When you write about complex subjects such as security for a mainstream publication like The Washington Post — as I did for so many years until very recently — you sort of have to assume that a non-trivial number of your readers don’t have the strongest grasp of technology and security issues. But I’m curious how krebsonsecurity.com readers would describe their level of comfort with computers and the steps it takes to remain safe online.
FBI Investigating Theft of $500,000 from NY School District
The FBI is investigating the theft of nearly a half million dollars from tiny Duanesburg Central School District in upstate New York, after cyber thieves tried to loot roughly $3.8 million from district online bank accounts last month.
 On Friday, Dec. 18, thieves tried to electronically transfer $1.86 million from the district’s account at NBT Bank to an overseas account. The following Monday, the attackers attempted to move another $1.19 million to multiple overseas location. It wasn’t until the next day, when transfers totaling $758,758.70 were flagged by a bank representative as suspicious, that the two previous unauthorized transactions were discovered, school officials said.
On Friday, Dec. 18, thieves tried to electronically transfer $1.86 million from the district’s account at NBT Bank to an overseas account. The following Monday, the attackers attempted to move another $1.19 million to multiple overseas location. It wasn’t until the next day, when transfers totaling $758,758.70 were flagged by a bank representative as suspicious, that the two previous unauthorized transactions were discovered, school officials said.
As of today, Duanesburg and its bank have succeeded in recovering $2.55 million of the stolen funds, but the school district is still out $497,000.
Hackers May Have Unearthed Dirt on Stanford
In early 2008, while federal investigators were busy investigating disgraced financier Robert Allen Stanford for his part in an alleged $8 billion fraudulent investment scheme, Eastern European hackers were quietly hoovering up tens of thousands customer financial records from the Bank of Antigua, an institution formerly owned by the Stanford Group.
 According to a fraud investigator with first-hand knowledge of the break-in, the hackers responsible infiltrated a component of the Stanford Group’s network by exploiting vulnerabilities in the company’s Web servers and databases. On the condition of anonymity, the investigator shared with this author files recovered from the breach, which were stored in plain text for at least several weeks on a Web site controlled by the attackers. This source said he forwarded the same information on to the FBI shortly after discovering it in early 2008.
According to a fraud investigator with first-hand knowledge of the break-in, the hackers responsible infiltrated a component of the Stanford Group’s network by exploiting vulnerabilities in the company’s Web servers and databases. On the condition of anonymity, the investigator shared with this author files recovered from the breach, which were stored in plain text for at least several weeks on a Web site controlled by the attackers. This source said he forwarded the same information on to the FBI shortly after discovering it in early 2008.
Once inside of Stanford’s network, the unidentified hackers appear to have swiped the credentials from an internal network administrator, and soon had downloaded the user names and password hashes for more than 1,000 employees of Stanford Financial, Stanford Group, Stanford Trust, and Stanford International Bank Ltd.
Among the purloined files is a listing of what appear to be ownership and balance information for tens of thousands of customer accounts at Bank of Antigua. Each listing includes the account number, owner’s name, address, balance, and accrued interest.
Mr. Stanford is set to go on trial this month for allegations that he led a $8 billion fraud scheme. In addition, federal authorities reportedly have been investigating whether Stanford was involved in laundering drug money for Mexico’s notorious Gulf Cartel.
Security Tweaks for Adobe Reader
Adobe is planning to ship an update a week from today that fixes a critical vulnerability in its free and widely used PDF Reader program. Unfortunately, according to experts, criminal hackers are starting to step up attempts to exploit the flaw and install malicious software via poisoned PDFs.
Buried Warning Signs
In a year marked by record bank failures and Wall Street swindlers walking away with tens of billions of investor dollars, it’s perhaps not surprising that the activities of organized cyber gangs looting at least $100 million dollars from small to mid-sized businesses went largely unheralded.
 The mainstream media could be forgiven for focusing on bigger fish. For one thing, this particular strain of fraud has many moving parts and is challenging to explain to broad audiences. Also, raising awareness about fraud is always tough because the issue almost invariably involves U.S. banks and federal law enforcement, two entities that by their very genetic makeup resist discussing anything that is not tightly scripted and on-message: The FBI is hyper-reluctant to discuss or even acknowledge ongoing investigations (particularly those in which the main actors are overseas), and the banks simply don’t want to spook customers in any way.
