Global spam volumes have fallen precipitously in the past two months, thanks largely to the cessation of junk e-mail from Rustock – until recently the world’s most active spam botnet. But experts say the hackers behind Rustock have since shifted the botnet’s resources toward other money-making activities, such as installing spyware and adware.
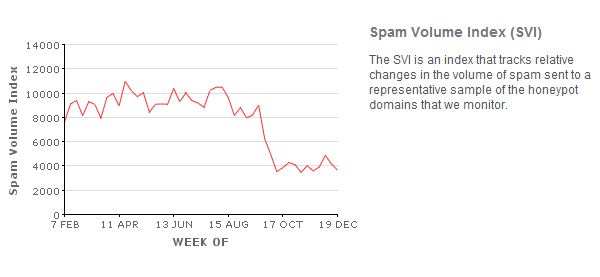
The decline in spam began in early October, shortly after the closure of Spamit, a Russian affiliate program that paid junk e-mail purveyors to promote Canadian Pharmacy brand pill sites. The graphic below, from M86 Security Labs, shows a sharp drop in overall spam levels from October through the end of 2010.
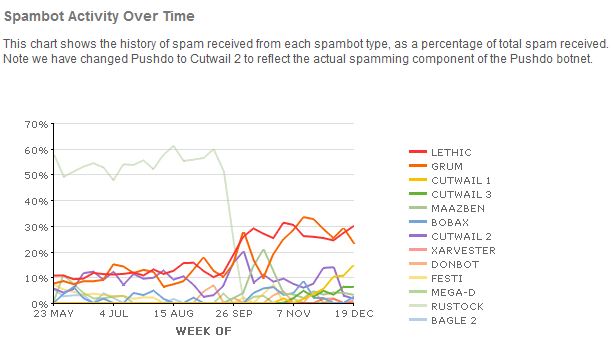
 Another graphic from M86 shows that spam from Rustock positively tanked after Spamit’s closure. Rustock is indicated by the pale blue line near the top of the graphic.
Another graphic from M86 shows that spam from Rustock positively tanked after Spamit’s closure. Rustock is indicated by the pale blue line near the top of the graphic.
 Prior to the Spamit closure, Rustock was responsible for sending a huge percentage of all spam worldwide, M86 reported. But since Christmas Day, the Rustock botnet has basically disappeared, as the amount of junk messages from it has fallen below 0.5 percent of all spam, according to researchers at Symantec‘s anti-spam unit MessageLabs.
Prior to the Spamit closure, Rustock was responsible for sending a huge percentage of all spam worldwide, M86 reported. But since Christmas Day, the Rustock botnet has basically disappeared, as the amount of junk messages from it has fallen below 0.5 percent of all spam, according to researchers at Symantec‘s anti-spam unit MessageLabs.
Turns out, other spam botnets also have been MIA since Christmas: “The Lethic botnet has been quiet since December 28, and the Xarvester botnet went silent on December 31,” writes Symantec’s Eric Park.
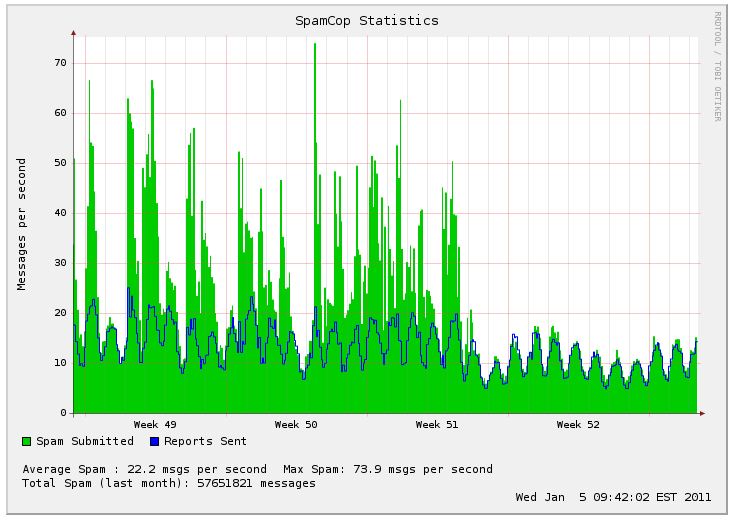
Statistics from SpamCop, shown in the graphic below, also illustrate a substantial drop in spam volumes, particularly during the final week of 2010.
On Tuesday, I interviewed Phil Hay, senior threat analyst with M86, about the possible reasons for the decline. Hay said individual bots infected with the Rustock malware were still phoning home to the Rustock control servers, which appeared to be responding with instructions to download files. But he said the files didn’t appear to have anything to do with spam.
I asked Hay whether it was possible that Rustock was simply being used to install spyware and adware for affiliate programs that pay people to generate installations. As I reported in a Washington Post Magazine story from 2006, this is a very reliable way for botnet owners to make money. Hay said he’d check into it and get back to me.
