Fake online reviews generated by unscrupulous marketers blanket the Internet these days. Although online review pollution isn’t exactly a hot-button consumer issue, there are plenty of cases in which phony reviews may endanger one’s life or well-being. This is the story about how searching for drug abuse treatment services online could cause concerned loved ones to send their addicted, vulnerable friends or family members straight into the arms of the Church of Scientology.
As explained in last year’s piece, Don’t Be Fooled by Fake Online Reviews Part II, there are countless real-world services that are primed for exploitation online by marketers engaged in false and misleading “search engine optimization” (SEO) techniques. These shady actors specialize in creating hundreds or thousands of phantom companies online, each with different generic-sounding business names, addresses and phone numbers. The phantom firms often cluster around fake listings created in Google Maps — complete with numerous five-star reviews, pictures, phone numbers and Web site links.
The problem is that calls to any of these phony companies are routed back to the same crooked SEO entity that created them. That marketer in turn sells the customer lead to one of several companies that have agreed in advance to buy such business leads. As a result, many consumers think they are dealing with one company when they call, yet end up being serviced by a completely unrelated firm that may not have to worry about maintaining a reputation for quality and fair customer service.
Experts say fake online reviews are most prevalent in labor-intensive services that do not require the customer to come into the company’s offices but instead come to the consumer. These services include but are not limited to locksmiths, windshield replacement services, garage door repair and replacement technicians, carpet cleaning and other services that consumers very often call for immediate service.
As it happens, the problem is widespread in the drug rehabilitation industry as well. That became apparent after I spent just a few hours with Bryan Seely, the guy who literally wrote the definitive book on fake Internet reviews.
Perhaps best known for a stunt in which he used fake Google Maps listings to intercept calls destined for the FBI and U.S. Secret Service, Seely knows a thing or two about this industry: Until 2011, he worked for an SEO firm that helped to develop and spread some of the same fake online reviews that he is now helping to clean up.
More recently, Seely has been tracking a network of hundreds of phony listings and reviews that lead inquiring customers to fewer than a half dozen drug rehab centers, including Narconon International — an organization that promotes the theories of Scientology founder L. Ron Hubbard regarding substance abuse treatment and addiction.
As described in Narconon’s Wikipedia entry, Narconon facilities are known not only for attempting to win over new converts, but also for treating all drug addictions with a rather bizarre cocktail consisting mainly of vitamins and long hours in extremely hot saunas. The Wiki entry documents multiple cases of accidental deaths at Narconon facilities, where some addicts reportedly died from overdoses of vitamins or neglect:
“Narconon has faced considerable controversy over the safety and effectiveness of its rehabilitation methods,” the Wiki entry reads. “Narconon teaches that drugs reside in body fat, and remain there indefinitely, and that to recover from drug abuse, addicts can remove the drugs from their fat through saunas and use of vitamins. Medical experts disagree with this basic understanding of physiology, saying that no significant amount of drugs are stored in fat, and that drugs can’t be ‘sweated out’ as Narconon claims.”
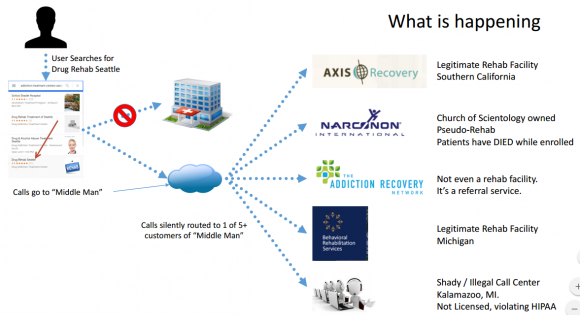
Source: Seely Security.
FOLLOW THE BOUNCING BALL
Seely said he learned that the drug rehab industry was overrun with SEO firms when he began researching rehab centers in Seattle for a family friend who was struggling with substance abuse and addiction issues. A simple search on Google for “drug rehab Seattle” turned up multiple local search results that looked promising.
One of the top three results was for a business calling itself “Drug Rehab Seattle,” and while it lists a toll-free phone number, it does not list a physical address (NB: this is not always the case with fake listings, which just as often claim the street address of another legitimate business). A click on the organization’s listing claims the Web site rehabs.com – a legitimate drug rehab search service. However, the owners of rehabs.com say this listing is unauthorized and unaffiliated with rehabs.com.
As documented in this Youtube video, Seely called the toll-free number in the Drug Rehab Seattle listing, and was transferred to a hotline that took down his name, number and insurance information and promised an immediate call back. Within minutes, Seely said, he received a call from a woman who said she represented a Seattle treatment center but was vague about the background of the organization itself. A little digging showed that the treatment center was run by Narconon. Continue reading →









 Owned by Santa Clara, Calif. based networking giant
Owned by Santa Clara, Calif. based networking giant  The latest update brings Flash to v. 22.0.0.192 for Windows and Mac users alike. If you have Flash installed, you should update, hobble or remove Flash as soon as possible.
The latest update brings Flash to v. 22.0.0.192 for Windows and Mac users alike. If you have Flash installed, you should update, hobble or remove Flash as soon as possible. According to
According to  FBI Special Agent Timothy J. Wilkins wrote that investigators also subpoenaed and got access to that michaelp77x@gmail.com account, and found emails between Persaud and at least four affiliate programs that hire spammers to send junk email campaigns.
FBI Special Agent Timothy J. Wilkins wrote that investigators also subpoenaed and got access to that michaelp77x@gmail.com account, and found emails between Persaud and at least four affiliate programs that hire spammers to send junk email campaigns. Yes, that’s right it’s once again Patch Tuesday, better known to mere mortals as the second Tuesday of each month. Microsoft isn’t kidding around this particular Tuesday — pushing out
Yes, that’s right it’s once again Patch Tuesday, better known to mere mortals as the second Tuesday of each month. Microsoft isn’t kidding around this particular Tuesday — pushing out  During the height of tax-filing season in 2015, KrebsOnSecurity
During the height of tax-filing season in 2015, KrebsOnSecurity 