Authorities in Ukraine this week detained five individuals believed to be the masterminds behind sophisticated cyber thefts that siphoned $70 million – out of an attempted $220 million — from hundreds of U.S.-based small to mid-sized businesses over the last 18 months, the FBI said Friday.
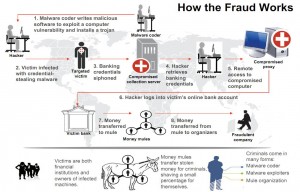 At a press briefing on “Operation Trident Breach,” FBI officials described the Ukrainian suspects as the “coders and exploiters” behind a series of online banking heists that have led to an increasing number of disputes and lawsuits between U.S. banks and the victim businesses that are usually left holding the bag.
At a press briefing on “Operation Trident Breach,” FBI officials described the Ukrainian suspects as the “coders and exploiters” behind a series of online banking heists that have led to an increasing number of disputes and lawsuits between U.S. banks and the victim businesses that are usually left holding the bag.
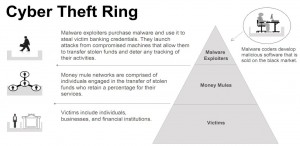
The FBI said five individuals detained by the Security Service of Ukraine (SBU) on Sept. 30 were members of a gang responsible for creating specialized versions of the password-stealing ZeuS banking Trojan and deploying the malware in e-mails targeted at small to mid-sized businesses.
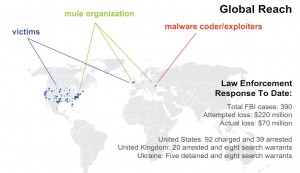
Investigators say the Ukrainian gang used the software to break into computers belonging to at least 390 U.S. companies, transferring victim funds to more than 3,500 so-called “money mules,” individuals in the United States willingly or unwittingly recruited to receive the cash and forward it overseas to the attackers. In connection with the investigation, some 50 SBU officials also executed eight search warrants in the eastern region of Ukraine this week.
Friday’s media briefing at the FBI Hoover building in Washington, D.C. was designed to give reporters a clearer view of the sophistication of an organized crime group whose handiwork had largely escaped broader national media attention until this week. On Wednesday, authorities in the United Kingdom charged 11 people there – all Eastern Europeans – with recruiting and managing money mules. Then on Thursday, officials in New York announced they had charged 92 and arrested 39 money mules, including dozens of Russians who allegedly acted as mules while visiting the United States on student visas.
 According to sources familiar with the investigation, the arrests, charges and announcements were intended to be executed simultaneously, but U.K. authorities were forced to act early in response to intelligence that several key suspects under surveillance were planning to flee the country.
According to sources familiar with the investigation, the arrests, charges and announcements were intended to be executed simultaneously, but U.K. authorities were forced to act early in response to intelligence that several key suspects under surveillance were planning to flee the country.
SBU officials could not be reached for comment. But FBI agents described the Ukrainian group as the brains behind the attacks. Gordon M. Snow, assistant director of the FBI’s Cyber Division, said the individuals detained by the SBU are thought to have worked with the developer of the ZeuS Trojan to order up custom-made components and versions of ZeuS.
For example, security researchers identified one ZeuS variant that was specific to the Ukrainians known as JabberZeuS because it alerted the gang via Jabber instant message whenever online banking credentials for customers of specific institutions were stolen.
Snow said this week’s law enforcement action was a particularly big deal because of the unprecedented level of cooperation from foreign governments, particularly Ukraine and the Netherlands.
“We worked with legal attachés in 75 countries, and we are very proud of the level of coordination that took place to get this done,” Snow said.
 Pim Takkenberg, team leader for the Netherlands Police Agency’s High Tech Crime Unit, said his group played a “small but important role” in helping to identify the hackers by monitoring the miscreants’ use of Dutch infrastructure.
Pim Takkenberg, team leader for the Netherlands Police Agency’s High Tech Crime Unit, said his group played a “small but important role” in helping to identify the hackers by monitoring the miscreants’ use of Dutch infrastructure.
“We helped in connecting all the dots together,” Takkenberg said in a phone interview. “The Netherlands provide for a large portion of the critical internet infrastructure, of which we can monitor certain parts. When criminals are unaware of the fact that they use Dutch infrastructure, that gives us good investigative opportunities. In this particular case we had an interest of our own, since the ZeuS malware made a lot of Dutch victims as well.”
The FBI’s Snow said the investigation began in May 2009, when FBI agents in Omaha, Neb. were alerted to automated clearing house (ACH) batch payments to 46 separate bank accounts through the United States.
I will continue to follow this important story in the days ahead, particularly as more information about the Ukrainian suspects is made public. Stay tuned.