NetworkSolutions Sites Hacked By Wicked Widget
Hundreds of thousands of Web sites parked at NetworkSolutions.com have been serving up malicious software, thanks to a tainted widget embedded in the pages, a security company warned Saturday.
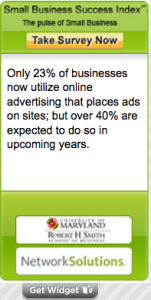 Web application security vendor Armorize said it found the mass infection while responding to a complaint by one of its largest customers. Armorize said it traced the problem back to the “Small Business Success Index” widget, an application that Network Solutions makes available to site owners through its GrowSmartBusiness.com blog.
Web application security vendor Armorize said it found the mass infection while responding to a complaint by one of its largest customers. Armorize said it traced the problem back to the “Small Business Success Index” widget, an application that Network Solutions makes available to site owners through its GrowSmartBusiness.com blog.



