The FBI this week announced it is offering a USD $3 million bounty for information leading to the arrest and/or conviction of one Evgeniy Mikhailovich Bogachev, a Russian man the government believes is responsible for building and distributing the ZeuS banking Trojan.
Bogachev is thought to be a core architect of ZeuS, a malware strain that has been used to steal hundreds of millions of dollars from bank accounts — mainly from small- to mid-sized businesses based in the United States and Europe. Bogachev also is accused of being part of a crime gang that infected tens of millions of computers, harvested huge volumes of sensitive financial data, and rented the compromised systems to other hackers, spammers and online extortionists.
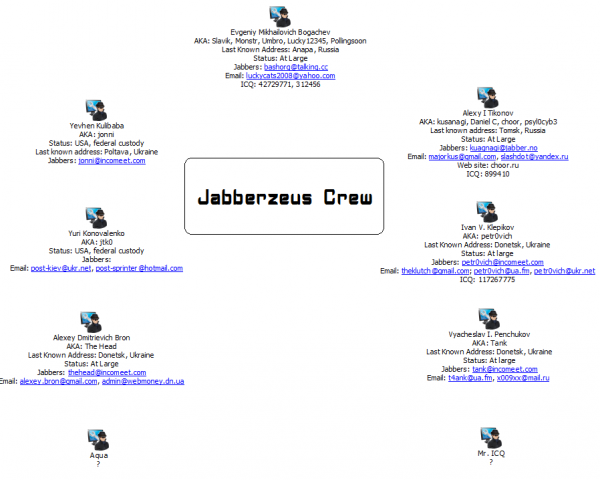
So much of the intelligence gathered about Bogachev and his alleged accomplices has been scattered across various court documents and published reports over the years, but probably just as much on this criminal mastermind and his associates has never seen the light of day. What follows is a compendium of knowledge — a bit of a dossier, if you will — on Bogachev and his trusted associates.
I first became aware of Bogachev by his nickname at the time –“Slavik” — in June 2009, after writing about a $415,000 cyberheist against Bullitt County, Kentucky. I was still working for The Washington Post then, but that story would open the door to sources who were tracking the activities of an organized cybercrime gang that spanned from Ukraine and Russia to the United Kingdom.

Yevgeniy Bogachev, Evgeniy Mikhaylovich Bogachev, a.k.a. “lucky12345”, “slavik”, “Pollingsoon”. Source: FBI.gov “most wanted, cyber.
Not long after that Bullitt County cyberheist story ran, I heard from a source who’d hacked the Jabber instant message server that these crooks were using to plan and coordinate their cyberheists. The members of this crew quickly became regular readers of my Security Fix blog at The Post after seeing their exploits detailed on the blog.
 They also acknowledged in their chats that they’d been in direct contact with the Zeus author himself — and that the gang had hired the malware author to code a custom version of the Trojan that would latter become known as “Jabberzeus.” The “jabber” part of the name is a reference to a key feature of the malware that would send an Jabber instant message to members of the gang anytime a new victim logged into a bank account that had a high balance.
They also acknowledged in their chats that they’d been in direct contact with the Zeus author himself — and that the gang had hired the malware author to code a custom version of the Trojan that would latter become known as “Jabberzeus.” The “jabber” part of the name is a reference to a key feature of the malware that would send an Jabber instant message to members of the gang anytime a new victim logged into a bank account that had a high balance.
Here’s a snippet from that chat, translated from Russian. “Aqua” was responsible for recruiting and managing a network of “money mules” to help cash out the payroll accounts that these crooks were hijacking with the help of their custom Jabberzeus malware. “Dimka” is Aqua’s friend, and Aqua explains to him that they hired the ZeuS author to create the custom malware and help them troubleshoot it. But Aqua is unhappy because the ZeuS author declined to help them keep it undetectable by commercial antivirus tools.
dimka: I read about the king of seas, was that your handiwork?
aqua: what are you talking about?
dimka: zeus
aqua: yes, we are using it right now. its developer sits with us on the system
dimka: it seems to be very popular right now
aqua: but that fucker annoyed the hell out of everyone. he refuses to write bypass of [anti-malware] scans, and trojan penetration is only 35-40%. we need better
aqua: http://voices.washingtonpost.com/securityfix read this. here you find almost everything about us
aqua: we’re using this [custom] system. we are the Big Dog. the rest using Zeus are doing piddly crap.
