An organized cyber crime gang known for aggressively pushing male enhancement drugs and other knockoff pharmaceuticals used Internet addresses belonging to Microsoft as part of a massive denial-of-service attack against KrebsOnSecurity.com late last month.
 The attack on my Web site happened on Sept. 23, roughly 24 hours after I published a story about a criminal online service that brazenly sold stolen credit card numbers for less than $2 each (see: I’ll Take Two MasterCards and a Visa, Please). That story got picked up by BoingBoing, Gizmodo, NPR and a variety of other sites, public attention that no doubt played a part in the near-immediate suspension of that criminal Web site.
The attack on my Web site happened on Sept. 23, roughly 24 hours after I published a story about a criminal online service that brazenly sold stolen credit card numbers for less than $2 each (see: I’ll Take Two MasterCards and a Visa, Please). That story got picked up by BoingBoing, Gizmodo, NPR and a variety of other sites, public attention that no doubt played a part in the near-immediate suspension of that criminal Web site.
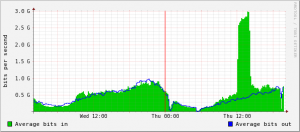
At first, it wasn’t clear what was behind the attack, which at one point caused a flood of traffic averaging 2.3 gigabits of junk data per second (see graph above). Not long after the attack ended, I heard from Raymond Dijkxhoorn and Jeff Chan, co-founders of SURBL, which maintains a list of Web sites that have appeared in spam. Chan sent me a message saying he had tracked the attack back to several Internet addresses, including at least one that appeared to be located on Microsoft’s network — 131.107.202.197.
According to SURBL, the culprits were botnets under the thumb of “the usual Russian pill gangs”: Dozens of domains that resolve(d) to online pharmacy sites — including bridgetthefidget.com, crazygraze.com, firstgang.com, triplefixes.com and philsgangdirect.com — were using a compromised machine at that Microsoft address as a domain name server.
The attackers then told machines they controlled to access a number of non-existent pages at sites that were pointing to the Internet address my hosting provider has assigned to KrebsOnSecurity.com (94.228.133.16). This forced several hundred or thousand machines to direct their traffic at my site, all in an attempt to prevent legitimate visitors from visiting it.
For example, the attack packets included DNS for false requests such as:
mzkzalczdznzjzfbszvzazd.jumpgirlsaloud.nl A 94.228.133.163
sdfsdfsdfsdfsdffbszvzazd.youralveolarbone.nl A 94.228.133.163
zzncmzkzalczdznzjzfbszvzazd.cheapxenonbulbs.com A 94.228.133.163
zzncmzkzalczdznzjzfbszvzazd.expletivedirect.com A 94.228.133.163
I found the unusual method of attack interesting because it called attention to a significant amount of infrastructure used by the bad guys. For all I know, this may have been intentional, either to let me know who was responsible, or to make me think I knew who was responsible.
In any case, the attack took place in the early morning U.S. time, and by the time I’d woken up that day, my hosting provider, Dijkxhoorn’s Prolocation.net, had already dealt with the attack handily. Chan said SURBL had alerted Microsoft regarding the compromised IPs, and I filed the information away for a future blog post but for a variety of reasons forgot about it. Until Tuesday.
That’s when I read a story in The Register by tech reporter Dan Goodin, who wrote that for the past three weeks, Internet addresses belonging to Microsoft had been used to route traffic to more than 1,000 fraudulent pharmacy Web sites maintained by a notorious group of Russian criminals responsible for promoting Canadian Health&Care Mall pill sites. That story jogged my memory because it highlighted the very same Microsoft IP address that was implicated in the attack on my site.
Ronald F. Guilmette, the security researcher who shared that information with The Register, told KrebsOnSecurity that the pharmacy domains referenced in Goodin’s story appeared to be tied to an ICANN-accredited domain registrar in Turkey named Alantron. Although the pill site domain names that were associated with the Microsoft server are registered through a variety of non-Alantron registrars, all of them appear to use DNS servers tied to Alantron’s domain.
