A Ukrainian security researcher this week leaked several years of internal chat logs and other sensitive data tied to Conti, an aggressive and ruthless Russian cybercrime group that focuses on deploying its ransomware to companies with more than $100 million in annual revenue. The chat logs offer a fascinating glimpse into the challenges of running a sprawling criminal enterprise with more than 100 salaried employees. The records also provide insight into how Conti has dealt with its own internal breaches and attacks from private security firms and foreign governments.
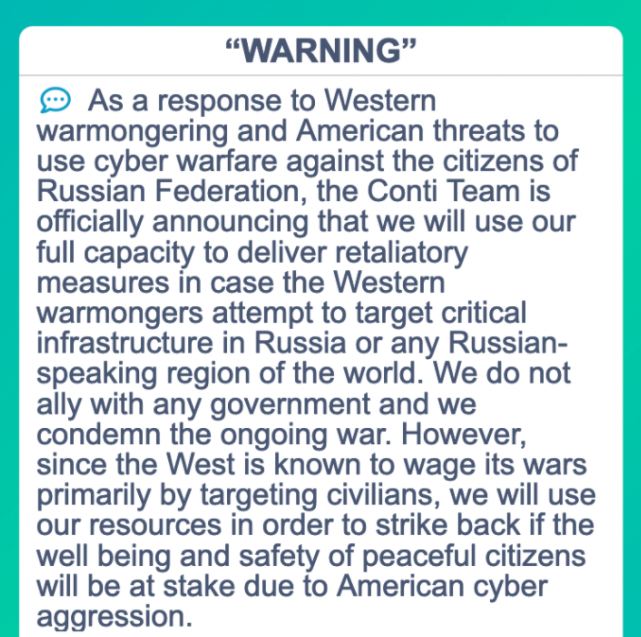
Conti’s threatening message this week regarding international interference in Ukraine.
Conti makes international news headlines each week when it publishes to its dark web blog new information stolen from ransomware victims who refuse to pay an extortion demand. In response to Russia’s invasion of Ukraine, Conti published a statement announcing its “full support.”
“If anybody will decide to organize a cyberattack or any war activities against Russia, we are going to use all our possible resources to strike back at the critical infrastructures of an enemy,” the Conti blog post read.
On Sunday, Feb. 27, a new Twitter account “Contileaks” posted links to an archive of chat messages taken from Conti’s private communications infrastructure, dating from January 29, 2021 to the present day. Shouting “Glory for Ukraine,” the Contileaks account has since published additional Conti employee conversations from June 22, 2020 to Nov. 16, 2020.
The Contileaks account did not respond to requests for comment. But Alex Holden, the Ukrainian-born founder of the Milwaukee-based cyber intelligence firm Hold Security, said the person who leaked the information is not a former Conti affiliate — as many on Twitter have assumed. Rather, he said, the leaker is a Ukrainian security researcher who has chosen to stay in his country and fight.
“The person releasing this is a Ukrainian and a patriot,” Holden said. “He’s seeing that Conti is supporting Russia in its invasion of Ukraine, and this is his way to stop them in his mind at least.”
GAP #1
The temporal gaps in these chat records roughly correspond to times when Conti’s IT infrastructure was dismantled and/or infiltrated by security researchers, private companies, law enforcement, and national intelligence agencies. The holes in the chat logs also match up with periods of relative quiescence from the group, as it sought to re-establish its network of infected systems and dismiss its low-level staff as a security precaution.
On Sept. 22, 2020, the U.S. National Security Agency (NSA) began a weeks-long operation in which it seized control over the Trickbot botnet, a malware crime machine that has infected millions of computers and is often used to spread ransomware. Conti is one of several cybercrime groups that has regularly used Trickbot to deploy malware.
Once in control over Trickbot, the NSA’s hackers sent all infected systems a command telling them to disconnect themselves from the Internet servers the Trickbot overlords used to control compromised Microsoft Windows computers. On top of that, the NSA stuffed millions of bogus records about new victims into the Trickbot database.
News of the Trickbot compromise was first published here on Oct. 2, 2020, but the leaked Conti chats show that the group’s core leadership detected something was seriously wrong with their crime machine just a few hours after the initial compromise of Trickbot’s infrastructure on Sept. 22.
“The one who made this garbage did it very well,” wrote “Hof,” the handle chosen by a top Conti leader, commenting on the Trickbot malware implant that was supplied by the NSA and quickly spread to the rest of the botnet. “He knew how the bot works, i.e. he probably saw the source code, or reversed it. Plus, he somehow encrypted the config, i.e. he had an encoder and a private key, plus uploaded it all to the admin panel. It’s just some kind of sabotage.”
“Moreover, the bots have been flooded with such a config that they will simply work idle,” Hof explained to his team on Sept. 23, 2020. Hof noted that the intruder even kneecapped Trickbot’s built-in failsafe recovery mechanism. Trickbot was configured so that if none of the botnet’s control servers were reachable, the bots could still be recaptured and controlled by registering a pre-computed domain name on EmerDNS, a decentralized domain name system based on the Emercoin virtual currency.
“After a while they will download a new config via emercoin, but they will not be able to apply this config, because this saboteur has uploaded the config with the maximum [version] number, and the bot is checking that the new config [version number] should be larger than the old one,” Hof wrote. “Sorry, but this is fucked up. I don’t know how to get them back.”
It would take the Conti gang several weeks to rebuild its malware infrastructure, and infect tens of thousands of new Microsoft Windows systems. By late October 2020, Conti’s network of infected systems had grown to include 428 medical facilities throughout the United States. The gang’s leaders saw an opportunity to create widespread panic — if not also chaos — by deploying their ransomware simultaneously to hundreds of American healthcare organizations already struggling amid a worldwide pandemic.
“Fuck the clinics in the USA this week,” wrote Conti manager “Target” on Oct. 26, 2020. “There will be panic. 428 hospitals.”
On October 28, the FBI and the U.S. Department of Homeland Security hastily assembled a conference call with healthcare industry executives warning about an “imminent cybercrime threat to U.S. hospitals and healthcare providers.”
Follow-up reporting confirmed that at least a dozen healthcare organizations were hit with ransomware that week, but the carnage apparently was not much worse than a typical week in the healthcare sector. One information security leader in the healthcare industry told KrebsOnSecurity at the time that it wasn’t uncommon for the industry to see at least one hospital or health care facility hit with ransomware each day. Continue reading