Part I of this series examined newly-leaked internal chats from the Conti ransomware group, and how the crime gang dealt with its own internal breaches. Part II explored what it’s like to be an employee of Conti’s sprawling organization. Today’s Part III looks at how Conti abused popular commercial security services to undermine the security of their targets, as well as how the team’s leaders strategized for the upper hand in ransom negotiations with victims.
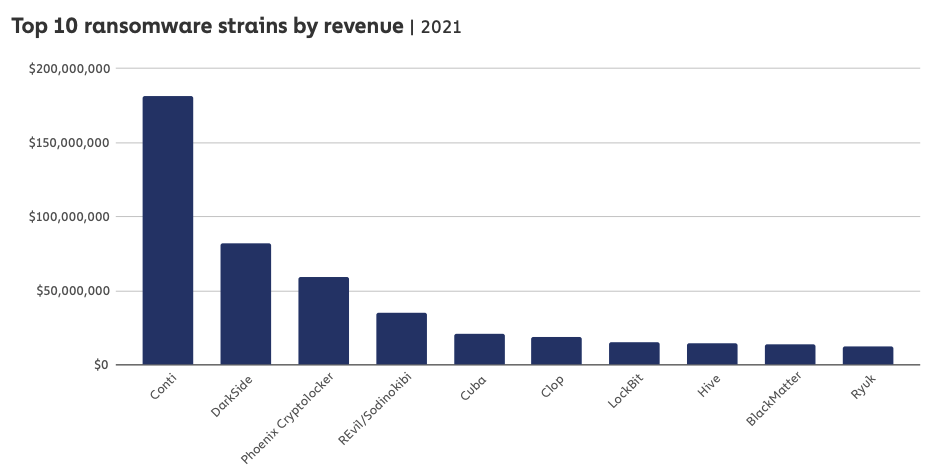
Conti is by far the most aggressive and profitable ransomware group in operation today. Image: Chainalysis
Conti is by far the most successful ransomware group in operation today, routinely pulling in multi-million dollar payments from victim organizations. That’s because more than perhaps any other ransomware outfit, Conti has chosen to focus its considerable staff and talents on targeting companies with more than $100 million in annual revenues.
As it happens, Conti itself recently joined the $100 million club. According to the latest Crypto Crime Report (PDF) published by virtual currency tracking firm Chainalysis, Conti generated at least $180 million in revenue last year.
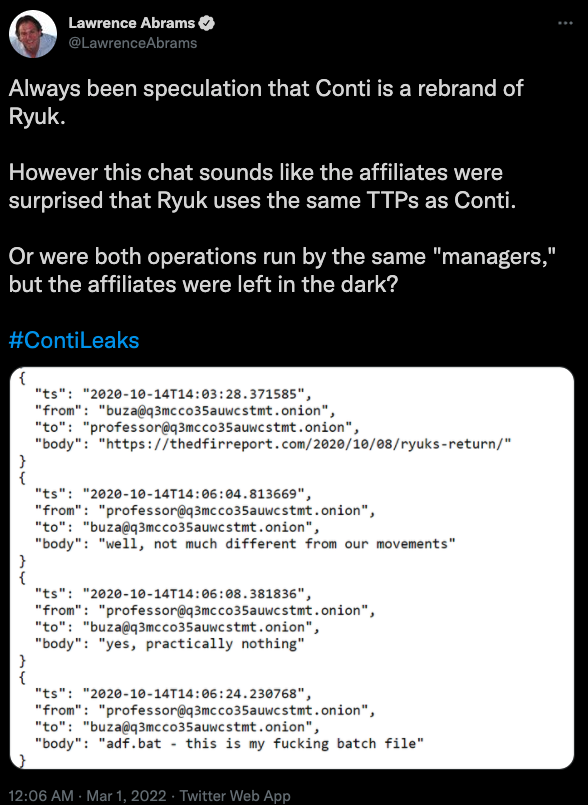
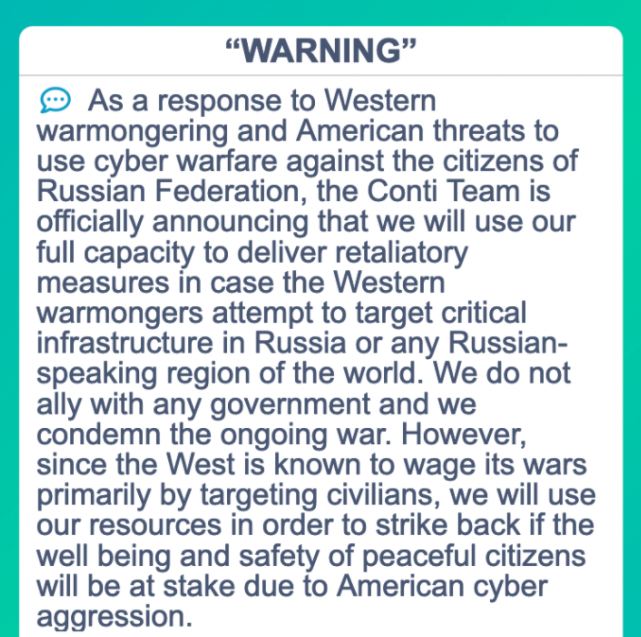
On Feb. 27, a Ukrainian cybersecurity researcher who is currently in Ukraine leaked almost two years’ worth of internal chat records from Conti, which had just posted a press release to its victim shaming blog saying it fully supported Russia’s invasion of his country. Conti warned it would use its cyber prowess to strike back at anyone who interfered in the conflict.
The leaked chats show that the Conti group — which fluctuated in size from 65 to more than 100 employees — budgeted several thousand dollars each month to pay for a slew of security and antivirus tools. Conti sought out these tools both for continuous testing (to see how many products detected their malware as bad), but also for their own internal security.
A chat between Conti upper manager “Reshaev” and subordinate “Pin” on Aug. 8, 2021 shows Reshaev ordering Pin to quietly check on the activity of the Conti network administrators once a week — to ensure they’re not doing anything to undermine the integrity or security of the group’s operation. Reshaev tells Pin to install endpoint detection and response (EDR) tools on every administrator’s computer.
“Check admins’ activity on servers each week,” Reshaev said. “Install EDR on every computer (for example, Sentinel, Cylance, CrowdStrike); set up more complex storage system; protect LSAS dump on all computers; have only 1 active accounts; install latest security updates; install firewall on all network.”
Conti managers were hyper aware that their employees handled incredibly sensitive and invaluable data stolen from companies, information that would sell like hotcakes on the underground cybercrime forums. But in a company run by crooks, trust doesn’t come easily.
“You check on me all the time, don’t you trust me?,” asked mid-level Conti member “Bio” of “Tramp” (a.k.a. “Trump“), a top Conti overlord. Bio was handling a large bitcoin transfer from a victim ransom payment, and Bio detected that Trump was monitoring him.
“When that kind of money and people from the street come in who have never seen that kind of money, how can you trust them 1,000%?” Trump replied. “I’ve been working here for more than 15 years and haven’t seen anything else.” Continue reading