For example, bafereuti.com, lixduoxbe.com and others as of late Tuesday used yok15.alantron.com, and dozens of other pill sites associated with this gang use similar Alantron DNS entries, all the way up to yok87.alantron.com, yok88.alantron.com, and yok89.alantron.com. A complete list is available here.
Alantron did not respond to requests for comment. Again, the Alantron connection could be just willful misdirection on the part of the pill pushers. Still, the company has a history of abuse and neglect issues. In April, ICANN warned Alantron that it was in breach of its registrar accreditation agreement with ICANN because it failed to provide a WHOIS server to allow visitors to look up the ownership information of domains registered through its service. A copy of that ICANN order is available here (PDF).
 Guilmette said that since The Register story ran, Microsoft appears to have addressed the compromised system on its network. Redmond did not respond to requests for comment about the compromised server; no doubt, most of their botnet experts are tied up at Microsoft’s Digital Crimes Consortium, an anti-botnet conference going on this week up in…well Canada, naturally.
Guilmette said that since The Register story ran, Microsoft appears to have addressed the compromised system on its network. Redmond did not respond to requests for comment about the compromised server; no doubt, most of their botnet experts are tied up at Microsoft’s Digital Crimes Consortium, an anti-botnet conference going on this week up in…well Canada, naturally.
In just one of the many ironies in this story, the compromised server inside of Microsoft appears to have been running Linux, not one of Microsoft’s server technologies. According to Guilmette, all of the hacked servers used by this pill gang are Unix or Linux servers. This mode of operation matches that of “Bulker.biz,” a rogue pharmacy affiliate program known for promoting rogue “Canadian Health&Care Mall” pill sites — as well as a number of other brands — by hijacking poorly-secured Linux and Unix servers.
Update, 7:34 p.m. ET: Christopher Budd, Microsoft’s response manager for trustworthy computing, sent this statement via email: “Microsoft became aware of reports on Tuesday, October 12, 2010, of a device on the Microsoft network that was possibly compromised and facilitating spam attacks. Upon hearing these reports, we immediately launched an investigation. We have completed our investigation and found that two misconfigured network hardware devices in a testing lab were compromised due to human error. Those devices have been removed and we can confirm that no customer data was compromised and no production systems were affected. We are taking steps to better ensure that testing lab hardware devices that are Internet accessible are configured with proper security controls.”




The in/out bandwidth is almost identical for most of the day. Does the graph not include a different (smaller) bitrate for inbound bandwidth? After all, I assume your site is mostly serving?
Also I’m curious what a normal graph would look like, when you’re not being linked to from Boingboing etc.
HA! Well! A little mud on Redmond, and a feather in your cap for your fine journalism!!
Obviously you are doing a fine, fine job of exposing the little rats as they skitter into the shadows! HA! :^0
Just more kudos to Brian, in my not so humble opinion!
Your explanation of the attack is unclear. Are you saying that the attack packets were DNS requests? Requests don’t contain IP addresses. They’re also typically UDP, which means you can’t actually trace their origin.
If the attack packets were DNS answers, which can contain IP addresses, again, these are typically UDP, and you still can’t trace the origin of the corresponding requests, since those also are UDP and you don’t even see them.
What makes you think the Microsoft IP(s) were on compromised systems? If this was a DNS amplification attack of some kind, then the Microsoft system(s) may simply have been performing DNS recursion.
Was this attack really just a high load of HTTP requests using virtual host names that did not reside on the server that host’s krebsonsecurity.com? If so, is krebsonsecurity.com the only site hosted on the target server? If not, you might be a unintended victim of an attack on some other virtual host that resolves to the same IP. In addition, the appearance of those hostnames in HTTP requests doesn’t demonstrate that DNS was involved in any way in the attack; the bots could be instructed to contact 94.228.133.163 and issue HTTP requests with randomly synthesised Host: headers.
I think also you are getting into pretty thinly supported speculation when you imply that groups that happen to target UNIX and Linux systems are somehow cooperating.
The krebs site is not on a shared server. Traffic was combined http flooding and udp flooding.
Congratulations, Brian. You know you’re somebody when you’ve garnered enough attention to invite your own attack. Keep up the good work.
