Rove Digital, the company run by six men who were arrested in Estonia this week for allegedly infecting four million PCs worldwide with malware, was an early investor in ChronoPay, a major Russian payment processing firm whose principal founder Pavel Vrublevsky also is now in prison and awaiting trial on cyber crime charges, KrebsOnSecurity has learned.
Estonian authorities on Tuesday arrested Rove Digital founder Vladimir Tsastsin, 31, along with five other Estonian nationals indicted on charges of running a sophisticated click fraud scheme. Yesterday’s blog post details Tsastsin’s criminal history, and his stewardship over Rove and a sister firm, EstDomains.. Today’s post will reveal how Tsastsin and his company were closely allied with and early investors in ChronoPay, and how that relationship unraveled over the years.
In my Pharma War series, I’ve published incorporation documents showing that Igor Gusev, a man currently wanted in Russia on criminal charges of running an illegal business in the notorious pharmacy spam affiliate programs GlavMed and SpamIt, was a co-founder of ChronoPay back in 2003. That series also details how Gusev sold his shares in ChronoPay, and that Vrublevsky later started a competing rogue pharmacy/spam operation called Rx-Promotion.
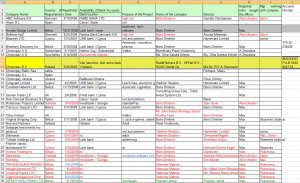
It turns out that ChronoPay also had two other major and early investors: Rove Digital and a mysterious entity called Crossfront Limited. This information was included in the massive trove of internal ChronoPay emails and documents that was briefly published online last year and shared with select journalists and law enforcement agencies. Among those documents is a spreadsheet (XLS) listing all of the various shadowy companies allegedly owned and managed by ChronoPay founder Pavel Vrublevsky and associates. It lists ChronoPay B.V., the legal entity in The Netherlands that formed the initial basis of the company, as jointly owned by Gusev’s firm DPNet B.V., Red & Partners (Vrublevsky’s adult Webmaster provider) and Rove Digital OU.
When I met with Vrublevsky at his offices in Moscow in February of this year, he confirmed that Tsastsin was an old friend and that Rove Digital had been a key shareholder in the company. Further evidence of the connection between ChronoPay and Rove Digital is provided in a series of internal ChronoPay emails from May 2010.
At that time, ChronoPay was under investigation by Dutch banking regulators who suspected that the company’s intricate network of front companies and financial channels were acting in violation of the country’s anti-money laundering laws. In a tersely-worded email exchange, the Dutch bank demanded a slew of additional accounting and administrative records, including “all documents that show the structure of ChronoPay BV, such as statutes, incorporation documents, names and addresses of director(s) and shareholders.”