I’ve written a great deal about “money mules,” people looking for part-time employment who unwittingly or willingly help organized cyber thieves launder stolen funds. The most common question I get about money mules is: “Do any of them ever get prosecuted?” The answer is generally “no” because it’s hard to prove that these mules weren’t scammed. But recently, I encountered a mule who made it abundantly clear that he understood exactly what he was doing.
In June 2011, I was investigating an online banking heist against a company called Jackson Properties. Thieves had broken into Jackson’s computers and stolen the firm’s online banking credentials. They added a half dozen money mules to the company’s payroll account, using mules they’d acquired from a gang I call the Back Office group. This mule gang uses multiple bogus corporate names, and the Back Office front company that supplied the mules in this attack was called AMR Company.
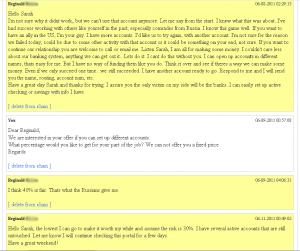
Reginald, a 45-year-0ld Texas resident, was among the mules hired by AMR Company. Reggie communicated with the mule recruiters by logging into a Web site set up by the fake company, and checking for new messages. A source who had figured out how to view the administrator’s account (and hence, all messages on the server) sent me some choice screenshots from several mule communications.
On June 7, the mule recruiters sent Reginald a transfer of $4,910, claiming that Jackson Properties was its client. Reginald was to withdraw the money in cash and wire it overseas, minus a small commission. The payment never landed in his account; it was blocked when Jackson detected the fraudulent transactions and worked with its bank to get them reversed.
But that apparently did not deter our Reginald, who told his recruiter and manager at AMR Company that he understood the whole thing was a scam, and that he had done this sort of thing before. He said he was ready and willing to open additional bank accounts to help with future fraud schemes.
On June 8, Reggie signed into his account at AMR Company and wrote the following to Sarah, his erstwhile boss:
“Let me say from the start. I knew what this was about. I’ve had success working with others like yourself in the past, especially comrades from Russia. I know this game well. If you want to have an ally in the US, I’m your guy. I have more accounts. I’d like us to try again, with another account…Listen Sarah, I am all for making some money. I couldn’t care less about our banking system, anything we can get out [sic] it. Lets [sic] do it. I cant do this without you. I can open up accounts in different names, that’s easy for me. But I have no way of funding them like you do. Think it over and see if there’s a way we can make some money. Even if we only succeed one time…we will still succeeded. I have another account ready to go. Respond to me and I will send you the name, routing, account num, etc.”
The eager mule ended his proposal with a startling declaration:
“Have a great day, Sarah, and thanks for trying. I assure you the only victim on my side will be the banks. I can easily set up active checking or savings with info I have.”
Sarah wrote back that she was interested in his idea:
“Dear Reginald,
We are interested in your offer if you can set up different accounts. What percentage would you like to get for you part of the job We can not offer you a fixed price.”
Reginald replied:
“I think 40 percent is fair. That’s what the Russians give me.”
Apparently, Reggie’s percentage was too high; he never heard from Sarah again, even after he offered to lower his cut to 30 percent of future fraudulent transfers.
I could not reach Reginald at the number he gave to AMR Company; the line was disconnected. But a search on his email address revealed more information about his current activities. He is currently the registered contact for a shady-looking enterprise that has all of the hallmarks of a multi-level marketing or pyramid scheme.




Wow! Well, I would hope that it’s possible for him to be prosecuted if he’s caught. It amazes me how people don’t realize, ok most likely don’t care, about the people they’re impacting.
Unfortunately, such activities may necessitate some type of national tracking database of money mule participants, to crack down on the “Reginalds” out there.
Many mules allegedly recruited through phony job ads whose text is pretty standard. FTC FBI ought to be able to trace by locating suspicious text.
Someone like Reginald cannot be doing the standard approach where the stolen money goes to bank account in Reginald real identity, then gets re-transmitted.
Reginald needs to have a string of phony accounts, so that when any one of them is traced, he is long gone.
In other words, he is in the identity theft business, in addition to the mule business.
What is the web address for Back Office group?
“Brown.” Is he Reginald Brown?
How does a banking client restrict online banking features?
Is there an option to prevent the addition of new Account Payable entries?
If there was a procedure for double checking (triple?) the adding of accounts payable, then Money Mules would cease to have a function. No institution would approve the sudden addition of a bunch of unknown entities to its payable accounts.
If banks would require a 2 week delay for adding payables, then this sort of bank theft would be greatly diminished.
If banks required a multi-factor (RSA keyfob or cellphone text message) over voice lines before the bank would add a new account, then Money Mules would be close to being out of business.
I can not figure why this simple procedure is not already the standard.
Money mules operate after the bank heist occurred … like in the physical world when masked people with guns go off with money to getaway driver to some place where they switch vehicles and the money mules are involved, while the bank accounts of customers are insured.
Techniques of thieves are a moving target needing evolving defenses, where some defenses become no good as thievery techniques figure out how to defeat them.
This applies how the bank functions, how the bank customer accounting functions, and how the two are reconciled. Account Payable entries are constantly added as part of the job of the AP clerk. If the clerk is only checking input that the clerk knowingly made, then the business never catches input made in the name of an authorized person, but not by that person.