BTW – still seeing viruses attacking HP software/drivers – several different versions now.
As a team of legitimate, licensed Canadian pharmacies; The Canadian International Pharmacy Association places patient safety as our top priority in serving seniors using valid prescriptions to obtain maintenance medications for chronic conditions – and none of our members resort to Spam. We’re glad you are shining a light on the bad guys, so the good guys (CIPA) can continue to serve American patients who are burdened by the high cost of U.S. drugs.
Thanks for your hard work and let us know if we can assist in your efforts.
Welcome, Tim. I enjoyed meeting you last week. Will be in touch soon. Thanks for dropping by.
> The krebs site is not on a shared server. Traffic was combined http flooding and udp flooding.
That answers one question.
In what specific way was DNS involved? And what is the meaning of the statement in the article that “the attack packets included DNS for false requests” that contain A RRs?
I’m moderately amused to observe that two people have voted down my comment above. If they think there’s something technically wrong with it, they should respond with rebuttal. I can only assume they don’t know much.
Hi antibozo,
Not everything you said makes sense to me, for instance why do you say attack packets based on UDP are untraceable?, but other things do and imho they are legitimate questions. I’m very fond of Brian’s column and he’s far above other journalists when reporting about security. But he’s human and might omit information, make mistakes, etc. To come to my point, it is a bit disconcerting to me that comments challenging any of Brian’s statements using an appropriate language and essentially adding value to the discussion are thumbed-down so heavily by other participants like they are blasphemies against an intangible god. I think the voting buttons are meant to be used to single-out comments with inappropriate language, SPAM, with no connection to the subject, before the moderator can remove them and not to burn-at-stake anyone whose (lack of) religious fervor makes him ask challenging questions.
I was wondering the same thing what is the difficulty of monitoring the traffic also would appear highly improbably that just at the time of the release of a very revealing article that an attack of such magnitude occurs, emanating from associated suspected locations also identified in someone else’s work, was not designed to prevent access to the article.
The difficulty with UDP traffic is that it is trivial to forge UDP packets with false source addresses. In some cases such packets will be filtered at egress from the origin networks but in many or most cases they will not. Because UDP packets can carry payloads without first establishing bidirectional communication (unlike TCP), the forged packets can actually accomplish things even though the sender will never see replies (because replies will be routed to the forged address, not the sender’s true address).
An example using RFC1918 addresses: an attacker might be sitting on 192.168.0.1 and transmitting packets that have a source IP of 172.16.0.1 and destination IP of 10.0.0.1. These packets get routed to 10.0.0.1, and 10.0.0.1 has no way of knowing that they didn’t actually originate from 172.16.0.1. This is the basis of DNS amplification attacks; the attacker forges the victim’s IP address on DNS queries to legitimate name servers, and the servers respond by sending replies to the victim. This can be effective because some DNS queries are quite small compared to the replies, so with a moderate amount of bandwidth for queries an attacker can achieve a flood of larger DNS response packets.
In contrast, TCP communications don’t carry payload until each host has communicated successfully with the other. Nevertheless, TCP packets with forged source addresses are useful for some attacks, and these are similarly not traceable. But UDP attacks very commonly rely on forged source addresses and reflection/amplification, so knowing an attack uses UDP makes it likely that the true origin is not reliably traceable.
Very good post antibozo;
Thanks for the enlightenment. We were simply told in school, that UDP had no QOS and is sent without error checking.
Perhaps the bad guys watch this blog and like to hide insightful comments. I have wondered about some of the “thumbs down” votes.
You’re now on the theregister.co.uk 🙂
http://www.theregister.co.uk/2010/10/14/microsoft_confirms_ip_hijack/
Hmmm! Since the servers were Linux, I wonder what if anything Redmond was trying to convey with that? I mean; you got to wonder when it took them so long to shut it down?
So the moral of the story is that Microsoft only takes steps to plug security holes after the flaw is widely publicized.
Yeah, we already knew that.
I have two comments.
First, a message to “Dan”: NO POACHING! This is Brian’s site, and he’s your competitor, so advertising your web site on his web site is not very gentlemanly.
