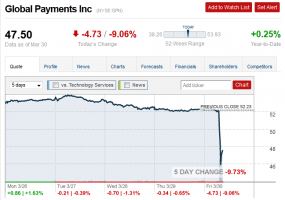
Global Payments Inc., the Atlanta-based credit and debit card processor that recently announced a breach that exposed fewer than 1.5 million card accounts, held a conference call this morning to discuss the incident. Unfortunately, that call created more questions than it did answers, at least for me. The purpose of this post is to provide some information that I have gathered, and a few observations about the reporting on this breach so far.
 In a conference call this morning, Paul Garcia, Chairman and CEO of Global Payments (NYSE: GPN), declined to offer few new details about how the breach happened, beyond the details the company released in its press release last night. He also declined to comment on reports that the breach may have dated back to at least January 2012. Garcia emphasized that the company self-reported and discovered the intrusion in early March, and proactively notified law enforcement officials and hired independent forensics investigators.
In a conference call this morning, Paul Garcia, Chairman and CEO of Global Payments (NYSE: GPN), declined to offer few new details about how the breach happened, beyond the details the company released in its press release last night. He also declined to comment on reports that the breach may have dated back to at least January 2012. Garcia emphasized that the company self-reported and discovered the intrusion in early March, and proactively notified law enforcement officials and hired independent forensics investigators.
When asked about the timeline first reported by KrebsOnSecurity.com last Friday — that Visa and MasterCard were warning of a payment processor that had an exposure between Jan 21, 2012 and Feb. 25, 2012 — Garcia said, without elaborating:
“There’s a lot of rumor and innuendo out there which is not helpful to anyone, and most of it incredibly inaccurate. In terms of other timelines, I just cannot be specific further about that.”
He went on to state that, “This does not involve our merchants, our sales partners, or their relationships with their customers. Neither merchant systems, or point of sale devices, were involved in any way. This was self-discovered and self-reported.” Databreaches.net has a decent round-up of the call details, as well as other reporting on this breach. A recording of the conference call is available here.
I’d like to share a few thoughts on my own reporting as it relates to this breach. First, when I published the story early last Friday morning that is widely credited as the first to break the news of a large processor breach, at that time I did not know for sure that Global Payments had been compromised. I’d heard it from one source, but could not get it from a second source. The old-school reporter in me held back those details from my story.
Several readers have called me irresponsible for quoting anonymous sources stating that the Global Payments breach may have affected more than 10 million cards. This is simply not true. I didn’t even mention Global Payments in my original piece. That information was dug up by reporters at The Wall Street Journal. Indeed, given GPN’s statements thus far, I continue to be nagged by the possibility that my initial reporting may have been related to a separate, as-yet undisclosed breach at another processor. I mentioned this to a reporter at ABC News today, who included my perspective in a story here.
RUMOR AND INNUENDO
GPN said it would allow an hour for the call and for questions, but it told callers at the beginning of the conference that it would be using a portion of the call time to talk about its 4th quarter earnings. Although I sat in on the GPN call this morning for the entire hour and waited in the queue to ask questions, I was not afforded the opportunity. Nor did I hear questions allowed from reporters at mainstream news media outlets cited in this story. The company has not yet responded to my questions, which I submitted in a phone call after the news conference.
What follows is a partial brain dump on some of the information and interesting tidbits I’ve been able to uncover in my reporting today, in no particular order. Some or all of them may turn out to be relevant to the Global Payments breach, to a separate incident, or not at all. Continue reading