Authorities in the United States, United Kingdom and Ukraine launched a series of law enforcement sweeps beginning late last month against some of the world’s most notorious gangs running botnets powered by ZeuS, a powerful password-stealing Trojan horse program. ZeuS botnet activity worldwide took a major hit almost immediately thereafter, but it appears to be already on the rebound, according to one prominent ZeuS-watching site.
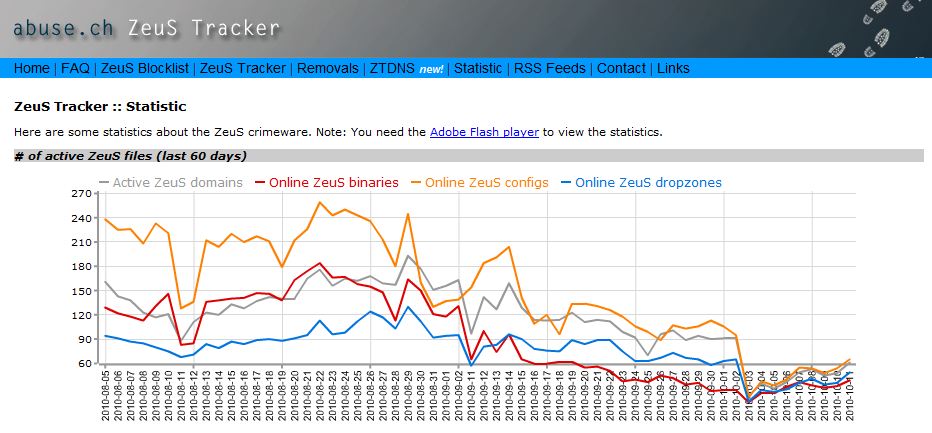 Statistics collected by the Web site Zeus Tracker indicate that while ZeuS botnet activity was already on the wane in the weeks leading up to the end of last month, that activity positively tanked following the recent busts, dipping to its lowest level since the Troyak takedowns earlier this year. For instance, prior to the arrests that began on Sept 29, Zeus Tracker was tracking more than 90 active Zeus control domains. By Oct. 3, that number had fallen to just 20.
Statistics collected by the Web site Zeus Tracker indicate that while ZeuS botnet activity was already on the wane in the weeks leading up to the end of last month, that activity positively tanked following the recent busts, dipping to its lowest level since the Troyak takedowns earlier this year. For instance, prior to the arrests that began on Sept 29, Zeus Tracker was tracking more than 90 active Zeus control domains. By Oct. 3, that number had fallen to just 20.
I contacted Roman Hüssy, the Swiss information technology expert who maintains the tracking site, to see if there could be some technical or glitchy explanation for the dramatic drop. Hüssy said while there are criminal technologies being built into malware that try to prevent ZeuS Tracker from being able to follow ZeuS botnet infrastructure, he’s fairly sure he has managed to bypass it.
“Another thing which I’ve seen is that some [ZeuS botnet command servers] are using geo-IP location, [so that] if a ZeuS group just targets U.K. banks, they will do a geo-location restriction on the [control] server, and allow just bots from the U.K.” to ping the servers, he wrote in an instant message.
Some folks who probably know more about what’s really going on here (targeted takedowns, maybe?) aren’t responding at the moment, which tells me we may hear more about other factors that contributed to this drop in the days or weeks ahead. Stay tuned.




The new levels of flying under the radar for these bot masters, never ceases to amaze me!
I hope you are not tired of us thanking you over and over again for your coverage Brian! 🙂
Tired? Never! Bring it! 🙂
@ JCitizen:
Let me second your thanks to Brian. His talents are widely known and appreciated:
http://blogs.forbes.com/trevorbutterworth/2010/10/13/dim-reading-in-geekville/#
@BrianKrebs
Microsoft has added the detection of ZeusBotnet client to it’s Malicous Software Removal Tools some days ago and is spreading it with the windows auto update. That might additionally explain the activity drop.
PWS:Win32/Zbot
PWS:Win32/Zbot.A
http://www.microsoft.com/security/portal/Definitions/WhatsNew.aspx?package=AM&Release=Released&Version=1.91.1759.0
Not unless they have a time machine 🙂
Definition available date: Oct 14, 2010 05:36 AM UTC
In the UK the e-crime unit (http://www.met.police.uk/pceu/) that undertook the Zeus investigation and arrests is getting a 30% funding cut. Doesn’t seem like a very smart move.
That’s great news, but Zeus is already starting to recover. We can’t just have a big push and back off, we need constant pressure to take them down.
Of course, in order to do that, we need to provide better funding to cybercrime law enforcement.
