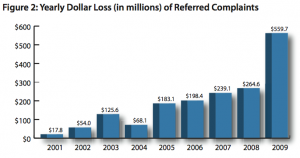
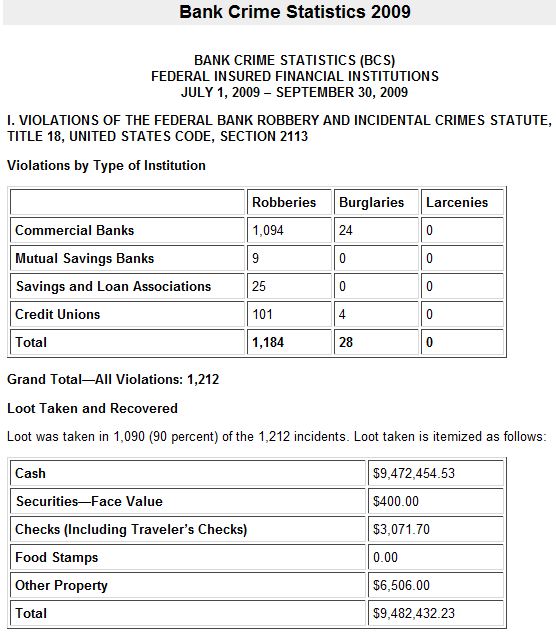
Over the past nine months, I have spent a substantial amount of time investigating and detailing the plight of dozens of small businesses that have had their bank accounts cleaned out by organized criminals. One of the most frequent questions I get from readers and from my journalist peers is, “How many of these stories are you going to tell?”
The answer is simple: As many as I can verify. The reason is just as plain: I’m finding that most small business owners have no clue about the threats they face or the liability they assume when banking online, even as the frequency and sophistication of attacks appears to be increasing.
I am now hearing from multiple companies each week that have suffered tens of thousands or hundreds of thousands of dollar losses from a single virus infection (last week I spoke with people from four different companies that had been victimized over the past two months alone). In each of these dramas, the plot line is roughly the same: Attackers planted malicious software on the victim’s PC to steal the company’s online banking credentials, and then used those credentials to siphon massive amounts of money from the targeted accounts. The twists to the stories come in how the crooks evade security technologies, how the banks react, and whether the customers are left holding the (empty) bag.
In most cases I’ve followed, the banks will do what they can to reverse the fraudulent transactions. But beyond that, the bank’s liability generally ends, because — unlike consumers — businesses do not have the same protection against fraud that consumers enjoy. Indeed, most companies that get hit with this type of fraud quickly figure out that their banks are under no legal obligation to reimburse them.
Earlier this month, I spoke with the CEO of Eskola LLC, a Treadway, Tenn. roofing firm that had $130,000 stolen from its online bank accounts in a series of five unauthorized wire transfers in late January. The bank was able to reverse most of those transfers, but Eskola was unable to recover more than $30,000 of the stolen money.
“It really took our bank by surprise and triggered a whole series of internal reviews, because they told me they’ve been hit several other times since then,” Jon Eskola said. “They said so far this year, it’s been the number one thing that’s come across their plate, and that this type of crime had increased 500 to 600 percent over a year ago.”