How much does it cost for thieves to discover the data that unlocks identity for creditors, such as your Social Security number, birthday, or mother’s maiden name? Would it surprise you to learn that crooks are selling this data to any and all comers for pennies on the dollar?
At least, that’s the going price at superget.info. This fraudster-friendly site has been operating since July 2010, and markets the ability to look up SSNs, birthdays and other sensitive information on millions of Americans. Registration is free, and accounts are funded via WebMoney and Liberty Reserve, virtual currencies that are popular in the cybercriminal underground.
Superget lets users search for specific individuals by name, city, and state. Each “credit” costs USD$1, and a successful hit on a Social Security number or date of birth costs 3 credits each. The more credits you buy, the cheaper the searches are per credit: Six credits cost $4.99; 35 credits cost $20.99, and $100.99 buys you 230 credits. Customers with special needs can avail themselves of the “reseller plan,” which promises 1,500 credits for $500.99, and 3,500 credits for $1000.99.
“Our Databases are updated EVERY DAY,” the site’s owner enthuses. “About 99% nearly 100% US people could be found, more than any sites on the internet now.”
Customers who aren’t choosy about the identities they’re stealing can get a real bargain. Among the most trafficked commodities in the hacker underground are packages called “fullz infos,” which include the full identity information on dozens or hundreds of individuals.
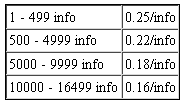 The table at the right shows the bulk lookup price-per-identity in this class. In the “Fullz Info USA Type A” package, each record includes the subject’s first name, last name, middle name, email address, email password, physical address, phone number, date of birth, Social Security number, drivers license number, bank name, bank account number, bank routing number, the victim employer’s name, and the number of years that individual has been at his or her current job. The proprietor of this shop says he has more than 330,000 records of this type, and is adding 300-400 new records each day.
The table at the right shows the bulk lookup price-per-identity in this class. In the “Fullz Info USA Type A” package, each record includes the subject’s first name, last name, middle name, email address, email password, physical address, phone number, date of birth, Social Security number, drivers license number, bank name, bank account number, bank routing number, the victim employer’s name, and the number of years that individual has been at his or her current job. The proprietor of this shop says he has more than 330,000 records of this type, and is adding 300-400 new records each day.
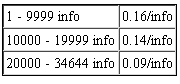 If you want the mother’s maiden name included in each of the bulk records, you’ll need to select “Fullz Info USA Type B”; the site’s owner says this package includes data from an older database, and perhaps that explains why the prices for these identities (pictured at left) are so much lower than those in the Type A category. The price in Type B starts at 16 cents per identity, and falls as low as nine cents per record for those requesting more than 20,000 fullz from this category.
If you want the mother’s maiden name included in each of the bulk records, you’ll need to select “Fullz Info USA Type B”; the site’s owner says this package includes data from an older database, and perhaps that explains why the prices for these identities (pictured at left) are so much lower than those in the Type A category. The price in Type B starts at 16 cents per identity, and falls as low as nine cents per record for those requesting more than 20,000 fullz from this category.
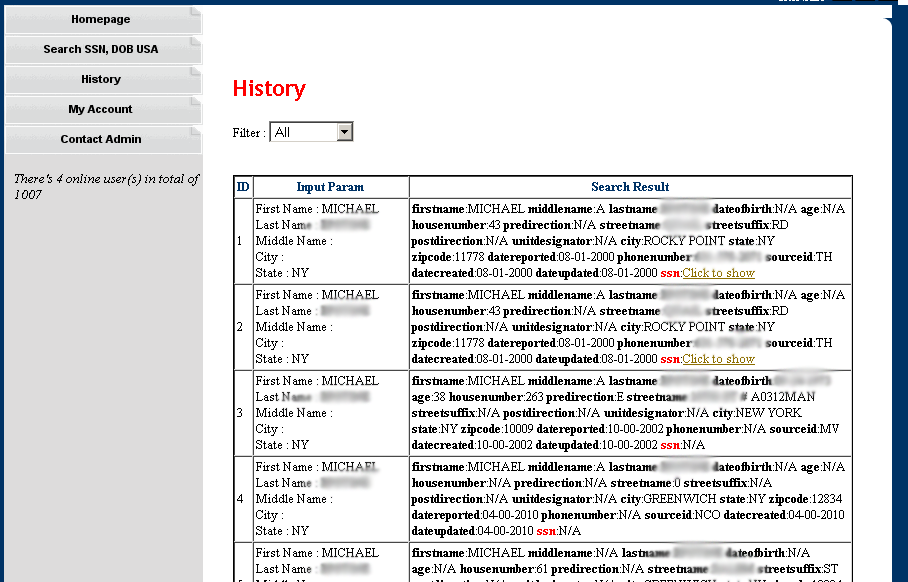
It’s not clear how many records Superget has got, but even lookups for uncommon names produce numerous “hits.” Interestingly, each purchasable record contains a two- to three-letter “sourceid,” which may provide clues as to the source of this identity information. In the screen shot below, there are three different sourceids shown: “TH,” “MV,” and “NCO”. I found two other sourceids, including “EX” and “CM,” but there may be others I haven’t yet encountered. If anyone has a clue what these abbreviations stand for, please drop me a line in the comments or via email. My money is on the credit reporting bureaus and/or state motor vehicle departments, or real estate firms that have access to such information.
