The unceasing barrage of targeted email attacks that leverage zero-day software flaws to steal sensitive information from businesses and the U.S. government often are described as being ultra-sophisticated, almost ninja-like in stealth and anonymity. But according to expert analysis of several recent zero-day attacks – including the much publicized break-in at security giant RSA — the Chinese developers of those attack tools left clues aplenty about their identities and locations, with one apparent contender even Tweeting about having newly discovered a vulnerability days in advance of its use in the wild.
Zero-day threats are attacks which exploit security vulnerabilities that a software vendor learns about at the same time as the general public does; The vendor has “zero days” to fix the flaw before it gets exploited. RSA and others have labeled recent zero-day attacks as the epitome of the so-called “advanced persistent threat” (APT), a controversial term describing the daily onslaught of digital assaults launched by attackers who are considered highly-skilled, determined and possessed of a long-term perspective on their mission. Because these attacks often result in the theft of sensitive and proprietary information from the government and private industry, the details usually are shrouded in secrecy when law enforcement and national security investigators swoop in.
Open source information available about the tools used in recent attacks labeled APT indicates that some of the actors involved are doing little to cover their tracks: Not only are they potentially identifiable, they don’t seem particularly concerned about suffering any consequences from their actions.
Bragging rights may play a part in the attackers’ lack of duplicity. On Apr. 11, 2011, security experts began publishing information about a new zero-day attack that exploited a previously unknown vulnerability in Adobe‘s Flash Player software, a browser plug-in installed in 96 percent of the world’s Microsoft Windows PCs . The exploit code was hidden inside a Microsoft Word document titled “Disentangling Industrial Policy and Competition Policy.doc,” and reportedly was emailed to an unknown number of U.S. government employees and contractors.
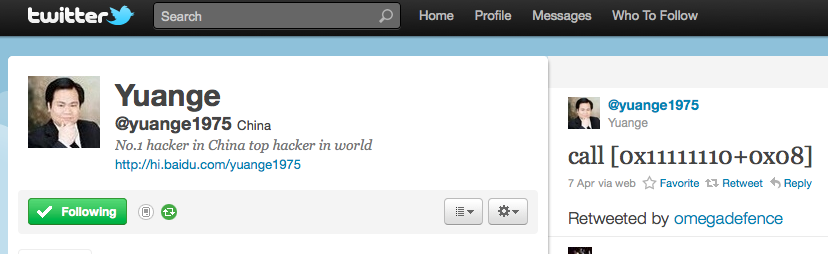
Four days earlier, on Apr. 7, an individual on Twitter calling himself “Yuange” and adopting the humble motto “No. 1 hacker in China top hacker in the world,” tweeted a small snippet of exploit code, apparently to signal that he had advance knowledge of the attack:
“call [0x1111110+0x08].”
It wasn’t long before malware researchers were extracting that exact string from the innards of a Flash exploit that was landing in email inboxes around the globe.
Tweeting a key snippet of code hidden in a zero-day exploit in advance of its public release may seem like the hacker equivalent of Babe Ruth pointing to the cheap seats right before nailing a home run. But investigators say the Chinese Internet address used to download the malicious files in the early hours of the April Flash zero-day attacks — 123.123.123.123 — was in some ways bolder than most because that address would appear highly unusual and memorable to any reasonably vigilant network administrator.
This wasn’t the first time Yuange had bragged about advance knowledge of impending zero-day attacks. On Oct. 27, 2010, he boasted of authoring a zero-day exploit targeting a previously unknown vulnerability in Mozilla’s Firefox Web browser:
“Wrote the firefox 0day. You may see “for(inx=0’inx<0x8964;inx++). You should know why 0x8964 here.”
That same day, experts discovered that the Web site for the Nobel Peace Prize was serving up malicious software that exploited a new vulnerability in Firefox. An analysis of the attack code published by a member of Mozilla’s security team revealed the exact code snippet Yuange had tweeted.
On February 28, 2011, Yuange taunted on Twitter that new zero-day traps were being set:
“ready? new flash 0day is on the way.”
On Mar. 14, Adobe acknowledged that a new Flash flaw was being exploited via a booby-trapped Flash component tucked inside of Microsoft Excel files. Three days after that, EMC’s security division RSA dropped a bombshell: Secret files related to its widely used SecurID authentication tokens had been stolen in “an extremely sophisticated cyber attack.” A follow-up blog post from RSA’s Uri River two weeks later stated that the break-in was precipitated by the zero-day Adobe had warned about on Mar. 14, and that the lure used in the attack on RSA was an Excel file named “2011 Recruitment Plan.”
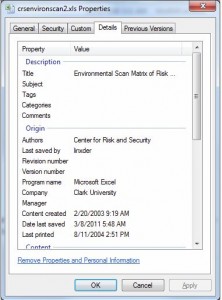
On Mar. 16, just one day before RSA disclosed the breach, researchers at Milpitas, Calif. based security firm FireEye released their analysis of an exploit that used the same zero-day Flash flaw. The specific attack FireEye analyzed included a different lure than the one used against RSA: An Excel file titled “Environmental Scan Matrix of Risk and Security Organizations.” When FireEye investigators dug deeper into the Excel file, they found metadata indicating the file had last been saved by a user named “Linxder.”
