Organized cyber thieves took roughly $600,000 from the coastal city of Brigantine, New Jersey this week after stealing the city’s online banking credentials.
 The break-in marks the second time this year that hackers have robbed the coffers of an Atlantic County town: In March, a similar attack struck Egg Harbor Township, N.J., which lost $100,000 in a similar intrusion.
The break-in marks the second time this year that hackers have robbed the coffers of an Atlantic County town: In March, a similar attack struck Egg Harbor Township, N.J., which lost $100,000 in a similar intrusion.
Like the Egg Harbor incident and dozens of others documented here, the loot from the Brigantine heist was sent to multiple “money mules,” willing or unwitting people hired through work-at-home job offers to help computer crooks launder stolen cash.
Brigantine City officials said the incident began sometime before 6 p.m. on September 28th, when TD Bank notified city finance officers that multiple wire transfers had been made from its accounts. Brigantine Police’s Lt. James Bennett said in a written statement:
“Unknown person(s) had apparently obtained a user name and password for the city’s main TD Bank account when our finance personnel attempted to login (through either a fake Web page or an undetectable virus). Then several wire transfers were started with amounts ranging from a few thousand to over $300,000, for a total of about $600,000. The last update from TD Bank was that they were able to recall approximately $400,000 in transfers and were working on recalling the remainder. The investigation is being handled by the FBI, New Jersey State Police with the Brigantine Police Department and TD Bank security.”
The attack occurred in the middle of a week in which federal officials announced dozens of arrests and charges against money mules and the organized criminals responsible for orchestrating these types of break-ins. While it’s unclear whether those responsible for the attack on Brigantine were apprehended or charged this week, the method by which the thieves made off with at least some of the loot bears the same fingerprint as past breaches, including the Egg Harbor attack.
Lori Tharp, a 47-year-old from Goodlettsville, TN, said she recently started working for an entity calling itself the Forte Group, which found her résumé on Careerbuilder.com and recruited her into a work-at-home job where she was to serve as a “financial agent” for the company.
Tharp, who recently lost her job as a buyer for a local automotive supplier, said she figured out the job was a money laundering scam several days before the Brigantine robbery, and closed the bank account she had given her erstwhile employers. But she said the thieves still tried to transfer her $7,394 of the city’s money on Sept. 29. Tharp said she confirmed with her bank that the thieves never managed to deposit the stolen funds.
“Just last week the group called me again and told me they had put money into my account, but I told them it had already been closed,” Tharp said in a phone interview. “There’s too many people out of work, and I guess I just got overwhelmed and excited at the same time and made a stupid move.”
Brigatine Mayor Phil Guenther told pressofatlanticcity.com he is confident that the city will recoup its losses. Still, it remains to be seen whether these types of attacks will diminish following the law enforcement sweeps last week aimed at one of the largest international organized crime gang involved in this type of activity. According to the FBI, crooks involved in e-banking fraud have stolen more than $70 million from companies, small businesses, towns, cities and nonprofits, and attempted to steal more than $220 million.
