The U.S. Justice Department is expected to announce today an international law enforcement operation to seize control over the Gameover ZeuS botnet, a sprawling network of hacked Microsoft Windows computers that currently infects an estimated 500,000 to 1 million compromised systems globally. Experts say PCs infected with Gameover are being harvested for sensitive financial and personal data, and rented out to an elite cadre of hackers for use in online extortion attacks, spam and other illicit moneymaking schemes.
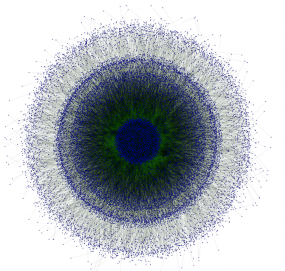
This graphic, from 2012, shows the decentralized nature of P2P network connectivity of 23,196 PCs infected with Gameover. Image: Dell SecureWorks
The sneak attack on Gameover, dubbed “Operation Tovar,” began late last week and is a collaborative effort by investigators at the FBI, Europol, and the UK’s National Crime Agency; security firms CrowdStrike, Dell SecureWorks, Symantec, Trend Micro and McAfee; and academic researchers at VU University Amsterdam and Saarland University in Germany. News of the action first came to light in a blog post published briefly on Friday by McAfee, but that post was removed a few hours after it went online.
Gameover is based on code from the ZeuS Trojan, an infamous family of malware that has been used in countless online banking heists. Unlike ZeuS — which was sold as a botnet creation kit to anyone who had a few thousand dollars in virtual currency to spend — Gameover ZeuS has since October 2011 been controlled and maintained by a core group of hackers from Russia and Ukraine.
Those individuals are believed to have used the botnet in high-dollar corporate account takeovers that frequently were punctuated by massive distributed-denial-of-service (DDoS) attacks intended to distract victims from immediately noticing the thefts. According to the Justice Department, Gameover has been implicated in the theft of more than $100 million in account takeovers.
The curators of Gameover also have reportedly loaned out sections of their botnet to vetted third-parties who have used them for a variety of purposes. One of the most popular uses of Gameover has been as a platform for seeding infected systems with CryptoLocker, a nasty strain of malware that locks your most precious files with strong encryption until you pay a ransom demand.
According to a 2012 research paper published by Dell SecureWorks, the Gameover Trojan is principally spread via Cutwail, one of the world’s largest and most notorious spam botnets (for more on Cutwail and its origins and authors, see this post). These junk emails typically spoof trusted brands, including shipping and phone companies, online retailers, social networking sites and financial institutions. The email lures bearing Gameover often come in the form of an invoice, an order confirmation, or a warning about an unpaid bill (usually with a large balance due to increase the likelihood that a victim will click the link). The links in the email have been replaced with those of compromised sites that will silently probe the visitor’s browser for outdated plugins that can be leveraged to install malware.
It will be interesting to hear how the authorities and security researchers involved in this effort managed to gain control over the Gameover botnet, which uses an advanced peer-to-peer (P2P) mechanism to control and update the bot-infected systems.
The addition of the P2P component in Gameover is innovation designed to make it much more difficult for security experts, law enforcement or other Internet do-gooders to dismantle the botnet. In March 2012, Microsoft used a combination of legal maneuvering and surprise to take down dozens of botnets powered by ZeuS (and its code-cousin — SpyEye), by seizing control over the domain names that the bad guys used to control the individual ZeuS botnets.
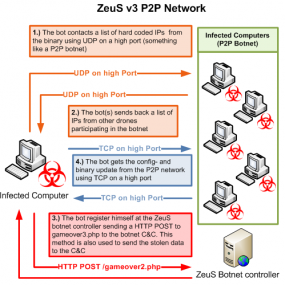
But Gameover would be far trickier to disrupt or wrest from its creators: It uses a tiered, decentralized system of intermediary proxies and strong encryption to hide the location of servers that the botnet masters use to control the crime machine.