“Who is this linxder?” FireEye’s Atif Mushtaq asked in a Mar. 16 posting to the company’s blog. “My colleague Darien pointed me to few links on google that tells us that a guy named ‘linxder’ is a known chinese threat actor. This guy is an old-school hacker that has a fairly expansive social network. If one searches linxder’s baidu profile, we can see that he talks a ton about weaponizing flash containers in other file formats, which is exactly what happens in this attack.”
The Linxder profile linked in FireEye’s write-up has since been wiped clean of more than two years worth of blog posts, but Google’s cache still contains some of his older blog entries from 2009, including one that indicates Linxder and Yuange were acquaintances.
WILL THE REAL YUANGE PLEASE COME FORWARD?
The Yuange1975 character on Twitter may be very well be a composite of several different individuals, said Andre M. DiMino, a cybersecurity expert and former director of Shadowserver.org, a group that tracks cybercrime activity.
“At first, there were a lot of people really intrigued by this guy,” DiMino said. “But it looks pretty likely that there are a group of folks who are tweeting to this account.”
Yuange’s Twitter profile lists a blog account on Chinese Internet provider Baidu.com by the same name, but the Yuange at that blog appears to be an old school hacker from Chinese Internet security firm NSFocus who claims to have had nothing to do with the RSA exploit. He also complains that the “Yuange1975” on Twitter is impersonating him.
Neither the Twitter Yuange nor the Baidu Yuange responded to requests for interviews. Frank Ip, vice president of North America operations for NSFocus, said the Baidu Yuange is a man named Yuan Renguang, one of 12 co-founders of NSFocus, and that Renguang left the company in 2005 to start his own data loss prevention firm. Ip said Renguang was being impersonated, and that he is quite widely respected in China.
“Not only is this [Twitter] impersonator using his name, but he stole [Renguang’s] picture,” Ip said, adding that the real Yuange doesn’t speak English and has never published anything in English, wheres the Twitter Yuange tweets only in English.
Earlier this month, Reuters ran a story based on secret U.S. State Department diplomatic cables released by Wikileaks. The piece chronicled the theft of terabytes of data from U.S. firms and the government over the past several years, and attributed the attacks to specialized electronic espionage units within the Chinese People’s Liberation Army (PLA). But that piece didn’t address the legions of civilian hackers who conduct the same classes of attacks for patriotic reasons, for bragging rights, or simply to earn money.
Scott Henderson, a military analyst at the U.S. Army’s Foreign Military Studies Office in Ft. Leavenworth, Kans., wrote extensively about this phenomenon in his eBook titled “The Dark Visitor” (Henderson co-authors a blog on this subject). Henderson said it may be that the RSA attack was launched by members of what’s known as the Red Hacker Alliance, a Chinese nationalist hacker network made up of many independent Web sites directly linked to one another, in which individual sites educate their members on computer attack and intrusion techniques. Henderson said the Red Hacker Alliance is characterized by its members launching coordinated attacks against foreign governments and entities to protect actual and perceived injustices done to their nation, but that monetary motivations increasingly are becoming as important as patriotic passion.
“It’s interesting because so many of these guys are doing this stuff out in the open, and you have to ask why, and what’s the risk-to-reward ratio for these guys, and does [the Chinese government] use them as a political hammer or as a quasi-intelligence gathering network that is tacitly approved by Beijing, and I think you’d have to say ‘yes’ to all of those,” Henderson said in a phone interview. “I don’t think there has been enough pressure on Beijing to change that, because these guys are very much out in the open and talking about what they’re doing, and in some cases almost crowd-sourcing their work.”
Henderson said the most damaging common aspect of all the attacks is that the assailants never seem to quit. “We hear about these really sophisticated attacks these guys are doing, but really it always boils down to social engineering,” Henderson said. “They send out enough emails to enough recipients at Company X that someone eventually clicks on these things and suddenly the attacker gets access to the target’s system. There are so many of these groups and this activity is going on so continuously that the challenge is trying get a handle on what exactly we should be looking at. I always wonder, if this is the stuff we’re seeing, where are the really good guys, the ones you don’t see? If the successful attacks are so blatant and open, and these guys probably aren’t the crème de la crème, where are the really good guys?”
This is the first in a series of planned stories on the RSA attack and the menace from advanced persistent threats.





We need other terminology than “really good guys” to describe “expert cyber criminals.”
“where are the really good guys?” In gainful employment.