I scoured the interwebs for this domain to see who might be promoting it. I found a scammer-friendly forum called talkgold.com where a user named “hieupc” is promoting superget.info as his site. It’s unclear whether this same individual is related, but there is a fairly active Vietnamese hacker who uses the nickname “hieupc;” That user appears to have gotten started defacing Web sites, even attacking the Web site of his former university in New Zealand after the school kicked him out for alleged credit card fraud. As it happens, the Web server address history for superget.info shows that it was hosted last year in Vietnam.
This hieupc character struck me as a bit too amateurish to have come up with this service on his own, so I had another look around the underground for some more clues. I can’t be certain, but it appears that Superget is little more than a reseller of this service, which offers the same products but at a slightly cheaper price point.
[EPSB]
Have you seen:
How Much is That Phished PayPal Account?…Compromised PayPal accounts are a valuable commodity in the criminal underground, and crooks frequently trade them in shadowy online forums. But it wasn’t until recently that I finally encountered a proper Web site dedicated to selling hacked PayPal accounts.
[/EPSB]




You do realize that in the screen cap you took in the very first item you block out the person’s name but not their telephone number.
A reverse look-up indicates the phone number is listed in the same location so it could very well be a “live” number.
Thanks. I’ve fixed that. Then again, sounds like I haven’t leaked any data that wasn’t already public.
Excellent reporting as usual Brian. Terrible that prices are so low now, as barrier to entry is basically nonexistent for aspiring criminals. I’d say the only good news is that protection against identity theft has gotten much better than it was in the late 90’s when the crime was flourishing. Back then, an identity thief could easily pull $100k-300k off a single target (and maybe jail-free if caught). Today, it’s nowhere near as profitable for them & financial traceability is higher.
(Probably contributes to the high volume & low pricing of fullz: their profit margins these days are more like grocery chains than, say, Apple or Microsoft. I’d say increased supply is the main driver, though.)
NCO is maybe http://www.consumerhelpunit.org/about-us.html
Founded in 1926, NCO Financial Systems, Inc. has more than 83 years of experience in working with both consumers, businesses, and other organizations to resolve debts owed by one party to another in a timely and accurate manner. As part of our services, we talk with and/or correspond with literally hundreds of thousands of consumers annually. In working with consumers and businesses, NCO Financial Systems, Inc. is committed to maintaining the highest standards of ethics, professionalism, and customer service, treating others with respect, complying with applicable regulations, and protecting the security and confidentiality of account information.
For whatever reason, my browser redirected your http adress to the following:
http://www.nomenu.com/Images/GeorgeBurnsSpam.gif
Mine doesn’t, FF. The site describes what the poster says… for what it’s worth…
Great. We need good Spam.
Not sure why this is so heavily downvoted. Do people disagree with the suggestion for NCO or consider it spam? Have more people gotten KFritz’s odd redirect? (The link worked for me, too.) Krebs specifically requested: “If anyone has a clue what these abbreviations stand for, please drop me a line in the comments or via email.”
I know it’s a bit late, but thanks to anyone willing to satisfy my curiosity.
MV is motor vehicle departament like this http://www.nydmv.state.ny.us/licrepl.htm
How different is this than the “PI” and “US Search” type databases available just about everywhere on the web? I know with very little effort I can uncover just about the same amount of information, albeit with a higher price point per hit.
I think we’ve hit the point where databases know everything about us, and the assumption should be information is out there. That doesn’t negate the duty of the legitimate holders of that information from doing their due diligence. But it seems that protection from identity theft may need to move to the next level with 2 and 3 stage authentication for *using* that information.
