Over the holidays, I heard from a number of readers who were seeing strange, unauthorized charges showing up on their credit and debit cards for $9.84. Many wondered whether this was the result of the Target breach; I suppose I asked for this, having repeatedly advised readers to keep a close eye on their bank statements for bogus transactions. It’s still not clear how consumers’ card numbers are being stolen here, but the fraud appears to stem from an elaborate network of affiliate schemes that stretch from Cyprus to India and the United Kingdom.
 One reader said the $9.84 charge on her card came with a notation stating the site responsible was eetsac.com. I soon discovered that there are dozens of sites complaining about similar charges from similarly-constructed domains; for example, this 30-page thread at Amazon’s customer help forums includes gripes from hundreds of people taken by this scam.
One reader said the $9.84 charge on her card came with a notation stating the site responsible was eetsac.com. I soon discovered that there are dozens of sites complaining about similar charges from similarly-constructed domains; for example, this 30-page thread at Amazon’s customer help forums includes gripes from hundreds of people taken by this scam.
I did a bit of digging into that eetsac.com domain, ordering a historic WHOIS report from domaintools.com. The report shows that the domain eetsac.com was originally registered using the email address walter.kosevo@ymail.com. Domaintools also reports that this email address was used to register more than 230 other sites; a full list is available here (CSV).
A closer look at some of those domains reveals a few interesting facts. Callscs.in, for example, is a Web site for a call center and a domain that has been associated with these $9.84 fraudulent charges. Callscs.in lists as its local phone number 43114300. That number traces back to a call center in India, Call Connect India, Inc., which registers its physical address as Plot No 82, Sector 12 A, Dwarka. New Delhi – 110075.
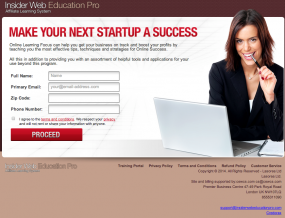 The next site like that one on the list — cewcs.com — references the domain insiderwebeducationpro.com, another domain on the list of sites registered to that ymail.com email address. The homepage of insiderwebeducationpro.com lists the following contact information:
The next site like that one on the list — cewcs.com — references the domain insiderwebeducationpro.com, another domain on the list of sites registered to that ymail.com email address. The homepage of insiderwebeducationpro.com lists the following contact information:
Copyright © 2014. All Rights Reserved – Lasorea Ltd
Lasorea Ltd.
Site and billing supported by:cewcs.com cs@cewcs.com
Premier Business Centre 47-49 Park Royal Road
London UK NW107LQ
8555311090
A search at companieshouse.gov.uk, a government site which maintains records about companies based in the United Kingdom, turned up incorporation records (PDF) showing that Lasorea Ltd. was founded in January 2013 by Emil Darbinian, a 28-year-old self-described accountant from Nicosia, Cyprus. Other records searches on Mr. Darbinian indicate he owns at least two other companies at the same address, including Testohealth Labs. Ltd — which appears to be a software company — and a firm called Levantos Venture Ltd. Mr. Darbinian did not return messages seeking comment.
Another domain on the list — etosac.com — is listed as the support and billing site for webtutorialpro.com, a site which bills itself as an “affiliate learning system.” In fact, of the 235 domains registered to walter.kosevo@ymail.com, all seem to be either affiliate programs of one kind (diet pills, work-at-home) or support/call center sites.
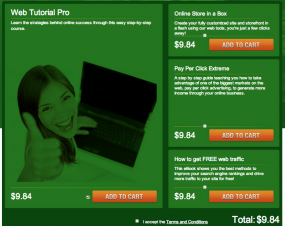
Dozens of sites like this one are the apparent source of the $9.84 charges.
Webtutorialpro.com lists on its homepage a company named Lukria, Ltd., and an address at the same London business park as Mr. Darbinian’s companies. If we step through the signup process to become an affiliate at Webtutorialpro.com, we can see that everything — from the “online store in a box” to “pay per click extreme” and the tutorial on “how to get FREE web traffic — all retail for….wait for it….$9.84!
