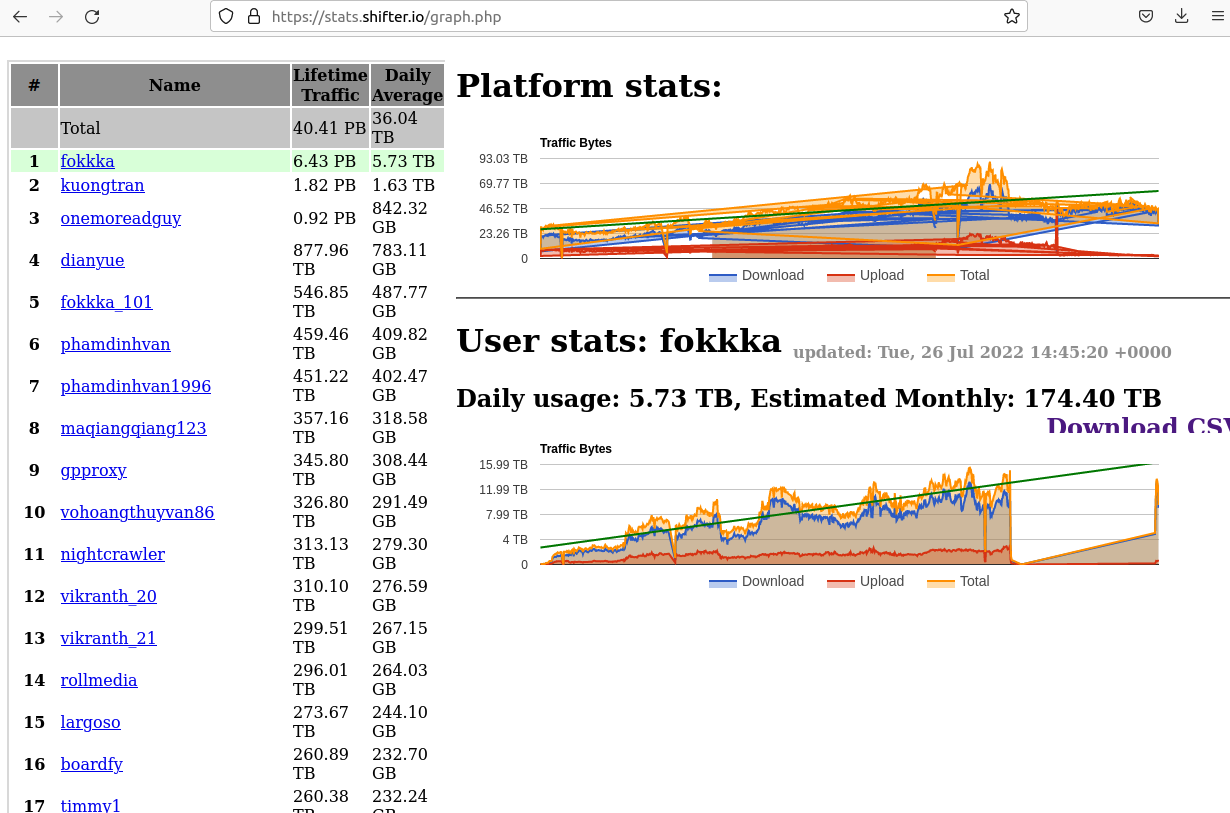
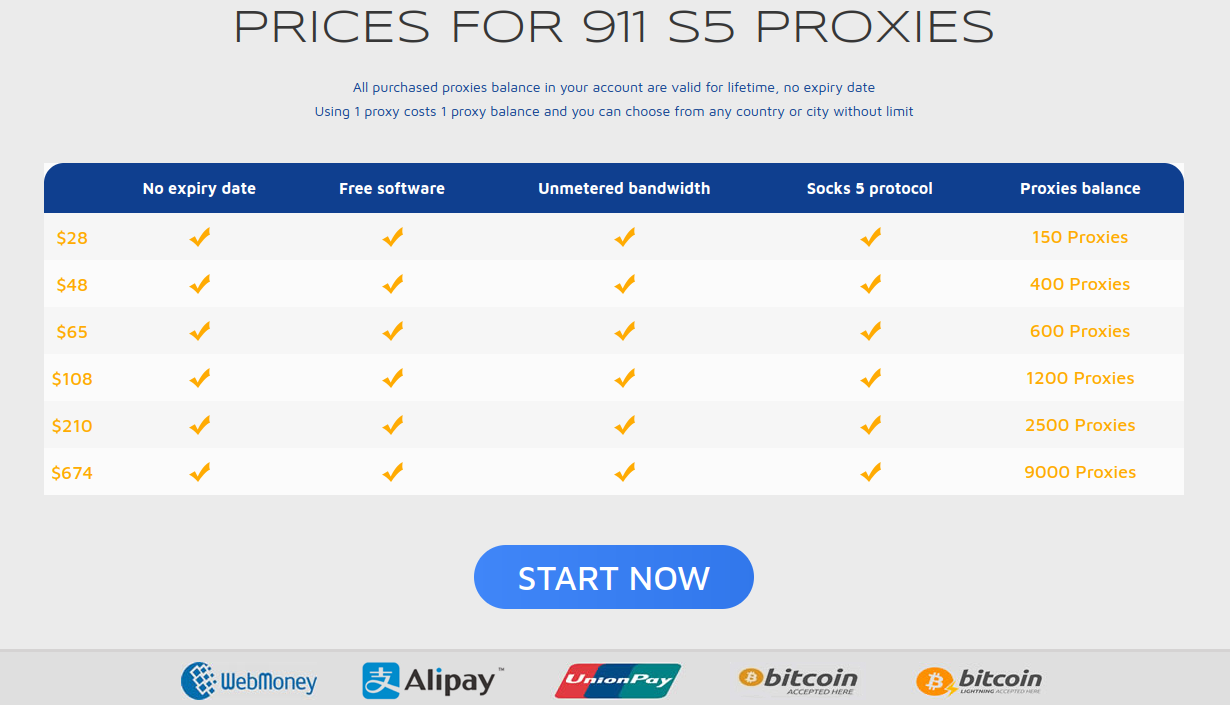
A class action lawsuit has been filed against big-three consumer credit bureau Experian over reports that the company did little to prevent identity thieves from hijacking consumer accounts. The legal filing cites liberally from an investigation KrebsOnSecurity published in July, which found that identity thieves were able to assume control over existing Experian accounts simply by signing up for new accounts using the victim’s personal information and a different email address.

The lawsuit, filed July 28, 2022 in California Central District Court, argues that Experian’s documented practice of allowing the re-registration of accounts without first verifying that the existing account authorized the changes is a violation of the Fair Credit Reporting Act.
In July’s Experian, You Have Some Explaining to Do, we heard from two different readers who had security freezes on their credit files with Experian and who also recently received notifications from Experian that the email address on their account had been changed. So had their passwords and account PIN and secret questions. Both had used password managers to pick and store complex, unique passwords for their accounts.
Both were able to recover access to their Experian account simply by recreating it — sharing their name, address, phone number, social security number, date of birth, and successfully gleaning or guessing the answers to four multiple choice questions that are almost entirely based on public records (or else information that is not terribly difficult to find).
Here’s the bit from that story that got excerpted in the class action lawsuit:
KrebsOnSecurity sought to replicate Turner and Rishi’s experience — to see if Experian would allow me to re-create my account using my personal information but a different email address. The experiment was done from a different computer and Internet address than the one that created the original account years ago.
After providing my Social Security Number (SSN), date of birth, and answering several multiple choice questions whose answers are derived almost entirely from public records, Experian promptly changed the email address associated with my credit file. It did so without first confirming that new email address could respond to messages, or that the previous email address approved the change.
