Previous stories in my Pharma Wars series have identified top kingpins behind the some of the biggest spam botnets. Today’s post does that and more, including never-before-published information on “Google,” the lead hacker behind the world’s busiest spam botnet — Cutwail.
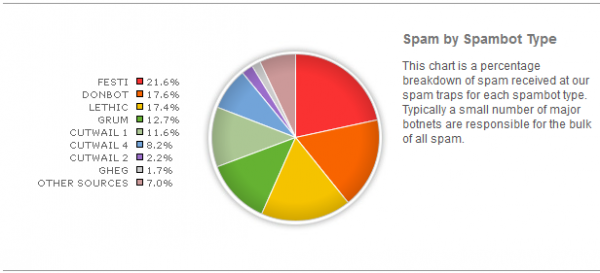
For many years, Cutwail has been among the top three most prolific spam botnets. With the recent takedown of the Rustock botnet, Cutwail now is the top spam bot; according to M86 Security, versions of Cutwail are responsible for about 22 percent of the daily spam volumes worldwide.
Security researchers have extensively dissected the technical machinery that powers Cutwail (a.k.a. “Pushdo” and “Pandex”), but until now little has been published about the brains behind it. Krebs On Security has learned that the individual principally responsible for developing and renting this crime machine to other miscreants was a top moneymaker for SpamIt, until recently the world’s largest rogue Internet pharmacy affiliate program.
By the time he joined SpamIt in early 2007, the hacker named Google had already spent several years fine-tuning his spam botnet. Just months prior to its closure in Oct. 2010, SpamIt was hacked, and its customer and affiliate data leaked online. The data shows that Google used close to a dozen affiliate accounts at SpamIt, and made nearly $175,000 in commissions advertising SpamIt’s rogue online pharmacies with the help of Cutwail.
But Google would make far more money renting his botnet to other spammers, and SpamIt affiliates quickly became his biggest client base. Interestingly, the proprietors of SpamIt initially asked for Google’s help not to spam rogue pharmacies, but to jump-start a new affiliate program called Warezcash to sell “OEM” software — mostly pirated copies of Microsoft Windows and other high-priced software titles.
That relationship is evident from hundreds of chat logs between Google and SpamIt co-founder Dmitry “Saintd” Stupin. The conversations were part of thousands of hours of logs obtained by Russian cybercrime investigators who examined Stupin’s computer. The chats were later leaked online, and provide a rare glimpse into the day-to-day operations of Cutwail from the botmaster’s perspective. They also provide tantalizing clues as to the real-life identity of Google and his co-workers. Snippets of those conversations appear below, translated from their original Russian into English by native Russian speakers.
THE CUTWAIL MACHINE
Some of the best techical analysis of Cutwail came earlier this year in a paper from researchers at the University of California, Santa Barbara and Ruhr-University Bochum, which described in detail how the Cutwail botnet was operated, rented and promoted on the exclusive SpamIt forums. From their paper (PDF):
“The Cutwail spam engine is known in spam forums by the name 0bulk Psyche Evolution, where it is rented to a community of spam affiliates. These affiliates pay a fee to Cutwail botmasters in order to use their botnet infrastructure. In return, the clients are provided with access to a Web interface (available in Russian or English language) that simplifies the process of creating and managing spam campaigns…”
SpamIt affiliate records show that Google registered with the program using the email address psyche.evolution@gmail.com (according to historical WHOIS records, the domain name psyche-evolution.com was registered in 2005 by that same email address, to an organizations called “0bulk corp.” in Moscow).
In several chats with Stupin, Google describes how he and his pals switched to pharmacy spamming when promoting stocks via spam became less lucrative. In a discussion on Feb. 25, 2007, Google said he was “renting software for spam,” to competing spam affiliate programs “Mailien,” “Bulker,” and “Aff Connection,” and that all of his clients had great success converting traffic into sales. “We have been spamming stocks, however now stocks started converting badly, so we decided to spam in parallel with some affiliate programs. We organized people, gave them tasks to do. We’ve been spamming them for a week only, but I think we’ll do good.”