The mainstream media could be forgiven for focusing on bigger fish. For one thing, this particular strain of fraud has many moving parts and is challenging to explain to broad audiences. Also, raising awareness about fraud is always tough because the issue almost invariably involves U.S. banks and federal law enforcement, two entities that by their very genetic makeup resist discussing anything that is not tightly scripted and on-message: The FBI is hyper-reluctant to discuss or even acknowledge ongoing investigations (particularly those in which the main actors are overseas), and the banks simply don’t want to spook customers in any way.
But law enforcement and the banking industry appear to have been at odds over how and how much to communicate with the public about the seriousness and impact of these crimes. The following anecdotes offer a peek into some of the struggles I experienced last year trying to extract useful and truthful information from both parties.
Friday, Aug. 21, 3:00 p.m. ET: I was wrapping up a story for The Washington Post about a confidential alert drafted by the Financial Services Information Sharing and Analysis Center (FS-ISAC), an industry group representing some of the nation’s largest banks. The document I’d gotten hold of seemed to validate the focus of my reporting for the previous 10 weeks: It said the FBI was tracking a major upswing in incidents involving organized computer thieves who were using malicious software to steal tens and hundreds of thousands of dollars from countless small- to mid-sized businesses throughout the United States.
I had finagled a draft version of the alert, and understood that the final version would be sent sometime later that day, although the distribution list was reportedly limited to a few hundred people — mostly law enforcement and bankers. Problem was, I couldn’t confirm whether the alert had in fact been sent as planned, or whether the final version was changed much from the version I’d obtained.
What’s more, after two days of waiting, I still had no meaningful response from the FBI to my query, which sought to verify the alert’s statement that the FBI believes organized cyber thieves involved in this type of crime were stealing at least a million dollars a week from victims, and that several new victim firms were coming forward each week.
My editor was restless: Without an answer to these questions, the story would hold until next week. The answers didn’t come, and the story held.
When I finally got confirmation the following Monday that the alert had gone out, I also learned that the final version had been significantly watered down. Gone were the monetary damage estimates, including this stark assessment: ‘Total economic impact of these activities, if they continue unabated, is likely to be in the hundreds of millions of dollars.’
Gone was any mention of specific countries to which the stolen tens of millions were flowing (Russia, Ukraine and Moldova). Removed was the part about the quasi-financial institutions responsible for the cross-border flow of stolen cash (Moneygram and Western Union).
Mind you, this was an alert that was not intended for public distribution, but merely to be sent to a small group of banks and law enforcement folks.
Virus Scanners for Virus Authors
I have often recommended file-scanning services like VirusTotal and Jotti, which allow visitors to upload a suspicious file and scan it against dozens of commercial anti-virus tools. If a scan generates any virus alerts or red flags, the report produced by the scan is shared with all of the participating anti-virus makers so that those vendors can incorporate detection for the newly discovered malware into their products.
That pooling of intelligence on new threats also serves to make the free scanning services less attractive to virus authors, who would almost certainly like nothing more than to freely and simultaneously test the stealth of their new creations across a wide range of security software. Still, there is nothing to stop an enterprising hacker from purchasing a license for each of the anti-virus tools on the market and selling access to a separate scanning service that appeals to the virus-writing community.
Enter upstart file-scanning services like av-check.com and virtest.com, which bank on the guarantee that they won’t share your results with the anti-virus community.
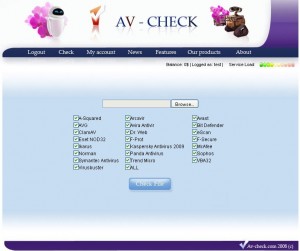 For $1 per file scanned (or a $40 monthly membership) av-check.com will see if your file is detected by any of 22 anti-virus products, including AVAST, AVG, Avira, BitDefender, NOD32, F-Secure, Kaspersky, McAfee, Panda, Sophos, Symantec, and Trend Micro. “Each of them is setten [sic] up on max heuristic check level,” av-check promises. “We guarantee that we don’t save your uploaded files and they are deleted immediately after the check. Also , we don’t resend your uploaded files to the 3rd person. Files are being checked only locally (without checking/using on other servers.” In other words: There is no danger that the results of these scans will somehow leak out to the anti-virus vendors.