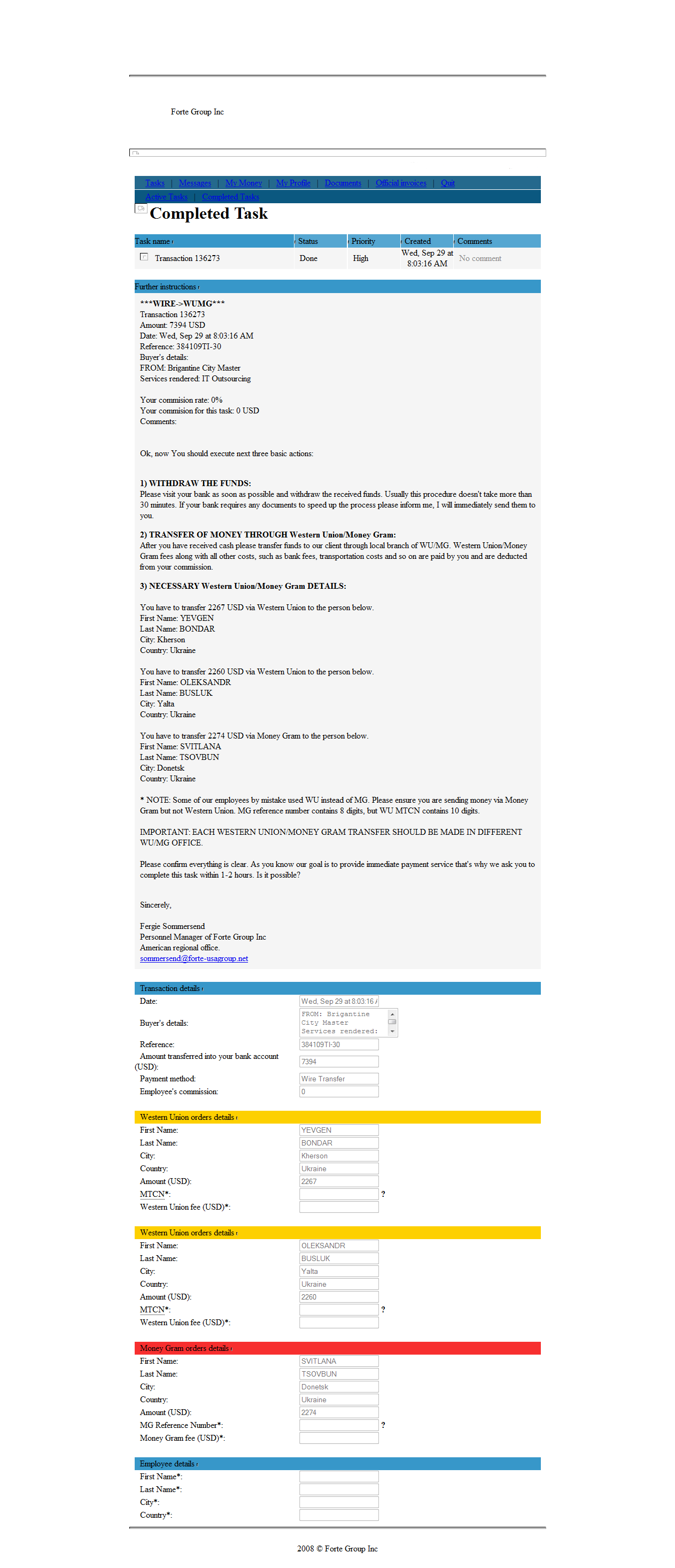
Below is a screen shot of the alert the Forte Group sent Tharp on the day of the Brigantine breach. Click the image for a larger version.




Brian,
Thanks for continuing to shine a light on these illicit activities. I need to point some friends here to further their education about computer safety and security.
A couple of quick comments – in para 3, you have a ‘help help” phrase, and in the para where you introduce Lori Tharp, you say “found her job on Careerbuilder’, I think you must have meant “found her resume”…
Keep up the good work!
Scott
Hi Brian
I’m not sure that placing so much of the emphasis on the mules is very helpful; wouldn’t it be better to delve into whether Brigantine and other towns and cities are using best practice or learning from the others misfortunes.
Mules are only useful once the criminals have already broken into the bank… ultimately it’s better to stop them before they get in the bank rather than fill jails with feckless mules after the event.
You are right about focusing on security best practices, but it’s important to work on all links of this chain. For BK’s usual audience of security-oriented folk, it makes sense to push end-user security, but it is a huge help to push education about money mules, as well.
If we can stop or slow money mules, it will stop or slow the money, which is, after all, the only reason the criminals do what they do. If we can make it harder for them to get their money, it might make them think twice about this type of crime.