“Microsoft’s 2012 takedown action had no effect on the P2P version of ZeuS because of its network architecture,” reads Dell SecureWorks’s 2012 paper on Gameover. “In the P2P model of ZeuS, each infected client maintains a list of other infected clients. These peers act a massive proxy network between the P2P ZeuS botnet operators and the infected hosts. The peers are used to propagate binary updates, to distribute configuration files, and to send stolen data to the controllers.”
According to McAfee, the seizure of Gameover is expected to coincide with a cleanup effort in which Internet service providers contact affected customers to help remediate compromised PCs. The Department of Homeland Security’s U.S. Computer Emergency Readiness Team (US-CERT) today published a list of resources that may help in that effort.
Update, 11:07 a.m. ET: The Justice Department just published a complaint (PDF) that names the alleged author of the ZeuS Trojan, allegedly a Russian citizen named Evgeniy Mikhailovich Bogachev. The complaint mentions something that this blog has noted on several occasions – that the the ZeuS author used multiple nicknames, including “Slavik” and “Pollingsoon.” More court documents related to today’s action are available here.





Tovar was flagged on McAfee at the weekend – then taken down…Woops.
http://blogs.mcafee.com/mcafee-labs/game-zeus-cryptolocker
The McAfee blog was removed (and is still missing) but at least one person took a copy and re-posted it. The only reason for its removal must be that it announced the operation a couple of days early.
There is a copy of that blog at http://www.404techsupport.com/2014/05/mcafee-writes-about-operation-tovar-taking-a-swipe-at-cryptolocker-and-gameover-zeus/
The McAfee blog has now re-apppeared. It wasn’t up for long, but it seems someone did take notice …
http://www.bleepingcomputer.com/forums/t/536370/operation-tovar-a-success-but-is-it-really-gameover-for-cryptolocker/
“This blog post was only public for a brief period before it was taken down. Unfortunately, it may have been enough time to let the Gameover or CryptoLocker developers know what was going on as the CryptoLocker Decryption Service page was replaced with a simple message. “stupid mcafee :)”. Unfortunately, this page is no longer accessible and showing a “Bad Gateway” message.”
Whoever posted the offending McAfee blog must either be stupid or in league with the criminals. The least bad that can be said is that self-control was completely absent.
How can progress be made against cyber criminals when information helpful to them is published under the name and auspices of such as McAfee, a computer security company for heaven’s sake?*!?*!?
This is war. Thank God that the people at Bletchley Park did not indulge in chit-chat 70+ years ago. As Churchill said, they were the geese that laid the golden egg and never cackled.
I am mindful that one of the many great WW2 collaborations between Britain and the USA took place at Bletchley Park. Long may it continue.
“Whoever posted the offending McAfee blog must either be stupid or in league with the criminals.”
No, it makes them human. Smart, competent people make mistakes all the time. For example, the goto fail bug in Apple’s code and the Heartbleed bug in openssl. It would be nice if people could be perfect, but they aren’t. That doesn’t make them stupid or criminal. However I do understand your incredulity.
Well put.
“These junk emails typically spoof trusted brands”
Before clicking on any link, hover your mouse-cursor over it without clicking and notice the URL in the lower-left corner of the screen; if the URL is not as expected, don’t click on it. I don’t have a PC running XP so I’m not sure if it works there, but it works in 7.
1. To see where a hyperlink goes:
In OS X, turn on info bar at bottom of Safari window (under view), then hover to see embedded hyperlink.
In iOS, put AND HOLD(!) finger on hyperlink and iOS will generate a save card pop up showing embedded hyperlink; after reading card just cancel it.
2. For seeing where an email comes from:
In OS X, click little triangle on right side of address bubble and originating address will be shown.
In iOS, tap address and a save to contacts card will be generated; read address then cancel saving of card.
Notes:
1. Apple’s mail clients don’t send read receipts back to the originators.
2. To reduce eventual risk of a pic with malware code being delivered into your iOS device, in the configuration page under mail, restrict the loading of pics when a mail is opened.