For $1 per file scanned (or a $40 monthly membership) av-check.com will see if your file is detected by any of 22 anti-virus products, including AVAST, AVG, Avira, BitDefender, NOD32, F-Secure, Kaspersky, McAfee, Panda, Sophos, Symantec, and Trend Micro. “Each of them is setten [sic] up on max heuristic check level,” av-check promises. “We guarantee that we don’t save your uploaded files and they are deleted immediately after the check. Also , we don’t resend your uploaded files to the 3rd person. Files are being checked only locally (without checking/using on other servers.” In other words: There is no danger that the results of these scans will somehow leak out to the anti-virus vendors.
The service claims that it will soon be rolling out advanced features, such as testing malware against anti-spyware and firewall programs, as well as a test to see whether the malware functions in a virtual machine, such as VMWare or VirtualBox. For safety and efficiency’s sake, security researchers often poke and prod new malware samples in a virtual environment. As a result many new families of malware are designed to shut down or destroy themselves if they detect they are being run inside of a virtual machine.
 Virtest checks malware suspicious files against a similar albeit slightly different set of anti-virus programs, also promising not to let submitted files get back to the anti-virus vendors: “Your soft isn’t ever sent anywhere and the files being checked will never appear in the fresh AV signature bases after scanning,” the site pledges. “On purpose in all AV-products are turned off all possible methods and initiatives of exchange of files’ info with the AV-divisions.”
Virtest checks malware suspicious files against a similar albeit slightly different set of anti-virus programs, also promising not to let submitted files get back to the anti-virus vendors: “Your soft isn’t ever sent anywhere and the files being checked will never appear in the fresh AV signature bases after scanning,” the site pledges. “On purpose in all AV-products are turned off all possible methods and initiatives of exchange of files’ info with the AV-divisions.”
The proprietors of this service don’t even try to hide the fact that they have built it for malware writers. Among the chief distinguishing features of virtest.com is the ability for malware authors to test “exploit packs,” pre-packaged kits that — when stitched into a malicious or hacked Web site — serve the visitor’s browser with a kitchen sink full of code designed to install software via one of several known security holes. Many anti-virus programs now also scan Web pages for malicious content, and this service’s “exploits pack check” will tell malware authors whether their exploit sites are triggering virus alerts across a range of widely-used anti-virus software.
But don’t count on paying for these services via American Express: Both sites only accept payment via virtual currencies such as Webmoney and Fethard, services that appear to be popular with the online shadow economy.
Welcome to Krebsonsecurity.com
Welcome, everyone, to krebsonsecurity.com. Here’s to new beginnings, and a happy, healthy and prosperous New Year!
Some of you may be familiar with my work at The Washington Post and the Security Fix blog. Krebsonsecurity.com will feature similar content: Original reporting and analysis on important security threats and trends.
With a few exceptions, I will continue to eschew chasing the security story-of-the day, as there are plenty of sites you can go to for that. My focus will remain on publishing information and reporting that you won’t find anywhere else – and with a minimum of editorializing.
Visitors who are unfamiliar with my work can browse through a collection of what I think represents some of my best reporting over the past few years. The About the Author and About this Blog tabs include a bit more detail about who I am and how this blog will be organized.
Finally, this blog will be a whole lot more interesting if folks participate, so if you’ve got something to add or have a strong feeling one way or another on a topic, take a second to leave your comments and voice your opinion. I will be moderating comments, but only for spam and probably only at the outset of this blog launch (unless your post is truly offensive to other readers, exists merely to pimp some product, links to nasty sites, etc). If you want to shoot me a note directly, send it here.
Thanks for visiting, and look for actual reporting and news content here in the next 24 hours or so as I iron out a few remaining kinks in the blog.
Story-Driven Résumé: My Best Work 2005-2009
I began writing for The Washington Post in 1996, and started covering computer and Internet security in 1999. Below are links to what I believe is some of my best work over the past four years or so. Virtually all of the stories and blog posts listed here were either Washington Post/Security Fix exclusives, or were the result of my investigative reporting and research aimed at shining a light on the Internet’s darkest corners, and educating readers about the importance of security.