Adobe has released an emergency update for its Flash Player software that fixes three critical vulnerabilities, two of which the company warns are actively being exploited to compromise systems.
 In an advisory, Adobe said two of the bugs quashed in this update (CVE-2013-0643 and CVE-2013-0648) are being used by attackers to target Firefox users. The company noted that the attacks are designed to trick users into clicking a link which redirects to a Web site serving malicious Flash content.
In an advisory, Adobe said two of the bugs quashed in this update (CVE-2013-0643 and CVE-2013-0648) are being used by attackers to target Firefox users. The company noted that the attacks are designed to trick users into clicking a link which redirects to a Web site serving malicious Flash content.
Readers can be forgiven for feeling patch fatigue with Flash: This is the third security update that Adobe has shipped for Flash in the last month. On Feb. 12, Adobe released a patch to plug at least 17 security holes in Flash. On Feb. 7, Adobe rushed out an update to fix two other flaws that attackers were already exploiting to break into vulnerable computers.
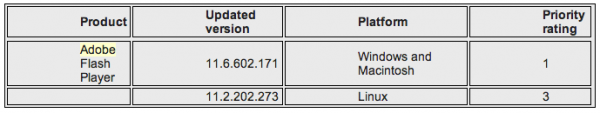
Updates are available for Windows, Mac and Linux installations of Flash (see the chart below for the appropriate version number). This link should tell you which version of Flash your browser has installed. The most recent versions are available from the Adobe download center, but beware potentially unwanted add-ons, like McAfee Security Scan). To avoid this, uncheck the pre-checked box before downloading, or grab your OS-specific Flash download from here.
Chrome and Internet Explorer 10 have built-in auto-update features that should bring Flash to the most recent version. The patched version of Flash for Chrome is 11.6.602.171, which Google appears to have already pushed out to Chrome useres. Windows users who browse the Web with anything other than Internet Explorer will need to apply this patch twice, once with IE and again using the alternative browser (Firefox, Opera, e.g.).



What a pile.
I’m getting tired of these patches, why don’t they start paying up for the real pro’s to find these flaws internally and start pushing these in a normal release
They do, the prior update preemptively patched 17 vulnerabilities that were not exploited in the wild. However due to the nature of zero days, you can’t catch them all.
Happens to the best companies, including Firefox, the last being the nobel peace prize zero day hack in 2010 that specifically targeted Firefox users.
On another note, wasn’t the Sandbox they introduced for Vista/Seven systems supposed to mitigate this kind of stuff? I read the security bulletins but they were vague, they just stated Windows, along with Mac and Linux without any specifics.
Secondly, how fast did they patch it? When were the exploits first reported? Firefox back in 2010 looked like they patched it in a day.
The zero-day exploit apparently includes a sandbox escape. Adobe and Mozilla recently implemented a sandbox for the Flash Player plug-in on Firefox (Windows Vista/7/8 only). The sandbox utilizes Windows integrity levels introduced with Windows Vista. More here (linked in Brian’s article):
http://www.adobe.com/support/security/bulletins/apsb13-08.html
“This update resolves a permissions issue with the Flash Player Firefox sandbox (CVE-2013-0643). *
“This update resolves a vulnerability in the ExternalInterface ActionScript feature, which can be exploited to execute malicious code (CVE-2013-0648). *
“This update resolves a buffer overflow vulnerability in a Flash Player broker service, which can be used to execute malicious code (CVE-2013-0504). **
A good time to download the NoScript add-on for Firefox and start whitelisting frequently-visited (and legitimate) web sites for JavaScript and plug-ins.
* Vulnerabilities used in the exploit.
** The [privilege] broker service is associated with the Flash Player sandbox.
Sandboxing the browser as a whole could be worth it to the security-minded as well. Sandboxie is a well-known solution for Windows users. It’s free for non-business use, although their site states that it’ll give you nag screens after 30 days to remind you they’ve got a paid version with more features.
