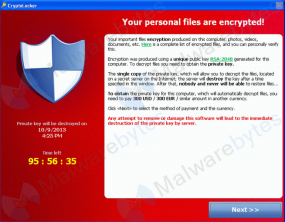
Facebook is mining data leaked from the recent breach at Adobe in an effort to help its users better secure their accounts. Facebook users who used the same email and password combinations at both Facebook and Adobe’s site are being asked to change their password and to answer some additional security questions.
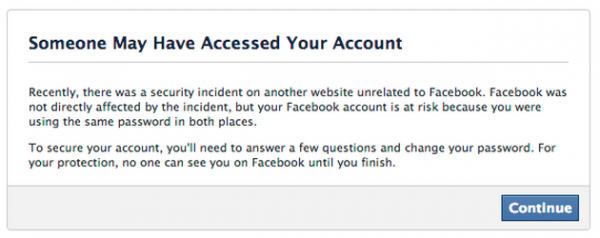
Message that Facebook has been sending to certain users whose information was found in the stolen Adobe data.
Facebook spokesman Jay Nancarrow said Facebook is constantly on the lookout for data leaked from other breach incidents that may endanger accounts of its own users. Nancarrow said that the social networking service has similarly acted in the wake of other high profile breaches to determine if any of its own users’ credentials may have been affected.
“We actively look for situations where the accounts of people who use Facebook could be at risk—even if the threat is external to our service,” said Nancarrow, who declined to say exactly how many Facebook users were seeing the above message. “When we find these situations, we present messages like the one in the screenshot to help affected people secure their accounts.”
In a breach first announced on this blog Oct. 3, 2013, Adobe said hackers had stolen nearly 3 million encrypted customer credit card records, as well as login data for an undetermined number of Adobe user accounts. Earlier this month, Adobe said it had actually notified more than 38 million users that their encrypted account data may have been compromised. But as first reported here on Oct. 29, the breach may have impacted closer to 150 million Adobe users.
What’s more, experts say Adobe appears to have used a single encryption key to scramble all of the leaked user credentials, meaning that anyone who computes, guesses or acquires the decryption key immediately gets access to all the passwords in the database. In a detailed analysis of the enormity of Adobe’s blunder, Paul Ducklin of Sophos describes how researchers managed to work out a decent chunk of the encrypted user passwords just by comparing the leaked data to other large password breaches and to password hint information included in the Adobe account cache.
Update, 2:07 p.m. ET: Looks like Diapers.com and Soap.com sent similar notices to their customers on Sunday. A hit tip to readers Arthur and Dave for sharing copies of the emails from those two sites.
Update, Nov. 12, 4:07 p.m. ET: The initial story seems to have confused a number of readers, perhaps because I left out an explanation of what exactly Facebook did. As a result, many readers seem to have hastily and erroneously concluded that Facebook doesn’t properly secure its users passwords if it can simply compare them in plain text to the Adobe passwords that have already been worked out.
As I proffered in a follow-up comment on this story, Facebook and any other company can take any of the Adobe passwords that have already been guessed or figured out and simply hash those passwords with whatever one-way hashing mechanism(s) they use internally. After that, it’s just a matter of finding any overlapping email addresses that use the same password. Facebook’s Chris Long confirmed that this is more less what the company did.