New fraudster-friendly content management systems are making it more likely than ever that crooks who manage botnets and other large groupings of hacked PCs will extract and sell all credentials of value that can be harvested from the compromised machines.
I’ve often observed that botmasters routinely fail to fully eat what they kill. That is, they tend to chronically undervalue the computers at their disposal, and instead focus on extracting specific resources from hacked PCs, such as using them as spam relays or harvesting online banking credentials. Meanwhile, other assets on the hacked PC that have street value go unused and “wasted” from the fraudster’s perspective.
More often, when miscreants do seek to extract and monetize all of the account credentials from their hacked PCs, they do so by selling access to their raw botnet “logs” — huge text files that document the notable daily activities of the botted systems. To borrow from another food metaphor, this is the digital equivalent of small farms selling their fruits and vegetables as “pick-your-own;” such commerce produces some added revenue without requiring much more work on the seller’s part.
Recently, I’ve been spotting more online fraud shops set up using what appear to be pre-set templates that can be used to sell all manner of credentials from hacked PCs. These shops all sell credit and debit card information, of course, but also lists of emails culled from victim computers, hacked VPN and RDP credentials, Cpanel installations, PHP mailers, FTP access, SSH logins, and online gambling accounts. Some of the panels are even reselling hacked credentials at popular porn sites. Goods can be purchased via virtual currencies such as Perfect Money and bitcoin.
The shop shown below — blackhatstore[dot]ru — borrows the trademarked image of the Black Hat security conference franchise. It’s sometimes said that there’s no such thing as bad press, but I’m pretty sure the folks at Black Hat don’t want their brand advertised or associated in this way (by the way, I’ll be speaking at this year’s Black Hat in Las Vegas next week). I alerted the Black Hat organizers to this fraudulent site, so I wouldn’t expect it to remain live much longer.
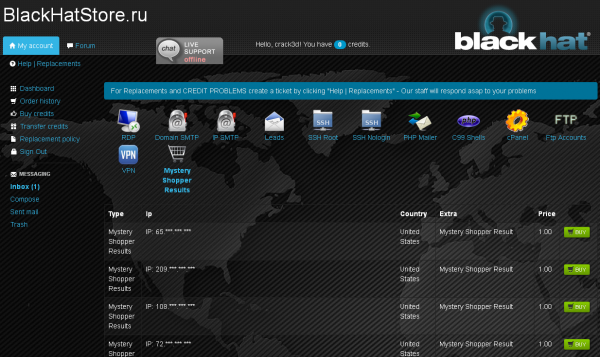
This bot chop shop trades on the good name and trademarks of the Black Hat security conference franchise owned by UBM Tech.
I have no idea what the exact figures are, but I’m confident that a huge percentage of malware in circulation today has the ability to steal all credentials from hacked PCs. Finding and removing these infections is challenging enough, but many victims also fail to take stock of the information that was potentially exposed as a result of the compromise. And who can blame users for not knowing what to do? If your antivirus program detects malware, how much information does it give you about the extent or lifetime of the infection? If it finds and eradicates a deeply-rooted infection, does it remind you that it might be a good idea to change your passwords?
Understandably, the average user is probably more interested in merely having a malware-free computer than he is contemplating whether he needs to then change all of his passwords. It is this very argument that separates much of the security industry into two camps: Those who believe that anti-malware tools can sufficiently scrub a compromised PC so that it can be safely used again (hopefully by the victimized user to change their important passwords), and those who hold that the only way to ensure the integrity of a system is to back up its data, wipe the drive, and re-install the operating system.
I hold with the latter camp, which is why I keep my data on a separate drive from my operating system installation, and use disc imaging tools like Macrium Reflect and Acronis True Image to make regular backups of both the OS and the data drives. That way, if the computer does suffer a compromise, I can save hours of time and headache by restoring the operating system drive with a known-good backup.





Haha…
Porn Access – coming soon
“I hold with the latter camp, which is why I keep my data on a separate drive from my operating system installation”
Having data on a separate partition amounts to the same thing. Either way, you are correct, having data separate makes a system restore an easy job. Even if you do not have a backup, you can mount that system drive using a USB 3.0 docking station and copy the data to the new drive (if you want to use the same drive, you will need a temporary storage drive for the data, but you knew that).
Was that before or after you got recruited by KGB Brian Crebsky ? 🙂
Whos is going to buy access to porn site when you can just use stolen credit card instead ? Credit cards are free if you know where to look .So is porn .
Lame Brian very lame article .No exclusive , No Big mafia deals .Nothing .one shop that all , it must have took you 5 minutes to write this post .