I don’t relly think that the social engineering tricks are anything new, hackers have been using these since way back when…( paging Kevin Mitnick )..as for the zero days, there are those that find them and report them…those that are using them for un-ethical purposes either have bravado or financial gain in mind….the depth that attcks have been coming against goverment agencies and e-commerce aren’t new either but I believe are becoming more prevelant as the media is reporting it more and getting the word out. Ex cyber secuity czar Richard Clarke warned of the scenario that the goverment needed to be more proactive on the threats against goverment facilities and networks and companies needed to do a better job of making their software more secure instead of rushing products to market with vulnerabilities…Clarke even said that it would be nice to get ahead of the problem before e have to find out after the fact… and his warnings pretty much went on deaf ears…China has greatly upped their cyber espionage IMO and will continue to do so… as for what hackers are doing with some of this info, I don’t think they are sitting on it, I am sure there is some finacial reward to do so…the guys using spe eye and Zeus seem to have a fairly clear aim..money…and the seem to be really the East block countries that are geared toward that end. China on the orther hand seems more inclined to get information that they want, need and can use to further their own means tactically for military and technology reasons that are beneficial to them for future endeavours… and the way that China encourages their own citizens hacktivism and monitors their citizens internet activities, whats makes anyone think that they aren’t getting this same information indirectly… are other naations involved in cyber espionage… sure they are , but Chine seem to be prevelant and proficent in it’s activities…
CHINA STRONG!
When I asked someone at Mandiant if compromised companies/organizations had ever attempted to prosecute those responsible in China, he quickly and simply said; No. Because these attackers are government supported or knowingly ignored, they have absolutely no fear of prosecution. I think that even if those responsible for some of these attacks came forward with their identities, there wouldn’t be much that the US could do.
Because they have absolutely no fear of prosecution, these types of attacks will continue to grow at an exponential rate in number and sophistication. I firmly believe that as soon as one group of Chinese hackers is brought to justice and incarcerated, we will see an immediate and dramatic drop in cyber attacks targeting classified/confidential information.
Blacklist any connections to or from my network to China: check.
Good luck if you work in any research environment.
Or if you work with suppliers or clients in China.
Did that years ago – my router blocks anything from a chinese domain. Of course that isn’t going to stop them going via servers in other countries, but it’s a start.
Yes, while you are blocking all the “scary” chinese IPs, they are coming in via Abe’s trucking in Pensacola Florida. They attack the victim from the victims own countries IT assets.
Great stuff, Brian. I’m looking forward to the next installments.
Why announce a zero day exploit in advance? To ramp up pressure as part of an extortion demand, I would suspect.
Or, as “evidence” to later take credit for exploits done using said zero day.
An extortion demand? It seems unlikely – CVE-2011-0611 got dropped on people like capitol hill staffers, think tank fellows and politicos at global consultancies.
It’s hard not to interpret these things as taunts, gloating about their apparent immunity from repercussions and an attempt to bring shame on the US infosec apparatus. The previous Flash 0-day seemingly by the same author used DNS entries that included http://www.usgoodluck .com, obama.servehttp.com, and prc.dynamiclink.ddns.us -> http://krebsonsecurity.com/2011/03/domains-used-in-rsa-attack-taunted-u-s/
Maybe it’s time to relocate one of those find, fix & finish teams a bit farther east.
Great piece, Brian. Look forward to the rest.
It seems like tech support people of these high profile companies don’t follow simple rule “do not open attachments from unknown persons”. If they have to in some cases, they can adjust some settings like disabling flash content or java. But these tech support people are cyber experts and poorly paid. Criminals know this and if these cyber criminals can social engineer a highly skilled admin at hbgary, one can how successful they are when dealing with poor tech support people.
It really highlights the problems inherent in including programming capabilities in files that users think of as simple documents. That’s a nice idea when everyone is nice and trustworthy, but a horrible idea when some are not.
At this stage it seems unlikely that the software vendors will eliminate these features so perhaps what’s needed is a standard set of reading software for use with email that either disallows programming actions or severely limits them (in the case of spreadsheets). I’m not sure how feasible this would be or how it would be received by users.
When you work in a networked environment, it only takes one clerk to try to open a suspicious attachment, or violate company security rules, to get that one clerk’s PC infected, and place at risk all the other networked sites used by that clerk’s PC, in the course of his or her work.
Many people are hired not for their cyber security expertise, but their abilities in accounting, human resources, the full spectrum of duties needed in any company.
@Siva, it looks easy when you have no firsthand experience with this sort of thing. Your comments show your ignorance clearly.
1) it is not tech support staff that is targeted, it is non-technical business users such as HR or sales.
2) the attachments appear to come from known sources not unknown senders, thanks to preliminary reconnaissance by the attackers, and forged email headers.
3) the better attacks are well crafted emails and often appear legitimate until header internals are examined (mailer forwarding chains, originating IP addresses, etc.).
4) saying that Flash can be disabled overlooks the fact that nobody would expect Microsoft to routinely open Flash objects embedded in an Excel spreadsheet to even think of disabling it.
etc.
Great work Brian!
“This is the first in a series of planned stories on the RSA attack and the menace from advanced persistent threats.” – Sounds interesting, can’t wait 🙂
@Siva, I open unknowns attached files for fun, I decompile them and I realize which kind of attack have the sender in his mind! It’s funny.
But yes, it’s important to avoid to run all the SPAM we receive in the mailbox, can seriously compromise a Windows Machine in seconds.
By the way, this kind of twitter attack… it’s not the first time that I see something like this, I was able to read some identical “memes” on identi.ca… at the end nothing new, but cool hacking technique too!
No, wait! It’s still there! I cant believe…
http://identi.ca/key
I dont know it’s since one year I notice this username writing this things…