Days later, other members of the Jabberzeus crew were all jabbering about the Bullitt County cyberheist story. The individual who uses the nickname “tank” in the conversation below managed money mules for the gang and helped coordinate the exchange of stolen banking credentials. Tank begins the conversation by pasting a link to my Washington Post story about the Bullitt County hack.
tank@incomeet.com: That is about us. Only the figures are fairytales.
haymixer@jabber.ru/dimarikk: This was from your botnet account. Apparently, this is why our hosters in service rejected the old ones. They caused a damn commotion.
tank@incomeet.com: I have already become paranoid over this. Such bullshit as this in the Washington Post.
haymixer@jabber.ru/dimarikk: I almost dreamed of this bullshit at night. He writes about everything that I touch in any manner…Klik Partners, ESTHost, MCCOLO…
tank@incomeet.com: Now you are not alone. Just 2 weeks before this I contacted him as an expert to find out anything new. It turns out that he wrote this within 3 days. Now we also will dream about him.
In a separate conversation between Tank and the Zeus author (using the nickname “lucky12345” here), the two complain about news coverage of Zeus:
tank: Are you there?
tank: This is what they damn wrote about me.
tank: [pasting a link to the Washington Post story]
tank: I’ll take a quick look at history
tank: Originator: BULLITT COUNTY FISCAL Company: Bullitt County Fiscal Court
tank: Well, you got it from that cash-in.
lucky12345: From 200k?
tank: Well, they are not the right amounts and the cash out from that account was shitty.
tank: Levak was written there.
tank: Because now the entire USA knows about Zeus.
tank: 🙁
lucky12345: It’s fucked.
After the Bullitt County story, my source and I tracked this gang as they hit one small business after another. In the ensuing six months before my departure from The Post, I wrote about this gang’s attacks against more than a dozen companies in the United States.
By this time, Slavik was openly selling the barebones ZeuS Trojan code that Jabberzeus was built on to anyone who could pay several thousand dollars for the crimeware kit. There is evidence he also was using his own botnet kit or at least taking a fee to set up instances of it on behalf of buyers. In late 2009, security researchers had tracked dozens of Zeus control servers that phoned home to domains which bore his nickname, such as slaviki-res1.com, slavik1[dot]com, slavik2[dot]com, slavik3[dot]com, and so on.
On Dec. 13, 2009, one of the Jabberzeus gang’s money mule recruiters –a crook who used the pseudonym “Jim Rogers” — somehow intercepted news I hadn’t shared beyond a few trusted friends at that point: That the Post had eliminated my job in the process of merging the newspaper’s Web site with the dead tree edition. The following is an exchange between Jim Rogers and the above-quoted “tank”.
jim_rogers@
jabber.org: There is a rumor that our favorite (Brian) didn’t get his contract extension at Washington Post. We are giddily awaiting confirmation 🙂 Good news expected exactly by the New Year! Besides us no one reads his column 🙂 tank@incomeet.com: Mr. Fucking Brian Fucking Kerbs!
I continued to write about new victims of this gang even as I was launching this blog, and in the first year I profiled dozens more companies that were robbed of millions. I only featured victims that had agreed to let me tell their stories. For every story I wrote, there were probably 10-20 victim organizations I spoke with that did not wish to be named.
By January 2010, Slavik was selling access to tens of thousands of hacked PCs to spammers, as well as large email lists from computer systems plundered by his malware. As I wrote in the story, Zeus Trojan Author Ran With Spam Kingpins, Slavik was active on multiple crime forums, not only finding new clients and buyers for his malware, but for the goods harvested by his own botnets powered by ZeuS.
 Eight months later, authorities in the United Kingdom arrested 20 individuals connected to the Jabberzeus crime ring, and charged 11 of them with money laundering and conspiracy to defraud, including Yevhen “Jonni” Kulibaba, the ringleader of the gang, and Yuri “JTK” Konovalenko.
Eight months later, authorities in the United Kingdom arrested 20 individuals connected to the Jabberzeus crime ring, and charged 11 of them with money laundering and conspiracy to defraud, including Yevhen “Jonni” Kulibaba, the ringleader of the gang, and Yuri “JTK” Konovalenko.
In conjunction with that action, five of the gang’s members in Ukraine also were detained, but very soon after released, including the aforementioned Vyacheslav “Tank” Penchukov and a very clever programmer named Ivan “petr0vich” Klepikov. More details about these two and others connected with the Jabberzeus crew is available from this unsealed 2012 complaint (PDF) from the U.S. Justice Department.