Good tips for Apple products. In some browsers, JavaScript tricks can disguise even the popup link when you hover over the URL, and internationalized character sets allow fraudulent web sites that may be visually identical to the real thing though. So-called “IDN Homograph Attacks” are a difficult problem. I showed some examples at http://dnlongen.blogspot.com/2013/07/disguised-links.html
@Krebs, great investigative work on this story.
Good blog. I never thought of using tool tips to fool people, but then again I’m not a slime-bag. I think people could be trained to ignore anything but the bottom-left link, but perhaps I’m optimistic.
Also, I use Firefox with NoScript, so I am pretty much invulnerable to JavaScript misdirection of links.
Of course, if someone is truly paranoid, they can enter the link manually, as you wrote; that’s what I do. Another option is to right-click copy the link and paste it into Notepad, but some people might accidentally left-click it instead.
And yes, I ignored Saint Steve’s products, but the truth is that the vast majority of people use Windows. Only 7-8% of people use OS X and those people seem to be fairly well-informed on computer matters.
Please note that I am NOT implying that David Longenecker is a slime-person.
The fact is that a large number of people who barely understand any of this are sadly gullible enough to accept any email they receive at face value and click on a given URL without thinking twice. They don’t even realize that emails that pretend to be from, say, the IRS, UPS or a bank they don’t even use, are fake — and don’t wonder how those entities would even know their email address!
Until we can educate these people to use some degree of common sense and caution, their vulnerability will make it easy for this stuff to proliferate exponentially.
While some version(s) of OS X may refer to that low bar as an “Info Bar,” it has always been called a “Status Bar” on my Macs.
“Apple’s mail clients don’t send read receipts back to the originators.”
Now you’ve got me a bit worried. I use only web-based email; do any web-based email services send read receipts by default? (I already know not to display images in emails by default because of web beacons.)
For months I’ve been getting the odd email purporting to be from the Liberal Party of Canada, begging for donations and sprinkled liberally (no pun intended) with links seemingly pointing to liberal.ca. Only hovering over any of the links invariably reveals that their true destination is some site called marketing.davia.com instead.
Needless to say I’ve never followed any of these links.
I agree and do the same however try teaching this to the 65+ year old retired people who don’t understand computers that well. I’ve all but given up on trying to teach my parents basic computer security knowledge.
As a 65+ retired person, I can assure you that many of us still have all of our faculties and are fully aware of these issues. It would be interesting to see a profile of victims sorted by age group …
I quite agree with BillC I’m over 75 and also female. I have tried to teach basic email and computer security to a retired school master though and got nowhere so you are both right
+1
Another interesting article, keep them coming Krebs
Pretty sure I’ve liberated a PC or two from this botnet in my day. Removing malware is always a challenge.
Yeah, if you can get the client to cooperate and use best practices! I usually have to threaten to never help them again to get them to do what has to be done to mitigate things like this. I’m pretty sure I have at least one client like this. Imagine how many more don’t even try to get help! I’ve given up on one client who has destroyed more than one of his own machines because he refuses to do what is necessary, even if I do all the maintenance for them! I’d wager there is a very large number of folks like that out there. I wish them luck with trying to get the users on each ISP to clean up their act! Maybe if they charged them a fee for being an infected client on their network – maybe THEN, they would finally WAKE UP!! They should allow providers the legal base to do this.
I recently had to deal with a computer repeatedly infected with a nasty piece of malware. Her laptop’s display was broken, so she decided to purchase a new one.
I convinced her to buy a Macbook Air. If I couldn’t change her behavior, at least I could change her risk level.
Brian, you mentioned that McAfee expects the seizure to coincide with a cleanup effort; have you seen any details on which ISPs will participate and how?
Are you seeing anything along the lines of “alert fatigue” among consumers after a series of high-profile security events this spring? Any thoughts on how we that are in the industry (corporate security analysts, independent researchers, bloggers, those known to our friends as “experts” whether or not true) can educate and address these events without our audience getting tired of hearing that they need to do something yet again?
Probably most of the ISPs out there will have a few infected people. I don’t know which ones will be participating, sorry.
