New mobile apps from the Chinese artificial intelligence (AI) company DeepSeek have remained among the top three “free” downloads for Apple and Google devices since their debut on Jan. 25, 2025. But experts caution that many of DeepSeek’s design choices — such as using hard-coded encryption keys, and sending unencrypted user and device data to Chinese companies — introduce a number of glaring security and privacy risks.

Public interest in the DeepSeek AI chat apps swelled following widespread media reports that the upstart Chinese AI firm had managed to match the abilities of cutting-edge chatbots while using a fraction of the specialized computer chips that leading AI companies rely on. As of this writing, DeepSeek is the third most-downloaded “free” app on the Apple store, and #1 on Google Play.
DeepSeek’s rapid rise caught the attention of the mobile security firm NowSecure, a Chicago-based company that helps clients screen mobile apps for security and privacy threats. In a teardown of the DeepSeek app published today, NowSecure urged organizations to remove the DeepSeek iOS mobile app from their environments, citing security concerns.
NowSecure founder Andrew Hoog said they haven’t yet concluded an in-depth analysis of the DeepSeek app for Android devices, but that there is little reason to believe its basic design would be functionally much different.
Hoog told KrebsOnSecurity there were a number of qualities about the DeepSeek iOS app that suggest the presence of deep-seated security and privacy risks. For starters, he said, the app collects an awful lot of data about the user’s device.
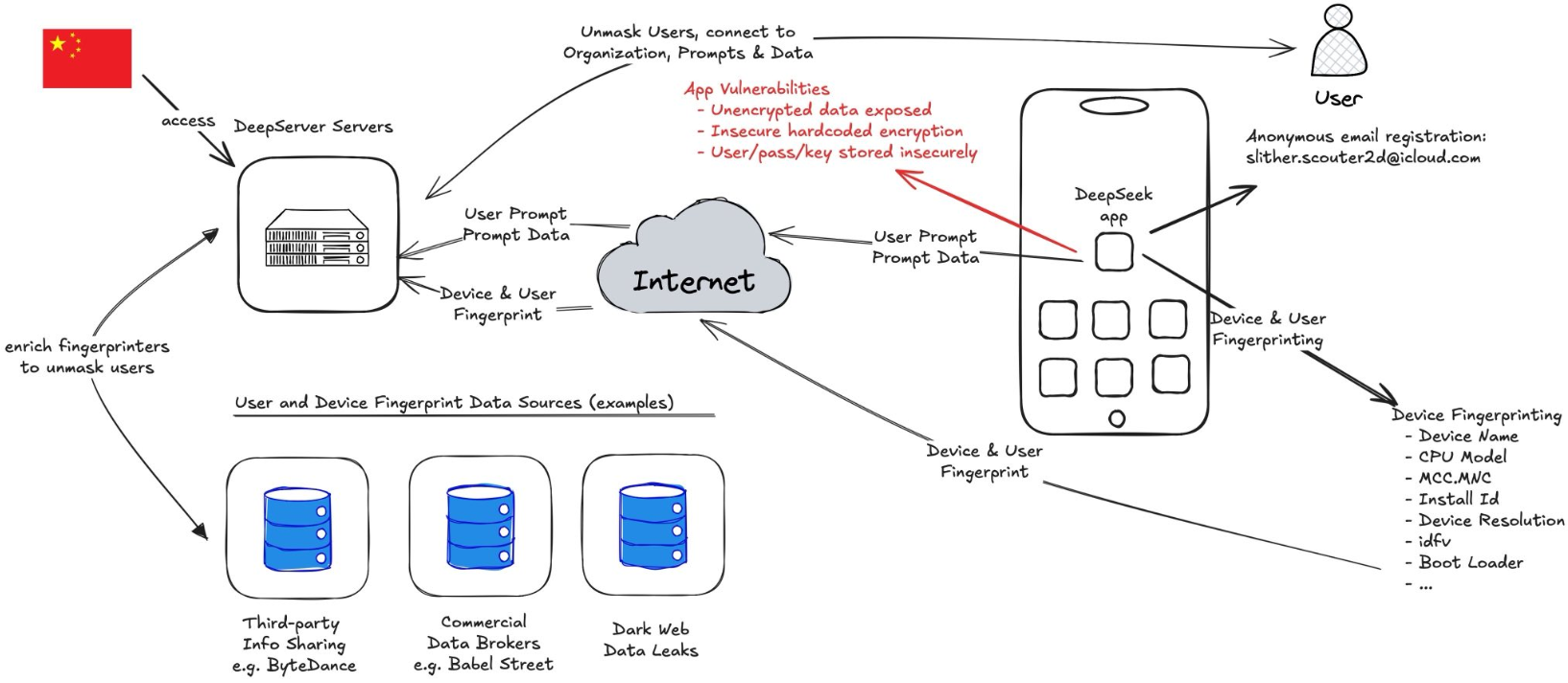
“They are doing some very interesting things that are on the edge of advanced device fingerprinting,” Hoog said, noting that one property of the app tracks the device’s name — which for many iOS devices defaults to the customer’s name followed by the type of iOS device.