Unsurprisingly, not long after the global law enforcement crackdown, Slavik would announce he was bowing out of the business, handing over the source code for Zeus to a hacker named “”Harderman” (a.k.a. “Gribodemon”), the author of a competing crimeware kit called SpyEye (25-year-old Russian man Alexsander Panin pleaded guilty last year to authoring SpyEye).
Near as I can tell, Slavik didn’t quit developing Zeus after the code merger with SpyEye, he just stopped selling it publicly. Rather, it appears he began developing a more robust and private version of Zeus.
By late 2011, businesses in the United States and Europe were being hit with a new variant of Zeus called “Gameover” Zeus, which used the collective, global power of the PCs infected with Gameover Zeus to launch crippling distributed denial-of-service (DDoS) attacks against victims and their banks shortly after they were robbed.
In late March 2012, Microsoft announced it had orchestrated a carefully planned takedown of dozens of botnets powered by ZeuS and SpyEye. In so doing, the company incurred the wrath of many security researchers when it published in court documents the nicknames, email addresses and other identifying information on the Jabberzeus gang and the Zeus author.
A few months later, the Justice Department officially charged nine men in the Jabberzeus conspiracy, including most of the above named actors and two others — a money mover named Alexey Dmitrievich Bron (a.k.a.”TheHead”) and Alexey “Kusanagi” Tikonov, a programmer from Tomsk, Russia. Chat records intercepted from the incomeet.com server that this crew used for its Jabber instant message communications strongly suggest that Bron and Penchukov (“Tank”) were co-workers in Donetsk, Ukraine, possibly even in the same building.
In June 2014, the U.S. Justice Department joined authorities in many other countries and a large number of security firms in taking down the Gameover ZeuS botnet, which at the time was estimated to have infected more than a million PCs.
It’s nice that the Justice Department has put up such a large bounty for a man responsible for so much financial ruin and cybercrime. Kulibaba (“Jonni”) and his buddy Konovalenko (“Jtk0”) were extradited to the United States. Unfortunately, the rest of the Jabberzeus crew will likely remain free as long as they stick within the borders of Ukraine and/or Russia.





Wasn’t Evgeniy Mikhailovich Bogachev supposedly on a boat traveling the Red Sea trying to hide from authorities?
According to the FBI, “Bogachev was last known to reside in Anapa, Russia. He is known to enjoy boating and may travel to locations along the Black Sea in his boat. He also owns property in Krasnodar, Russia.”
Right now Ukraine is begging Canada and the US to send them military equipment – and maybe we should – if they hand over criminals like these guys first.
I think Sen. Mark Warner tried to attach a condition like that to a funding bill for Ukraine. I’m unsure if it actually passed.
http://www.opednews.com/articles/Sen-Warner-s-views-on-Ukra-by-Neal-Herrick-Democracy_Economic_Government_International-140820-351.html
Your article has me thinking – maybe they should offer these types of rewards all the time much like Google etc with their bug-bounty programs. Like all criminals many will turn on others for the money (if sufficient) and could bring in more people to monitor and hunt them down for the rewards?
You mean like Dogavich the мисливець за головами? Ha! 😀
The bill in question became Public Law 113-95 on 4/3/2014. But, I couldn’t find the amendment or inclusion into the bill.
http://thomas.loc.gov/cgi-bin/bdquery/z?d113:HR04152:@@@R
According to Stephen Cobb, ESET, the amendment to the bill did not pass:
http://www.welivesecurity.com/2015/01/20/cybercrime-deterrence-6-important-steps item 1.
A very similar amendment was agreed to in 2005, but seemingly was removed from the final passed bill (Public Law No 109-102, Section 583):
http://www.congress.gov/amendment/109th-congress/senate-amendment/1271
And, since the full Congress won’t pass it:
http://www.congress.gov/bill/113th-congress/senate-resolution/563/text
Another fascinating piece. Thank you.
I bet Al Gore wishes he’d never invented the internet.
Agreed, look at all the global warming it caused.
Are you ever going to fix your “Donate Bitcoins” link, Krebbo…?
Brian
It has got to be satisfying to find your are so reviled by these scumbags! You are the best!
Oh King, Live Forever! Long Live The KIng!
Brian, what is the current state of the botnets? Has Microsoft’s efforts done anything to minimize their potential damage?
