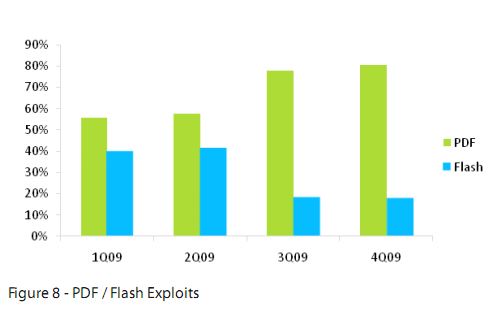
Adobe is urging users of its PDF Reader and Acrobat software to install an update that fixes a couple of critical security holes in the products. The patches come amid news that booby-trapped PDF files were responsible for roughly 80 percent of the exploits detected in the 4th quarter of 2009.
The latest update brings Adobe Reader to version 9.3.1, and fixes a pair of vulnerabilities that Adobe has labeled “critical,” which means the flaws could be used to install malicious software on vulnerable systems. Updates are available for Windows, Mac and Linux versions.
If you use Adobe Reader, please apply this update. Then, take a moment to turn off Javascript, the feature in Reader that is most exploited by attackers. To do this, follow these instructions:
1. Launch Acrobat or Adobe Reader.
2. Select Edit>Preferences
3. Select the JavaScript Category
4. Uncheck the ‘Enable Acrobat JavaScript’ option
5. Click OK
Better yet, consider using an alternative PDF reader, such as the free Foxit Reader. I also disable Javascript in Foxit, mainly because I find I don’t need it.
Earlier this week, Web security firm ScanSafe released a report (.pdf !) showing that roughly 80 percent of the Web-based exploits it detected in the last three months of 2009 attacked Adobe Reader vulnerabilities. Add Adobe Flash vulnerabilities into the mix, and the two programs made up the lion’s share of the Web exploits ScanSafe detected in Q409.
For its part, Firefox maker Mozilla at the end of last year began tracking a huge uptick in the number of Firefox crashes due to Adobe Reader. As some posters to this Mozilla Bug Database entry posit, the crashes were almost certainly due to increased exploitation of the Adobe Reader zero-day vulnerability that Adobe finally patched on Jan. 12, weeks after evidence surfaced that criminal hackers were exploiting the flaw in targeted attacks.
Update, 4:06 p.m. ET: If you decide to do without Adobe Reader and uninstall it, you might want to nix the Adobe Download Manager as well. Researcher Aviv Raff points to some nifty work he’s done which shows that Adobe’s Download Manager — which ships with all new versions of Flash and Reader — can be forced to reinstall an application that’s been removed, such as Reader. According to Raff, a Web site could hijack the Adobe Download manager to download and install any of the following:
Adobe Flash 10
- Adobe Reader 9.3
- Adobe Reader 8.2
- Adobe Air 1.5.3
- ARH tool – allows silent installation of Adobe Air applications
- Google Toolbar 6.3
- McAfee Security Scan Plus
- New York Times Reader (via Adobe Air)
- Fanbase (via Adobe Air)
- Acrobat.com desktop shortcut
Raff writes: “So, even if you use an alternative PDF reader, an attacker can force you to download and install Adobe Reader, and then exploit the (yet to be patched, but now known) vulnerability. The attacker can also exploit 0-day vulnerabilities in any of the other products mentioned above.” Read more on his findings at this link here.




The PDF format used to be about putting documents into a medium where the OS, office suite, and fonts didn’t matter and could be easily shared so as long as the recipients also had a PDF reader.
Those of you going to Adobe’s site to grab the installer (which as of last night was still 9.3.0) and fortunate enough to see the ad of the suit will notice that in an effort to stay relevant and keep shops paying up for Acrobat, PDFs can embed multimedia. This also means that without Reader, multimedia-embedded PDFs will not be fully readable in other readers.
It should also go without saying that introducing these doo-dads adds new vectors for exploitation.
Where have we seen this kind of behavior before where a standard format became laden with proprietary garbage in order for the company responsible for it to stay relevant and keep users upgrading?
The PDF format should stick to what it is best for and not try to be a reinvention of HTML. Lose the JavaScript and other doo-dads. In the meantime, since Adobe won’t warn you about any scripting in PDFs (except that you should turn JS back on), it would be wise to completely disable the PDF browser plugin and let your browser hand off the PDF to the application of your choice.
I don’t really like the idea of a non-native PDF reader. Apple’s Preview.app has come leaps and bounds over the years. We running OS X have no need for this excess Adobe flotsam and jetsam. And today both Safari and Preview cover this natively and that’s a big boon.
Seen this?
http://secunia.com/blog/75
SMH @ Adobe. Warnock and Jobs used to be such good friends. They invented DTP together. What happened? Maybe Adobe get the brunt end of the stick these days but what’s happened? They’re acting like losers on the way out.
Thank you yet again, Brian.
My copy of Adobe Reader 9.3 (installed without the accursed Download Manager) didn’t want to install the update, so I downloaded it from here:
ftp://ftp.adobe.com/pub/adobe/reader/win/9.x/9.3.1/misc/AdbeRdrUpd931_all_incr.msp
Just run the file (with Reader closed).