Second, to Mr. Smith, representing the Canadian International Pharmacy Association, it is both reasonable and proper for you to thank Brian, as I do, for turning the spotlight on this ongoing massive festering problem of the fake online “Canadian” pharmacies, and all of the massive amount of spams that go with those. But ya know, you could have also dropped a kind word or two about _me_, since I’m the one who found and outted the sons of bitches. But nevermind that, my REAL beef with you is much bigger and much more important. You guys CLAIM to be against this stuff, but has your association ever spent even a penny to actually DO anything to combat this stuff? And what about your counterparts to the south, in the United States? We have pharmacy associations here too ya know! And THEY have even more to lose that you Canadians do because of all of these crooked fake pharmacies. But how many dollars have either they or you actually spent to combat the problem? I mean seriously? I am NOT talking about the dollars you all spend to fly in corporate jets to Washington or Ottowa so that you can testify in front of some phoney baloney legislative hearing that allows everybody to get their pictures in the paper. I am asking you how many dollars either you or your US brethern have spent on guys like me… serious white-hat hackers who might actually be able to DO something about the problem, instead of just making press statements about it all of the time… eh? (In fact I doubt that either your association or your U.S. counterparts would even take my calls, even if I was offering my help FOR FREE! That’s the way bureaucracies are… insular.)
Sure sure sure. Whenever anybody from the PRESS is around, all you legitimate pharmacy people talk about how unhappy you are at these rogue operators on the Internet, but that’s easy and cheap to do. As my father used to say “Talk is cheap. Put your money where your mouth is.” Or as Tom Cruse once said “Show me the money!”
I know where all of the domains and all of the web servers and all of the name servers for all of these illegal fake Canadian pharmacy crooks are right now. You read that right. Not some of them, all of them. But neither you nor your cousins to the south even pick up the phone to call me. Now why is that? I guess that you guys don’t really care THAT much, and your public outrage is just a show you put on for the media.
I’m sorry, but this problem has already been festering for years and years now. The “Canadian Pharmacy” spammers are THE biggest sources of spam on the Internet, and have been for several years running. And frankly, the only reason that this goes on and on and on is because the people who have the most to lose… i.e. your membership and your counterparts to the south, are just too cheap and tightfisted to hire even a single actual serious Internet geek to even advise your association on the problem.
Sheesh, Ron, is there anyone you *don’t* pick fights with?
Dan has a free pass here. 🙂 Nice to see you, Dan. Thanks for the link love in your update.
The Canadian and Mexican pharmacies, legit or otherwise, who sell drugs to Americans exist because the pharmaceutical industry is allowed to charge the highest prices in the ‘developed’ world here in the US. If you don’t direct similar anger at Big Pharma or if you’re in their employ, turn the anger on yourself.
@Ron, if you have all the details, why not be a hero and form the “Canadian Pharmacy Spam Working Group” (CPSwag) and orchestrate a take-down? Surely you will be the toast of the town, whether the industry writes you a check or not, and folks will line up to pay you for your skills and Con appearances.
Ron: First off, my apologies for not thanking you for your work. It’s great work and it will make a difference for millions of Americans who need to find a safe alternative to the high prices of drugs in the U.S. without being lured by spam and internet bandits. So thanks.
Regarding the corporate jets – we don’t have any.
Will I take your calls? – you bet.
probably the same criminal scumbags who repeatedly hack others’ legit websites with impunity
and oh yeah @Ron : geesh, that’s more than harsh re Dan’s link. That’s called ‘link love’ and it’s not poaching FYI/fwiw.
huzzah.
“network hardware devices in a testing lab were compromised due to human error.” – Hardware with embeded Linux with simple ssh password and without network ACL to ssh?
Linux in their testing lab… it sure begs the question as to WHAT they were testing with those two servers …
Increasing Win7’s compatibility with Linux?
Improving Mono’s compliance with .NET?
Trying to develop malware that can infect Linux via emails?
and my favorite, but most unlikely ….
developing versions of the office and game software that run as binaries on Linux.