From a chat dated August 16, 2007, Google explains how to use the Cutwail botnet:
1) Access to the interface: http://208.72.173.10:3571/login.cgi
2) Stats and loader: http://208.66.194.231:3081/ldr/vn.cgi
3) Manual about our software: http://208.72.173.10:3571/man.cgi
4) Technical support contacts/Personal ICQ addresses for support:
198922489 – Psyche Support 1
468559240 – Psyche Support 2
481896712 – Psyche Support 3
353149439 – Psyche Sypport 4
5) Contact of Manager: He handles questions about payments and all non-technical questions, also questions regarding complaints about the software and technical support, ICQ: 43266131
6) Technical support forum: http://psychetalk.com, Login saintd, Password: VeryNice
Google’s alliance with SpamIt would quickly cement the Cutwail botnet as a top contender. On Sept. 7, 2007, Google bragged to Stupin that his malware had “made it to #14” on Kaspersky’s most prevalent malware threats, pasting this link into the conversation. Kaspersky Labs confirmed that the Trojan Downloader.Win32.Agen.brk listed at #14 in that index is one of the aliases for a downloader Trojan used to deploy Cutwail.
GOOGLE’S IDENTITY REVEALED?
According to the Stupin logs, the SpamIt administrators worried that Google would not be mature enough to handle such a big operation, noting in one chat that Google was said to be only about 25 years old. Shortly after that conversation, on May 14, 2007 Stupin and Google agreed to hold a face-to-face meeting in Moscow to discuss the Warezcash OEM partnership. In that chat, Google asks Stupin to call him on his mobile number, which he gives as +7-916-4444474.
 That same phone number is tied to the historic Web site registration records for several domains, including antirootkit.ru, einfinity.ru, electronicinfinity.ru, hoha.ru, lancelotsoft.com, and ssbuilder.ru. In each record, the name of the initial registrant is “Dmitry S Nechvolod,” and the contact phone number is +7-916-4444474.
That same phone number is tied to the historic Web site registration records for several domains, including antirootkit.ru, einfinity.ru, electronicinfinity.ru, hoha.ru, lancelotsoft.com, and ssbuilder.ru. In each record, the name of the initial registrant is “Dmitry S Nechvolod,” and the contact phone number is +7-916-4444474.
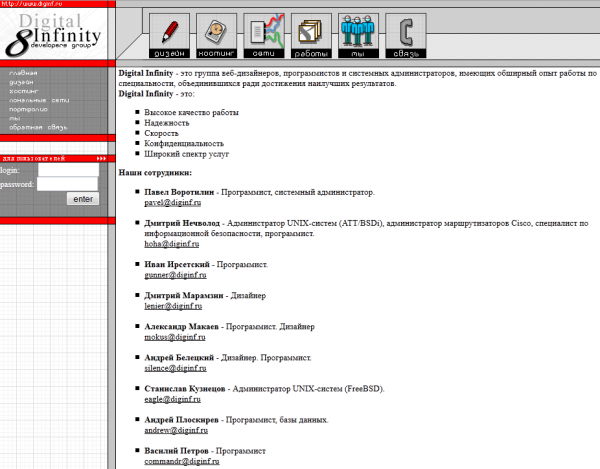
According to the Web site of Russian software firm Digital Infinity Developers Group (the search engine Google currently flags diginfo.ru as malicious), Nechvolod is part of a team of developers, and is described as an “administrator of UNIX-based systems (ATT/BSDi),” an “administrator of Cisco routers,” and “a specialist in information security software.”
It’s unclear whether Nechvolod is Google’s real name, a pseudonym, or merely clever misdirection to implicate someone else. But there are other interesting connections: spam.hoha.ru was at one point listed as a reliable place to rent mass spam campaigns, at least according to several members participating in this Russian Webmaster forum discussion.