Sorry, but I doubt if Microsoft’s definition fits the highly variable Zues malware. Zues and its variants are durn near undetectable. I simply assume I and all my clients are infected with it. Definition driven anti-malware is for all intents and purposes obsolete.
The new wave in security is in the kernel space; and operational while infected.
“Definition driven anti-malware is for all intents and purposes obsolete”
Until something new replaces it, how is it obsolete when it does provide some layer of protection against known threats? I’ve seen it quarantine and stop malware when it got past other defenses. The key though is to setup a system to where it is difficult that malware even gets past the perimeter and NEVER even gets to the desktop to where anti-malware even has to try to act on it.
Therein is the problem as far too many systems are setup the opposite with anti-malware as the primary defense hoping to protect the system AFTER malware has already gotten onto it! Worse, those systems are running as full administrator providing malware all the access it needs to fully compromise a system. That’s why running as a non-admin is so critical and a huge defense SHOULD malware make it to the desktop.
Also, a BIG part of keeping malware from getting to the desktop is user behavior! There are many preventative things you can do while using a computer to head off threats. 🙂 Unfortunately, that requires education first, then continual due diligence that most just don’t want to be bothered with. 🙁
I won’t argue with that xAdmin;
But your answer still points to new solutions; for example the new Comodo Defense+ HIPS. It seems to work in the kernel space, and does a good job of watching file manipulations there. It can do this with minimal updating, and is behavioral and not definition based. If it uses definitions at all, it would sooner be categorized as a process white list. In my opinion Kaspersky’s is using similar technology.
This is just one example. I don’t use Defense+ because it clashes with other kernel space solutions, that I feel are more important – like SSL session-riding blocking, and video/keyboard blocking. Also possible without definitions.
So far kernel space solutions are less likely to be diverted by malware; and I’ve not seen successful attempts by malcode in this area. As long as the control console is password protected, all bets are off the malware will meet with success.
However, I still recommend backup defense in-depth with older tech definition scanners. They eventually catch almost everything. A good root kit defense is paramount too – of course.
I disagree. I know you like to put most of the onus on the user, but I blame the anti-malware vendors and their marketing for keeping most computer users in the dark. These vendors give the impression that their products will stop virtually anything, with names like “Complete or Total Protection”. Thus, if a computer user purchases one these products, they assume that they’ve done the due diligence. They battened down the hatches, so to speak.
I also blame Microsoft and computer vendors (at least in regards to Windows XP) for setting up systems out of the box that defaulted to an administrator account, without providing any information about the inherent risk or how to create a limited user account to protect themselves.
Who TJ?
I or xAdmin?
I put the onus on the bad guys! That is the only criminals I blame for any of this.
Sorry, JCitizen – I was responding to xAdmin comment.
And to reiterate my point, here’s some of the marketing I’m referring to:
Norton Internet Security 2011
*Powerful, fast protection to email, shop and bank online without worry
Key Benefits
*Lets you email, chat and surf the web without worrying about cybercriminals ripping you off.
*Delivers the industry’s fastest security suite for protection from online dangers without sacrificing performance.
*Guards against online identity theft so you can shop, bank and visit social networks with confidence.
*Updates automatically, offers easy-to-use features and includes free customer support during your subscription period.
Personally, I think Symantec and all the anti-malware vendors that make such BS claims should be sued for false advertising by the FTC.
I’d also love to know how many of the Zeus victims that Brian has chronicled over the years were using some iteration of Norton Internet Security.
@TJ,
I do agree in placing some blame on Anti-malware vendors and even on the computer industry itself as I stated here:
http://krebsonsecurity.com/2010/07/rogue-antivirus-victims-seldom-fight-back/comment-page-1/#comment-7773
But, it still comes back to the end user to take responsibility for the security of their computer. It’s like a home owner who believes the alarm company salesman who says all they need to do to protect their home is to have an alarm system installed! But as we should’ve learned at some point in our lives, that alone is NOT going to fully protect your house! What about fortifying doors and windows and their locks, actually using the locks, keeping the house well lit at night, keeping doors and windows clear of plant overgrowth to avoid hiding areas, not leaving valuables in plain sight as an invitation, being aware of suspicious behavior and reporting it to the authorities, etc (each of these equate to a layer of security just as is recommended for the best computer security!). All of these things are within the control of the homeowner, just as their computer and home network should be. That is why I put the onus on the user.
I’ll add my voice at the bottom saying “Thank you!” We do appreciate your investigations and warnings. Trust is helped by having beliefs validated, so your reports help to prove when trust is properly placed and when it is not.
Hey thanks for staying on the Java case, I had no idea as to how serious the threat was until I saw the .nt Jerkface post that references your blog.
http://www.binplay.com/2010/10/oh-btw-java-is-under-massive-attack.html