Today, I received the following response:
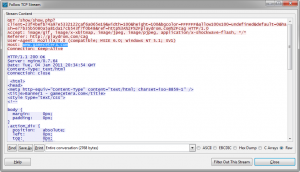 “Hello Brian. After talking to you today, we had another look at Rustock. While it was still quiet on the spam front, we did notice the malware performing what looks to be a pay-per-click fraud. When we doubled checked our older Rustock trace files from December, we also noticed the same sort of traffic. We missed it the first time because the sheer volume of spam-related traffic overshadowed the pay-per-click traffic. So Rustock was spamming and ‘clicking’ concurrently, but now is just clicking. The attached image is from Rustock traffic today. It shows a GET request made to www.gamecetera.com with a referrer set to playdrom.com. Other sites we saw Rustock making requests to today include:
“Hello Brian. After talking to you today, we had another look at Rustock. While it was still quiet on the spam front, we did notice the malware performing what looks to be a pay-per-click fraud. When we doubled checked our older Rustock trace files from December, we also noticed the same sort of traffic. We missed it the first time because the sheer volume of spam-related traffic overshadowed the pay-per-click traffic. So Rustock was spamming and ‘clicking’ concurrently, but now is just clicking. The attached image is from Rustock traffic today. It shows a GET request made to www.gamecetera.com with a referrer set to playdrom.com. Other sites we saw Rustock making requests to today include:
Funklicks.com
Bannerflux.com
Gamesbannernet.com
Mochimedia.com
GirlGamesBanner.com
Update, Jan. 10, 6:13 p.m. ET: As several researchers have noted, Rustock seems to have gone back to its old pharma spamming ways overnight.





Great post. It will be interesting to see if this is an ‘industry’ wide paradigm shift, or if some other ‘industrious’ folk step in to fill the ‘void’ left by Rustock.
Has there been a pattern of diminishing returns fr/ the ‘classic’ spam model?
It’s too soon to tell. I think that as long as there is demand, someone will step in to provide the supply.
Right now, one of the oldest and largest spam affiliate programs is in a period of transition. I would be surprised if there wasn’t a new affiliate program on the block in a few months, along with a resumption in spam volumes.
For me first comes in mind that someone made some (re-)calculations, and spam got numbers that indicated it ate other methods’ profits. Thus the shared report in certain forum led to that some botnet owners retought their strategy.
Just a thought…
Quite interesting thought. As always, follow the money. They’re optimizing the use of assets, acting almost like a normal corporation. I wonder when the taxman is going to show up on the scene. 🙂 Or maybe he’s been paid off – baksheesh is always popular.
> Rustock is indicated by the pale blue line near the top of the graphic.
Maybe my eyes are going, but it didn’t look blue to me :(. From the key, it looks like Bagle 2 would be pale blue.
Bagle 2 is pale blue.
Rustock is *very* pale blue.
Ah. So how would you have described it?
On my screen, it somehow looks like a pale green-brown instead, closer to Mega-D above it than Bagle2 below it.
I would describe it as:
“The very pale blue-grey line, clearly distinguishable from the other spambots, that starts at the top-left of the graph on May 23 at approximately 58%”
I would just say “the one that fell off the damn cliff”. Color is irrelevant when looking at Rustock in that chart.
Probably greyish brown. But couldn’t you have recolored it?
I’ve done a quick survey and other suggestions included:
* Rust
* Silver
* Pale Green-Grey
* Light Olive (as opposed to Dark Olive for Mega-D)
I only got one person who suggested one of the above “with a faint touch of blue”
one person suggests: though if you are going to make it the primary topic of your article it should be red. or some other easy to id primary color
another offers: as opposed to one which looks 15 different shades depending on my LCD angle
Ahhh…TN panels in consumer grade lcd’s are wonderful with color accuracy and viewing angles aren’t they
Always funny when graphic designers deliver their work and their clients call back absolutely pissy about “getting the corporate colors wrong” bwahahaha
IPS or even VA based panels will do far better (in most cases if you had an early lcd monitor it was VA…pull it out and check out how much better the colors are)
Having been dragged to home depot to look at paint samples more times then my tortured eyes can recall, I believe I can conclusively say with authority that color is “Ocean Mist Blue” or perhaps “Whale Breath Blue”.
Either way I thought the context of the article made it obvious 🙂
Looking at the stats from NiX Spam DNSBL it shows quite the same. But only with a slight decrease since October and a magic drop at Christmas.
http://www.dnsbl.manitu.net/stats.php?language=en
I started to get excited – spam to my domain is down by almost 2/3 – till I had a look at the Messagelabs Intelligence report for November: http://www.messagelabs.com/mlireport/MLI_2010_11_November_FINAL.pdf
The top graph in the PDF shows spam levels at Messagelabs since 2005.. We are just off an all-time peak – spam is still running at 84% of all email routed through Messagelabs.
Hi Brian
Do you think that other/new cyber criminals will commence internet banking thefts again after the massive recent arrests?
If so, what sort of time frame do you think would be likely?
Can businesses prone to that type of theft now relax relative to that type theft?
@Bigkev — The commercial account takeovers haven’t stopped, although they may have slacked a bit.
Thanks for the info Brian
Those type thefts have also been occurring over the past few years in Australia according to NSW state police cyber crime department sources but are essentally unreported in the press or elsewhere
Do you expect any reporting to recommence in US of thefts there or in any other jurisdictions?
Brian,
As always…very informative. On this transition, I’m trying to get my wee brain around the particulars.
Can you or any of your big brained league of followers unpack this for me in laymens terms?
“…experts say the hackers behind Rustock have since shifted the botnet’s resources toward other money-making activities, such as installing spyware and adware.”
Or, point me to a non-malware-laden area to learn more about this activity and how it is perpetuated.
Thanks in advance for any guidance.
Mark
Great question Mark
I can’t help…..hope someone can