Our ISP, AT&T, sent us this email yesterday:
AT&T has received information indicating that one or more devices using your Internet connection may be part of a zombie computer network (“botnet”). Internet traffic consistent with a bot infection was observed on Jun 1, 2014 at 8:00 PM EDT from the IP address xxx.xx.xxx.xxx. Our records indicate that this IP address was assigned to you at this time. Infection details:
Type: gameover-zeus-proxy
Source port: xxxxx
Destination IP: 192.xx.xx.2
Destination port: xxxx
For security reasons, the destination IP is partially obscured.
Yes, we were hit. Now I can’t get MSE to turn back on or update its virus definitions. Thankfully, I have all my data backed up, so I’m looking at reformatting my hard drive.
Whoa! Thanks for sharing that, LC. Was your internet access in any way restricted after receiving this notification? Did you receive any other communications (phone, email, etc.) from AT&T about this?
We received a very detailed email from AT&T; I copied a small portion before. Here’s more:
******************************************************
…
3. When you have taken action, please respond by forwarding this email to abuse@att.net with an acknowledgement of: “I am taking steps to address this infection.” When we receive such an acknowledgment, we can maintain the high quality of service you expect from us. We welcome feedback on what removal tools or methods were used.
Thank you for your prompt attention to this matter. We welcome your feedback and questions. Please contact abuse@att.net with any questions you may have by replying to this email, leaving the subject line unchanged.
…
******************************************************
I was afraid our Internet service would be temporarily shut down, but so far it hasn’t. I became aware something was up when I was browsing Amazon yesterday and was suddenly looking at a page informing me that my Amazon account was “locked due to suspected fraudulent activity” and that I could unlock it by filling in all my personal info, including my credit card number. That was the red flag for me and I immediately started investigating, not realizing we’d already been hit with it. Malwarebytes found 7 files and now I can’t get my virus scanner to update virus definitions or even turn on. I can’t even reload Windows 7, so I’m getting ready to reformat. Such a waste of time!!
Quote from Justice.gov:
“Here is what we did: first, on May 7, in coordination with the FBI, Ukrainian authorities seized and copied key Gameover Zeus command servers in Kiev and Donetsk.”
It’s a mistake. Donetsk is not in Ukraine anymore. It’s a new country called Donetsk People Republic. I doubt that USA has any deal with Donetsk People Republic. So seizing was illegal.
> So seizing was illegal.
I hope they do many “illegal” things to Evgeniy Mikhailovich Bogachev and his ilk.
You are Russian provocateur. Donieck is Ukrainian, there’s no such country as the one mentioned by you. Stop spreading war propaganda. Of course, Crimea is also Ukrainian, just occupied by Russia (you got used to doing this).
The Donetsk servers were seized on 7th May, four days before the referendum was held. If there had been any delay in taking action it is likely that access to those servers would have been impossible. It was a close call.
To quote (and translate) Grumpy Cat: НІ
I look forward to Russia’s future recognition of neighborhoods and similar areas that the owners have declared are no longer part of Russia and are, instead, the territory of another country. In this nouveau-secessionist movement all it takes is a public declaration to change nationalities; quite a refreshing change from the armed conflicts of the past.
Thanks, I will be following this.
It will be interesting how they plan to inform current
infected computer owners.
Will it be an email with a link?
I think it should start with an open letter to everybody telling them that bot pwned computers would be charged an extra “bandwidth” fee, and if they see this on their bill, they will know that is why they are getting stiffed! Then maybe they can help them individually as they call in wonder why they have this special fee on their bill! Actually I think this is the only legal way to do it, also!
At the ISP I used to work for, we frequently shut off people’s service for being infected. It’s part of the Terms of Service agreement.
I don’t believe there should be a fee for clients using a computer on a ISP that is infected. Regardless of the level of carelessness by the user, it is not their fault for the infection. It is the fault of the people administering/developing the malware.
There could be many reasons why they could still be running infected computers. I.E. they could perhaps not have the know how or money to pay a tech to come clean their machine.