The device information shared, combined with the user’s Internet address and data gathered from mobile advertising companies, could be used to deanonymize users of the DeepSeek iOS app, NowSecure warned. The report notes that DeepSeek communicates with Volcengine, a cloud platform developed by ByteDance (the makers of TikTok), although NowSecure said it wasn’t clear if the data is just leveraging ByteDance’s digital transformation cloud service or if the declared information share extends further between the two companies.
Perhaps more concerning, NowSecure said the iOS app transmits device information “in the clear,” without any encryption to encapsulate the data. This means the data being handled by the app could be intercepted, read, and even modified by anyone who has access to any of the networks that carry the app’s traffic.
“The DeepSeek iOS app globally disables App Transport Security (ATS) which is an iOS platform level protection that prevents sensitive data from being sent over unencrypted channels,” the report observed. “Since this protection is disabled, the app can (and does) send unencrypted data over the internet.”
Hoog said the app does selectively encrypt portions of the responses coming from DeepSeek servers. But they also found it uses an insecure and now deprecated encryption algorithm called 3DES (aka Triple DES), and that the developers had hard-coded the encryption key. That means the cryptographic key needed to decipher those data fields can be extracted from the app itself.
There were other, less alarming security and privacy issues highlighted in the report, but Hoog said he’s confident there are additional, unseen security concerns lurking within the app’s code.
“When we see people exhibit really simplistic coding errors, as you dig deeper there are usually a lot more issues,” Hoog said. “There is virtually no priority around security or privacy. Whether cultural, or mandated by China, or a witting choice, taken together they point to significant lapse in security and privacy controls, and that puts companies at risk.”
Apparently, plenty of others share this view. Axios reported on January 30 that U.S. congressional offices are being warned not to use the app.
“[T]hreat actors are already exploiting DeepSeek to deliver malicious software and infect devices,” read the notice from the chief administrative officer for the House of Representatives. “To mitigate these risks, the House has taken security measures to restrict DeepSeek’s functionality on all House-issued devices.”
TechCrunch reports that Italy and Taiwan have already moved to ban DeepSeek over security concerns. Bloomberg writes that The Pentagon has blocked access to DeepSeek. CNBC says NASA also banned employees from using the service, as did the U.S. Navy.
Beyond security concerns tied to the DeepSeek iOS app, there are indications the Chinese AI company may be playing fast and loose with the data that it collects from and about users. On January 29, researchers at Wiz said they discovered a publicly accessible database linked to DeepSeek that exposed “a significant volume of chat history, backend data and sensitive information, including log streams, API secrets, and operational details.”
“More critically, the exposure allowed for full database control and potential privilege escalation within the DeepSeek environment, without any authentication or defense mechanism to the outside world,” Wiz wrote. [Full disclosure: Wiz is currently an advertiser on this website.]
KrebsOnSecurity sought comment on the report from DeepSeek and from Apple. This story will be updated with any substantive replies.




I have already forwarded this to everyone in our company who has a company cell phone. Already we only allow a small list of applications on our company phone via Intune. I am also concerned about the security of our employee’s personal phones.
I have my one own phone and believe you me, EVERY one’s cut off from deep-seek.
Australian federal government, as well as several state governments, have all banned DeepSeek (for government usage) for these reasons – and one, suspects questions about Chinese government access and involvement.