Everyone seems to be making a big fuss and assuming Microsoft is testing with Linux servers/systems/etc. All MS says is that a “device” running a Linux kernel was used. Heck, that describes about every DSL/Cable modem/router out there in the world. So what’s the big deal in that?
@aerobrent;
The big deal; is why did it take so long to shut it down, or correct it?
We would have to ask Ron, as he claims he set it up; but my take on it, is that Redmond seems to be taking an opportunity to make Linux look bad, even though it was their fault – obviously.
Call me paranoid; I’m just that kind of guy. ]:)
Microsoft, like every other corporation in america, uses devices with the Linux Kernel baked in. Appliances, though stirpped down, are as susseptible to attack as any other device with RAM. The discocerting problem with “appliances” is not what the operating system is, but how do we know if it’s compromised. What kind of anti-virus is running on your company’s Chaeckpoint Firewall appliance? What kind of AV software are you running on your phone? Boo.
Good post catfish;
I should think Checkpoint would be running ZoneAlarm anti-virus! 😀
You need to print that BOO! It is more scary that way! 😉
Hi Brian –
It was good to meet you at the PSM conference. I hope you had a chance to look at the study I gave you.
As you can imagine, we often hear from consumers who were burned by rogue online pharmacies, usually sites that have not been verified by PharmacyChecker.com or VIPPS.
Your reporting to expose rogue online pharmacies is a boon to public safety and health.
Thank you.
Gabriel Levitt
Vice President
PharmacyChecker.com
The real story here should be ” Microsoft Uses Linux on it’s computers!”
Fascinating and very well written account. Your blog is going from strength to strength… and the criminals keep providing top content!
Microsoft probably didn’t even know Linux was running on it. They said it was two misconfigured “network hardware” devices. Probably a couple of Linksys WRT54G’s running DD-WRT or something similar.
It goes to show that anyone can be “pwned” if you don’t take proper precautions. You can’t be careless even a little bit, or this kind of thing happens.
Thanks for the story, Brian.
Good analysis Sum Yung Gai;
The ole DD-WRT has been cracked; they probably didn’t update the firmware.
Cute pseudonym. 🙂
The existence of Microsoft is endangering to the internet. It’s like a vehicle manufacturer that sells cars without locks.
What? That makes no sense! Car analogies don’t translate to computers very well for starters! To completely lay blame at computer and/or OS manufacturers ignores the car/OS owner’s responsibility in operating said car in a safe manner. Problem is: computer users, like many car operators, are too stupid to know better about how to properly operate the device at hand! It’s a hard truth, but relevant! Like many auto drivers, there are many computer users who should NEVER be allowed behind the proverbial wheel/keyboard so to speak! 🙁
They only endanger others on the road, as well as, themselves! Years of experience in real life and in the computer field have taught me that empirically and undeniably!
What? If the collective genius that works for Microsoft can’t even secure their own systems, how can we expect that they sell anything but a shabby product to the unsuspecting mugs that use MS software every day of their lives?
The car analogy with no safety brakes is a good one.
“Problem is: computer users, like many car operators, are too stupid to know better about how to properly operate the device at hand!
That comment needs total ridicule – are you calling people with physical disabilities like limited movement or poor eyesight, “too stupid to know better” ?
The computer is a tool for them to use as best they can, it’s not their fault the computer is not adequately protected against external exploitation.
“It’s a hard truth, but relevant! Like many auto drivers, there are many computer users who should NEVER be allowed behind the proverbial wheel/keyboard so to speak!”
“They only endanger others on the road, as well as, themselves! Years of experience in real life and in the computer field have taught me that empirically and undeniably!”
Yet you don’t mention at all the endangerment to others on the road and to computer systems caused by arrogant bullies or ignorant know-it-alls, which are other classes of people who cause far more trouble than the ignorant, because they intentionally change things thinking they will cause no damage.
The other two comments :
“It’s like a vehicle manufacturer that sells cars without locks.”
Like the door locks on a Jeep ?
“The car analogy with no safety brakes is a good one.”
Safety brakes are mechanically integrated with the automobile. They are hardware. They require a conscious effort by the driver to use them, and they are used frequently in city driving.