I am perfectly fine with the ISP alerting the user of a potential infection emanating from their machine, and potentially suspending service if multiple alerts go unheeded/addressed.
I’d agree with prior notice and a time frame for action; the ISP could put up a site for newbies on how to mitigate much of the problem with standard security and cleanup practices, with links to free forums for computer help – but when it comes to suspension of service, you enter a trickier legal quagmire than you would with simply charging them a fee. The fees could always be reimbursed once the offending machine is taken care of. I definitely don’t feel it should be dealt with in any namby pamby way; because it just won’t work.
I have tried to train my clients to do simple things to keep them selves out of trouble, and make them more independent. I believe in working smarter, not harder. I get plenty of work even without these problems. But I also know that people can be stubborn, recalcitrant, and can’t see why they need to worry even when faced with the facts. Many of them never wake up until they literally have their network and/or machines blowup in their faces. For this reason alone, you are going to have to be firm, or nothing will come of it – and staying legal would be a requirement for an ISP interested in avoiding lawsuits.
This is excellent news, particularly the naming of a main suspect in relation to Gameover Zeus. However it sounds like only a temporary disruption is expected to the overall system. Perhaps it is too early just yet but It is noticeable that there has been no mention of recovered funds or recovered keys in relation to CryptoLocker. I’d like to hope that the long game has not been sacrificed in favor of scoring a fleeting victory.
On the one hand, going after the botnets will be inefficient; such actions, however necessary (and yes, they are necessary) leads to an arms race between law enforcement, IT security professionals around the world, and the malicious coders who create and run the nets. And it doesn’t take much for those folks to increasingly confound takedown attempts.
At the same time, it’s the *only* way to do things given that the countries these malicious programmers reside in don’t appear to give a damn about investigating and prosecuting them. If those governments would be willing to be a good neighbor and do so then maybe the ‘net would be a better place. But if pigs had wings, yadda yadda… the fact remains that those governments don’t feel the need to take action, and wishing otherwise doesn’t do jack to change that.
Evgeniy Mikhailovich Bogachev’s similar visage to Uncle Fester is justified karma… I’ll love to see him twitch in jail when, everytime he tries to use a keyboard, he’s given an electrical shock.
Easier said than done…as long as he’s in Russia, how are we going to arrest him?
It could be as simple as waiting for someone who’s overconfident in his intelligence and arrogant about his abilities to make a mistake. This is how countries, worldwide, arrest many international criminals.
The legal way is to simply wait for them to travel to an area you have an extradition treaty with. A quasi-legal way is to simply wait for them to travel to an area that you don’t have an extradition treaty with, but the authorities are willing to turn them over to you anyway (usually after a quid-pro-quo arrangement). All they have to do is commit a crime in that area (note: communicating with botnet = crime) and the balls get set in motion.
The former is a lot less problematic for the US legal system.
Hi! I need to ask something. Until now ‘Slavik’ was the developer of the ZeuS trojan, which gives it’s source away for everyone some years ago. Now this guy Evgeniy is also known as ‘Slavik’ but involved in CryptoLocker malware. They are the same person? Because so far, the developer of ZeuS was unknown.
Quick question guys, do the Russian / Ukrainian governments ( I know the latter is new so have plenty of other things they need to do first) not care because he only attacks Western companies (as the saying goes don’t s… where you eat) or is it the case they don’t know where he is or does he grease plenty of palms with the millions he supposedly brings in through cryptolocker, etc. so everyone turns a blind eye?
You can see from my cynical response up above that I feel that some governments don’t do jack about cybercrime. That said, even I admit that law enforcement activity in those countries is not zero.
Back in October 2013, the man behind the “Blackhole” and “Cool” exploits was arrested by Russian police. In April of that same year, a Ukrainian banking malware gang – 21 people, apparently – were arrested by Ukrainian police. Back in 2011, some credit card fraudsters/hackers were also arrested by the Ukrainian police in cooperation with the US Secret Service. It’s not like absolutely nothing happens, regardless of my curmudgeonly post above.