P.s How is Mr Lee doing anyway ?? You neighbor .
Yes you are 🙂
“It is this very argument that separates much of the security industry into two camps: Those who believe that anti-malware tools can sufficiently scrub a compromised PC so that it can be safely used again (hopefully by the victimized user to change their important passwords), and those who hold that the only way to ensure the integrity of a system is to back up its data, wipe the drive, and re-install the operating system.”
For me it depends on the client and the detected infection. Adware is Malware, IMO but I wouldn’t necessarily wipe a PC because the owner inadvertantly installed a crappy program with some unwanted adware programs. Also some clients aren’t prepared to go through the sometimes long procedure of configuring everything just the way they like it.
In addition, I think it’s a good idea to get an idea of just where they might have picked up the infection–not always possible of course, but useful if you can detect it with tools/scans.
I also wonder if, by simply replacing all of the backed up data, you couldn’t be putting an infected file right back on the computer. I don’t think it’s that common, but I also do not think it is impossible.
For clients PCs we choose to clean (we make the decision together) I typically follow up a few times to make sure nothing new has sprung up after the initial cleaning.
Its definitley possible. Look at the old school Michaelangelo virus. it tried to infect every file on the computer, while eating up the fat table…. and you just kept infecting yourself again adding the data back, or just using the floppy disc. When i was a kid I remember throwing away 100s of floppy discs…
Imo we all have viruses, its just a matter of which ones are detectable and from who and where. I got a virus from ea’s battlelog website last year. They thought i was nuts when I told them that….. This also might sound crazy, but I think most of are branded for life, in essence, unless we just throw our lifes work and harddrives into the garbage we are always going to be infected…. Michaelangelo virus was like 20 years ago, chernobyl was infecting bios’s in the late 90s, and you just have to assume they are 10x more sophisticated nowadays.
I piss so many people off online i get hacked all the time. Recenlty, and this one blew my mind, ive been using diff linux distros recenlty try out diff ones, and i was using a thumb drive to install them burning it from windows. well at one point…..the linux stopped booting up the grub somehow got corrupted…..it turns out the thumb drive got corrupted also, and heres the kicker…..it turned my bios boot password blank. In other words….the prompt would still come up, but all i had to do was hit enter and type nothing and it went right through! right after i got threatened. I almost keeled over haha. I had to go into bios and reset the password again so its working again now. I doubt it was anyone in my house, then again family can be crazy too…..
And i agree with Brian. for the past couple years i’ve had this virus that hits me every christmas……one christmas day my pc fried…..even doing a full format with diskpart writing 0s to the whole drive doesn’t get rid of some of these viruses . Actually this samsung hardrive i have right now, had a emergency firmware update last year that I think i was too late on….
But whos is going to throw away their data, which might be their whole lifes work? not me….malware is so ridiculous nowadays, I fix my friends and families pcs that are using xp. Every single one of them, their pc turns to crap within a couple months again. Theres really nothing that can be done anymore for windows xp except to give them linux….
I guess now its just about assuming your infected…and mitigating it because you prolly can’t get rid of it. Like living with hepatitus or something….
For windows at least I think the issue that usually leads to reformat/wipe is the registry… Files can be backed up, moved around, deleted/restored but the registry is often a mess after a 3-10 year old installation. Generally if I can find any trace at all of something I don’t want on there, I will wipe it if I have any doubt. For other people’s computers they prefer not to, but how much trust can you ever have in a machine you can’t verify is clean?
I agree with Brian, I have a recent build that I put an SSD for the programs and main OS and a raid 1 for everything else… If I need to wipe and restore I can do so without losing too much.
“the registry is often a mess after a 3-10 year old installation”
After a few years, almost any PC is a mess, period. I won’t even try to clean-up old XP installations because of the multiple anti-virus and ISP products, not to mention the myriad of screensavers and other borderline malware applications. Ever try to remove AOL from years back? It won’t uninstall unless you use regedit and know which dll files to erase.
I’ve been able to get 5+ years reliably out of my own machines, but in the past working with other people’s they are often a mess of toolbars, adware, partially uninstalled programs and junk files… Unless there are some really important files on there 9/10 its best to just start over with a clean install for those folks.
Ultimately though I blame microsoft for a lot of the problems, from windows 95 and maybe before they have suffered from the same user design flaws, program design flaws, and networking flaws.
“I wouldn’t necessarily wipe a PC because the owner inadvertantly installed a crappy program with some unwanted adware programs”
Most people do not realize that most of their precious downloads are actually adware at best and often malware. They want you to remove only the viruses, yet when you tell them that you really need to remove their wallpaper or other application, their eyes glaze over.