School Report Card:
Aptitude: A+
Achievements: A+
Diligence: B-
Impact: A++++++++
Deepseek has a tendancy to come up with some novel approaches and doesn’t always follow the norms which have been set by his peer group. He is a loner in some respects, but I sense his presense, approach and following will grow over the course of 2025. His last piece of work was completed with haste, no doubt due to family commitments (MIC2025), but I liked the openness of the code which will allow his peer group to study and learn from it for future submissions. I’ve given his peers a copy, so they can study it in earnest and I’m hoping they will learn from it and it will inspire them to further their knowledge and understanding for all to share within the community in an open manner.
/s
Excellent overview on the risks thus far identified.
Big yawn. Does anyone legitimately think OpenAI, etc doesn’t have access to this data and wouldn’t turn it over to the USG on simple ask, much less demand. You know kind of like how every US company has since CALEA.
I’d trust the Chinese government way more than I’d trust the USG with my life’s details. US public officials just mad they can’t force Chinese companies to spy on US citizens or manufacturer evidence against them.
This complacency is the biggest problem of all, particularly for Gen Z and younger. They only know life in the digital world, where Western corporate practices have slowly eroded all manner of privacy; they don’t know any different and could not care less. Who can blame them when your only choice is; do you want US tech giants abusing your data or the Chinese government? The genie got out of the bottle long ago: good luck putting that back in.
Off topic but this is really a problem of education. I’m Gen Z and from Germany. We take data security to extreme measures. We learn about it early on in school and it’s a topic that gets picked up over and over throughout the years. Protecting personal data is essential and a fundamental right. Companies and institutions must comply to strict privacy laws like GDPR. Even the goverment can’t do anything about it. This is an awareness that should be teached and trained anywhere in the world.
As a long-time proponent of sharing awareness of all things privacy and security related, this is encouraging to hear. I applaud the courage and actions of the EU in leading the way in protecting its citizens from the harms of the mass harvesting of private and personal data, performed by corporations today. Bravo.
One can only hope that other jurisdictions take note but I’m not going to hold my breath.
“I applaud the courage and actions of the EU in leading the way in protecting its citizens from the harms of the mass harvesting of private and personal data, performed by corporations today. Bravo.”
And let me be on record defending mosquito netting over beds!
The Germans and old Eastern bloc nations are leading the way on this because they still have the actions of the Stasi in recent memory to act as a great motivator. Five eyes nations do not. Privacy legislation, like a mosquito net is better than nothing, but over time it can be improved. Maybe we need a repellent. And more education.
“I’d trust the Chinese government way more than I’d trust the USG with my life’s details.”
Sure you would sweetheart. Move there and we’ll see.
Absolutely! This is a warning about nothing unexpected.
Anyway, you can run DeepSeek locally, without having to send anything to China.
I thought it was the first LLM I have seen which actually displayed behaviour that I’d call “Intelligent” – it explained the reasoning it used to answer my question and that reasoning was actually quite impressive. It’s certainly the first LLM I have seen which might actually deserve being called an “AI”.
Too bad the company lied, it’s a CCCP pet project, and it can’t do basic mathematics…
great reasoning otherwise, derp.
Living in the US as a retired civilian with no security clearance whatsoever, I am actually more comfy with Chinese companies knowing stuff about me than American. Actually, that’s a choice between two lesser evils. If I truly have a choice, I’d put my trust in European companies outside of UK.
BUT i I were living in China, then I would trust European companies first, then American – and the Chinese ones not at all – not even a little bit.
My points are: who you are and where you live can make a difference which country’s companies/governments can affect you more.
Wait for it.
Same security concerns over the desktop/laptop version? DIYs are airing on Youtube showing Deepseek running on a Raspberry Pi.
No. As long as you follow security best practise in hosting your own LLMs, there should be on problems. That is; running any LLMs locally, be it Deepseek, Llama, Mistral or otherwise, should be entirely sandboxed or cantainerised, with say Kubernetes or Docker to ensure there is no data leakage. I have yet to see any attempts at reaching out and I have been running Deepseek R1 since its release.
RPI is not able to run the real deal, just the distilled version which is a poor imitation of the real 671b model
I am fully aware of that. I was answering Mark’s question concerning security as this is a Security site not an LLM guide.
I am fully aware of that. Mark asked a security related question then made a statement. I replied to the question not the statement.