But it’s fair to say that not enough happens, and what little is happening is only fairly recent and stands out because they’re either new or exceptional events, not the rule. Senator Mark Warner back in March of this year charged that “The previous Ukrainian government routinely turned a blind eye to cybercrime”, and while he held out hope that the current one would be more active, the point remains that it’s talk about future hope, not present action and certainly not past activities. His cross party colleague and cybercrime bill cosponsor Mark Kirk agrees, noting that “Ukraine is a known hub for cybercrime…” and talked about how necessary it is for the US to work with that country to build a “framework” for fighting the problem. The positive being that the cooperation is being worked towards, the negative being that it’s not in place yet and that cybercriminals have thrived in those eastern European and Asian nations in the meanwhile.
At some point, I think – I hope! – that these “sheltering” governments will be more serious and active about fighting these crimes. But until then, it’s something the rest of the world has to suffer through.
Oh, unfortunately I don’t know the answer to whether the issue with those governments is simply blind-eye turning or outright payola. My guess is that it’s a bit more complex than that: Some blind-eyeness, some “We have other things on our plate” attitude, some simple ignorance about the nature of the problems, and so on. There may even be active corruption involved; I wouldn’t be surprised, but I simply don’t know.
Thanks E.M.H., I am surprised as surely they must at least attack some if not directly target Ukrainian / Russian Eastern European citizen’s, maybe it’s like Fred says below you that the Government security forces allow them to do it / turn a blind eye because they get the Intelligence in return.
This seemingly does happen as we have seen with the guy who has been released after less than 12 months in jail on Brian’s Ne’er-Do-Well News article.
It would seem that “the enemy of my enemy” is the paradigm which is in place here. Think in terms of La Cosa Nostra’s business model and you’ll begin to understand the workings of the latest batch of cybercriminals.
Someone or some thing is providing operational security for the lot of them. Motivators? Political and/or fiscal, plain and simple.
If I was a government covering for such a collection of actors, I would want any intelligence take as the price for allowing them to operate unfettered. Ponder that point, if you will.
I’ve been getting a ping timeout on krebsonsecurity.com for the past 5 hours Brian. The site resurfaced only a couple of minutes ago.
they forgot monstr as one of his nicknames.
he said he was retiring, but then he went on to write murofet/pony, gameover, and so on. This reminds me of the citadel authors making reveton, extra special for the spanish gang.
peer to peer isn’t entirely hard to take down. the c&cs are often usually hosted on victim machines’ NAT addresses like 192.168.*.* – if you can track down those, shut them down, clean those hosts, then you just keep it up. still hard, but not impossible. follow the trail of command centers.
cutting off the BP hosts that spawn these drivebys, is another issue though, it will never be done, as most are either in Russia, Romania, Latvia, Moldova, China, North Korea, etc.
they had said the same thing about onionland being hard to take down, but if you follow the breadcrumb trails…….just think outside the box.
putin’s not giving him up, no doubt, though…. we should wait until he goes somewhere where we have a treaty with, like our good ol’ bud-bud, Gribo.
derr for some reason the other posts didn’t go through…..?? …
anyway, we all knew slavik wasn’t retired. he went on to code gameover, along with pony and murofet, etc. reminds me of citadel authors making reveton for the spanish gang before the code being leaked and reveton gang being arrested.
the fbi forgot the pseudonym, monstr, which he used.
putin won’t give this guy up willingly, so we have to wait for him to go somewhere where we have a treaty, like our good ol’ bud-bud, gribo did.
also classic phishing technique. RS game scams go to runesca*Q*e [dot] com
If you are being told to click on a link to a website you have never seen before and do not know who the link is coming from, chances are it is going to be malicious. Emails claiming you have won something that tell you all you have to do is click this link or download this file to win a prize should be a dead giveaway. If you are unsure whether a website is credible or not, visit the website http://who.is/ to find out more information about the website such as when it was created and who it was created by.