A hardware appliance with a trusted path totally defeats schemes like this. Me, Mark Currie, Clive Robinson and tommy discussed numerous solutions at various price points on Schneier’s blog (link below). My appliance was to prevent ACH fraud (among other things), would be designed using high assurance principles, and cost from $200-2000. Clive promoted the principles behind its design. Mark Currie pushed for a SSL offloading & password substituting device that he prototyped at around $10 cost. Tommy pushed for a standardized, hardened LiveCD that could only connect to the bank’s web site & never touched RAM.
I determined that combining the concepts allowed a LiveCD or LiveUSB solution that would be certifiably immune to most attacks. (Possibly using Mark Currie’s device for the login.) The solution would be anywhere from $1-10 per customer per year. In other words, we can easily beat this stuff & cheaply, but banks wont do it. The court rulings saying their current measures are OK are a problem too. There’s little incentive to secure their systems if the courts rule they’re secure enough already. But, if a bank really wants to, we can do it cheaply.
Court Ruling on “Reasonable” Electronic Banking Security
http://www.schneier.com/blog/archives/2011/06/court_ruling_on.html#comments
Speaking generally, businesses are by nature conservative – well, the mature end of the spectrum is anyway.
If something works most of the time and makes money over and over again often the organisation is loathe to change anything unless they “have to”. It is, as they say, better to have 80% of something (the existing process) than the risk of 0% of something (if the new process – ie. your proposals – don’t work as expected, don’t prevent further attacks etc and so on.)
Which probably (this is purely a guess on my part) means the problem of fraud isn’t big enough to pose a large risk to the organisation where risk means a loss of money large enough to offset the fact that the existing processes work most of the time essentially.
Working in online banking security for a swiss bank we’ve tested the user acceptance of devices like hardened usb sticks. There are already devices like that available on the swiss market (expensive) http://www.crealogix.com/en/products-services/e-banking/products/clxsentinel.html
Problem is, 99 of 100 customers didn’t like the hassle of setting it up and using it.
Regarding money mules. We don’t have any problems in switzerland to get them prosecuted. They are guilty of money laundering as soon as they transfer the money away through western union etc. even if they haven’t been fully aware of what they are doing. In most of the cases i was involved with the sad thing was that those people weren’t intelligent enough to see what they where doing. Some of them really believed that they’ve found a legit job in transferring money out of the country
Regarding online banking security in switzerland i can say that the banks are pretty secure. All of them use three factor authentification (ID/password/cardreader, mobile phone..) and are requiring the signing of suspicious transactions by the user. Problem is that most of the attacks are MITM or MITB and there is not a lot the banks can do about it.
Some questions I have had about mules.
1) What are the likely consequences to a mule taking the money and not forwarding it?
2) What if law enforcement were to pose as mules, opening multiple accounts under multiple names, etc.? (All “legally”, with the cooperation of the banks, prosecuting attorneys, etc.) If the market for recruiting mules were sufficiently flooded with bogus mules, be they law enforcement of other concerned parties, would that force a change in the behavior of those perpetuating the bank heists? If they could not count on receiving their ill-gotten money, what would they do? A “poison” few percent of the mule population might be all it would take. If the current mule system were unreliable, the offenders would of course try something else, but for a while would be much reduced in what they take.
I keep asking the same question but would take it a step further: Why not have those fake mules’ accounts used as alerts to unauthorized activity, so that all the other transfers out of a victimized account are reversed as soon as one is sent to a decoy account? It could all be done before the banks open in the morning and allow the other mules in their doors to make their withdrawals.
(1) This is why the people, who remove the money, send it to multiple mules.
They might steal $ 1 million, but each mule gets no more than $ 10,000.00 to move, and keep their 10% or whatever.
The main reason they break up their takings are US currency laws. Transactions above a certain amount have to be reported by the financial firms handling them. These laws were originally designed to thwart drug cartels and terroroists.
So, any chance this guy was actually an undercover mule?
It’s funny, I read Reginald’s initial email and it reads like someone who’s trying *too* hard to get some work… discretion goes a long way in both sides of society and this guy seems to be lacking it in a way that belies his savvy at accumalating multiple bank accounts (and presumedly multiple identites?).
As an aside, if I were running a shady corp and relied upon mercs like this, recalling Machiavelli’s The Prince, I wouldn’t want ones that were too smart… or too dumb. This guy is a weird mix of both… could have a higher throughput for cash flow, but he’s either playing me to be trusted with more money at one time (so he can disappear with a big score at one time) or he’s just greedy and presumedly sloppy and hasn’t been “in the game” long enough to roll in and demand a 40% cut on an initial exchange.
Well presumably the Back Office group was well aware of all this since he apparently didn’t get a reply.
I doubt he was undercover TBH as it takes some level of intelligence and awareness of human nature to carry out undercover work and an agent working on organised crime is unlikely to be on his first rodeo if you get what I’m saying.
Yeah, good point, of course, they wouldn’t put a rookie in as mule. But the silence could also be because by the 8th, the BOG knew something was up and figured to jsut dump and restart elsewhere…
So the Reginald’s desperation could just be an eagerness for a payout – like a pushy sales guy. How drole.
So rather, I’ll just conclude Reginald is a guy more likely angling to be trusted with more $ at one time (either for income flow sake or looking to cash in by pocketing all of the transfers at once (if the BOG would be dumb (or desperate) enough to send dough to all of his accounts at once.))
🙂
Ditto on “he’s trying too hard, is he real” comment. I wonder what linguistic analysis could be done.