Probably the best clue in support of a connection between Google and Nechvolod comes from the payment data that Google himself provided to SpamIt. Google asked SpamIt administrators to send his affiliate payments via WebMoney, a virtual currency that is quite popular in Russia and Eastern Europe. He requested that his commissions be paid to the WebMoney purse Z046726201099. According to a source that has the ability to look up identity information tied to WebMoney accounts, the personal information provided when this account was opened in 2004 was:
Нечволод Дмитрий Сергеевич (“Nechvolod Dmitry Sergeyvich”)
• Passport – 4507496669
• Date of Issue (ММ/DD/YYYY) – 7/23/2004
• Place of Issue – Moscow/Russia
• Issued – ATS District Cheryomushki
• Date of birth (as on passport) – July 9, 1983
• E-mail – wm.lancelot@gmail.com
• Telephone – +7 9164444474
Another strong link provided by Google (the search engine Google, not the spammer) stems from one of the domains registered to Nechvolod — einfinity.ru. In 2006, a Stanislav representing himself as a job recruiter for a company called “E-infinity” posted a message to the Russian programmer forum Delphimaster.net that he was seeking UNIX programmers for work at an E-infinity office in Moscow. Stanislav asked interested applicants to contact him at ICQ number 903445.
SpamIt affiliate records show that in Sept. 2007, a new spammer signed up with the usernames Feligz/Eagle providing the email address maravanio@gmail.com and ICQ 903445 as his contact information. Stupin’s ICQ chat logs show that on Sept. 3, 2007, Stupin contacted Google’s manager (ICQ 43266131, see above) about an urgent problem, complaining that he was unable to reach Google or two of Google’s usual support personnel by ICQ or by phone. The manager says he will try to get in touch with the technical director within Google’s operation, a hacker who uses the screen name Eagle. Minutes later, Stupin receives an instant message from Eagle, who is using the ICQ number…wait for it….. 903445.
Remember the page at Diginf.ru referenced above that lists Dmitry Nechvolod as a system administrator? That same page lists a Stanislav Kuznetsov as another team member. What is Stanislav’s email? Eagle@diginf.ru.
CRIMEWARE EVOLUTION
For a variety of reasons, spam is not nearly as prevalent as it once was. According to a recent report (PDF) from Symantec, just 70 percent of email sent worldwide was spam in November 2011, the lowest rate since the rogue ISP McColo was shut down in late 2008. At that time, about 90 percent of email was junk.
Cutwail may have begun as a popular vehicle for sending male enhancement and OEM software spam, but in recent years it has morphed into a major spam cannon for malicious software. These days it seems more often involved in sending emails that try to trick recipients into opening malware-laden attachments, most often variants of the ZeuS and SpyEye trojans.
Information obtained by KrebsOnSecurity.com shows that as early as 2009, Google’s botnet was hired by a Ukrainian cyber fraud gang known as the JabberZeuS crew to help spread malicious emails that the gang used to conduct a number of lucrative cyber heists.
More recently, Cutwail has been seen sending out malicious spam campaigns with a variety of themes such as airline ticket orders, wayward Automated Clearing House (ACH) payments, Facebook notifications, and scanned documents. On Dec. 19, Microsoft warned about a Cutwail campaign that was blasting out ransomware attacks that used information about the recipient’s geographic location to tailor the email lure, which spoofed various national law enforcement organizations and warned victims that they were being investigated for possessing child pornography.




Excellent article, and groundbreaking stuff. Is it too much to hope that Dmitry Nechvolod will fall in much the same way as Leo Kuvayev, Igor Gusev and Pavel Vrublevsky? And is it too much to hope that Microsoft will stage another coup over Cutwail, a sizable target worth chasing down?
What’s wrong with Gusev & Vrublevsky? Both of them are free of jail, Igor now somewhere in Europe or Maldives, Pavel lives at his home in “Rublevka” (elite Russian district near Moscow).
