DocuSign, a major provider of electronic signature technology, acknowledged today that a series of recent malware phishing attacks targeting its customers and users was the result of a data breach at one of its computer systems. The company stresses that the data stolen was limited to customer and user email addresses, but the incident is especially dangerous because it allows attackers to target users who may already be expecting to click on links in emails from DocuSign.
San Francisco-based DocuSign warned on May 9 that it was tracking a malicious email campaign where the subject line reads, “Completed: docusign.com – Wire Transfer Instructions for recipient-name Document Ready for Signature.” The missives contained a link to a downloadable Microsoft Word document that harbored malware.
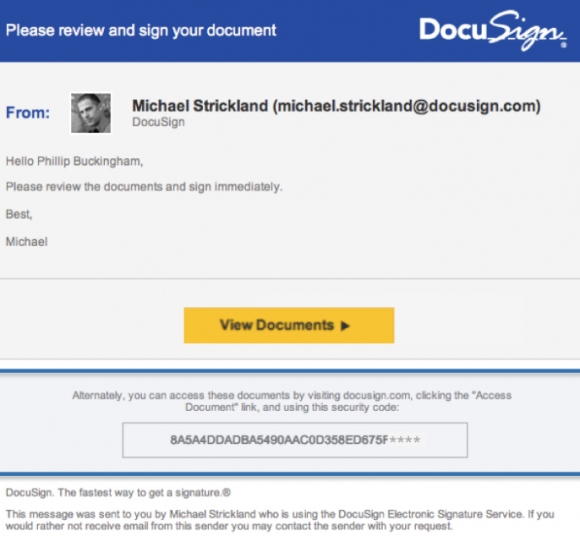
A typical DocuSign email. Image: DocuSign.
The company said at the time that the messages were not associated with DocuSign, and that they were sent from a malicious third-party using DocuSign branding in the headers and body of the email. But in an update late Monday, DocuSign confirmed that this malicious third party was able to send the messages to customers and users because it had broken in and stolen DocuSign’s list of customers and users.
“As part of our ongoing investigation, today we confirmed that a malicious third party had gained temporary access to a separate, non-core system that allows us to communicate service-related announcements to users via email,” DocuSign wrote in an alert posted to its site. “A complete forensic analysis has confirmed that only email addresses were accessed; no names, physical addresses, passwords, social security numbers, credit card data or other information was accessed. No content or any customer documents sent through DocuSign’s eSignature system was accessed; and DocuSign’s core eSignature service, envelopes and customer documents and data remain secure.”
The company is asking people to forward any suspicious emails related to DocuSign to spam@docusign.com, and then to delete the missives.
“They may appear suspicious because you don’t recognize the sender, weren’t expecting a document to sign, contain misspellings (like “docusgn.com” without an ‘i’ or @docus.com), contain an attachment, or direct you to a link that starts with anything other than https://www.docusign.com or https://www.docusign.net,” reads the advisory.
If you have reason to expect a DocuSign document via email, don’t respond to an email that looks like it’s from DocuSign by clicking a link in the message. When in doubt, access your documents directly by visiting docusign.com, and entering the unique security code included at the bottom of every legitimate DocuSign email. DocuSign says it will never ask recipients to open a PDF, Office document or ZIP file in an email.
DocuSign was already a perennial target for phishers and malware writers, but this incident is likely to intensify attacks against its users and customers. DocuSign says it has more than 100 million users, and it seems all but certain that the criminals who stole the company’s customer email list are going to be putting it to nefarious use for some time to come.




I used Docusign last year when selling a house. Sure enough, got one of these phishing emails yesterday. Had it arrived in the middle of that deal I would have opened it.
Shame on Docusign for not protecting their info. Oh, and death to the perps.
I’m in the process of selling/closing on my house and have recieved several of these phishing emails-
Mon 6/12/2017 11:45 AM
To:
valparaiso6@msn.com;
larsenbk3@msn.com;
This message was identified as spam. We’ll delete it after 10 days.
You forwarded this message on 6/12/2017 12:01 PM spam@docusign.com
Please review your document Invoice 1084013 for msn.com
William Scott via DocuSign
DocuSign
Your document is ready
REVIEW DOCUMENT
Your Invoice 1084013 from msn.com for May Document is Ready for Signature.
