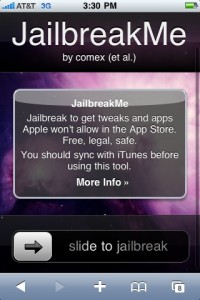
 One of the more interesting developments over the past week has been the debut of jailbreakme.com, a Web site that allows Apple customers to jailbreak their devices merely by visiting the site with their iPhone, iPad or iTouch. Researchers soon learned that the page leverages two previously unknown security vulnerabilities in the PDF reader functionality built into Apple’s iOS4.
One of the more interesting developments over the past week has been the debut of jailbreakme.com, a Web site that allows Apple customers to jailbreak their devices merely by visiting the site with their iPhone, iPad or iTouch. Researchers soon learned that the page leverages two previously unknown security vulnerabilities in the PDF reader functionality built into Apple’s iOS4.
Adobe was quick to issue a statement saying that the flaws were in Apple’s software and did not exist in its products. Interestingly, though, this same attack does appear to affect Foxit Reader, a free PDF reader that I often recommend as an alternative to Adobe.
According to an advisory Foxit issued last week, Foxit Reader version 4.1.1.0805 “fixes the crash issue caused by the new iPhone/iPad jailbreak program which can be exploited to inject arbitrary code into a system and execute it there.” If you use Foxit, you grab the update from within the application (“Help,” then “Check for Updates Now”) or from this link.
Obviously, from a security perspective the intriguing aspect of a drive-by type jailbreak is that such an attack could easily be used for more nefarious purposes, such as seeding your iPhone with unwanted software. To be clear, nobody has yet seen any attacks like this, but it’s certainly an area to watch closely. F-Secure has a nice Q&A about the pair of PDF reader flaws that allow this attack, and what they might mean going forward. Apple says it plans to release an update to quash the bugs.
I’m left wondering what to call these sorts of vulnerabilities that quite obviously give users the freedom that jailbreaking their device(s) allows (the ability to run applications that are not approved and vetted by Apple) but that necessarily direct the attention of attackers to very potent vulnerabilities that can be used to target jailbreakers and regular users alike. It’s not quite a “featureability,” which describes an intentional software component that opens up customers to attack even as the vendor insists the feature is a useful, by-design ability rather than a liability.
I came up with a few ideas.
– “Apptack”
– “Jailbait” (I know, I know, but it’s catchy)
– “Freedoom”
Maybe KrebsOnSecurity readers can devise a better term? Sound off in the comments below if you come up with any good ones.
Finally, I should note that while Adobe’s products may not be affected by the above-mentioned flaws, the company said last week that it expects to ship an emergency update on Tuesday to fix at least one critical security hole present in the latest version of Adobe Reader for Windows, Mac and Linux systems.
Adobe said the update will fix a flaw that researcher Charlie Miller revealed (PDF!) at last month’s Black Hat security conference in Las Vegas, but it hinted that the update may also include fixes for other flaws. I’ll have more on those updates when they’re released, which should coincide with one of the largest Microsoft Patch Tuesdays ever: Redmond said last week that it expects to issue at least 14 updates on Tuesday. Update, Aug. 10, 5:06 p.m. ET:Adobe won’t be releasing the Reader update until the week of Aug. 16.
![]() Adobe Systems Inc. today issued software updates to fix at least two security vulnerabilities in its widely-used Acrobat and PDF Reader products. Updates are available for Windows, Mac and UNIX versions of these programs.
Adobe Systems Inc. today issued software updates to fix at least two security vulnerabilities in its widely-used Acrobat and PDF Reader products. Updates are available for Windows, Mac and UNIX versions of these programs.