I’d also be interested to hear anyone’s results at forcing FireFox to run at Low integrity using icacls. Microsoft has a generic how-to here: http://msdn.microsoft.com/en-us/library/bb625960.aspx Maybe I’ll toy with it in a VM this weekend, as I have some idle Win7 licenses right now.
If you rely on FileHippo for notification of updates for software installed on your computer(s), be wary of direct downloads for the IE and non-IE versions of Flash as they are just 65Kb stub installers and will subsequently download another installer file that seems to contain even more bloatware than reflected in the easily-found versions which Adobe pushes. Use the OS-specific link Brian provides above to get the full installer files for whatever flavor(s) needed which don’t have any add-ins.
Good tip, thanks for the warning JimV.
The first news I got about this particular update was that my Win8 boxes at work had it queued up to install from Windows Update, since Flash is built into IE10 on Win8 systems.
For those who might like to tweak Group Policy on Windows systems, you can enable a setting in Computer Configuration > Administrative Templates > Windows Components > Windows Update named “Allow Automatic Updates immediate installation.” When enabled, this should allow systems to install non-disruptive updates on the spot, rather than waiting for the next designated installation time (e.g. 3AM). There’s also an “Automatic Updates detection frequency” setting in there.
Group Policy, it’s awesome 🙂
Apparently mine updated itself with the Adobe auto updater, or Secunia PSI did it – either way I was rechecking the version and noticed it had changed again, a day or so ago. I’m sure glad you’re watching this Brian, because Adobe can make my head spin sometimes! O.o
Come to think of it – do we even need the actual flash plugin anymore? One of my clients was surprised to find that FireFox was playing flash files just fine with no flash installed!
Does this mean HTML-5 capability is already available on Mozilla’s version 19?
Firefox and I believe other browsers have been HTML5 enabled for a few years now, just been waiting on sites to catch up – which they’re finally starting to. Some things like youtube have been html 5 for a while also (although occasionally I still find the odd video that won’t play, but not enough to say so). Even if you animate in flash you can always just upload the videos on youtube, which again, can be HTML 5. And if you do games, then just make your games downloadable. So, for us, I’d say we’re pretty much at the stage where we can live without it in our browsers. I might even uninstall after I type this and see what happens. If it works out, I’ll be plugin free.
For clients on the other hand then it becomes like Java for the odd thing that needs it. Or if they have kids, then games.
Follow up: Within a few minutes of disabling it I found a low view count youtube video which wouldn’t play with flash disabled. However I found a workaround: just download it with something like Video DownloadHelper and just watch the video in whatever player you like. So long flash. If anything, you could just treat it like Java and use the two browser approach for things that just have to have it. My main browser now has zero plugins. *flex*
For those who want it:
https://www.youtube.com/html5
Second thing is: What do you mean by “FireFox was playing flash files just fine with no flash installed”? I know you mean flash-like html 5 stuff, but what sites? Just wondering.
“What do you mean by “FireFox was playing flash files just fine with no flash installed”? I know you mean flash-like html 5 stuff, but what sites? Just wondering”
My answer: Near as I know he was going to news feeds, political sites, and YouTube, if that helps. Your test was very interesting!!! Thanks for your expertise and input here! 🙂
If I’m not mistaken, he claimed PDF documents worked despite not having Adobe or Foxit Reader installed as well! He had just re-installed his operating system, and was going to rely on download alerts to give him the latest plug-ins/extensions – but he obviously doesn’t feel the need for them anymore! :O
I did a little test. I uninstalled the Flash plugin for Firefox and then tested a few sites using the Firefox browser. Youtube and the Onion worked just fine. I ran only one Youtube video. The following sites required the Flash plugin: Aljazeera, BBC, CNBC, CNN, Fox News, the New York Times and the Wall Street Journal. Therefore, it is with great sadness that I must announce that I will reinstall the Flash plugin.