“BIG DEAL”
P.s If you are scared my American friends then use Bank of Nikolai its very safe .Trust me i have pen .
youtube.com /watch?v=0o8XMlL8rqY
Hello,
Krebs how are you finding these stores ?!
If you are a member of blackhat forums or use subscribe to any of their services, you don’t even need to look much. You get flooded with ads
“Backup, backup, backup” Its been said millions of times yet how many have done it?
There is another problem though, and that’s the issue of having multiple online accounts. People should create a way to consolidate their online accounts so that when security breaches occur, its will be much easier to perform damage control.
It all goes back that simple phrase:
‘When you fail to plan, you plan to fail’
i have qwerty1323 as password, is the same for all my accounts so i can remember it easy.
is that bad?
Your password technique is ranked just below sticking a needle in your eye and just above marrying Lindsay Lohan.
Hey !
That’s unfair for the needle to say. Newton actually stuck a darning needle between his eye and the eye socket.
http://www.omg-facts.com/History/Isaac-Newton-Was-So-Devoted-To-Science-T/50895
It cannot be that bad so that you rank it slightly better than Mr. ding dong password technique.
What the heck is it with some of the comments on your articles recently?
Some comments bring out the braindead more than others. I try to delete them when I see them, but sometimes you will see inane, profane, spammy and just plain random comments for a while before I get around to culling them. There are also a handful of carders and trolls who like to post offensive and childish comments because apparently they have nothing better to do. I have a feeling these are the same low-lifes sending fraudulent donations to my PayPal account via hacked PayPals, for no apparent reason other than spite.
There is always a reason .I think It was a birthday present for you .And a little help to pay off your mortgage . You welcome : )
You already crying your about couple of comments imagine what would happened if bad guys turn the there spamming bots on you , this blog will be flooded with all sorts of comments and you wont be able to clear all that in years . Just saying .
This was my favorite so far, you got to hand it to trolls who are actually really funny:
http://krebsonsecurity.com/2012/06/who-is-the-festi-botmaster/comment-page-1/#comment-83083
I agree…a lot of these comments should be deleted. Could you have a different type of auth that would prevent some of these? Or perhaps comments that had to be “approved” before being posted? I do enjoy your articles though. I keep your website on my “daily” list that I check to make sure you have nothing new. 🙂 I admire your work. It takes a lot to do what you do and then have to get in the line of fire for people who despise you.
It’s about striking a balance, I believe. There aren’t enough hours in the day for me to moderate every comment on every post, nor would I want to do this. I have anti-spam filters that catch a ton of this stuff, but sometimes it slips through.
I used to rely on a comment voting/rating system where readers could and very often did bury comments that were OT/noisy/annoying/etc, but that plugin (Comment Rating Pro) was so buggy and full of holes that I abandoned it. Also, the author of the plugin stopped fixing things and responding to requests, so that was it for me.
I wanted to “praise” the poet who sent you a poem in russian.
Did not understood what he wrote there, but I guess only a very sensitive soul could post poetry in a security related blog.
He must be crushed seeing you removed his opera. 🙂
Although I enjoy the articles, I often enjoy the comments even more. I would be very disappointed if I could no longer read the weird and often delusional feedback you receive from the underworld.
Note to underworld: Please never learn how to spell or communicate in a logical message deserving of respect, it would be a real downer.
See Brian people do like inappropriate comments too . I think we should employ couple freelance writers so they can post 24/7 all soft of inappropriate things in here .U can`t delete them when you are a sleep can you .Only joking .
Page views are ad views are money. Is crap comments really crap always?
Ever hear of statement analysis techniques?…just like someone might try to masquerade their education, its just as fake if they are doing the opposite. Grammar nazis, on informal forums and chatrooms….are suspect.
I miss the plugin, it’s unfortunate that the author stopped supporting it.
ENIAC used ten-position ring counters to store digits; each digit used 36 vacuum tubes, 10 of which were the dual triodes making up the flip-flops of the ring counter. Arithmetic was performed by “counting” pulses with the ring counters and generating carry pulses if the counter “wrapped around”, the idea being to emulate in electronics the operation of the digit wheels of a mechanical adding machine. ENIAC had twenty ten-digit signed accumulators which used ten’s complement representation and could perform 5,000 simple addition or subtraction operations between any of them and a source (e.g., another accumulator, or a constant transmitter) every second. It was possible to connect several accumulators to run simultaneously, so the peak speed of operation was potentially much higher due to parallel operation.
What’s the name of the bus driver?
If he is driving backwards, maybe name is ‘CAINE’. 😉