Computer users expect the software to be the “brakes” on a computer, and when the software gets out of control, the only recourse is the kill the power by pulling the AC cord or removing the battery. (I have one computer whose power supply has a defective power switch. Go China !)
Grumble grumble. I wish I still had a VW Beetle, I would go push it uphill just so I could let it roll downhill to start it. Or push start it on level ground but there isn’t any where I live.
I get very cranked up when people try to compare automobiles to computers. I have to put my foot down on this because people who praise computers seem to let their fingers do the talking and the walking but don’t walk the talk about automobiles.
Brian,
While I very much enjoyed your article and will share it with my students, it seems a bit of a jump to assume that the compromised machine was running Linux. Just think of the position that put’s Microsoft in.
On one hand, MS would have to admit that they were using Linux (or Unix) in a production environment despite selling a competing product. On the other, they would have to admit that the machine in question was not running Linux (or Unix) but that a Windows server running at Microsoft was compromised. That’s a lose-lose situation.
It’s bad enough that they did not rectify the problem immediately. Imagine how the bad press will tarnish their otherwise stellar (..blrmf..blrmf..) reputation. Excuse me, I have to wretch now.
Paul
What’s with all the interest in Microsoft using anything Linux based? You don’t think other OS vendors (ex. Apple – Mac OS X, Red Hat – Linux) don’t have some flavor of Windows running somewhere in their facilities for whatever purpose (say in a test lab)? Seems a bit silly to me. Geez 😉
What with all the history of Linux being called a “cancer” by MS top brass, why would they even allow an embedded Linux OS on their network?
I did notice that human error was proffered as the underlying cause – again how are the public to view the fact that MS can’t secure a system which has all technical details relating to it freely available to download under an Open Source ethos?
In my earlier comment I said the real story was that Microsoft was running Linux, having run everything from DOS 2.0 to windows 7, I assumed that they were just looking for a stable system for their in house computers rather than the stuff they sell to the rest of us.
I believe that’s a rather superfluous reason. I’ve been running Windows systems for 13+ years now and they have always been stable and reliable. I don’t experience crashes or system problems. The only time I need to reboot is when patching (if a patch requires it) or when periodic system maintenance (ex. disk check) requires it. I know others who experience the same things. More often than not, the problems are attributable to other reasons than the operating system platform. While the car analogy is poor at best, I still like the comparison that computers like cars need maintenance and attention to their operation in order to operate at their best and to avoid operational issues. 🙂
Besides, back to the point at hand, while we don’t the exact details, the Linux systems that were compromised have been reported as “hardware” devices, not desktop/server computers. 🙂
So, who is routing their traffic now that Microsoft has caught on?
Domain: zlaepezpa.com
(registered with stolen identity information in June 2010
That identity theft victim confirms she didn’t register the site. She also reports her credit card company detected fraudulent information and shut down her card number about that time.
Yet the registrar,
DATTATEC.COM BELONGING TO VERONICA P. IRAZOQUI
doesn’t seem to consider a denied payment (and possibly a chargeback) to be a reason to suspend a domain registration — it’s still alive.)
Nameserver: ns1.af7.ru
192.138.193.142
= University of Houston Information Technology Computing & Telecommunication Services
(Hope nobody at UH is laughing too hard about Microsoft’s pwned server.)
The other listed nameserver
ns2.greencacti.com [0.0.0.0] is blackholed and on Client Hold (Distribute IT Pty is the registrar that took action)
None of the image servers referenced in the site source code are cooperating at present:
61.133.218.206 Road & Bridge Engineering Co., Ltd. in Ningxia, China
203.255.181.238 Scientific Computing Laboratory, Department of Mathematics, at Ewha Women’s University in Korea
61.166.124.12 (dynamic IP?)
60.191.123.107 Communication Technology Co., Ltd. Hangzhou Wah h3c.cn
66.205.203.150 AllWest.net
Most of those were compromised long enough to have listings on Spamhaus, yet all have stopped working at once. Apparently it was sudden enough that the spammer hasn’t found new ones to substitute (and they do substitute them pretty regularly). They also haven’t switched to their old standby, an IP address in Turkey they sometimes use instead of using five compromised servers for images.
