This blog has featured stories about a vast array of impressive, high-tech devices used to steal money from automated teller machines (ATMs). But every so often thieves think up an innovation that makes all of the current ATM skimmers look like child’s play. Case in point: Authorities in Brazil have arrested a man who allegedly stole more than USD $41,000 from an ATM after swapping its security camera with a portable keyboard that let him hack the cash machine.

Photo: TV Bahia
The story comes from O Estado de S. Paulo (“The State of São Paulo“), a daily newspaper in Brazil’s largest city. According to the paper, late last month a crook approached an ATM at the Bank of Brazil and somehow removed the security camera from the machine. Apparently, the camera was a USB-based device, because the thief then was able to insert his own USB stick into the slot previously occupied by the camera. As you can imagine, a scene straight out of Terminator 2 ensued.
The attacker was then able to connect a folding keyboard to the ATM’s computer and restart the machine. The newspaper story isn’t crystal clear on the role of the USB device — whether it served as a replacement operating system or merely served to connect the keyboard to the machine (it’s not hard to imagine why this would be so easy, since most ATMs run on some version of Microsoft Windows, which automatically installs drivers for most USB-based input devices).
At any rate, after the thief rebooted the ATM’s computer, he was reportedly able to type the value of the currency notes that he intended to withdraw. According to the story, the thief started by removing all of the R $100 bills, and then moved on to the R $50 notes, and so on.

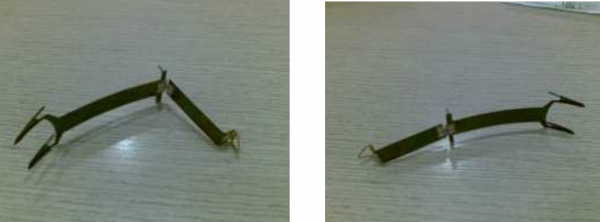
A crude skimming device removed from an Inova Hospital in Fairfax, Va. last month.
As clever as this hack was, the crook didn’t get away: The police were alerted by the central bank’s security team, and caught the thief in the process of withdrawing the funds. Brazilian authorities said they believe the man was being coached via phone, but that the guy they apprehended refused to give up the identity of his accomplice. My guess is the one coaching the thief had inside knowledge about how these machines operated, and perhaps even worked at a financial institution at one point.
These kinds of attacks make traditional ATM skimmer scams look positively prehistoric by comparison. But the sad part is that even really crude skimming devices can be very lucrative and go undetected for months. I was reminded of this last week, when, for the third time in as many months, authorities discovered ATM skimmers at hospitals within a few miles of here. Local police believe the same thieves are responsible for planting all of the fraud devices, which are relatively unsophisticated but nonetheless enabled the theft of thousands of dollars over a period of several weeks.
Continue reading →
![]() A majority of the bugs quashed in Microsoft’s patch batch are critical security holes, meaning that malware or miscreants could exploit them to seize control over vulnerable systems with little or no help from users. Among the critical patches is an update for Internet Explorer versions 9 and 10 (Redmond says these flaws are not present in earlier versions of IE).
A majority of the bugs quashed in Microsoft’s patch batch are critical security holes, meaning that malware or miscreants could exploit them to seize control over vulnerable systems with little or no help from users. Among the critical patches is an update for Internet Explorer versions 9 and 10 (Redmond says these flaws are not present in earlier versions of IE).