Nowadays those links could be from any website. As long as a website has exploitable vulnerabilities, hackers can place malicious code in them or redirect victims to any infected page.
June 14?
The “14” indicates the year. Perhaps it would make sense if you take the date shown as being in the dd-mon-yy order that almost the entire world outside of the U.S. uses.
Yesterday I was talking to colleagues in the US and Canada and mentioned Brian’s piece about the Tovar operation. None of us could connect to the website, which appeared to be down. About an hour later we were able to connect. Did this site go down for a while, or was it simply overwhelmed by visitors?
Yes, the site was (and still is) under DDoS attack. Sorry for the downtime.
It was a DDOS, huh? I wondered about that…
Man, that’s such juvenile behavior by those criminals . More so given that they tend to be in their 20s or above. If one’s behavior is above reproach, then usually it can be defended without resorting to such attempted bullying tactics. If one’s behavior is not, DDOS’ing someone’s not going to change anybody’s perception of it.
They’re not good people, end of story. They may not be physically dangerous, murderous criminals, but that doesn’t change the fact they’re bad.
DATALOSSdb is announcing that an earlier dump by Anonymous Ukraine now includes some 7 million credit cards:
Update 7:40P EST – In addition to the 1 million cards disclosed earlier, Anonymous Ukraine has followed up with an additional leak of over 6 million more cards announced in a Tweet. Initial analysis of the new dump by RBS shows 6,064,823 new cards. That breaks down to 668,279 American Express, 3,255,663 Visa, 1,778,749 Mastercard, and 362,132 Discover. Counting the disclosure earlier today and the subsequent dump, the grand total now sits at 7,020,402. Upon cursory examination, a majority of cards seem to come from United States banks. Among the information released, approximately 4,000 come with full user data including social security number, credit card, card card expiry, name, pins, floats, dates of birth, states, and zip codes. The new Pastebin dump from the group also suggests the data may come from ATMs or POS systems.
Normally this blog isn’t the place for politics but with the events currently taking place in the Ukraine and Russia and the response from the West – we may just see more Western businesses plundered of their digital booty and the culprits firmly out of reach.
While Ukraine is in need of the West right now, how willing are they going ahead to hand over their compatriots involved in these activities? And as for Russia – the more we attempt to isolate them, the more they will entrench themselves. We’ve had decades to witness this so it wouldn’t be surprising that mould didn’t fit here as well.
I would love to learn more about how these people just get away with wiring $1,000,000 USD? Okay so they wire that out with no issue… to where??
Money mules are trusted with 10k a head. But 1 mill is a different game.
Let’s say they’ve set up a bank account in Latvia with a fake passport, and they wire it there. Then what?
The only way I’ve figured this to be even remotely untracable is if they were to then purchase 1 million dollars worth of Diamonds in person via wire transfer from the latvian bank, and then walk away with the hard goods.
How are they getting off with the money?
Here’s one very common way
http://krebsonsecurity.com/2011/04/fbi-20m-in-fraudulent-wire-transfers-to-china/
Thanks for your reply. That doesn’t really explain how they get away with it, though. I assume the companies are front companies set up just to receive the wires. Does China simply have zero interest in working with our FBI on what are clear-cut cases of fraud? Are they also internally choosing to simply do nothing when they could be shaking down criminals for million-dollar wire transfers?
At some point someone has got to walk into a bank and withdrawal a million dollars in cash, don’t they? Is that a thing? Are they using Hawala?
hmm… on second thought, maybe it’s not so terribly difficult. If they simply sent their bank a list of 300 fake employee names they could have been given 300 ATM cards and then cashed out 300,000$ per day with ATMs assuming some physical legwork is no issue. This is very people-heavy, though.
Also I have heard of Hawala being used to get $xxx,xxx in cash from offshore banks.
Cheap NBA Kendrick Perkins Jerseys authentic Good Quality Online For Sale
cheap nba jerseys for kids,cheap nba jerseys wholesale,Will Barton jerseys,nba jerseys wholesale http://maspromo.co.za/old_files.html