Surely the first sign after having the money wired to your account is that the email of additional instructions is written in poor English. This is meant to be a professional company, “Ok, now You should execute next three basic actions:”. Not only that, but then at the bottom is says to do the transfers at _different_ WU offices.
I have to disagree with prior comments, if people are given an education about such matters, then there would be fewer money mules and the money laundering would become harder.
I’m not sure a jail sentence for money mules is sensible, but perhaps a bit more education so they don’t get caught out again… Then you’d have to spot repeat offenders, there might be a reason they’re doing it, blackmail comes immediately to mind.
Dominic, I wish I could agree with you, but I’ve seen worse English in published documents written by native speakers. I grant you that the message is obviously written by someone who, among other things, doesn’t know how to use articles, but as I read the letter I found myself thinking that the crooks have become pretty sophisticated. Whoever came up with name “Forte” has some grasp of American branding.
With or without an education, Ms. Tharp realized what was going on and closed her bank account. So, an education is always a good thing.
That’s one of the first mules who seemed to have basic critical thinking skills (or was an honest person). Can anyone read that they need to make three deposits at three different offices and *not* think there’s something criminal going on?
During my painful stint with unemployment a while back, I too saw a few of these type of offers hit my mailbox. But, either term “work at home” or “financial agent”, or worse when combined in the same sentence, just start triggering red flags all over the place!
Sounds like Ms. Tharp was smart enough to quickly recognize the error she made and did the right thing in the end. And she went further and closed her bank account to protect herself. Very smart. 🙂
Perhaps her on-the-job experience as buyer for an automotive supplier provided her vital clues.
Was Brigantine not aware of what had happened to Egg HArbor? Or were they aware, but just didn’t bother to take precautions? Why didn’t the county police inform everyone of what had happened last March.
I would hope that, here in Fairfax County VA, if Vienna got attacked this way that Herndon would be immediately notified and would take precautions.
Changes to IT in city governments take a lot of time. Even if some in the organization were aware of the problem, it’s very possible red tape slowed them down, or that their security was compromised a while ago, and is was only just now being exploited. It’s fortunate for them that they got so much of their money back already. That means they noticed it quickly and their bank was fast on the reaction.
I hope they get most of their money back. It’s not easy to recover, though, and the longer it takes, the harder it is.
When I first began reading about online banking compromising, I was sympathetic. However, as time has past and the online banking security curve of users stay at the bottom of the bell, I’m becoming apathetic. Are the business/towns in an informatio9n coma? Every entity should now be aware of the danger of online banking. Momma said, “Stupid is as stupid does.”
After working in various facets of IT for over 14 years now, I can tell you from experience, people really are that stupid! It’s a harsh statement, but the truth! I used to hold out hope, in fact I used to go to great lengths to educate people and help secure their computers. But, there is absolute truth to the axiom, you can lead a horse to water… Now I’m just apathetic and wholeheartedly believe Ron White’s line, “You can’t fix stupid!”.
A prime example:
http://www.nbcmiami.com/news/local-beat/911-Does-Not-Stand-for-Emergency-in-Broward-104294569.html
Brian, have the authorities found that “sting” operations at places like Careerbuilder are not workable?
I don’t know of any sting operations of the sort you suggest. And I doubt they would be terribly successful.
The reason is that US prosecutors don’t want to have to haul one of these regular clueless mules up in front of a jury and try to explain to a jury of their peers why this person should go to jail.
Brian ,
First off I will never comment on any on going investigation (s) . The bottom line starts here , COMPUTER EDUCATION yup you got it . Now that I just opened pandora”s box lets start with safe surfing , the proper use of flash drives , antivirus and antimalware products . I can go on and on , a computer like a car turn the key and go . When something goes wrong with the car like the motor seizes up well we can all “ASS U ME ” we didn’t check the oil . Maybe they where never instructed of how to check the oil . The same applies to “COMPUTER EDUCATION” Who’s at fault now?