Hrm. I’m not sure you can buy full social security numbers and mothers maiden name in services like US Search, although I could be wrong. When I was at The Washington Post, we used to have access to partial SSNs and full birthdays, and it wasn’t hard to figure out MMN with that level of access. But full SSNs were reserved for law enforcement access, through a related service called Accurint. Someone correct me if I’m wrong, but I don’t believe US Search offers MMN and full SSN, at least not to the average commercial customer off the Web.
Accurint no longer gives up full SS#’s – although you may search with them if you already have it.
It seems to me that identity theft has more to do with convenience than the possession of specific information. The more convenient it is to use the info, the easier it is to steal an identity. The answer is to take a step back in convenience in exchange for improving the security of a customer’s assets, be they credit, money or property. In the old days, the banker knew his customers by face. Joe Blow couldn’t walk into the bank, claim to be John Smith and clean out Smith’s account – and knowing Smith’s SS # or his mother’s maiden name wouldn’t be worth a damn. True, we can’t do the face thing but we CAN emulate it. The answer is that you don’t gather all sorts of info on the front end of the credit relationship and then rely on that data for identification. You verify a person’s identity AT THE POINT of each transaction. The first step is to find an equivalent of the banker’s face ID and then use that to verify every change to the account (except closing said account) AND every purchase. Perhaps a cell phone number could be the ID. A customer provides it on his/her application and the credit provider verifies that the name, address and SS# on the application are the same as for the phone number. Better yet, in addition to the contact phone number, require a photo ID and fingerprint and/or eye scan and/or voice sample. Whatever it takes. Thereafter, every transaction has to be verified by the credit provider calling the customer at the contact phone number. If the person who answers the phone isn’t the person whose info is on the account, the transaction fails… and once again, knowing the person’s SS# or mother’s maiden name will be useless. The person trying to use the account will have to actually be the owner of that account.
I guess there’s a good chance this is the guy’s Flickr account…Pham Chung Hieu
https://secure.flickr.com/photos/11619682@N06/
Seems he likes the German Chancellor a lot.
On an unrelated note: The “Have you seen” layer advertising related articles in the bottom-right corner is very annoying.
MisFocused. WHO CARES about PII!
I mean really, there are controls that can stop attacks. Why not actually address the issue instead of looking to address the symptoms? When we look at controls over privacy to stop the “bad guys” using our information, we have created a fragile structure that can collapse without warning. It is about time we look at more resilient controls that actually work. The thing is, they are simple and cheap anyway.
http://gse-compliance.blogspot.com/2011/11/obscurity-and-pii.html
If our PII is already out there, then the cat is out of the bag and there is no way to get it back into the bag to protect with some sort of control. Make the current PII we have worthless, so the new controls have something to protect.
Mother’s maiden name should have been done away with eons ago. Especially since it may be YOUR name.
It’s time to completely start over.
Good work on your article Brian. Very well written.
@Lori There are controls. They are just not obscurity based.
I am an Executive Director at a company called LegalShield. Our affiliate partner is Kroll, the leading risk management company in the World. They operate on 6 different continents and keep us updated with tons of information. It is amazing to see how fast this crime can turn someone’s life into such turmoil. I would encourage anyone looking to further educate themselves and further more learn how to protect themselves from this to check out http://www.legalshield.com/hub/tonybasford. This company can help you with ‘legal’ and ‘restoration’ services. Identity theft as we all know is the fastest growing in the history of our Country. Kroll iand LegalShield are both 40 year old companies that have been leaders in this industry for quite some time now. 1 out of 10 Americans were effected by this dilemma this year. Identity theft will effect 1 out 4 in 2012. It wise to study post like this and gather knowledge from as many credible sources as you can. Education on this matter is the only way to get some kind of handle on this problem. Thanks for the information and I hope all of you never have to suffer at the hands of this horrible crime.
This is all news to me. I can’t believe all our PII is on the internet and anyone has access to it. Is anyone like the government doing about this? Maybe there should be a way to change our PII just like changing our password every so often.
Its no secret that the login credentials to credit reporting agencies are being swiped by ZeuS and other malware. The creds are then used to query credit reports for a variety of nefarious means like vetting money mules, identity theft, wholesale to others, etc. Think about how many companies have credit bureau login creds: banks, car dealers, rental companies, gyms, the list goes on….all compromised. Bad stuff.