Replying to Old School as well (nice work btw, it’s interesting to know what still uses flash)
Well, if he’s using Firefox 19, they have a built in .pdf reader now (and I believe Chrome does too).
Adding to News Sites, streaming sites in general don’t work without flash (their chatboxes included). Official TV/Movie sites are also flash heavy, for example, “The Hobbit” almost works without it but uses flash for video. Others are just full blown sites in flash just to be flashy.
Personally I’m leaving it disabled, or maybe toggleable, or even using a secondary browser -anything but “always on”. I really like the idea of your main browser being a kind of tank with a mine roller. You could say “Well gee, Vee, isn’t that overkill if you have noscript?” and I don’t feel it is. Over the past few months I’ve either gotten rid of or disabled in browser Java, Adobe Reader and Shockwave. Flash is the last plugin standing.
While I agree news sites are a legit use of flash (until they do it without it), the Flash plugin has always just been mainly either advertising or entertainment. And how do you force people to dump flash when there’s just so many people plugging away at Facebook games like Farmville? Yeah, sure, some of the Facebook games are html 5, but surely not all of them. I don’t know, flash needs some really heavy white listing functions for the general users. Or maybe, again like Java, Adobe Flash stuff should be run outside of the browser somehow, using a sort of whitelisted flash viewer for all legit sites that use it. But, I’m dreaming here.
Thank you Old School and Vee; your input is fascinating. I’m glad the subject came up! Maybe plug-ins like this will be obsolete soon. I did read somewhere(probably here) – that Adobe will continue to support flash, but will code with HTML-5 and produce kits for developers along that line. That is what my foggy memory tells me anyway.
It was an article that supposedly rang the death knell for flash as an separate application.
Another follow up. I just read Firefox 20 might get H.264 support (I hope the new HEVC/H.265 comes soon after) and that might fix some of the video playback issues with Youtube, possibly even make some of those news sites work. Right now Firefox 19 relies on WebM.
Yeah, they’ve been screaming that HTML5 is a flash killer since it first appeared, but time will tell. Adobe is like Java, there’s a place for it if that place isn’t with a browser plugin. Their creative software, like Photoshop, Flash CS6 and Premiere Pro (video editor) are really good with their only drawback being their price.
And yeah, I’ve been enjoying swapping tips and feedback around here.
Another follow up and then I’ll shut up about Flash.
I found some more interesting things. One is IE 10 apparently has started a Flash whitelist: http://www.zdnet.com/an-inside-look-at-internet-explorer-10s-mysterious-flash-whitelist-7000009740/
And then I found two more things that rely on Flash that don’t have a workaround unless you use a secondary browser. First is Google Street View relies on it. Second is “Videos with ads are not supported (they will play in the Flash player)” with Youtube, but hopefully long term they’ll fix that.
Until Firefox does something similar like IE 10’s Flash whitelist, I’m leaving it disabled.
Last thing!
https://blog.mozilla.org/security/2012/10/11/click-to-play-plugins-blocklist-style/
“This feature is enabled by default, so users are automatically protected. For the adventurous, the about:config preference “plugins.click_to_play” can be set to true to enable click-to-play for all plugins, not just out-of-date ones. However, this aspect of the feature is still in development”
So I’m doing that. Flash enabled again, but leashed.
I may have to include flash in my .exe file in EMET if this keeps up – I already do java (Thanks Jim V for that tip!) 😀
Hi JCitizen,
I am glad that you finding EMET useful. It is a great tool that does not always receive the attention it deserves.
