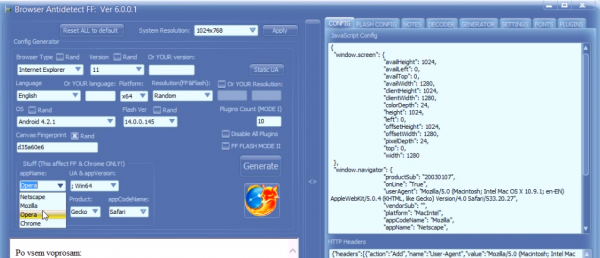
If you’re an American and haven’t yet created an account at irs.gov, you may want to take care of that before tax fraudsters create an account in your name and steal your personal and tax data in the process.
 Recently, KrebsOnSecurity heard from Michael Kasper, a 35-year-old reader who tried to obtain a copy of his most recent tax transcript with the Internal Revenue Service (IRS). Kasper said he sought the transcript after trying to file his taxes through the desktop version of TurboTax, and being informed by TurboTax that the IRS had rejected the request because his return had already been filed.
Recently, KrebsOnSecurity heard from Michael Kasper, a 35-year-old reader who tried to obtain a copy of his most recent tax transcript with the Internal Revenue Service (IRS). Kasper said he sought the transcript after trying to file his taxes through the desktop version of TurboTax, and being informed by TurboTax that the IRS had rejected the request because his return had already been filed.
Kasper said he phoned the IRS’s identity theft hotline (800-908-4490) and was told a direct deposit was being made that very same day for his tax refund — a request made with his Social Security number and address but to be deposited into a bank account that he didn’t recognize.
“Since I was alerting them that this transaction was fraudulent, their privacy rules prevented them from telling me any more information, such as the routing number and account number of that deposit,” Kasper said. “They basically admitted this was to protect the privacy of the criminal, not because they were going to investigate right away. In fact, they were very clear that the matter would not be investigated further until a fraud affidavit and accompanying documentation were processed by mail.”
In the following weeks, Kasper contacted the IRS, who told him they had no new information on his case. When he tried to get a transcript of the fraudulent return using the “Get Transcript” function on IRS.gov, he learned that someone had already registered through the IRS’s site using his Social Security number and an unknown email address.
“When I called the IRS to fix this, and spent another hour on hold, they explained they could not tell me what the email address was due to privacy regulations,” Kasper recalled. “They also said they could not change the email address, all they could do was ban access to eServices for my account, which they did. It was something at least.”
FORM 4506
Undeterred, Kasper researched further and discovered that he could still obtain a copy of the fraudulent return by filling out the IRS Form 4506 (PDF) and paying a $50 processing fee. Several days later, the IRS mailed Kasper a photocopy of the fraudulent return filed in his name — complete with the bank routing and account number that received the $8,936 phony refund filed in his name.
“That’s right, $50 just for the right to see my own return,” Kasper said. “And once again the right hand does not know what the left hand is doing, because it cost me just $50 to get them to ignore their own privacy rules. The most interesting thing about this strange rule is that the IRS also refuses to look at the account data itself until it is fully investigated. Banks are required by law to report suspicious refund deposits, but the IRS does not even bother to contact banks to let them know a refund deposit was reported fraudulent, at least in the case of individual taxpayers who call, confirm their identity and report it, just like I did.”
Kasper said the transcript indicates the fraudsters filed his refund request using the IRS web site’s own free e-file website for those with incomes over $60,000. It also showed the routing number for First National Bank of Pennsylvania and the checking account number of the individual who got the deposit plus the date that they filed: January 31, 2015.
The transcript suggests that the fraudsters who claimed his refund had done so by copying all of the data from his previous year’s W2, and by increasing the previous year’s amounts slightly. Kasper said he can’t prove it, but he believes the scammers obtained that W2 data directly from the IRS itself, after creating an account at the IRS portal in his name (but using a different email address) and requesting his transcript.
“The person who submitted it somehow accessed my tax return from the previous year 2013 in order to list my employer and salary from that year, 2013, then use it on the 2014 return, instead,” Kasper said. “In addition, they also submitted a corrected W-2 that increased the withholding amount by exactly $6,000 to increase their total refund due to $8,936.”
MONEY MULING
On Wednesday, March 18, 2015, Kasper contacted First National Bank of Pennsylvania whose routing number was listed in the phony tax refund request, and reached their head of account security. That person confirmed a direct deposit by the IRS for $8,936.00 was made on February 9, 2015 into an individual checking account specifying Kasper’s full name and SSN in the metadata with the deposit.
“She told me that she could also see transactions were made at one or more branches in the city of Williamsport, PA to disburse or withdraw those funds and that several purchases were made by debit card in the city of Williamsport as well, so that at this point a substantial portion of the funds were gone,” Kasper said. “She further told me that no one from the IRS had contacted her bank to raise any questions about this account, despite my fraud report filed February 9, 2015.”
The head of account security at the bank stated that she would be glad to cooperate with the Williamsport Police if they provided the required legal request to allow her to release the name, address, and account details. The bank officer offered Kasper her office phone number and cell phone to share with the cops. The First National employee also mentioned that the suspect lived in the city of Williamsport, PA, and that this individual seemed to still be using the account.
Kasper said the local police in his New York hometown hadn’t bothered to respond to his request for assistance, but that the lieutenant at the Williamsport police department who heard his story took pity on him and asked him to write an email about the incident to his captain, which Kasper said he sent later that morning.
Just two hours later, he received a call from an investigator who had been assigned to the case. The detective then interviewed the individual who held the account the same day and told Kasper that the bank’s fraud department was investigating and had asked the person to return the cash.
“My tax refund fraud case had gone from stuck in the mud to an open case, almost overnight,” Kasper sad. “Or at least it seemed to be that simple. It turned out to be much more complex.”
For starters, the woman who owned the bank account that received his phony refund — a student at a local Pennsylvania university — said she got the transfer after responding to a Craigslist ad for a moneymaking opportunity.
Kasper said the detective learned that money was deposited into her account, and that she sent the money out to locations in Nigeria via Western Union wire transfer, keeping some as a profit, and apparently never suspecting that she might be doing something illegal.
“She has so far provided a significant amount of information, and I’m inclined to believe her story,” Kasper said. “Who would be crazy enough to deposit a fraudulent tax refund in their own checking account, as opposed to an untraceable debit card they could get at a convenience store. At the same time, wouldn’t somebody who could pull this off also have an explanation like this ready?”
The woman in question, whose name is being withheld from this story, declined multiple requests to speak with KrebsOnSecurity, threatening to file harassment claims if I didn’t stop trying to contact her. Nevertheless, she appears to have been an unwitting — if not unwilling — money mule in a scam that seeks to recruit the unwary for moneymaking schemes. Continue reading