 Spam trackers are seeing a fairly dramatic drop in junk e-mail sent over the past few days, specifically spam relayed by one of the world’s largest spam botnets – although security experts disagree on exactly which botnet may be throttling back or experiencing problems.
Spam trackers are seeing a fairly dramatic drop in junk e-mail sent over the past few days, specifically spam relayed by one of the world’s largest spam botnets – although security experts disagree on exactly which botnet may be throttling back or experiencing problems.
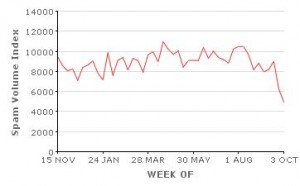
According to M86 Security Labs, the volume of spam has dipped quite a bit, approximately 40 percent since the beginning of the month by the looks of the graphic the company publishes on its site (pictured at right).
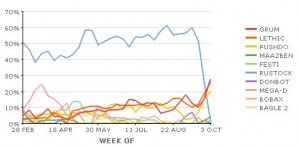
M86 says the decrease in spam is due to a rapid drop in activity from the Rustock botnet (see graphic below left), a collection of spam-spewing zombie PCs that experts say is responsible for relaying about 40 percent of all junk e-mail on any given day.
 The decline in spam volume comes at about the same time that the world’s largest spam affiliate program — spamit.com — said it would stop paying affiliates to promote its online pharmacy Web sites — on Oct. 1.
The decline in spam volume comes at about the same time that the world’s largest spam affiliate program — spamit.com — said it would stop paying affiliates to promote its online pharmacy Web sites — on Oct. 1.
Bradley Anstis, vice president of technical strategy for M86, said the most likely explanation is that the person(s) operating Rustock rented the botnet to a number of spamit.com affiliates, and many of those affiliates have not yet switched over to another pharmacy affiliate program.
“To me, that’s the most logical explanation,” Anstis said. “The timing certainly hooks up well, because we started seeing this decline right around the first of October.”
Several other spam watchers said they also were seeing the decline in junk e-mail, although they attribute it differently. Dmitri Alperovitch, vice president of threat research at McAfee, said his company’s sensors were attributing the drop in spam to a decline in activity from the Pushdo botnet.
Alperovitch said McAfee is seeing a 45 percent drop in the number of Pushdo-infected PCs sending spam spam since Oct. 1, and 27 percent decrease in overall spam levels since that same date.
The dispute over which botnet may be responsible for the missing spam is interesting because it dovetails with a discussion I had last month with a Russian source who has close contacts to many key players in the cybercrime underground. I had asked this source if he could connect me to the author of Rustock, and while my source couldn’t secure me an interview, he related the following tidbit from their conversation: He said the guy was amused because M86 was consistently conflating Pushdo and Rustock infections — effectively giving his Rustock botnet credit for spam that was being sent by Pushdo.
M86’s Anstis said his team would be checking their methodologies to make sure they weren’t misclassifying the spam sources.
“As security vendors, we try to work out which ones are most active and which ones we should concentrate on,” Anstis said. “In the end, the only person who is going to know who is sending what is the botnet authors.”
Update, Oct. 6, 5:13 p.m. ET: M86 said they re-checked their information after my story ran. Here was their response:
“We have also seen a drop since Sunday in Pushdo but not at the level of the Rustock drop. We are sure we have these labeled correctly, for example we saw the drop in just Pushdo last month when some of its controllers were taken offline. We still have no Rustock spam in our traps and since these traps come from many different sources we find it hard to believe that just we were blacklisted. We have double checked all our settings and algorithms, we were the first vendor to start reporting on spam bot traffic and we are positive that we have these labeled correctly.”




I don’t care about McAffe’s opinion or their products.
My spam dropped briefly, but the mailers have found new affiliate programs and are making up for lost time. I received nearly identical spam from the following IP addresses in the last hour, all to the same email address, all for medpillsom16.com, medpillsom17.com, medpillsom18.com and medpillsom19.com. The Composite Blocklist identifies some as part of the Grum botnet, but most aren’t associated with any botnet yet:
64.107.79.98
77.126.48.252
85.152.238.150
87.119.226.62
186.112.32.43
186.207.104.132
187.4.241.236
189.58.22.161
190.120.97.234
190.161.127.196
190.206.127.244
190.29.129.107
190.40.68.134
190.97.90.214
194.209.131.192
200.111.195.94
200.125.105.148
201.216.41.36
212.225.142.179
Nice work Alpha– Brian’s second graph from M86 seems to back up the uptick in Grum’s spam.
Great article Brian! It’s great to see more than one side of the story and always interesting when they don’t match up.
I came across another article this afternoon which actually mentions this post… I think you may have been slightly misquoted – says you suggest M86 is misclassifying… I may have read it wrong, but I thought you said that was McAfree – I missed where you agreed with that theory. Which leads to the question… which one do you think credit goes to?
http://threatpost.com/en_us/blogs/spam-volume-way-downbut-why-100510
Please get rid of that “Welcome Googler” banner at the top of your pages. You have a great blog, and I don’t know why but that stupid banner drives me nuts. Most likely because it is wrong and pumps out that message even if it is wrong. I come here from RSS feed, not google.
(Sorry to be crabby but I see that and go nuts. At least maybe the web designer could fix it so it is accurate, then I wouldn’t see it every time I come here).
Great blog. The Best (except that damn “Welcome Googler”).
Have you ever Googled “Welcome Googler”? Interesting results. Why just look what it did to this guy: http://welcome-googler.posterous.com/
It highly depends on which spammers’ lists you’re on. My honeypot account is getting the same ~100-200 per day it’s been getting for years. In fact, if anything, it has increased slightly in the past few months.
excellent journalism! its a good blow to other emerging spammers as well.
Latest Tues update of Microsoft caused my system to freeze up. I restored and all worked again. Re-updated and same thing happened!
Restored again. Now am ambivalent about the updates.
Do you know which patch caused the problem?
Sorry, I did not have time to install them one by one to detect the culprit.