If you are using EMET and have applied the All.xml protection profile located at either of the file paths below and as described in the short Microsoft video linked to below, you have already protected the Flash add-in using EMET:
64 bit Windows:
C:\Program Files (x86)\EMET\Deployment\Protection Profiles
32 bit Windows:
C:\Program Files\EMET\Deployment\Protection Profiles
Microsoft Video:
http://www.microsoft.com/en-us/showcase/details.aspx?uuid=7683a9cb-28c9-428f-ada6-8adafd2efbee
All.xml protects the Flash Plugin Container (plugin-container.exe) of Firefox as well the browser itself and all of the other major browsers, Apple Safari, Opera, Google Chrome and IE.
In the following thread on the EMET forum I have also added some further programs that I believe the next version of EMET should protect. Unfortunately, my suggestions have not received any positive/negative feedback yet:
http://social.technet.microsoft.com/Forums/en/emet/thread/46be01a8-6aac-4bca-a469-185d1a93e3be
If I can be of any further assistance, please let me know. Thank you.
Thanks again JimboC; I finally got the “All” profile on board. I had to disable some of the protections for iexplorer.exe, probably because I have Trusteer installed. I disabled one of them at a time until I could get Internet Explorer to open. My ATI driver was irritated at first, but has settled down. So far I haven’t found any other crashes yet. We will see. I wonder if it is worth trying EMET 3.5, or if any further stability will be gained?
Hi JCitizen,
I am glad to hear that Internet Explorer is working fine with EMET, it can be tricky to achieve sometimes.
EMET 3.5 adds 5 more mitigations to the existing 7 that are specifically designed to defend against exploits that make use of Return Oriented Programming (ROP) e.g. the exploit for the recent Adobe Reader XI 11.0.01 flaw and the Internet Explorer 6 – 8 flaw from January.
EMET 3.5 is not perfect yet e.g. it has a known issues when all ROP mitigations are enabled for the Snipping Tool (of Windows Vista and later) when it is used to take a screenshot of Internet Explorer. My thanks to mechBgon for his useful workaround of this issue:
http://social.technet.microsoft.com/Forums/en-US/emet/thread/2aee15fb-d339-4d5e-b403-9d221c6b8ffb/
According to Jonathan Ness, Microsoft’s Security Development Manager there will be another beta version of EMET 3.5 this month with the final version scheduled for release in the Summer (if all goes according to plan). Here is the link to his Twitter feed that mentions this:
https://twitter.com/jness/status/302128486804500481
My concern is that there were beta versions of EMET 3.0 last year and I was not aware of them i.e. I didn’t know they were available at the time and didn’t know where to download them from. I hope this year’s betas are more widely publicized.
A video of EMET 3.5 new capabilities is available from the following link:
http://www.microsoft.com/en-us/showcase/details.aspx?uuid=05d4872b-9130-4b36-a45c-9d0195763a9e
I am going to wait until at least the next beta of EMET 3.5 before I switch over to it. I hope this helps. Thank you.
Thanks again JimboC! I will take heed of your advice! 🙂
I may try v. 3.5 soon!
Brian – I think fatigue is an understatement…I spent over an hour at home trying to patch my browsers last week and there is still an adobe reader patch that the Qualys browser check flagged as unpatched, even after multiple applications of the patch / reboots, etc. I’m a risk / security professional and I can barely get it done or keep up. I’ve checked auto update in the browsers for the different products and this doesn’t seem to be getting the job done. Couple of questions:
1. How is the average user without a security hat on ever supposed to keep a system patched and up to date if the auto updates do not always work / turned on by default?
2. I don’t use IE often, but some govt. sites won’t render correctly without IE / Silverlight, etc… Q. If I never used IE, would I still need to patch it because while browsing with a fully patched Firefox browser, potentially a driveby download malware version could detect IE (even though not currently open) on the OS and use this as a vector to root the box?
3. How does malware like Zeus, etc. open a browser without the end user seeing it? What is the technical name for this ‘hidden browser’ so I can do more research?
Thanks as always for your great reporting! WL
This is a problem I come across a lot as well…
Good security design says not to let end users run as admins – so when programs can’t update themselves there is often nobody else around to do it for them…
Trying out Secunia PSI/CSI to see if it can resolve, I think there are a lot of corporate machines prone to this issue.