Брайан, ты ты в свой почтовый ящик заходишь? Почему не отвечаешь? Начинаю беспокоиться. 🙂
Что за болваны минусуют?
looks like someone just got “Krebsed” 🙂
Never ceases to amaze me how these people involved in such massive levels of criminal activity make the simplest of mistakes that allow them to if not be identified then at least have strong evidence of their identity revealed.
Maybe it’s just a reflection of how secure they feel. Or just maybe it’s an elaborate ruse as Brian points out (however this would involve years of planning and execution going on the dates in the article).
In any case these leaked Spamit documents are certainly a treasure trove and I’m looking forward to the next post with more analysis.
Since these are two very sensitive areas for Microsoft (Pirated software and Windows; being the larger OS base)…I really hope they are all over this. Not that I mind SPAM as it pitches-in revenue…but I am tired of the crap and broken computers because of sloppy dev’s…not that this guy is sloppy…just saying!
Congrats, Mr. Krebs, you’ve made the list!
“List of Websites the DHS Is Monitoring January 2, 2012”
http://cryptome.org/2012/01/0001.pdf
real Cutwail is one in big economy, you working in AV company and you run big botnet for converter profit money .
i see all same coder GRUM botnet know tedroo spambot
he working comodo but he code it’s and help spammer rent it’s and see here http://www.m86security.com/labs/bot_statistics.asp
^^ grum always in #10 top big spam botnet same cutwail,Lethic,Festi and more
they need loader know bot download spam bot every day
150k-250k/per day mix and i sell it’s for all use.
Easy know all if you working in economy russia spam underground!
goodluck kreb.
You have published personal information.
Saying something like Mr.X is cybercriminal or Mr.X is cyberterrorist without trial verdict is not something right also.
I know that it’s typical trait of Americans – they want to render justice at same the moment without any court sentences.
@Ivan…
the information in this story is not personal. It’s data taken from public Whois records, plus information from a criminal enterprise that got “wikileaked” online. Krebs is just drawing the connections between different elements. you are free to draw your own conclusions.
“The data shows that Google used close to a dozen affiliate accounts at SpamIt, and made nearly $175,000 in commissions advertising SpamIt’s rogue online pharmacies with the help of Cutwail. But Google would make far more money renting his botnet to other spammers…”
How much more? $175,000 is a nice chunk of change if the dollar sign is accurate and this is being converted to his native currency!
This report makes a lot of sense in conjunction with this report http://www.secureworks.com/research/threats/pushdo/ . Both suggest that the author is more familiar with UNIX systems.
Hello, Is this a typo in the article “according to historical WHOIS records, the domain name pysche-evolution.com” or was the address really pysche-… but the name of the software Psyche … ?
Very interesting read! The use of the pseudonym “google” is confusing though. 🙂
Yes, that is a typo. Thanks for pointing it out. Fixed.
As G. Cluley from Sophos observed yesterday, what better way to hide than to pick a screen name like “Google”. 🙂
TNX for reply. Truly, that is a clever hiding strategy. You can google a Feligz, but you can not google a Google. This would break the internet!!!11elf 😉
Congrats, Mr. Krebs, you’ve made the list!
“List of Websites the DHS Is Monitoring January 2, 2012″
http://cryptome.org/2012/01/0001.pdf
The “bury interesting posts” crew is at it, AGAIN.
You got mentioned in the daily open source infrastructure report, item 34.
http://www.dhs.gov/xlibrary/assets/DHS_Daily_Report_2012-01-05.pdf
More Adobe Flash Player Vulns, Remote Exploit(s):
– http://www.securityfocus.com/bid/49710
– http://www.securityfocus.com/bid/49717
– http://www.securityfocus.com/bid/49718
– http://www.securityfocus.com/bid/49716
Dont you love closed source? Thanks, Adobe!
Not sure why you’re posting these. Kind of OT. Anyway, they appear to have been patched already.