I’ve reported plenty of the compromised servers they’ve used in the past, and I know other people who have as well. It’s unusual to get any response to an email at all, let alone to get the server disinfected (Most admins look at their directories and are reassured because they don’t see anything unusual. The trojan — with a file name that sounds like a legitimate Unix file — relays requests to a remote server, so the images aren’t actually on the server whose IP is in the source code of the website. The trojan also blocks queries from those admins’ IPs, so if you give them a link to an image, they won’t see anything.)
So I am encouraged that perhaps someone with much more clout than me is pursuing these trojan infections now.
ADD: I just checked with hidemyass.com and was able to view some images. I don’t know if that means they have cached them or whether the sites are allowing me to view the website but blocking me from the images, which would be something I haven’t seen them do before.
First, in response to Brian: You’re 100% right. No there’s NOBODY I won’t get in a spat with if I think they are messing up. (Obviously, I didn’t realize that Dan’s posting would be just fine with you, so now I humbly apologize to both you and Dan.)
As regards to me letting loose with both gnus on the spokesmodel for the Canadian Legit Pharmacy Assoc., I don’t apologize for that at all. I’m just really really tired of _every_ type of PR bull pucky, no matter who is slinging it.
In response to the guy who suggested that _I_ alone might be able to take down all of these fake Canadian Pharmacies, well, sorry, but I can’t. I may know where they all are, but it is going to take a lawyer or two, and maybe (yikes!) some high-level international cooperation to make that happens, and I just don’t have either the money or the political juice for that. My point was that these US & Canadian Pharmacy Associations probably _do_ have both the cash and the juice to get the job done, but instead they sit on their hands and just expect everybody ELSE to do the job for them.
In response to the guy who said that US drug prices are being kept artificially high, yes, of course, you are absolutely right. We in the US are getting massively ripped off by big pharma and by their paid lackeys in congress. But the solution to THAT problems is NOT to simply let a bunch of Russian and/or Turkish criminals circumvent our laws just so that they can trans-ship to the US (with the aid & abbetance of Visa, MasterCard, UPS and FedEx) a bunch of crap of dubious potency… including even CANCER and CARDIAC drugs… that’s been manufactured in the same Indian factory that’s also used to manufacture fertilizer out of rat turds. I mean seriously… Have you been reading the news lately about the Commonwealth Games? It’s fine by me if the Indian government wants to allow their manufacturers to sell their crap to starving pregnant mothers in Calcutta. That’s their business. But when they start using Russian & Turkish criminal shills to ship it here, then I take offense.
In response to the guy who wondered if that MS machine (or two) was/were really running Linux, yes, I confirmed it, unambiguously. No doubt whatsoever. If you e-mail me privately, I’ll send you the proof.
In response to AlphaCentauri, I really would be very interested to know how you confirmed that a stolen credit card was involved. Please email me. As regards to one of the two name servers for that domain you mentioned being ns1.af7.ru and that name being equated to a machine at the University of Houston, yes, I found that one already weeks ago, and it got either shut down or cleaned before both Dan’s and Brian’s stories ran. (But yes, they were boneheads too, as were the admins at CUNY, which also had one of these 0wned Linux boxes for awhile, together with a fair number of other folks… mostly just dumb individuals with end-luser broadband lines.)
Last word: AlphaCentauri, don’t be too “encouraged”. As I’ve tried to stress, it’s still just volunteers, like me, trying to work on this stuff. None of the business entities with actual serious money and/or political juice seem to be doing a damn thing about any of this, except having much publicized meetings about it and issuing press statements. (I _do_ need to give well-earned credit to the FBI however for their recent take down of a fairly large carder ring. *That* was impressive.)
P.S. To Brian: Could you PLEASE arrange for there to be a date/time at the top of each of your stories. That’s important for researchers who may find your story via Google six months from now, and then not have any idea when it was from (which is important, forensically). And umm, not to whine TOO much, but how about a “print” button on these things, so I can put a hardcopy in my scrapbook and send one to my Aunt Mildred in Poughkeepsie, who ain’t got a computer. Lastly, regarding the date/time stamps on the comments, may I safely assume that that’s UTC?