It would be nice to see a correlation between attack vectors and attacked systems. To know better what type of malicious code was being used, what the malware strategy was, how it targeted which systems, and which systems were theoretically vulnerable and to what degree. 99.9% of the attacks were on Windows and we know that. What we need to know is to what extent these attack vectors can be used to push through malicious code on other platforms (if at all).
The reason these “attack vectors” keep appearing in Adobe products is because the company keeps injecting their new flying baloney into what was and should be a static file format.
PDF stands for Portable DOCUMENT Format. Not Portable FLASH Format. But don’t tell the newly acquired via M&A clubkids and offshored-to-Chindia “developers” that.
That’s why turning off Javascript and all the new(er) bells and whistles WORKS to disable all of these so-called exploits.
Where this is really leading is that Adobe wants to give content bunnies the ability to track who opened a PDF and for how long. Why else would you acquire a spyware {del} {del} “metrics” company like Omniture?
Trouble is, the hackers got to Adobe’s janky frameworks first, and spoiled the party. Awwwww, poor Adobe. Embed scripts in PDF and what did you think was going to happen?
I really loved parent post. Anybody who starts a handle with ‘drunken’ gets my vote just for humour contribution alone. And there are many good points presented as well. The semantics are not pedantic – they’re spot on. Cheers.
It’s really a shame that an ISV are creating so many issues. OK, so what happens if the clever black hats decide to provide attacks on multiple platforms from the same exploit? It’s been done before, people yawned a lot, but it can be done again. Adobe are quickly winning a special place in our hearts as the premier screw-up company.
Here’s the good news – at a stretch: we don’t really need PDF all that much and that CPU hog ‘flash’ could soon be gone with HTML5.
But where does that leave DTP? 😉
And to think Warnock started his days as an adept with Kay @ PARC… 😉
Thanks Brian
Have followed your advice, not that I am aware of any Adobe PDF Reader issues.
I’m not that familiar with Java Script from a technical standing. By disabling it what do I loose and should I disable it everywhere, or will that cause more problems than it would solve?
Also, as a former headhunter in both the engineering and the computer field, Compuserve with Management Recruiters some years ago, can you recommend any top shops in DP where such employment investigation might be fruitful
Ironically, most headhunting can be broken down to a simple formula, namely [function performing ability = functions to be performed.] While you must have or acquire knowledge about ‘said functions,’ the folks you are seeking out either have both sides of this equation or they don’t. The rest you pick up along the way
Brian
My objective is to whenever possible become INDISPENSABLE to the employer. That translates into much more than a 9-5 job, especially since most ‘raids’ [active recruitment efforts] as opposed to pursuing help wanted ad responses must occur after work hours in the evening. Perhaps one of my more noteable searches was for the position of Associate Justice of the US Supreme Court for a Hispanic candidate. This search was carried out twice under two separate Administrations c/o the Office of White House Counsel.
The candidate identified was Garza, who the 11pm news leaked [inaccurately] had received the nomination, but in the morning Justice Thomas was announced.
We finally got our Hispanic jurists, but long after the 500 year celebration of Hispanics in America — 1492 to 1992.
Since Adobe at least uses the Microsoft installer for its updates, your readers with several computers to update can use a logon script or the at command to easily apply the patches. It takes me about 2 minutes to run a simple batch files to update everyone from my workstation. Use a /q after the file name to turn off the dialog boxes. Here’s a sample that puts the patch on workstation1 at 5:30 pm.
copy c:\downloads\AdbeRdrUpd931_all_incr.msp \\workstation1\c$\patches
at \\workstation1 17:30 c:\patches\AdbeRdrUpd931_all_incr.msp /q
Of course you must have adminstrative rights.
To install any of the free Adobe products _without_ the pointless/insecure/cursed Adobe Download Manager, say no to any IE/Firefox “install software” popups/information bars that appear. Then click the manual “click here to download” link instead. The resulting .exe will not install ADM.
Thanks, B rian, for another great, useful article.
I’ve been using Foxit, on your recommendation, a long time now. Can you tell us how to disable Javascript in Foxit?
Thanks very much!
John
One question. I don’t have Adobe Reader as an application (Mac G5 PPC), but Acrobat Pro. I updated it per instructions to 9.3.1, but Safari still has Adobe Acrobat and Reader Web browser plug-in 9.3.0. How is the plug-in updated?
So, you can’t ask anyone for job leads on line without getting serious disapproval.
If this snow storm should have made anything clear it is all can get caught unprepared. Just imagine the humility that I had to evidence, to even ask.
YOUR DAY WILL COME SOON ENOUGH — OUCH
I give up; I am uninstalling adobe reader. Why bother with it?
I have had trouble with Adobe Acrobat Pro 9 now for five days and counting. The upgrades don’t appear to work and the help desk is clueless and just keeps repeating the same steps.
It has interfered with my operating programs.
I would be on the look out for problems to grow with Adobe.
I may go back to Version 6 – I did not have half the problems I have incurred in the last week.
I should add that their web site no longer works well with Internet Explorer 8 and basic settings. They added too much and it freezes.