Security experts have long maintained that running two different anti-virus products on the same Windows machine is asking for trouble, because the programs inevitably will compete for resources and slow down or even crash the host PC.
Security experts have long maintained that running two different anti-virus products on the same Windows machine is asking for trouble, because the programs inevitably will compete for resources and slow down or even crash the host PC.
But an upstart anti-virus company called Immunet Protect is hoping Windows users shrug off this conventional wisdom and embrace the dual anti-virus approach. Indeed, the company’s free product works largely by sharing data about virus detections from other anti-virus products already resident on the PCs of the Immunet user community.
Users can run Immunet alone, and many do: The program scans files using two types of threat profiles: specific definitions or fingerprints of known threats, and generic signatures that are more akin to looking for a specific malware modus operandi.
But what makes Immunet different from other anti-virus products is that it also incorporates detections for malware from other anti-virus products that may be resident on users’ machines. For example, each time someone’s PC in the Immunet user base encounters a virus, that threat is logged and flagged on a centralized server so that all Immunet users can be protected from that newly identified malware.
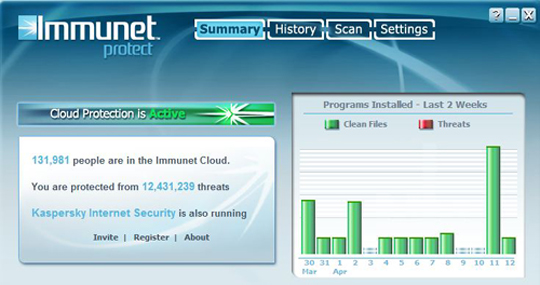
I’ve been running Immunet in tandem with Kaspersky Internet Security 2010 for the past three months, and have haven’t noticed any impact on system resources or stability issues. Immunet’s creators are especially proud of that last aspect of the program, and say it’s due to the fact that the program does most of its scanning and operations “in-the-cloud,” – that is, not on the user’s system. Immunet currently has about 133,000 active users, and that number changes constantly: Each time you reboot a system with it installed, chances are you will see a different – usually higher – number of users in the community.
I spoke recently with Immunet’s vice president of engineering, Alfred Huger, a former VP at Symantec Corp., and Adam O’Donnell, director of cloud engineering for the startup. That conversation — excerpts of which are included below — provides interesting insights into how the anti-virus industry operates, how consumers interact with these products, and how Immunet hopes to differentiate itself in already crowded field.