Experian’s system then sent an automated message to the original email address on file, saying the account’s email address had been changed. The only recourse Experian offered in the alert was to sign in, or send an email to an Experian inbox that replies with the message, “this email address is no longer monitored.”
After that, Experian prompted me to select new secret questions and answers, as well as a new account PIN — effectively erasing the account’s previously chosen PIN and recovery questions. Once I’d changed the PIN and security questions, Experian’s site helpfully reminded me that I have a security freeze on file, and would I like to remove or temporarily lift the security freeze?
To be clear, Experian does have a business unit that sells one-time password services to businesses. While Experian’s system did ask for a mobile number when I signed up a second time, at no time did that number receive a notification from Experian. Also, I could see no option in my account to enable multi-factor authentication for all logins.
In response to my story, Experian suggested the reports from readers were isolated incidents, and that the company does all kinds of things it can’t talk about publicly to prevent bad people from abusing its systems.
“We believe these are isolated incidents of fraud using stolen consumer information,” Experian’s statement reads. “Specific to your question, once an Experian account is created, if someone attempts to create a second Experian account, our systems will notify the original email on file.”
“We go beyond reliance on personally identifiable information (PII) or a consumer’s ability to answer knowledge-based authentication questions to access our systems,” the statement continues. “We do not disclose additional processes for obvious security reasons; however, our data and analytical capabilities verify identity elements across multiple data sources and are not visible to the consumer. This is designed to create a more positive experience for our consumers and to provide additional layers of protection. We take consumer privacy and security seriously, and we continually review our security processes to guard against constant and evolving threats posed by fraudsters.”
That sounds great, but since that story ran I’ve heard from several more readers who were doing everything right and still had their Experian accounts hijacked, with little left to show for it except an email alert from Experian saying they had changed the address on file for the account. Continue reading