The Washington Post acknowledged today that a sophisticated phishing attack against its newsroom reporters led to the hacking of its Web site, which was seeded with code that redirected readers to the Web site of the Syrian Electronic Army hacker group. According to information obtained by KrebsOnSecurity, the hack began with a phishing campaign launched over the weekend that ultimately hooked one of the paper’s lead sports writers.
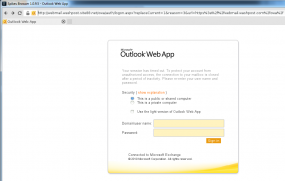
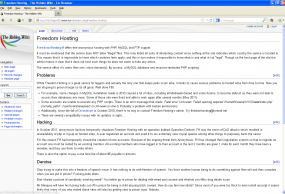
This phishing page used by the Syrian Electronic Army spoofed The Post’s’ internal email login page.
On Tuesday morning, KrebsOnSecurity obtained information indicating that a phishing campaign targeting the Post’s newsroom had been successful, and that the attackers appear to have been seeking email access to Post reporters who had Twitter accounts. The Post did not respond to requests for comment.
Update, August 16, 10:07 a.m. ET: Post spokesperson Kris Coratti finally responded, stating that the phishing attack and the site compromise were two separate incidents, and that one did not necessarily lead to the other. She emphasized that the site hack was the result of an attack on Outbrain, a third-party content recommendation site.
Original story:
But in a brief acknowledgment published today, The Post allowed that it had in fact been hacked, and in an update to that statement added that the source of the compromise was a phishing attack apparently launched by the SEA. From that message:
“A few days ago, The Syrian Electronic Army, allegedly, subjected Post newsroom employees to a sophisticated phishing attack to gain password information. The attack resulted in one staff writer’s personal Twitter account being used to send out a Syrian Electronic Army message. For 30 minutes this morning, some articles on our web site were redirected to the Syrian Electronic Army’s site. The Syrian Electronic Army, in a Tweet, claimed they gained access to elements of our site by hacking one of our business partners, Outbrain. We have taken defensive measures and removed the offending module. At this time, we believe there are no other issues affecting The Post site.”
According to sources, Post sports writer Jason Reid was among those who fell for a phishing scam that spoofed The Posts’s internal Outlook Web Access email portal (see screenshot above). Reid’s hacked email account was then used to send additional — likely malware-laced — phishing emails to other newsroom employees (see screenshot below). Reid did not respond to requests for comment.
Other well-known Posties came close to be tricked by the phishing attack. One of those nearly-phished was veteran Post staffer Gene Weingarten, one of the Post’s Pulitzer Prize winning editors and writers. Reached via email for comment, Weingarten was characteristically self-effacing about the whole ordeal (full disclosure: Gene edited my very first story to appear in The Washington Post, a 1996 Style section piece about living in the late President Gerald Ford‘s house, titled, “My Gerry Built Home“).
“I was phished….one of four, but I never entered any creds,” Weingarten wrote. “I’m stupid, but not THAT stupid.”
This type of phishing attack bears the hallmark of the SEA, which has taken credit for hijacking the Twitter accounts of several news outlets, perhaps most famously that of The Associated Press earlier this year. That campaign — which culminated in an unauthorized tweet sent from the AP’s Twitter account falsely claiming that bombs had exploded in the White House — briefly sent the Dow Industrial Average down 140 points.
As this incident highlights, phishing attacks and the phishers themselves are growing in sophistication. A survey released last month by Verizon Communications Inc. found nearly every incident of online espionage in 2012 involved some sort of phishing attack.
Update, August 16, 11:00 a.m. ET: One astute reader pointed out that the numeric Internet address (31.170.164.145) connected to the domain (site88[dot]net – see first screen shot above) used in the phishing attack against the Post this past weekend resides on the same subnet and hosting provider as blogs and Web sites belonging to some of the top Syrian Electronic Army members, including:
thepro[dot]sy (31.170.162.145)
victor[dot[thepro[dot]sy (31.170.162.145)
blog[dot]thepro[dot]sy (31.170.161.41)