So from I read you are saying that 5 of 7 members of team were Ukrainians? How it even possible? Last time when I watched the TV they said that Russians are bad guys, not Ukrainians! Ukrainians are peaceful nation, they are almost angels from the sky!
How much Kremlin paid you for this dirty propaganda?
Eastern block thiefs will continue until somebody does something about it. They regularly rip off US artists by grabbing tracks and putting them on sites hosted on eastern bock servers. One I know well, had 6 tracks being sold at $0.99…no royalties of course
Two of the guys are said to be working in Donetsk, where the conflict currently persists. The people in Donetsk are pro-Russian, and would much rather stay with Russia as under the rulership of that country their criminal activity is most likely to be ignored.
I hope Ukraine gets their act together in this conflict and focuses their effort on the previously ignored criminal activity in the country.
Damn, Krebs!
I *love* these stories!!!!
You should write a book!!!
Oh, wait, you already did — nevermind….
I love the comprehensive reporting here. Well done.
Another great post!
Love the line in the IM exchange between ‘Jim Rogers’ and ‘tank’ regarding Brian’s WP blog: “Besides us no one reads his column”
It’s such a joy to read your articles, Brian! Elsewhere I get lost in the technical jargon, but not here.
Good start. When a corporation gets hacked and our personal information exposed, I wish part of the penalty is the corporation must put money into this ransom kitty to go after future hackers and scammers.
I think the old headings of DEAD or ALIVE might have more interest to the people that might come in contact with him. So has our government done a fly over the area with posters??
Our relationship with Russia will get us nowhere, probably try to pin a medal on him
Where’s the NSA when you need them?
‘Slavik’ is a shortened form of the name Vyacheslav. The FBI could be after the wrong mastermind. The person listed on one of the illustrations, Vyacheslav Borisovich Penchukov, could turn out to be the real ‘Slavik’.
Oh but of course Vyacheslav Igorevich Penchukov!
My fault.
Oh but of course Vyacheslav Igorevich Penchukov!
My fault.
What is so bad about devolping software like Zeus or SpyEye?
It is just a tool ..
The people who use the tool are the bad guys, not the developers.
Nothing’s wrong with writing malware, at least not here in the US. it’s protected speech. But when you start selling it to known criminals and then assisting them in cashing out hacked accounts, that tends to swerve things into the criminal zone for you as a malware author.
Great job, congratulations Brian for all your great work
Truthfully I don’t think your going to capture anyone who is located in Russia and Ukraine unless you send some spies over there. Russia and Ukraine have many places to hide. You should probably first talk to relatives and talk to friends and people who they sold the information too. That might help. Track the computers that were used to hack and find that computer if you want to get any closer to finding them. If you were to send some spies, Then send some fluent Russian spies. Of you want any luck don’t forget to bring back up cause you don’t know what these hackers can do. They have as much as a mind to hack the internent and other computers as to building a robot or any dangerous thing that can affect your job. They could’ve deleted a lot of things by now but, you can never now, this might be Putins idea. Good luck and make sure to return the money to the rightful owners. 🙂
Evgeniy Mikhailovich Bogachev is know as EP_X0FF on some sites, and “Ivan “petr0vich” Klepikov” is supposedly living in Kehtna Estonia and drives a dark green car, living in the building by the bus stop by the road with a Russian relative..
Wow. I thought Hamsa/bx1 was the author of Zeus.
He was only running a Zeus net, then?
I saw him in Nightclub with his friends 😉
You’re always about crap. Why do you never write about NSA activity, for example? It is in earnest about InfoSec. Wake up, Brian. The matrix has you
I am a private researcher and investigator, an expert at locating individuals.
I am putting together a team to locate these individuals. I plan to reserve a portion of any reward to support Brian Krebs and his efforts here.
If you have an interest or ideas, feel free to contact me.
Richard Bartel rcbartel@yahoo.com initially.
yes there is fraud.but insurance will cover.i think.
100% cunsomer protection.
Who the f FBI thinks they are offering just a 3 million dead American presidents . They are just Pathetic .
I think “Slavik ” will give you 5 million dead American presidents if you can find him .Maybe even more if you be nice to him .
The Last time i checked he had old soviet submarine parked near his house and battery of S – 300 long range surface-to-air missile systems stationed in the back garden .Plus 10 former elite Spatsnaz solders guarding him 24/7 .
Slavink should put a 1 million bounty on Krebs head , Just for fun of it . Mexican gangs would love to do that job .
Everything is right. Only submarine isn’t so old