Hardware Security researcher Matt Brown performed Wireshark reconnaisance and packet inspection on the Chinese ‘RedNote’ app in the wake of the TikTok debacle a fortnight ago (link below). The results were alarmingly similar to these reports; use of hard-coded encryption keys and sending of plain text data to multiple Chinese based servers. Security does not seem to be a priority for any major Chinese software/app developer nowadays. Whether that is due to poor training/skills-base or by design, I’ll leave that up to you to decide.
https://www.youtube.com/watch?v=-MZV6T6ag0c
I remember a Far Side cartoon where a bunch of buffalo are stampeding and one says “as if we all know where we’re going”.
I’m also old enough to remember an Internet and Web where one could just play around with the latest and greatest application or website and not really worry about what was heading back the other way.
Those days are long gone, patience is not only a virtue now, it’s damn good cybersecurity and privacy practice, as well as not jumping on a bandwagon.
Thanks as always for keeping us informed.
How much of this is applicable to the version of DeepSeek that can be run on a local server? I’m guessing none…
If it’s china – everyone freaks out. This is projection from US firms – the US firms are spying on everyone, and playing ‘fast and loose’ with our data an could not care less about privacy – so therefore the Chineese must be doing the same (and maybe there are). Why not look in the mirror.
The bigger concern about AI, in the context of a blog like, this is the huge scope to train models in all things IT and to get the models to do the hacking for you. They will make human hackers look like children playing with wooden building blocks. But no one is talking about it.
?
While I agree that there is a lot of sensitive information going in to apps like ChatGPT as well as other social media applications none of them are hardcoding keys in to their application or disabling in transit encryption that is standard in the application. It’s not so much projection as it is pointing out that this app is very insecure and seemingly a fly by night type of operation.
@Mealy, see that’s the point, I’m not in their legal jurisdiction hence why I trust them. That’s all the USG is upset about here, it’s the other nations are providing data safe havens against them. If I lived in China as you suggested, obviously I’d try and use a US AI product. 9/11 killed Tim May, AI buried him. The Internet could have been great.
I read where Apple vetted apps published on its website to determine how much information was sent to the apps originators and even asked Facebook to stop collecting information that cost them millions of dollars. Why would they not do the same for DeepFake?
The image has a little typo on the upper left part where it says “DeepServer Servers” – it needs to read “DeepSeek Servers” (or similar). Good image still for those not technically well versed to explain it to them easily.
I asked DeepSeek, Google Gemini, and Microsoft Copilot:
“Axios reported on January 30 that U.S. congressional offices are being warned not to use the app.
“Threat actors are already exploiting DeepSeek to deliver malicious software and infect devices,” read the notice from the chief administrative officer for the House of Representatives.
Question: How does DeepSeek deliver malicious software and infect devices?”
The DeepSeek response was honest, detailed, and nuanced.
CoPilot was brief and less detailed.
Gemini was brief, the least insightful, and totally failed to mention the counterfeit Python package problem.
I think most people understand that everything you do on the internet is public. The use of a hard-coded key is not ideal, but even Chrome did that for Linux machines without a key-ring. (it’s “peanuts”) This would be for encryption at rest. Strange that they transmit credentials over http though… seems like a bad idea. The point about China company vs. US company is appropriate though… either way it’s a company who’s collecting info on you… whether that’s Google or this Chinese company, or an intelligence agency it’s a central repository that can be hacked by bad actors. A lot of the anti-Chinese privacy concerns do seem hypocritical to me. It’s one thing to prevent guv’ment employees with security clearances from accessing the apps… it’s another to prevent all US citizens. If they’re trying to protect us from threats they should do that across the board. Isn’t the threat the same whether it’s based in the US or China? A private company can gain access to secure guv’ment workers through associates or family just as easily whether it’s US, China, or multi-national based, no?
There are countless other apps with millions of users that collect the exact same user information, if not more, and transport it in the same way, with the same ‘security risks.’ The only reason for this is because of the suspected involvement of the Chinese government, which I would rather have control of my data than the U.S. government.
Yes, there are many apps that clearly don’t care about security. But not many are the top downloaded apps for weeks on end.
“which I would rather have control of my data than the U.S. government.”
So move to China. Problem solved, as far as you know.
So, basically, using Chinese Software means that the data is processed in China, is that the finding?
Security concerns I understand, by the way, what is it no unencrypted or bas encrypted… cant be both I suppose