Lukria, according to incorporation documents (PDF) purchased from companieshouse.co.uk, was created on the same day as Lasorea Ltd., and lists as its director a Sergey Babayan, also from Cyprus. According to the Facebook pages of both Mr. Darbinian and Mr. Babayan, the two men are friends. Mr. Babayan has not responded to requests for comment.
Mr. Babayan’s Facebook profile says he works at a company called Prospectacy Limited, which LinkedIn says is an accounting firm in Nicosia, Cyprus. According to Prospectacy’s Web site, this company specializes in “corporate services,” including “company formation,” “banking,” and “virtual office” services. The company seems to be in the business of establishing offshore firms; according to a reverse WHOIS record lookup from domaintools.com, the email address used to register Prospectacy’s domain also was used to register at least ten other domains, including registerincyprus.com, registerinuk.com, setupincyprus.com and setupineu.com.
A number of these affiliate sites include on their home page links to credorax.com, a Southborough, Mass. based acquiring bank Malta-based acquiring bank that is in the business of processing credit and debit card payments for merchants. It’s not clear whether either cewcs.com or insiderwebeducationpro.com use Credorax Inc. for payment processing, but it seems to suggest that by association. I reached out to Credorax to learn whether this site (and perhaps others that are the subject of this story) are customers, and will update this story if I hear back from them.
Update, 12:43 p.m. ET: I heard from Michael Burtscher, vice president of acquiring risk and fraud management at Credorax. Burtscher clarified that his company has offices in the U.S. but is based in Malta. Burtscher confirmed that Credorax had until recently helped to process cards for the network of sites named in this story, but that the company has severed that relationship. He declined to say when exactly the relationship ended, or indeed whether my information about the client’s identities was accurate. Burtscher would only say that Credorax terminated its relationship with the client in response to consumer complaints about the fraudulent charges. “This was one of those cases where when we onboarded them it looked like a legitimate account, but when we saw there were issues we decided to take action.”
Continue reading →
 All of the vulnerabilities that Microsoft fixed this month earned “important” ratings; not quite as dire as those labeled “critical,” which involve flaws so dangerous that they can be exploited by bad guys or malware to break into systems with no user interaction. Nevertheless, flaws marked “important” can be quite dangerous, particularly when used in tandem with other attack techniques.
All of the vulnerabilities that Microsoft fixed this month earned “important” ratings; not quite as dire as those labeled “critical,” which involve flaws so dangerous that they can be exploited by bad guys or malware to break into systems with no user interaction. Nevertheless, flaws marked “important” can be quite dangerous, particularly when used in tandem with other attack techniques.









![A private message on cpro[dot]su between Rescator and a member interested in his card shop. Notice the ad for Rescator's email flood service at the bottom.](https://krebsonsecurity.com/wp-content/uploads/2013/12/rescator-pm-cpro-600x153.png)
![Rescator, a.k.a. "Hel" a.k.a. "Helkern" the onetime administrator of the Darklife forum, introduces himself to vor[dot]cc crime forum members.](https://krebsonsecurity.com/wp-content/uploads/2013/12/vor-1edited-600x414.png)
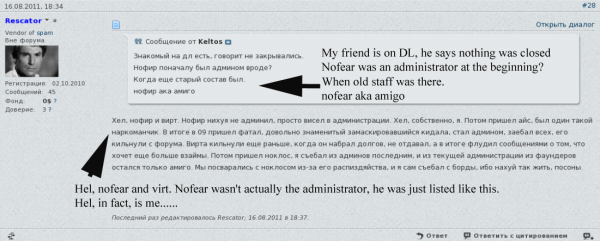
![Darklife admin "Helkern" brags to other members about hacking into cih[dot]ms, a more elite Russian hacking forum.](https://krebsonsecurity.com/wp-content/uploads/2013/12/cihhacked-600x470.png)