read about gollumfun performing the same sort of thing — but he was, ostensibly, supervised by the FBI, and they, in turn, by the Justice Department (even though I suspect a lot of that tomfoolery was kind of not quite legal, either… but, whatever).
As an aside, imagine you were given a list of one person who was robbed every single day. The clock resets until you defend that one person, but to do so requires you, your own self, or some judge, to have your or their perceived right to privacy violated, forever. How many iterations of doing the wrong thing would the average person go through before they’d notice a pattern or do ‘the right thing’? Would you?
You’re right. What was I thinking? We should definitely worry more about the privacy of the poor cybercriminals than concern ourselves with the plight of their victims.
As an aside, have you ever received a spam message to be a courier for any of these apparent miscreants? Technically, according to your guidelines, you are an accomplice even if it wasn’t intended for you.
Something to consider.
“Technically, according to your guidelines, you are an accomplice even if it wasn’t intended for you.”
Is not a fact, along with the vague notion of a “perceived right to privacy”.
These are your interpretations.
I like a bizarre hypothetical as much as anyone, but what are you getting at?