-Sept. 9, 12:30 p.m. CT, Yucatan Peninsula, Mexico: Halfway down the southbound four-lane highway from Cancun to the ancient ruins in Tulum, traffic inexplicably slowed to a halt. There was some sort of checkpoint ahead by the Mexican Federal Police. I began to wonder whether it was a good idea to have brought along the ATM skimmer instead of leaving it in the hotel safe. If the cops searched my stuff, how could I explain having ultra-sophisticated Bluetooth ATM skimmer components in my backpack?
The above paragraph is an excerpt that I pulled from the body of Part II in this series of articles and video essays stemming from a recent four-day trip to Mexico. During that trip, I found at least 19 different ATMs that all apparently had been hacked from the inside and retrofitted with tiny, sophisticated devices that store and transmit stolen card data and PINs wirelessly.
In June 2015, I heard from a source at an ATM firm who wanted advice and help in reaching out to the right people about what he described as an ongoing ATM fraud campaign of unprecedented sophistication, organization and breadth. Given my focus on ATM skimming technology and innovations, I was immediately interested.
My source asked to have his name and that of his employer omitted from the story because he fears potential reprisals from the alleged organized criminal perpetrators of this scam. According to my source, several of his employer’s ATM installation and maintenance technicians in the Cancun area reported recently being approached by men with Eastern European accents, asking each tech if he would be interested in making more than 100 times his monthly salary just for providing direct, physical access to the inside of a single ATM that the technician served.
One of my source’s co-workers was later found to have accepted the bribes, which apparently had only grown larger and more aggressive after technicians in charge of specific, very busy ATMs declined an initial offer.
My source said his company fired the rogue employee who’d taken the bait, but that the employee’s actions had still been useful because experts were now able to examine the skimming technology first-hand. The company tested the hardware by installing it into ATMs that were not in service. When they turned the devices on, they discovered each component was beaconing out the same Bluetooth signal: “Free2Move.”
Turns out, Free2Move is the default name for a bluetooth beacon in a component made by a legitimate wireless communications company of the same name. I also located a sales thread in a dubious looking site that specializes in offering this technology in mini form for ATM PIN pads and card readers for $550 per component (although the site claims it won’t sell the products to scammers).
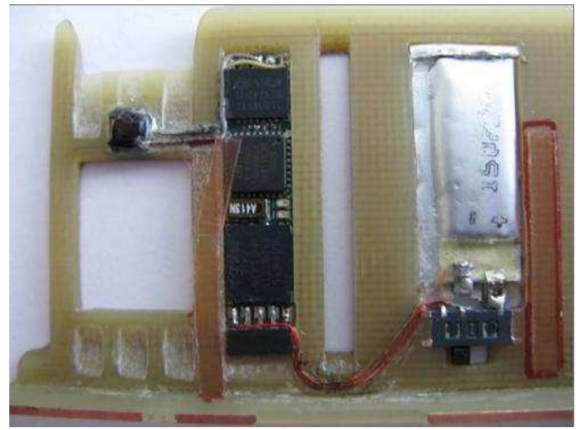
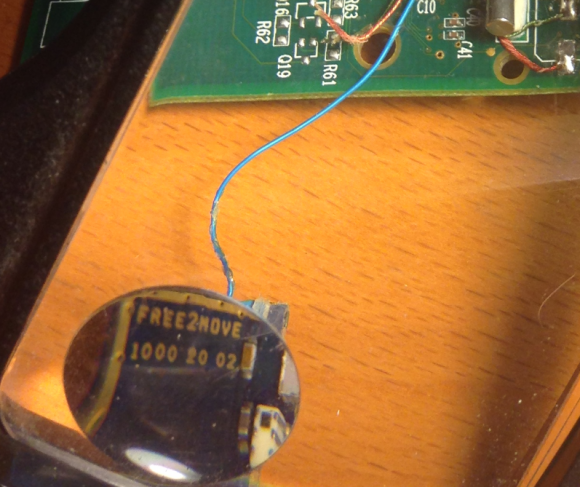 The Bluetooth circuit boards allegedly supplied by the Eastern Europeans who bribed my source’s technician were made to be discretely wired directly onto the electronic ATM circuit boards which independently serve the machine’s debit card reader and PIN pad.
The Bluetooth circuit boards allegedly supplied by the Eastern Europeans who bribed my source’s technician were made to be discretely wired directly onto the electronic ATM circuit boards which independently serve the machine’s debit card reader and PIN pad.
Each of the bluetooth circuit boards are tiny — wafer thin and about 1 cm wide by 2 cm long. Each also comes with its own data storage device. Stolen card data can be retrieved from the bluetooth components wirelessly: The thief merely needs to be within a few meters of the compromised ATM to pull stolen card data and PINs off the devices, providing he has the secret key needed to access that bluetooth wireless connection.
Even if you knew the initial PIN code to connect to the Bluetooth wireless component on the ATM —the stolen data that is sent by the bluetooth components is encrypted. Decrypting that data requires a private key that ostensibly only the owners of this crimeware possess.
These are not your ordinary skimming devices. Most skimmers are detectable because they are designed to be affixed to the outside of the ATMs. But with direct, internal access to carefully targeted cash machines, the devices could sit for months or even years inside of compromised ATMs before being detected (depending in part on how quickly and smartly the thieves used or sold the stolen card numbers and PINs).
Not long after figuring out the scheme used by this skimmer, my source instructed his contacts in Cancun and the surrounding area to survey various ATMs in the region to see if any of these machines were emitting a Bluetooth signal called “Free2Move.” Sure enough, the area was blanketed with cash machines spitting out Free2Move signals.
Going to the cops would be useless at best, and potentially dangerous; Mexico’s police force is notoriously corrupt, and for all my source knew the skimmer scammers were paying for their own protection from the police.
Rather, he said he wanted to figure out a way to spot compromised ATMs where those systems were deployed across Mexico (but mainly in the areas popular with tourists from Europe and The United States).
When my source said he knew where I could obtain one of these skimmers in Mexico firsthand, I volunteered to scour the tourist areas in and around Cancun to look for ATMs spitting out the Free2Move bluetooth signal.
I’d worked especially hard the previous two months: So much so that July and August were record traffic months for KrebsOnSecurity, with several big breach stories bringing more than a million new readers to the site. It was time to schedule a quasi-vacation, and this was the perfect excuse. I had a huge pile of frequent flier miles burning a hole in my pocket, and I wasted no time in using those miles to book a hotel and flight to Cancun. Continue reading