By the way if you way to have a good laugh , go to the nearest BestBuy and just listen to all the the stories at the geek squad counter . And that’s entertainment folks, bring lunch with you .
“When something goes wrong with the car like the motor seizes up well we can all “ASS U ME ” we didn’t check the oil . Maybe they where never instructed of how to check the oil ”
What about the manual that comes with the car?
The difference here is that damaging your car due to not reading the manual is your own problem and you have to pay for it. An infected bot is everyone’s problem and we all pay for it.
If this is a different gang and it’s based in (Mother) Russia, it will be more difficult to roll up.
KFritz- It could well be based in Russia. If you look at where the money is being wired to, though, it appears to be flowing to Ukraine.
I agree with Brian , this is what the news is reporting at this time .
Brian,
Do the banks get any kind of ABP or letter of warning sent to them for each “occassion” of massive wire fraud?
It demonstrates the banks (domestic and International) are not in communication between each other or at least not fast enough.
Given the timing of the other arrests this week it sounds like these cons bugged out with what the could out of fear of also have been compromised by FBI and other agencies.
Was there ever and Interpol (Orange Notice ) or whatnot ever issued on any of the ID theft + mule operations? Or are such handled by different channels?
Ed — I’ve deleted your ridiculously foul-mouthed comment. Please note that any comments that contain that kind of gross profanity will be deleted.
Brian, hate to say this , there’s one in every bunch .
One thing I keep wondering about. Common anti-fraud practices would require one employee to file a payment and another to release it. Thus, these towns are (a) either not adhering to common sense anti-fraud rules (b) all their staff is using one and the same PC for e-banking or (c) the crooks have spyware on more than one PC. I’m guessing one or more of the above, but (a) is the most daming: Even without any crooks in Ukraine going after your money, it would be irresponsible as a municipality to have one single employee/userid both file and authorize payments on an account that contains this kind of money.
Here is a good start for ebanking , one computer is locked down solely for this action . Then no unauthorized flash drives allowed oh yeh no surfing . There are flash drives out solely for the use of banking , and make sure your antivirus , antimalware is up to date and fully functional . Run scans before and after your bank session . Don’t forget to clean your system after use , there are many product out to do this .
TEMPTATION is when your in a room doing your on line banking for the company , hey no one is around and looking what your doing so you surf check your e-mails along with other sites . You just compromised your system , toss it out .
Just some basics to think about .
I have a 20-buck electronic key to protect my cloud computing account with a second authentication factor. A similar key is available for savings accounts and stock trading accounts. I can boot to a frozen OS on a CD or virtual machine.
I _can_ use any of these technologies for low cost, sacrificing a little time and a little convenience.
How can a municipality justify convenient online banking where outbound transfers are unaudited, and create no flags? You get those features for ten bucks a month from a credit card processor. We have the technology. We choose not to use it to make things more convenient. (Is it cheaper? Maybe, as long as you don’t get hit. Ask an underwriter if they’d take the risk for no extra fee.)
A simple expiring passcode would allow access for minutes instead of days, weeks, months. Electronic request/approve cycles would mimic traditional check writing processes where more than one data entry clerk saw the final transaction.
IMHO, there _are_ situations where bureaucracy and inconvenience are advantageous, and even prudent. Maybe that’s just paranoia.
Maybe somebody in Brigantine will be more paranoid in the future.
While I am not justifying neglectful actions by towns that should know better and implement strong information security measures I am always amazed the banks process these transactions. Shouldn’t new payees and massive transactions send off all kinds of alerts that make them just as responsible in the end. I am guessing these type of things should be sending off all kinds of warning signals vs. typical transactions the town did.
Hopefully this will finally be a wake-up call for the Jersey shore!
21st century stage coach robbery… The thing I find the most outrageous is the thieves have the audacity to deducted wire, bank and transportation fees from the mule’s “commission”! Unbelievable.