I’ve tried Secunia PSI on limited accounts and sometimes it works and when it doesn’t it at least lets you know with a popup that you need to do a manual update. I am using it on Vista Premium x64 to fairly good affect.
However I think Adobe’s auto updater did this last one, because it happened the day it came out; Secunia used to be 5 days behind. I never had to log in as administrator to get it to update – it didn’t alert me to the update either. I just look at the program version list in CCleaner to keep an eye on version information, and track it that way.
In the recent past, I’ve logged into the Administrator account and saw File Hippo suddenly report that a flash update was no longer needed – this because Adobe’s auto updater beat it to the punch a few seconds early during the log on process. I don’t know why it works seamlessly one day and not the next – but I’ll take what I can get. It definitely makes for a better security silhouette than the way I had to operate in the past. Zero day exploits will be harder to come by for the criminals in these instances.
You know, I once had a corrupt Adobe Reader install that I couldn’t remove/update. I finally removed it with:
http://labs.adobe.com/downloads/acrobatcleaner.html
So you could always try scrubbing it off your system and install the latest version fresh.
I’ll try to answer your other questions too best I can.
1. Well, one could say the same about car upkeep. You either learn it yourself or hope you know someone that knows about it. Which isn’t saying software giants should be excused from sloppy update methods, but how many of us can say we’ve never had a Windows Update go wrong? I’ve also said on here before I’d rather see Windows do a Linux way of updating all software installed, but I’ve had Linux updates go wrong too. That’s why I usually disable automatic updates on my own machine (but keep alerts on). When I can, I opt for clean install of software rather than installing over or patching to avoid issues. Pick your battles sort of thing.
2. Yes, you should always keep up on IE updates. IE has always been so tightly woven into Windows you can’t really remove it. If you can’t remove something, then you have to update it.
“Q. If I never used IE, would I still need to patch it ”
Yes. Some of its components could be called by other software, such as Office. I recently read a malware writeup (don’t remember which one, sorry) where this was the case.
In the big picture, you’re pointing out the difficulty of keeping everything up-to-date, particularly from a low-rights account. IE being a Windows component, it’s seldom an offender in that area. Ditto for the PDF reader and Flash Player on Win8. When I was convincing my boss to get the special-price $40 Win8 Pro upgrades for our SOHO environment, that was one of my arguments: the less time I have to spend updating PDF readers and Flash Player, the more time I can spend doing “the day job,” at a shop rate of $60/hour. The upgrades pay back their up-front cost in months just on that basis alone.
Thanks for the heads-up. BTW, Brian Krebs, it seems that you have posted something new on your website, but you don’t even share it on Facebook. Is there something wrong? 🙁
Thx all for the feedback and recommendations. I’ll take a closure look at Secunia and the other suggestions. I normally run as non privileged user..only logging in as admin when required or to do installs.
!BTW..can anyone answer my question #3? thx!
3. How does malware like Zeus, etc. open a browser without the end user ever seeing it? What is the technical name for this ‘hidden browser’ so I can do more research?
Any software (that runs on a computer that’s connected to the Internet) can, by default, connect to any computer on the Internet. This is called a “TCP socket”. The program “netstat” can be used to check what sockets are open; one of the configuration options for it shows what program is currently responsible for each socket. The program “tcpview” does the same thing with a much nicer interface.
As far a Zeus goes; I’d be more worried that they can ride your SSL session into the bank site when you log in. After that – they pretty much got complete control of your finances. That is – if your bank allows that sort of thing off the internet!
Mine doesn’t – you have to show up physically at the bank with the account number of your payee or vendor, before they will vouch for an electronic transfer.
I hate adobe. Not only are the updates incessant, but now they have changed their downloader and my MAC insists on treating the file as a Matlab file and opening it with that program.
How does that company stay in business?