If your Windows PC has been hijacked by fake anti-virus software or “scareware” anytime in the past few years, chances are good that the attack was made possible by ChronoPay, Russia’s largest processor of online payments.
Tens of thousands of documents stolen and leaked last year from ChronoPay offer a fascinating look into a company that has artfully cultivated and handsomely profited from the market for scareware, programs that infiltrate victim PCs to display fake security alerts in a bid to frighten users into paying for worthless security software.

Click image for PDF version of timeline. Each entry is clickable and links to supporting documents.
ChronoPay handles Internet bill payments for a variety of major Russian companies, including domestic airlines and utilities. But ChronoPay also specializes in processing the transactions of so-called “high-risk” industries, including online pharmacies, tobacco sales, porn and software sales. A business is generally classified as high-risk when there is a great potential for credit card chargebacks and a fair chance that it will shut down or vanish without warning.
In June 2009, The Washington Post published the results of a six-month investigation into ChronoPay’s high-risk business. At the time, ChronoPay was one of a handful of processors for Pandora Software, the most prevalent brand of rogue software that was besieging consumers at the time. That story drew links between ChronoPay and an entity called Innovagest2000, which was listed as the technical support contact in the end-user license agreements that shipped with nearly all Pandora rogue anti-virus products.
When I confronted ChronoPay’s CEO Pavel Vrublevsky in 2009 about the apparent ties between Innovagest and his company, he insisted that there was no connection, and that his company’s processing services were merely being abused by scammers. But the recently leaked ChronoPay documents paint a very different picture, showing that Innovagest2000 was but one example of a cookie-cutter operation that ChronoPay has refined and repeated over the last 24 months.
The documents show that Innovagest was a company founded by ChronoPay’s Spanish division, and that ChronoPay paid for everything, from the cost of Innovagest’s incorporation documents to the domain registration, virtual hosting and 1-800 technical and customer support lines for the company.
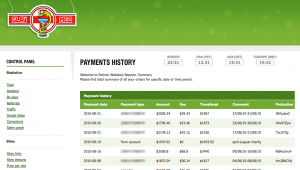
The same dynamic would play out with other ChronoPay “customers” that specialized in selling rogue anti-virus software. For example, leaked internal documents indicate that ChronoPay employees created two companies in Cyprus that would later be used in processing rogue anti-virus payments: Yioliant Holdings; and the strangely named Flytech Classic Distribution Ltd. ChronoPay emails show that employees also paid for domains software-retail.com and creativity-soft.com, rogue anti-virus peddling domains that were registered in the names and addresses of Yioliant Holdings and Flytech, respectively. Finally, emails also show that ChronoPay paid for the virtual hosting and telephone support for these operations. This accounting document, taken from one of the documents apparently stolen from ChronoPay, lists more than 75 pages of credit card transactions that the company processed from Americans who paid anywhere from $50 to $150 to rid their computers of imaginary threats found by scareware from creativity-soft.com (the amounts in the document are in Russian Rubles, not dollars, and the document has been edited to remove full credit card numbers and victim names).
Further, the purloined documents show these domains were aggressively promoted by external rogue anti-virus affiliate programs, such as Gelezyaka.biz, as well as a rogue anti-virus affiliate program apparently managed in-house by ChronoPay, called “Crusader.”
MEETING IN MOSCOW
Last month, I traveled to Moscow and had a chance to sit down with Vrublevsky at his offices. When I asked him about Innovagest, his tone was much different from the last time we discussed the subject in 2009. This may have had something to do with my already having told him that someone had leaked me his company’s internal documents and emails, which showed how integral ChronoPay was to the rogue anti-virus industry.
“By the time which correlates with your story, we didn’t know too much about spyware, and that Innovagest company that you tracked wasn’t used just for spyware only,” Vrublevsky said. “It was used for a bunch of shit.”
Vrublevsky further said that some of ChronoPay’s customers have in the past secretly sub-let the company’s processing services to other entities, who in turn used it to push through their own shady transactions. He offered, as an example, an entity that I wasn’t previously aware had been a customer of ChronoPay’s: A rogue anti-virus promotion program called TrafficConverter.biz.
Continue reading →
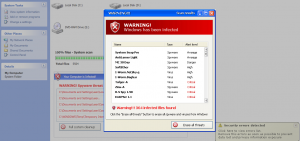 Scareware scams are nothing new to Skype: They have spread for some time now over the instant message client built into Skype, but this is the first I’ve heard of rogue anti-virus peddlers resorting to robocalls via Skype to spread their junk software.
Scareware scams are nothing new to Skype: They have spread for some time now over the instant message client built into Skype, but this is the first I’ve heard of rogue anti-virus peddlers resorting to robocalls via Skype to spread their junk software.