Please review and sign your Invoice 1084013 from msn.com for May
via DocuSign by clicking on the “Review Document” button above. Signing will not be complete until you have reviewed the document and confirmed your signature. Please contact us if you have any questions. Thank you.
Powered by
DocuSign
Do Not Share This Email
This email contains a secure link to DocuSign. Please do not share this email, link, or access code with others.
Alternate Signing Method
Visit DocuSign.com, click ‘Access Documents’, and enter the security code:
4C850
EC8F62G15E7A408B5763385
E2171
About DocuSign
Sign documents electronically in just minutes. It’s safe, secure, and legally binding. Whether you’re in an office, at home, on-the-go — or even across the globe — DocuSign provides a professional trusted solution for Digital Transaction Management™.
Questions about the Document?
If you need to modify the document or have questions about the details in the document, please reach out to the sender by emailing them directly or replying to this email.
If you are having trouble signing the document, please visit the Help with Signing page on our Support Center.
Normally someone requiring that you sign a document through Docusign would tell you in advanced they are sending this to you by email. That is the key. If you receive it over email without being alerted it is coming your way, then confirm with a phone call it was sent to you by the individual claiming it is from.
Be sensible with regards to email and things will be okay.
Kinda scary that a company like DocuSign gets to keep so much sensitive information. Everything from mortgage applications to background checks and smart contracts. Their databases are a treasure for manu different purposes, the least concerning if which is phishing. The documents are not encrypted with the user’s password or some other way to ensure that nobody other than the users can view them. Without this assurance, I just don’t trust them.
The subject line is morphing… now saying things like “legal documents for your approval”. The compromise at docusign explains why these are so targeted. Mine came from dousign.com while I was coincidentally awaiting legitimate docs from an attorney.
Nice updates.
How difficult would it be for these hackers to use informal lingo? Like: “Hey Phillip, could you review this and get back to me once you signed it?”
What is docusign? nobody dont use this crap anyways !!
I never use so its some crap,not needed.
i
I’ve used it to close the sale on my house. It came in handy without the need to travel just to sign papers while working with the Real estate agent.
One more reason not to trust ANY cloud-based solutions, including Dropbox, Google Drive and One Drive.
The only time I would trust such cloud service when we agree to share a particular folder and I ascent to be included. Worked great with Google Drive while I was working on a project at graduate school.
And no internet based email either, right?
This isn’t a “cloud” problem. Any organization that does anything near the Internet can be susceptible to attack, and needs to be vigilant (and avoid cutting any corners).
-ASB
I contact them before they made the announcement that they got hacked. My concern was the personal information on the documents I sent and received using their service.
After addressing my concern with customer service and management, they gave me a “Case” number and they would follow up the next day. Of course, they did not follow up with me.
The 2nd wave of phishing came again last week. Here we go again.
I have a feeling they are not telling us everything.
I used to work with their “Security Architect” when he was an email administrator years ago. I can tell you that covering up is the primary focus there. Not accountability, ownership, troubleshooting, nor future mitigation. Run fast. Run far.
I don’t think I ever used them that I remember. They hit my customer service email right after, and I mean within minutes of a legit ssl service that is setting up an ssl on my new site telling me to watch for an email to click to confirm the legals that I wanted to do that … they are not DocuSign and the legit email came about hour later BUT the hack came immediately, it looked legit, their name is recognizable for needing to sign something and I was expecting a email with a link to click to sign off … and I did … it went to a site in India running a php page with active code on it … I’ve been down all day trying to be sure I am clean and can go back to work … this is bs what DocuSign is saying … the odds of getting this email within minutes of being told to watch for one is slim to none … I think I just experienced that they hacked deeper into their system and the hack is monitoring email accounts that would tip them to “send to that one they are expecting” … this has cost $100’s in downtime, a day of productivity lost a few of my clients pissed off that I am not online to help them …
If all they got was email addresses then how did they get my name which was in the body of the email text. It was even spelled correctly, which doesn’t always happen with a last name like mine, chuckle. I agree their not being 100% truthful.