Ron, you’re new around here so I’m going to cut you some slack. : )
Seriously, though, the date is at the top of every article on the homepage. Go to http://www.krebsonsecurity.com and you’ll see it at the top left of every post.
If you’re viewing the version of the story that includes all of the comments, the day, date, and exact timestamp are at the bottom of every article text. You might have to actually look for it, but it’s there. For example, if you look just above where the comments section starts on this blog post, you’ll see this part:
This entry was posted on Wednesday, October 13th, 2010 at 5:04 pm and is filed under A Little Sunshine, Web Fraud 2.0. You can follow any comments to this entry through the RSS 2.0 feed.You can skip to the end and leave a comment. Pinging is currently not allowed.
I’m located on the East Coast, Ron, so all timestamps — both on comments and on posts themselves — are in Eastern Time (UTC – 4 EDT, UTC – 5 EST)
Brian,
The timestamps are governed not by where you are located physically, but by what timezone the server or blog software is configured in. A lot of us use UTC regardless of the physical location of the system. This makes it easier to correlate entries in logs, since no timezone conversion is needed, and it ensures that textual timestamps increase monotonically–systems configured in daylight saving time have jumps in the timestamp record, and it’s possible to have ambiguous timestamps when daylight time is enabled. I think it would be better if the timezone were indicated on the blog timestamps. With no timezone indication, UTC is the safest timezone to assume for otherwise undocumented timestamps, and that’s not what the blog is using so it’s potentially misleading.
Also, I agree with Ron that it would be nicer if the timestamp on individual blog entries appeared close to the title; it’s pretty hard to spot as it is.
Ron, you are correct at thinking that Indians are pumping cheap medicines. But trust me, the government has no hand in this. Those idiots are too clueless to even realise the goldmine that they are sitting on. And yes the Commonwealth Games have shown the India works _despite_ its government.
@Brian, sorry for this off topic rant.
@Ron, I checked a traversal, and I checked in a browser with ShowIP. Both confirmed that ns1.af7.ru was still at 192.138.193.142 this evening.
To AlphaCenturi: Yes, the name server address is still pointing to an IP belonging to the University of Houston _however_ that only means that the spammers are slow to update their own name server glue records.
I assure you that the machine in question is no longer answering DNS queries for the spammers.
@aerobrent, most cable modems are rather dumb devices. You almost never have a combo cable modem plus router – they are usually separate. Lone cable modems (no router) are definitely not built using Linux. Ditto with most of the combination DSL modems/routers, and home routers. But there are some home routers built using Linux. Believe it or not one DSL modem/router built using Linux used by many European telcos allowed configuration from the WAN side just like it was the LAN side! Hackers used them for spamming until people updated the firmware and set the enable password to something other than the default. With something like that there was no security. It is possible Microsoft had something like that and the person using it had no idea how insecure the thing was even if they were just using it for some sort of test. So everybody, update the firmware on your home router, change the admin password on it, and beef up the security settings on it. I imagine 95% of home routers are using the defaults. This shows what can happen if you do that. Some tips on how to configure your home routers so they are safer:
http://www.SecureMecca.com/public/HomeRouters/
I am not saying this is what Microsoft had but it sounds an awful lot like one of those European telco DSL modem / routers. 99% of the people using them did nothing to tighten up the security until after the hackers had compromised thousands of them. But really, unlimited setting changes on the router from the WAN side with no limits on where you could come from?
I’ve got a D-Link Wireless Router, Model WBP-1310, purchased less than 3 years ago.
I was surprised to find it had WAN access, and there was automatically enabled. I did not attempt to figure out if having the default password also made the router easily accessible from the WAN side – or any password, why give the hackers a target to attempt access constantly ? They already ping everything. I disabled the WAN side access.
Hey, I just appreciate your writing style 🙂 Sorry if that’s a lame comment, I didn’t find a “like” button 🙁